[Translation] We are looking for who sent the letter from the general mailbox. Using the Microsoft Exchange Event Log
The author of the article is Paul Cunningham, a Microsoft MVP status holder and several certificates for Exchange Server 2007, 2010 and 2013. Paul is also the publisher of Exchange Server Pro .
Original material in English .
In the years of my work as an administrator of ExChange, the most frequent task from the category of “who did this ?!” was to find the sender of a specific letter from the general mailbox.
Imagine that the HelpDesk shared mailbox is used by a large team of IT staff and all these employees have permission to send emails on behalf of a shared account (for example, to send alerts about shutdowns or system maintenance).
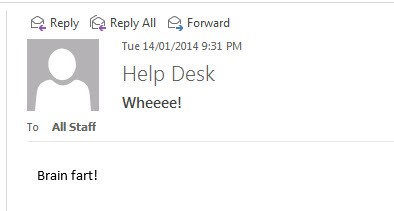
One day, an employee of the support service, tired of routine operations, sends a “brilliant” letter to the newsletter throughout the company, the letter receives a negative response.
')
The task is to find out who sent such a “gift”, the solution can be found in different ways: for example, you can track the ip-address from which the message was sent, then match the address with the computer and find the user. You can also spend time manually checking the Sent Items folder on all suspects. It is also a good option to ask the question who made it - sometimes you can hope for an honest answer.
In any case, the ability to determine the sender from the Exchange event logs does not hurt, and the good news is that there is such a possibility! (in case you use Microsoft Exchange 2010 SP1 or later, including Exchange 2013). The feature is called “mailbox audit logging,” and the bad news is that it is turned off by default. As you understand, the function had to be enabled before the incident with the letter, otherwise the dispatch event will not be included in the Exchange log.
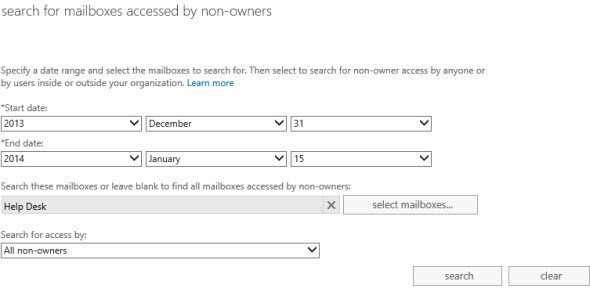
If the mailbox audit logging function was enabled before the incident, we can use the Exchange admin center: you must select the menu item “Compliance Management” and then “Auditing” on the right side of the screen.

You will see a list of several items, we are interested in the “Run a non-owner mailbox access report”
Set the required date interval, click on the “select mailboxes ...” button and select a shared mailbox, then select “All non-owners” in the Search for access by: list at the bottom of the screen and start the search! If a large interval of dates is chosen, or if employees are actively using the sending of letters on behalf of a general account, you will have to do a serious job to get to the bottom of the truth.
Another way to set the sender is to use the Search-MailboxAuditLog script.
For example, to search the journal for events that occurred from January 13 to 15, 2014. in the general HelpDesk mailbox, use the following command:
We will see that the time stamp corresponds to the letter sent and, also, additional information about the event that has occurred is displayed in the console. In order to see all the details you need to use the “–ShowDetails” parameter:
I described this common situation to demonstrate the importance and necessity of the mailbox audit logging function, I hope that you will think about including it in your organization, at least for the most important mailboxes.
___
Note:
This article describes the audit available in Exchange 2013. Unfortunately, for Exchange 2003/2007, such a detailed audit of mailbox access is not available.
For Exchange 2003 and 2007, one of the Netwrix Auditor modules is great. The program provides reports on access attempts (including date, time, list of actions with mailbox objects). The program can be tested online to evaluate its capabilities.
In addition, for Exchange 2003, 2007 and 2013 there is a module that reflects the information - who exactly assigned the rights to the user to the shared / alien mailbox. You can also test and see report examples online in test drive mode.
___
Question to the community: Did you have to deal with access incidents to other people's mailboxes? What means used?
Original material in English .
In the years of my work as an administrator of ExChange, the most frequent task from the category of “who did this ?!” was to find the sender of a specific letter from the general mailbox.
Imagine that the HelpDesk shared mailbox is used by a large team of IT staff and all these employees have permission to send emails on behalf of a shared account (for example, to send alerts about shutdowns or system maintenance).
One day, an employee of the support service, tired of routine operations, sends a “brilliant” letter to the newsletter throughout the company, the letter receives a negative response.

')
The task is to find out who sent such a “gift”, the solution can be found in different ways: for example, you can track the ip-address from which the message was sent, then match the address with the computer and find the user. You can also spend time manually checking the Sent Items folder on all suspects. It is also a good option to ask the question who made it - sometimes you can hope for an honest answer.
In any case, the ability to determine the sender from the Exchange event logs does not hurt, and the good news is that there is such a possibility! (in case you use Microsoft Exchange 2010 SP1 or later, including Exchange 2013). The feature is called “mailbox audit logging,” and the bad news is that it is turned off by default. As you understand, the function had to be enabled before the incident with the letter, otherwise the dispatch event will not be included in the Exchange log.
Search the sender using the Exchange admin center
If the mailbox audit logging function was enabled before the incident, we can use the Exchange admin center: you must select the menu item “Compliance Management” and then “Auditing” on the right side of the screen.

You will see a list of several items, we are interested in the “Run a non-owner mailbox access report”
Set the required date interval, click on the “select mailboxes ...” button and select a shared mailbox, then select “All non-owners” in the Search for access by: list at the bottom of the screen and start the search! If a large interval of dates is chosen, or if employees are actively using the sending of letters on behalf of a general account, you will have to do a serious job to get to the bottom of the truth.

Searching the sender using the PowerShell script
Another way to set the sender is to use the Search-MailboxAuditLog script.
For example, to search the journal for events that occurred from January 13 to 15, 2014. in the general HelpDesk mailbox, use the following command:
[PS] C:\>Search-MailboxAuditLog -Identity "Help Desk" -LogonTypes Delegate -StartDate 1/14/2014 -EndDate 1/15/2014 RunspaceId : d8142847-166a-488a-b668-f7b84c3f3ceb MailboxGuid : a0f10db1-5268-47a5-8f71-d1e65f55c653 MailboxResolvedOwnerName : Help Desk LastAccessed : 14/01/2014 9:31:08 PM Identity : exchange2013demo.com/Company/Resources/Help Desk IsValid : True ObjectState : New We will see that the time stamp corresponds to the letter sent and, also, additional information about the event that has occurred is displayed in the console. In order to see all the details you need to use the “–ShowDetails” parameter:
Desk" -LogonTypes Delegate -StartDate 1/14/2014 -EndDate 1/15/2014 -ShowDetails RunspaceId : d8142847-166a-488a-b668-f7b84c3f3ceb Operation : SendAs OperationResult : Succeeded LogonType : Delegate ExternalAccess : False DestFolderId : DestFolderPathName : FolderId : FolderPathName : ClientInfoString : Client=MSExchangeRPC ClientIPAddress : 192.168.0.181 ClientMachineName : ClientProcessName : OUTLOOK.EXE ClientVersion : 15.0.4551.1004 InternalLogonType : Owner MailboxOwnerUPN : Sarah.Jones@exchange2013demo.com MailboxOwnerSid : S-1-5-21-2175008225-1847283934-4039955522-1471 DestMailboxOwnerUPN : DestMailboxOwnerSid : DestMailboxGuid : CrossMailboxOperation : LogonUserDisplayName : Sarah Jones LogonUserSid : S-1-5-21-2175008225-1847283934-4039955522-1471 SourceItems : {} SourceFolders : {} SourceItemIdsList : SourceItemSubjectsList : SourceItemFolderPathNamesList : SourceFolderIdsList : SourceFolderPathNamesList : ItemId : ItemSubject : Wheeee! DirtyProperties : OriginatingServer : E15MB1 (15.00.0775.022) MailboxGuid : a0f10db1-5268-47a5-8f71-d1e65f55c653 MailboxResolvedOwnerName : Help Desk LastAccessed : 14/01/2014 9:31:07 PM Identity : RgAAAAD2fF/dZobvQoWbbV7P6N7eBwD7Y5OF+DDRQZRz1a4+yUyzAABaldDBAAD7Y5OF+DDRQZRz1a4+yUyzAABaldDCAAAJ IsValid : True ObjectState : New I described this common situation to demonstrate the importance and necessity of the mailbox audit logging function, I hope that you will think about including it in your organization, at least for the most important mailboxes.
___
Note:
This article describes the audit available in Exchange 2013. Unfortunately, for Exchange 2003/2007, such a detailed audit of mailbox access is not available.
For Exchange 2003 and 2007, one of the Netwrix Auditor modules is great. The program provides reports on access attempts (including date, time, list of actions with mailbox objects). The program can be tested online to evaluate its capabilities.
In addition, for Exchange 2003, 2007 and 2013 there is a module that reflects the information - who exactly assigned the rights to the user to the shared / alien mailbox. You can also test and see report examples online in test drive mode.
___
Question to the community: Did you have to deal with access incidents to other people's mailboxes? What means used?
Source: https://habr.com/ru/post/210702/
All Articles