Disabling ASLR when debugging third-party iOS apps
 This article provides a simple short tutorial on how to patch a third-party iOS application to disable ASLR during debugging. It is assumed that the reader has:
This article provides a simple short tutorial on how to patch a third-party iOS application to disable ASLR during debugging. It is assumed that the reader has:- iOS 7.0-7.0.4 device with evasi0n jailbreak and computer with Mac OS X 10.9.4 installed by XCode 5.1.1 and MacOView 2.4 (most likely for other versions will work too, but I have not tried it)
- some experience in debugging third-party iOS apps, well, it’s advisable to know what ASLR is and why you need to disable it
Well, let's get started.
To begin, select the executable file in which we will debug and in which we need to disable ASLR. Let it be the demon
/usr/sbin/absd , which is responsible for authorization in some Apple services. Of course, absd here solely for example, in fact, you can take any executable file.')
We use
scp to copy our executable file to the computer (hereinafter, 192.168.1.112 is the IP address of our iOS device): $ scp root@192.168.1.112:/usr/sbin/absd ./ WARNING! Before you do something with absd, be sure to save a copy somewhere!
Then we will use the
codesign utility from XCode and extract the plist with the list of entitlements from our executable file (I don’t know how it is in Russian, can a “list of rights”?): $ codesign -d --entitlements - absd > absd.entitlements After that, open the executable file in MachOView and find the Mach header for the architecture of interest. In the case of fat binary, there will be several such headers - one for each architecture; if we are not fat binary, there will be only one header. In the header, find the
MH_PIE flag and note the corresponding offset. In MachOView it all looks like this: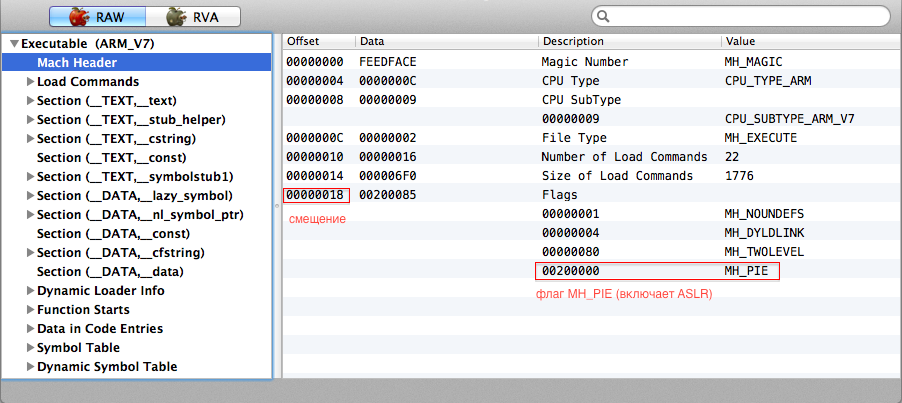
The flag needs to be reset, but in MachOView this cannot be done, so we will open the executable file in any HEX editor, go over the corresponding offset and reset the flag. Then rewrite the executable file with the retained entitlements:
$ codesign -s - --entitlements absd.entitlements -f absd and copy it back to the device
$ scp ./absd root@192.168.1.112:/usr/sbin/absd That's all. Now if you call a daemon - for example, logging in to iMessage - and drive it under debugging in lldb, we will see
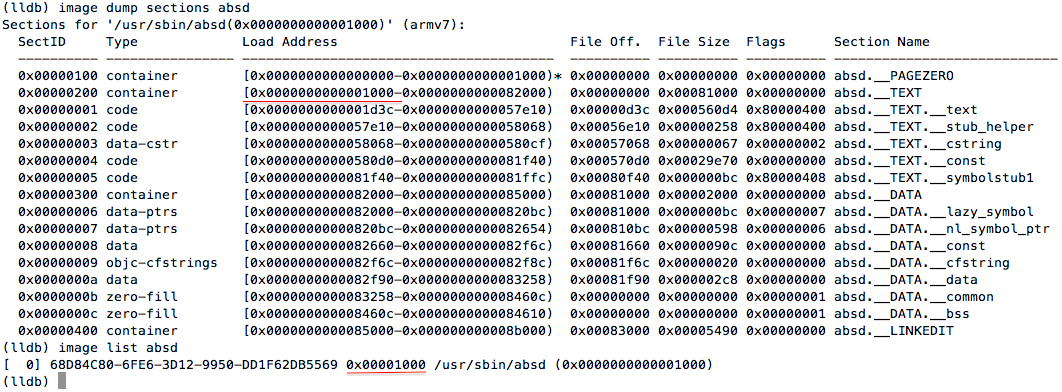
(if you are sitting on gdb instead of lldb, use the appropriate commands ). As you can see from the screenshot, no more ASLR! That's the whole manual - simple and short, as I promised at the beginning of the article.
PS Just in case: the author is aware that the method proposed in the article is not always the most optimal. The author is also aware of alternative ways to disable ASLR, and maybe they will be discussed in the following articles. But just today - an article about the Mach-header patching.
Happy debugging!
Source: https://habr.com/ru/post/210858/
All Articles