Fortigate - a worthy replacement for the outgoing Microsoft Forefront TMG
For all, it has long been no secret that Microsoft announced the termination of the further development of its Forefront TMG product . At the same time, the product became unavailable to purchase from December 1, 2012, its main support will be discontinued after April 14, 2015, and extended support will end on April 14, 2020.
The remaining Forefront Unified Access Gateway (UAG) to publish web resources such as MS Exchange, SharePoint, Lync, etc., does not provide the security features previously provided by TMG, which is displayed in a small comparative table of functions:

And since we started talking about the necessary security functions, let us briefly indicate with which of them TMG was able to bring happiness to us, the users:
• Firewall;
• Web proxy;
• Reverse proxy for publishing internal resources;
• Web and Email Filtering;
• Protection against malware / spyware;
• Intrusion Prevention System (IPS);
• Inspection of SSL traffic;
• load balancing;
• Remote user access and VPN functionality, both client-server (client-to-site) and between sites (site-to-site).
')
Thus, the TMG users will sooner or later (based on the voiced end dates of support) will be asked about the choice and subsequent migration to similar third-party products.
For example, some of the companies (Sophos, Citrix, Cyberoam, WatchGuard, Kemp, etc.) have already started their campaigns (I think such a tautology would be appropriate) to actively promote software and / or hardware solutions and provide a full-featured alternative to the inevitable and outgoing Tmg This is confirmed by the presence in the network of advertising flyers, promotions and other marketing materials in the form of “TMG Replacement Guide”, “ {Vendorname} VS. TMG Comparsion ", etc.
Fortinet went the same way as the rest of the vendors and today also offers its “ Microsoft TMG Replacement ” based on the flagship of its own network security product line - FortiGate .
Since TMG itself (Threat Management Gateway) was positioned as a unified threat management solution, it is logical to look for a replacement for it just from the UTM list. Therefore, looking at Gartner Square: www.gartner.com/technology/reprints.do?id=1-1H1RO5D&ct=130710&st=sb , “magically” we see here Fortinet in leadership among UTM solutions, and this leadership is already quite long-term - almost 6 past years.
So, we proceed to a detailed consideration of the functions provided by the proposed "alternative" solution, which, according to the vendor, is capable of providing an equivalent replacement for our subject.
Actually, Fortinet's offer is to migrate to FortiGate the following list of functions:

Here, first of all, I would like to say that for large enterprises in the presence of a complex network infrastructure, it is recommended to divide their tasks and use certain narrowly focused solutions. Fortinet, in particular, can offer an implementation of such a separate and focused, but at the same time flexible and easily scalable approach using Fortinet equipment lines:
- FortiWeb - Web Application Firewall, a solution for protecting web resources and applications (including the implementation of Reverse Proxy with secure publishing of web resources);
- FortiMail , a comprehensive anti-spam solution for mail protection;
- FortiBalancer, FortiADC, Coyote Point Equalizer - all lines of load balancers and application delivery controllers.
To ensure a full range of network security measures, it’s better to supplement all this with the inclusion of FortiGate itself into the infrastructure; however, small and medium-sized enterprises can only be managed with the services of this solution in hardware or virtual execution.
So, what provides FortiGate in a section of functions similar with TMG? We will consider them one by one through the prism of replacing the TMG, and at the same time we will take a general look at the skills of FortiGate.
Firewall - the beginning began filtering unwanted connections from the outside, from the Internet to the corporate network. At the same time, it is necessary to keep records, control and delimitation of user access from inside the network to external resources. Therefore, in addition to packet filtering, address and port translation, support for deep inspection of packets with stateful / Deep Packet Inspection, the FortiGate is primarily a comprehensive network protection platform, running the full FortiOS single operating system security, such as: antivirus, antispam, application control, intrusion prevention system, web filtering, data leakage prevention and others.
With all the wide range of functionality, the standard policy for web user access from the internal network to the Internet, created in the FortiGate web interface, will look like this:

One of the oldest and most used TMG features for providing users access to the Internet without additional authentication.
In FortiGate, there is an “Explicit web proxy” function for transmitting HTTP (HTTPS) and FTP sessions through a proxy, plus support for auto-configuration using a PAC file.
Also, thanks to the Single Sign-On (SSO) function, fully integrated in FortiGate, it is possible to interact with a domain controller (Active Directory, Novell eDirectory) and control the access of authenticated users, applying necessary rights and capabilities to certain domain groups.
In addition, anti-virus protection, intrusion prevention, web filtering and application control can be included in such security policies.

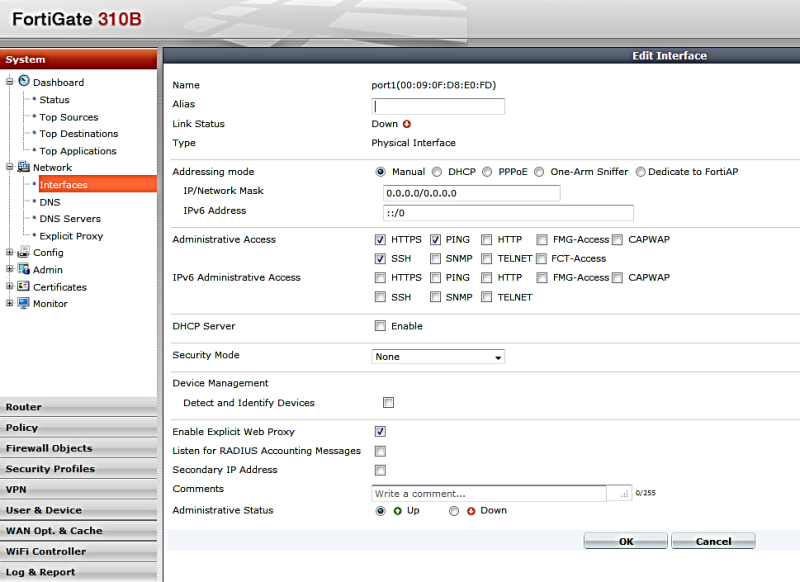
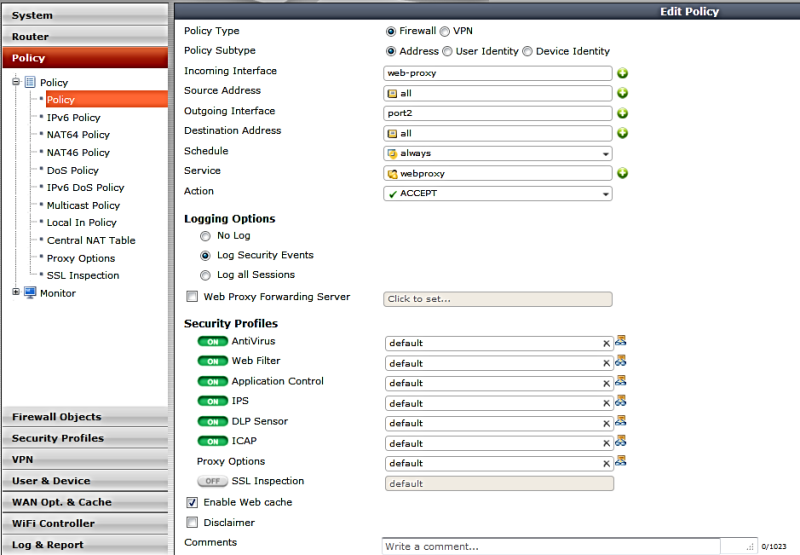
Web proxy is enabled on the required interface (s) ( “port1” in the upper figure) and by creating a permissive policy (in the figure below):
The introduction of Single Sign-On can be done in several ways:
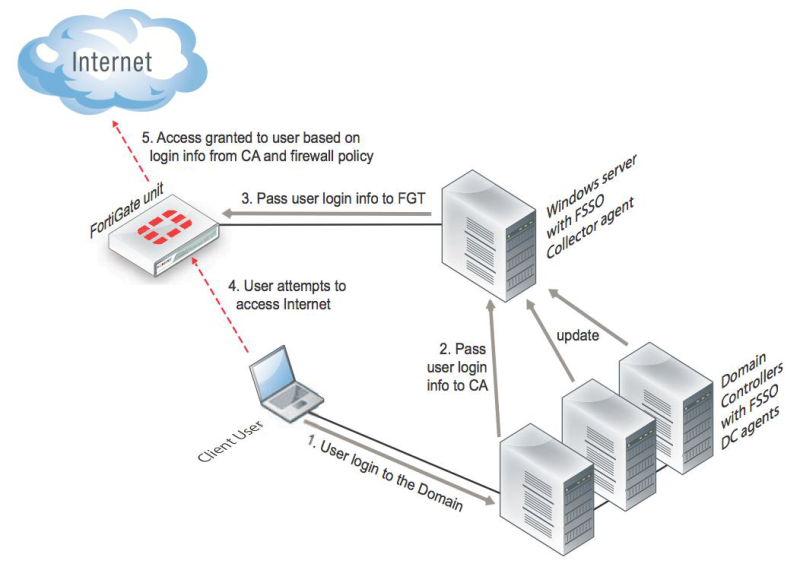
1. Using a special agent program on a domain controller ( DC Agent )
DC Agent is a software component in the form of a separate user tracking service installed on a domain controller. It interacts with FortiGate not directly, but through a collector agent (Collector Agent).
Collector Agent is installed on any server or, again, on a domain controller. The agent receives information about user logins and exchanges it with FortiGate. The number of agents installed can be more than one for fault tolerance.
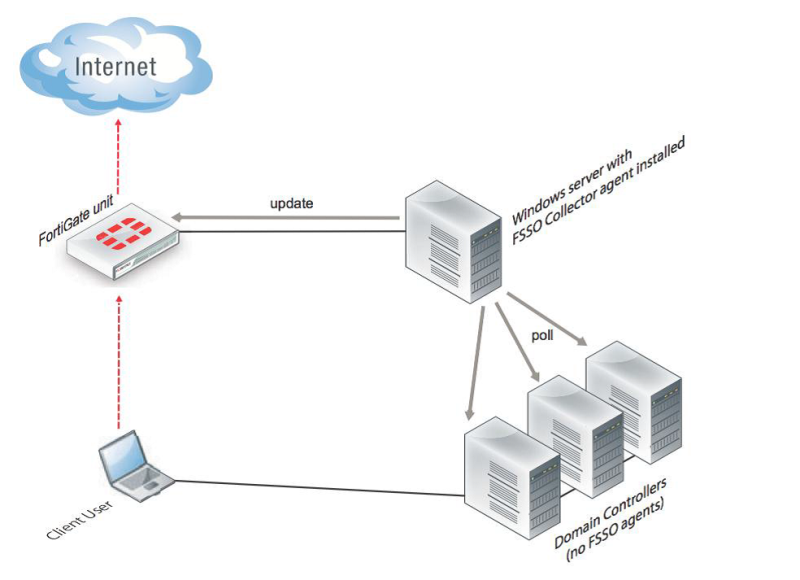
2. Poll Collector Agent
This method also provides for the installation of additional software in the form of a Collector Agent, but on the domain controller, the DC Agent service will not have to be installed. The Collector Agent can be installed anywhere on the network (preferably on one of the Windows servers) and then it can poll the domain controller about user authentication events (“logons”). Polling mechanisms are implemented using the Windows NetAPI or Security event log.
3. Survey directly with FortGate
Starting with FortiOS version 5, the logon polling mechanism from the domain controller was fully integrated into FortGate. At the same time, only the Security event log is used for polling, and the use method itself is positioned as for small network infrastructures, where there is no possibility to install the Collector Agent on the network perimeter.
However, at the same time, you should not forget that if FortGate saves you the trouble of installing software, it will take the load of storing the domain structure and polling user logons in your memory.
4. NTLM authentication
Using NTLM authentication requires an installed Collector Agent on the network perimeter to communicate with FortGate. When requesting a URL in a user's browser, FortGate will request its domain credentials (username / password), get it through a browser, check the Collector Agent for the user to belong to domain groups and provide access to resources according to its group security policy.
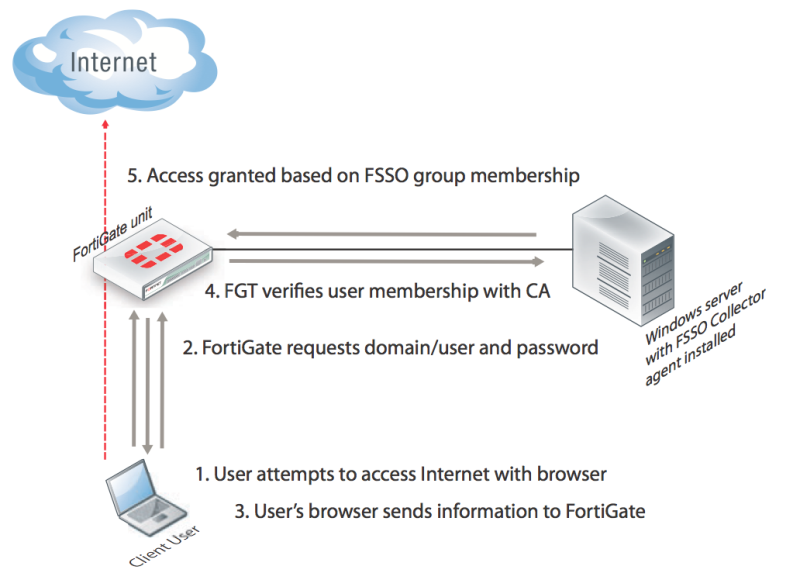
5. Terminal servers
Users who access corporate resources through Microsoft or Citrix terminal servers have one shared address or pool instead of their own IP address. For applying security policies to such users via SSO, Fortinet has another software component, the Terminal Server Agent (TS Agent), installed on the terminal server itself. He allocates a specified range of ports for each user and exchanges this information with the Collector Agent, which, in turn, knows about the user's belonging to domain groups, and which groups give what set of resources and which policy to apply - knows FortiGate. The agent looks like this:

On top of the description of the implementation of SSO, I would also like to note that the manufacturer seeks to improve the functionality even in the youngest UTM models. In confirmation of this, in 2012, the release of the radically reworked version of FortiOS 5 OS was announced, among the improvements of which was support for the Terminal Server Agent, and more correct operation of SSO as a whole, with its above-described abundance of application variations and auxiliary software.
Though believe, at least check, and taking the latest versions of the software: Collector Agent, DC Agent, TS Agent in combination with FortiGate on FortiOS version 5.0.4 and higher - everything will work like a clock. And if it will be interesting to comprehend the secrecy of SSO and dive into the details - we will “pisach ischo” about it, because This topic deserves a separate article.
Turning to the part of applying security policies, let's take a look at how it will look on FortiGate with successfully configured SSO software components:

The applicable rule for accessing a specific group or user is as follows:
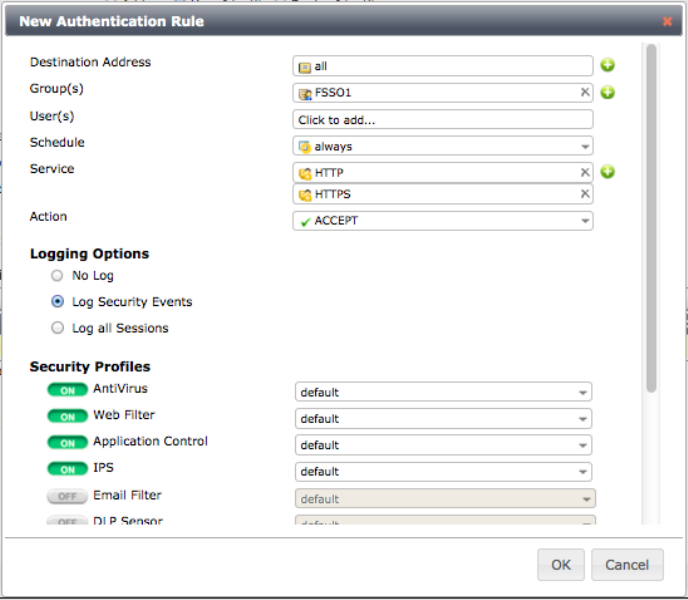
More differentiated policies with many different domain groups provide more options for controlling user access to network resources.
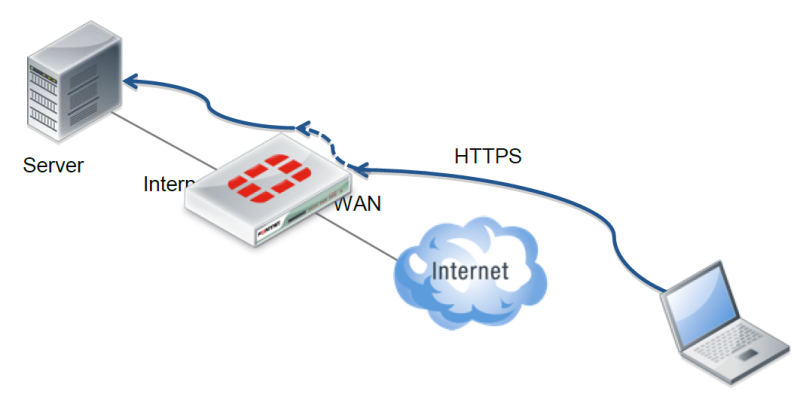
The main aspects of publishing an Outlook Web Access or SharePoint Web resource are the following:
- Broadcast external IP-address;
- Exchange of certificates with users from the outside.
First we need to import the certificate, this is done like this:
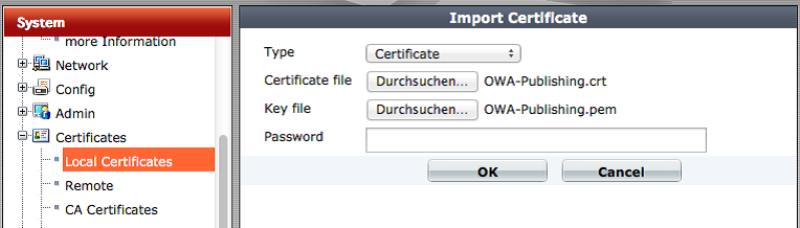
In the desired menu, simply select your certificate and click OK.
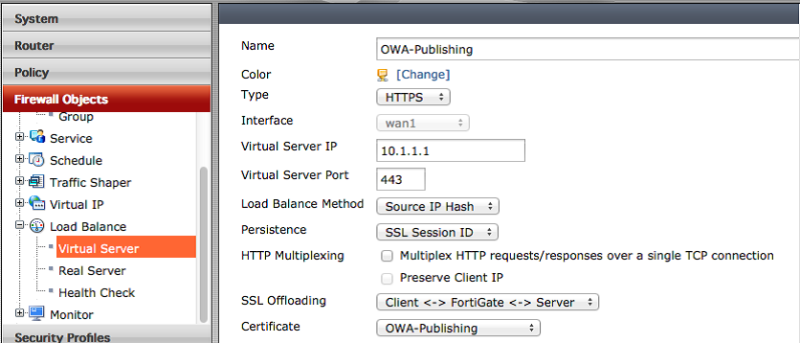
Further, to configure reverse proxy, you need to configure load balancing. Create a virtual server for this:
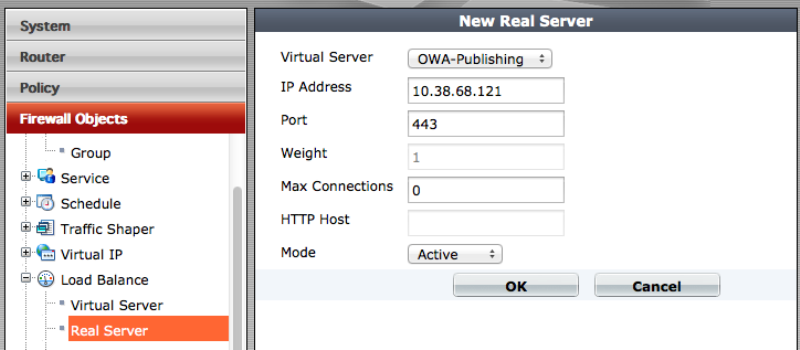
For a virtual server, you need to determine the real server:
The final step is to create a security policy where we allow traffic from outside:
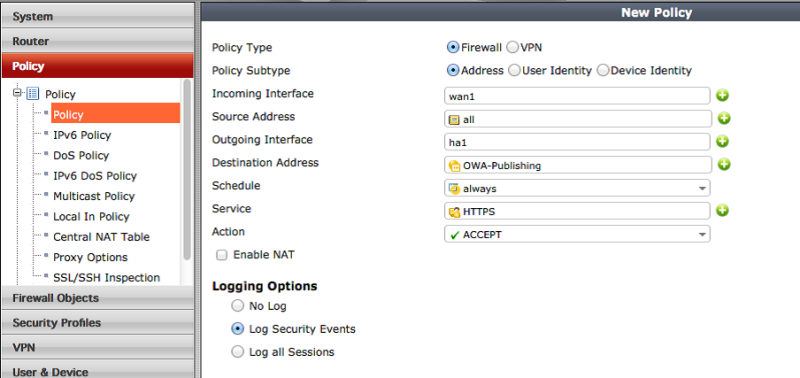
The incoming interface (Incoming Interface) in this case will be the external, source address (Source Address) will be “all”, and the destination address (Destination Address) will be the newly created virtual server. As a service, we skip HTTPS, because traffic exchange will occur only over HTTPS, and we don’t need more.
As with a regular proxy, it is possible to expand security features by including profiles in a policy:
- Antivirus protection;
- Intrusion Prevention Systems (IPS);
- Application Control (here we can limit or track down that, apart from the desired application, others are not used);
- URL filtering.
Another important feature when migrating from TMG is to inspect SSL traffic.
Turning on is as simple as other security features — a pre-configured profile in a policy.

Since the exchange of certificates is transparent to the end user within the network, you can use the standard embedded from the vendor, and if the internal server has its own self-signed certificate, you can simply enable “Allow invalid SSL Certificates”, because they will be perceived as incorrect, because Do not appear in the list of trusted Certificate Authority (CA).
In terms of publishing web resources on FortiGate, the inspection setting applies only to the published application and will not apply to other traffic, however, the SSL inspection function can also be used for more detailed control of SSL traffic for end users in corporate security policies.
In order to use the application control function, you must create an application “sensor”. This is the same profile, only - in profile :)
We look:
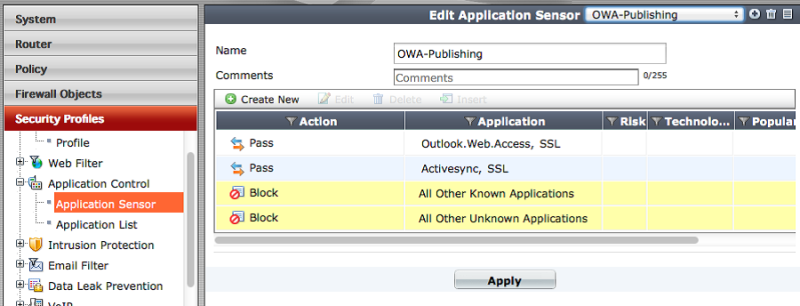
In our case, it is possible and necessary to select a specific application by switching the sensor type to “Specify Applications” and using the search method to find the desired application:

To be included in the security policy - again, a sensor for IPS is needed:
The only thing is that you cannot create a filter by application via the web interface, but this can be done from the CLI console by running such commands or copying them as a script:
After creating a filter in the CLI, it can use any signatures exclusively for IIS and Exchange.
Another “implicit” function is to write your IPS-signature to block access when you try to enter the wrong password. To create one for OWA 2012, it will look like this:
Here, the parameter "--rate 3,180;" symbolizes the number of false password entry errors (3) and the time of blocking the user by his IP address in seconds (180).
Antivirus profile looks like this:

As you can see, in addition to HTTP, there are other types of traffic (SMTP, POP3, IMAP, MAPI, FTP). We only need HTTP (S) for publishing.
So, put it all together. We create a policy for our reverse proxy with the publication, from the outside into the corporate network, or rather to the web application server, plus we include all configured profiles and sensors, including SSL inspection:

Now that we have examined in detail the issue of publishing OWA / SharePoint with the full possible set of security features, it is worth noting that publishing Lync as a web application takes place on FortiGate in almost the same way (address translation, certificate exchange, protection with UTM functions) and same protocols, with the exception of the need to control SIP traffic as well:

In order to take into account this aspect, in addition to the features described, FortiGate has built-in support for SIP ALG (Application Level Gateway), an application-level gateway that provides detailed inspection and filtering of SIP traffic. Like many functions of FortiGate, SIP ALG deserved from the manufacturer of a separate manual - so its detailed consideration also deserves a separate article in the future.
VPNs and secure encrypted access by remote users to corporate network resources or tunnels between separated sites of enterprises are already widely used for a lot of time, and TMG is not the only one here, providing us with this functionality. FortiGate is not a panacea either, but knowing that a solution for VPN can be done “out of the box” and that’s already, I'm sorry, moveton. Yes, and we made a reservation at the beginning that our solution is full-featured, so we will not cheat - but we will continue with the migration of all the functions of TMG.
So what do we have? We have L2TP / IPSec and IPsec VPN support for the so-called. "Site-to-site" connections and SSL-VPN for remote access from anywhere, which is quite suitable for "client-to-site".

For IPsec, several variations are available, a la static or “Dialup” -connections (having a static address on one side and dynamic from the remote end of the tunnel), Dynamic DNS. Tunnels are built between FortiGates and between PCs and FortiGate with the help of additional FortiClient software. There are many authentications (local user groups, local and remote host IDs, X.509 certificates, Active Directory credentials).
SSL is presented in two modes - web portal and tunnel. Web portals are designed for quick access to corporate resources from a web browser, which is especially important for thin clients and mobile devices. In this mode, FortiGate serves as a secure HTTP / HTTPS gateway, and authenticates users by giving them access to a web portal where HTTP / HTTPS, telnet, FTP, SMB / CIFS, VNC, RDP, SSH and other resources are available. Tunnel mode offers access to any application to the corporate network, but for this, FortiClient is installed or a separate part of it - the FortiClient SSL VPN application. FortiClient supports many operating systems: Windows, Mac OS X, Apple iOS and Android.
Another type of additional authorization for VPN is two-factor authentication using hardware FortiToken one-time password generator or FortiTokenMobile software for mobile devices.
In general, the VPN functionality is again quite wide and is described on a couple of hundred pages in all its glory, but at the same time, by practicing a little (straight arms) you can easily manage with numerous tunnels and web portals. Finally, we also note support for VPN tunnels with third-party (third-party) vendors, including the ability to connect to the Microsoft Windows Azure cloud service, which also uses IPSec VPN.
Finally, summing up all of the above, we can say with confidence that Fortinet, through its flagship FortiGate UTM device line, can provide with its purchase a very wide range of functionality for building an integrated network security system for enterprises of any size, while leaving a gap for their growth. You can not ignore the possibility of more narrowly enhancing protection using separate Fortinet equipment lines, such as: FortiWeb , FortiMail , FortiBalancer , FortiToken and FortiClient , which we mentioned as a transition from Microsoft TMG, as well as other product lines: FortiWifi and FortiAP for building secure wireless communications, centralized management of FortiManager , centralized reporting and analysis of FortiAnalyzer , protection from FortiDDoS DDoS attacks, FortiDB database protection, FortiCache web caching, FortiDNS caching DNS server, a separate authentication solution FortiAuthenticator invaders , work "in a gap" when FortiBridge network devices fail , FortiSwitch switching is not the end of the list ...
The issue of scalability needs to be addressed depending on the required functions previously used in TMG. And if you liked FortiGate alone or with another iron from Fortinet, then small businesses (up to about 100 users) should have paid attention to the FortiGate-90D model and lower, and to larger organizations - to FortiGate-100D and higher, t .to. support for some functions (as well as price) varies depending on the model.
In conclusion, I would like to emphasize on my own that whether or not FortiGate is worthy of becoming for you not only a full-featured, but also an imperceptible and problem-free transition from Microsoft TMG is up to you, of course. As for me - quite realizable.
Distribution of Fortinet solutions in Ukraine , Armenia , Georgia , Kazakhstan , Azerbaijan , Kyrgyzstan , Tajikistan , Turkmenistan , Uzbekistan , CIS countries .
Authorized Fortinet Training Courses
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
The remaining Forefront Unified Access Gateway (UAG) to publish web resources such as MS Exchange, SharePoint, Lync, etc., does not provide the security features previously provided by TMG, which is displayed in a small comparative table of functions:

And since we started talking about the necessary security functions, let us briefly indicate with which of them TMG was able to bring happiness to us, the users:
• Firewall;
• Web proxy;
• Reverse proxy for publishing internal resources;
• Web and Email Filtering;
• Protection against malware / spyware;
• Intrusion Prevention System (IPS);
• Inspection of SSL traffic;
• load balancing;
• Remote user access and VPN functionality, both client-server (client-to-site) and between sites (site-to-site).
')
Thus, the TMG users will sooner or later (based on the voiced end dates of support) will be asked about the choice and subsequent migration to similar third-party products.
For example, some of the companies (Sophos, Citrix, Cyberoam, WatchGuard, Kemp, etc.) have already started their campaigns (I think such a tautology would be appropriate) to actively promote software and / or hardware solutions and provide a full-featured alternative to the inevitable and outgoing Tmg This is confirmed by the presence in the network of advertising flyers, promotions and other marketing materials in the form of “TMG Replacement Guide”, “ {Vendorname} VS. TMG Comparsion ", etc.
Fortinet went the same way as the rest of the vendors and today also offers its “ Microsoft TMG Replacement ” based on the flagship of its own network security product line - FortiGate .
Since TMG itself (Threat Management Gateway) was positioned as a unified threat management solution, it is logical to look for a replacement for it just from the UTM list. Therefore, looking at Gartner Square: www.gartner.com/technology/reprints.do?id=1-1H1RO5D&ct=130710&st=sb , “magically” we see here Fortinet in leadership among UTM solutions, and this leadership is already quite long-term - almost 6 past years.
So, we proceed to a detailed consideration of the functions provided by the proposed "alternative" solution, which, according to the vendor, is capable of providing an equivalent replacement for our subject.
Actually, Fortinet's offer is to migrate to FortiGate the following list of functions:

Here, first of all, I would like to say that for large enterprises in the presence of a complex network infrastructure, it is recommended to divide their tasks and use certain narrowly focused solutions. Fortinet, in particular, can offer an implementation of such a separate and focused, but at the same time flexible and easily scalable approach using Fortinet equipment lines:
- FortiWeb - Web Application Firewall, a solution for protecting web resources and applications (including the implementation of Reverse Proxy with secure publishing of web resources);
- FortiMail , a comprehensive anti-spam solution for mail protection;
- FortiBalancer, FortiADC, Coyote Point Equalizer - all lines of load balancers and application delivery controllers.
To ensure a full range of network security measures, it’s better to supplement all this with the inclusion of FortiGate itself into the infrastructure; however, small and medium-sized enterprises can only be managed with the services of this solution in hardware or virtual execution.
So, what provides FortiGate in a section of functions similar with TMG? We will consider them one by one through the prism of replacing the TMG, and at the same time we will take a general look at the skills of FortiGate.
Firewall
Firewall - the beginning began filtering unwanted connections from the outside, from the Internet to the corporate network. At the same time, it is necessary to keep records, control and delimitation of user access from inside the network to external resources. Therefore, in addition to packet filtering, address and port translation, support for deep inspection of packets with stateful / Deep Packet Inspection, the FortiGate is primarily a comprehensive network protection platform, running the full FortiOS single operating system security, such as: antivirus, antispam, application control, intrusion prevention system, web filtering, data leakage prevention and others.
With all the wide range of functionality, the standard policy for web user access from the internal network to the Internet, created in the FortiGate web interface, will look like this:

Web proxy
One of the oldest and most used TMG features for providing users access to the Internet without additional authentication.
In FortiGate, there is an “Explicit web proxy” function for transmitting HTTP (HTTPS) and FTP sessions through a proxy, plus support for auto-configuration using a PAC file.
Also, thanks to the Single Sign-On (SSO) function, fully integrated in FortiGate, it is possible to interact with a domain controller (Active Directory, Novell eDirectory) and control the access of authenticated users, applying necessary rights and capabilities to certain domain groups.
In addition, anti-virus protection, intrusion prevention, web filtering and application control can be included in such security policies.

Web proxy is enabled on the required interface (s) ( “port1” in the upper figure) and by creating a permissive policy (in the figure below):


The introduction of Single Sign-On can be done in several ways:
1. Using a special agent program on a domain controller ( DC Agent )
DC Agent is a software component in the form of a separate user tracking service installed on a domain controller. It interacts with FortiGate not directly, but through a collector agent (Collector Agent).
Collector Agent is installed on any server or, again, on a domain controller. The agent receives information about user logins and exchanges it with FortiGate. The number of agents installed can be more than one for fault tolerance.

2. Poll Collector Agent
This method also provides for the installation of additional software in the form of a Collector Agent, but on the domain controller, the DC Agent service will not have to be installed. The Collector Agent can be installed anywhere on the network (preferably on one of the Windows servers) and then it can poll the domain controller about user authentication events (“logons”). Polling mechanisms are implemented using the Windows NetAPI or Security event log.

3. Survey directly with FortGate
Starting with FortiOS version 5, the logon polling mechanism from the domain controller was fully integrated into FortGate. At the same time, only the Security event log is used for polling, and the use method itself is positioned as for small network infrastructures, where there is no possibility to install the Collector Agent on the network perimeter.
However, at the same time, you should not forget that if FortGate saves you the trouble of installing software, it will take the load of storing the domain structure and polling user logons in your memory.
4. NTLM authentication
Using NTLM authentication requires an installed Collector Agent on the network perimeter to communicate with FortGate. When requesting a URL in a user's browser, FortGate will request its domain credentials (username / password), get it through a browser, check the Collector Agent for the user to belong to domain groups and provide access to resources according to its group security policy.

5. Terminal servers
Users who access corporate resources through Microsoft or Citrix terminal servers have one shared address or pool instead of their own IP address. For applying security policies to such users via SSO, Fortinet has another software component, the Terminal Server Agent (TS Agent), installed on the terminal server itself. He allocates a specified range of ports for each user and exchanges this information with the Collector Agent, which, in turn, knows about the user's belonging to domain groups, and which groups give what set of resources and which policy to apply - knows FortiGate. The agent looks like this:

On top of the description of the implementation of SSO, I would also like to note that the manufacturer seeks to improve the functionality even in the youngest UTM models. In confirmation of this, in 2012, the release of the radically reworked version of FortiOS 5 OS was announced, among the improvements of which was support for the Terminal Server Agent, and more correct operation of SSO as a whole, with its above-described abundance of application variations and auxiliary software.
Though believe, at least check, and taking the latest versions of the software: Collector Agent, DC Agent, TS Agent in combination with FortiGate on FortiOS version 5.0.4 and higher - everything will work like a clock. And if it will be interesting to comprehend the secrecy of SSO and dive into the details - we will “pisach ischo” about it, because This topic deserves a separate article.
Turning to the part of applying security policies, let's take a look at how it will look on FortiGate with successfully configured SSO software components:

The applicable rule for accessing a specific group or user is as follows:

More differentiated policies with many different domain groups provide more options for controlling user access to network resources.
OWA / SharePoint Publishing
The main aspects of publishing an Outlook Web Access or SharePoint Web resource are the following:
- Broadcast external IP-address;
- Exchange of certificates with users from the outside.

First we need to import the certificate, this is done like this:

In the desired menu, simply select your certificate and click OK.
Further, to configure reverse proxy, you need to configure load balancing. Create a virtual server for this:

For a virtual server, you need to determine the real server:

The final step is to create a security policy where we allow traffic from outside:

The incoming interface (Incoming Interface) in this case will be the external, source address (Source Address) will be “all”, and the destination address (Destination Address) will be the newly created virtual server. As a service, we skip HTTPS, because traffic exchange will occur only over HTTPS, and we don’t need more.
As with a regular proxy, it is possible to expand security features by including profiles in a policy:
- Antivirus protection;
- Intrusion Prevention Systems (IPS);
- Application Control (here we can limit or track down that, apart from the desired application, others are not used);
- URL filtering.
Inspecting SSL traffic
Another important feature when migrating from TMG is to inspect SSL traffic.
Turning on is as simple as other security features — a pre-configured profile in a policy.

Since the exchange of certificates is transparent to the end user within the network, you can use the standard embedded from the vendor, and if the internal server has its own self-signed certificate, you can simply enable “Allow invalid SSL Certificates”, because they will be perceived as incorrect, because Do not appear in the list of trusted Certificate Authority (CA).
In terms of publishing web resources on FortiGate, the inspection setting applies only to the published application and will not apply to other traffic, however, the SSL inspection function can also be used for more detailed control of SSL traffic for end users in corporate security policies.
Application control
In order to use the application control function, you must create an application “sensor”. This is the same profile, only - in profile :)
We look:

In our case, it is possible and necessary to select a specific application by switching the sensor type to “Specify Applications” and using the search method to find the desired application:

Intrusion Prevention System
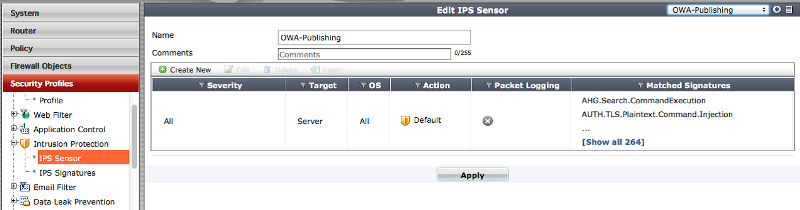
To be included in the security policy - again, a sensor for IPS is needed:

The only thing is that you cannot create a filter by application via the web interface, but this can be done from the CLI console by running such commands or copying them as a script:
config ips sensor edit "OWA-Publishing" config entries edit 2 set application IIS MS_Exchange set location server next end next end After creating a filter in the CLI, it can use any signatures exclusively for IIS and Exchange.
Another “implicit” function is to write your IPS-signature to block access when you try to enter the wrong password. To create one for OWA 2012, it will look like this:
config ips custom edit "MS.OWA.Login.Error" set comment '' set signature "F-SBID( --attack_id 3608; --name \"MS.OWA.Login.Error\"; --protocol tcp; --service http; --flow from_server,reversed; --pattern \"<div class=|22|signInError|22 20|role=|22|alert|22|>\"; --context body; --no_case; --pattern !\"<|2F|div>\"; --context body; --no_case; --within_abs 20; --rate 3,180;)" next end Here, the parameter "--rate 3,180;" symbolizes the number of false password entry errors (3) and the time of blocking the user by his IP address in seconds (180).
Malware / Spyware Protection
Antivirus profile looks like this:

As you can see, in addition to HTTP, there are other types of traffic (SMTP, POP3, IMAP, MAPI, FTP). We only need HTTP (S) for publishing.
So, put it all together. We create a policy for our reverse proxy with the publication, from the outside into the corporate network, or rather to the web application server, plus we include all configured profiles and sensors, including SSL inspection:

Lync Publish
Now that we have examined in detail the issue of publishing OWA / SharePoint with the full possible set of security features, it is worth noting that publishing Lync as a web application takes place on FortiGate in almost the same way (address translation, certificate exchange, protection with UTM functions) and same protocols, with the exception of the need to control SIP traffic as well:

In order to take into account this aspect, in addition to the features described, FortiGate has built-in support for SIP ALG (Application Level Gateway), an application-level gateway that provides detailed inspection and filtering of SIP traffic. Like many functions of FortiGate, SIP ALG deserved from the manufacturer of a separate manual - so its detailed consideration also deserves a separate article in the future.
Remote access of users and VPN networks
VPNs and secure encrypted access by remote users to corporate network resources or tunnels between separated sites of enterprises are already widely used for a lot of time, and TMG is not the only one here, providing us with this functionality. FortiGate is not a panacea either, but knowing that a solution for VPN can be done “out of the box” and that’s already, I'm sorry, moveton. Yes, and we made a reservation at the beginning that our solution is full-featured, so we will not cheat - but we will continue with the migration of all the functions of TMG.
So what do we have? We have L2TP / IPSec and IPsec VPN support for the so-called. "Site-to-site" connections and SSL-VPN for remote access from anywhere, which is quite suitable for "client-to-site".

For IPsec, several variations are available, a la static or “Dialup” -connections (having a static address on one side and dynamic from the remote end of the tunnel), Dynamic DNS. Tunnels are built between FortiGates and between PCs and FortiGate with the help of additional FortiClient software. There are many authentications (local user groups, local and remote host IDs, X.509 certificates, Active Directory credentials).
SSL is presented in two modes - web portal and tunnel. Web portals are designed for quick access to corporate resources from a web browser, which is especially important for thin clients and mobile devices. In this mode, FortiGate serves as a secure HTTP / HTTPS gateway, and authenticates users by giving them access to a web portal where HTTP / HTTPS, telnet, FTP, SMB / CIFS, VNC, RDP, SSH and other resources are available. Tunnel mode offers access to any application to the corporate network, but for this, FortiClient is installed or a separate part of it - the FortiClient SSL VPN application. FortiClient supports many operating systems: Windows, Mac OS X, Apple iOS and Android.
Another type of additional authorization for VPN is two-factor authentication using hardware FortiToken one-time password generator or FortiTokenMobile software for mobile devices.
In general, the VPN functionality is again quite wide and is described on a couple of hundred pages in all its glory, but at the same time, by practicing a little (straight arms) you can easily manage with numerous tunnels and web portals. Finally, we also note support for VPN tunnels with third-party (third-party) vendors, including the ability to connect to the Microsoft Windows Azure cloud service, which also uses IPSec VPN.
Finally, summing up all of the above, we can say with confidence that Fortinet, through its flagship FortiGate UTM device line, can provide with its purchase a very wide range of functionality for building an integrated network security system for enterprises of any size, while leaving a gap for their growth. You can not ignore the possibility of more narrowly enhancing protection using separate Fortinet equipment lines, such as: FortiWeb , FortiMail , FortiBalancer , FortiToken and FortiClient , which we mentioned as a transition from Microsoft TMG, as well as other product lines: FortiWifi and FortiAP for building secure wireless communications, centralized management of FortiManager , centralized reporting and analysis of FortiAnalyzer , protection from FortiDDoS DDoS attacks, FortiDB database protection, FortiCache web caching, FortiDNS caching DNS server, a separate authentication solution FortiAuthenticator invaders , work "in a gap" when FortiBridge network devices fail , FortiSwitch switching is not the end of the list ...
The issue of scalability needs to be addressed depending on the required functions previously used in TMG. And if you liked FortiGate alone or with another iron from Fortinet, then small businesses (up to about 100 users) should have paid attention to the FortiGate-90D model and lower, and to larger organizations - to FortiGate-100D and higher, t .to. support for some functions (as well as price) varies depending on the model.
In conclusion, I would like to emphasize on my own that whether or not FortiGate is worthy of becoming for you not only a full-featured, but also an imperceptible and problem-free transition from Microsoft TMG is up to you, of course. As for me - quite realizable.
Distribution of Fortinet solutions in Ukraine , Armenia , Georgia , Kazakhstan , Azerbaijan , Kyrgyzstan , Tajikistan , Turkmenistan , Uzbekistan , CIS countries .
Authorized Fortinet Training Courses
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/210582/
All Articles