Transparent file encryption on the local computer using CyberSafe Files Encryption
In the new version of CyberSafe, we have added the function of “transparent encryption” of files. In this article, I will discuss how this feature works, its main features, as well as the advantages over EFS, the standard Windows data encryption system.
Transparent encryption functions in CyberSafe are performed by a special file system driver that decrypts files when certain applications access them and encrypts them after working with files. Also, the driver encrypts all new files added to the protected folder.
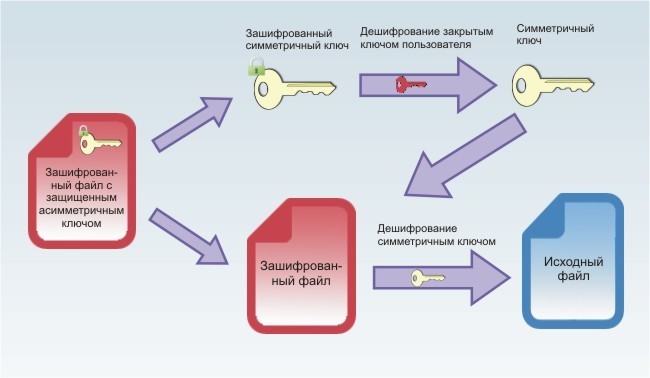
The encryption process is as follows:
')

When a user works with a file when the corresponding application is addressed to it, the file is automatically decrypted as follows:
The main advantage of “transparent encryption” is the convenience of working with protected files. Encryption / decryption processes occur automatically (transparently for the user) and do not require any additional actions from it.
Since CyberSafe uses alternate streams to store the encrypted symmetric key, transparent encryption using the program is possible only in the NTFS file system.
All files protected with transparent encryption are stored in folders.
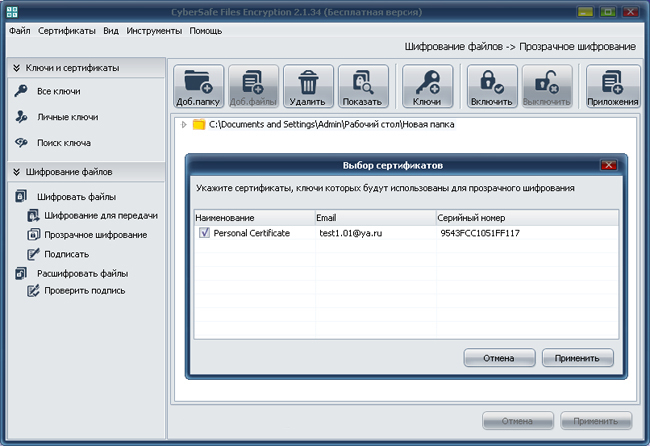
In order to create such a folder, open the program and select File Encryption> Transparent Encryption and add any empty previously created folder on the computer. In order to assign a pair of public / private key that will be used to encrypt and decrypt files, use the Keys button.
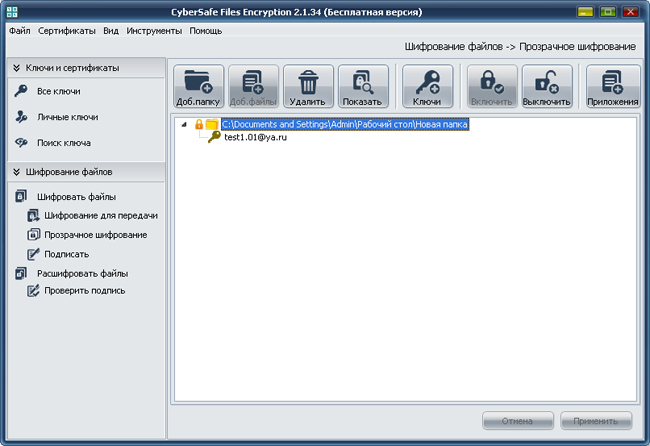
To work with existing files or to add new ones, the folder must be Enabled (you will need to enter the password to your private key).
All files added to the included folder are automatically encrypted. When working with files, the process of encrypting and decrypting them automatically (transparently).
When you finish working with the folder, it turns off. After that, access to encrypted files is closed for all applications: no one can view, edit or delete such files. This is also true even if CyberSafe is not functioning.
After encrypting files using CyberSafe on Windows, their cached copies may remain, so sometimes files in a protected folder may appear as unencrypted, but this is not the case. In fact, they are encrypted, but Windows shows their cached copies. Therefore, when using transparent encryption in the current version of CyberSafe 2.1.34, additional cache cleaning is required by restarting the computer. In the future, this deficiency will be eliminated.
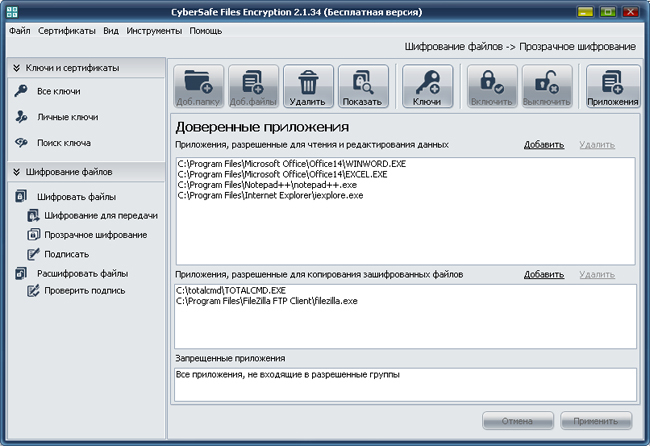
The Applications tab allows you to define trusted applications that will be allowed to work with encrypted files. By default, all applications are trusted. This means that no matter which application requests access to the files in the included folder, these files will be decrypted by the driver and available to the application for editing, copying, or deletion.
However, in order to limit access to confidential information of unwanted programs, you can make a list of trusted applications. In this case, only trusted applications will be able to access files in the encrypted folder, and all others will not. After compiling a trusted list, the rest of the applications automatically fall into the forbidden ones and do not have access to the files.
For example, in your protected folder you store only text documents. Then, it will be logical to allow access to these documents only to those applications that you use to work with them, for example Word, Excel, Notepad ++ or other text editors, and to forbid everyone else by defining them as prohibited.
Banned applications will not be able to access confidential information even while the trusted application is working with the file, that is, when the file is decrypted and vulnerable. Thus, we restrict access to confidential information for spyware, unwanted and malicious software.
Additionally, you can make a list of applications that will only be allowed to copy protected files.
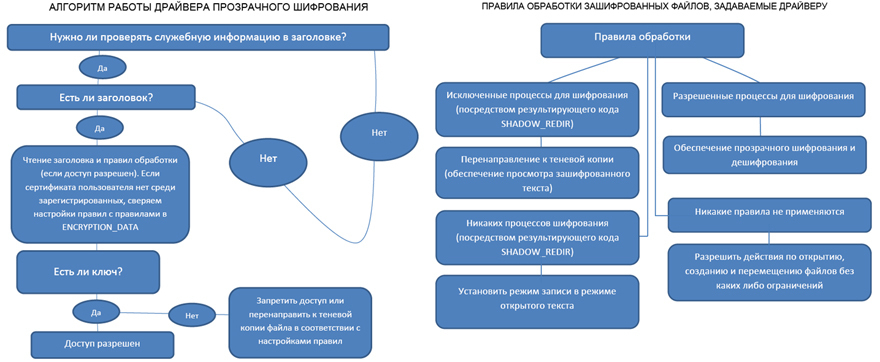
Functions for working with trusted and prohibited applications are assigned to the driver of transparent encryption. The driver works with protected files and allows or denies access to them to one or another application in accordance with the settings (rules) specified to it. Schematically, the algorithm of the driver is illustrated below:
By and large, the entire protection of encrypted files in EFS comes down to knowing the account password in the system. Any user who knows this password will be able to access all encrypted files. As you know, today password protection is not effective enough. If it is weak - you can pick it up, there are ways to track the password typed from the keyboard. In CyberSafe, we introduce a system of tokens (any flash drive can be used as a token), so even if an attacker somehow manages to get your password, the files encrypted using the program will still not be accessible to him.
As you know, EFS does not support encryption of files transmitted over the network, and to protect the information transmitted, the use of additional security protocols, such as IPsec or WebDAV, is required. In CyberSafe, there is no such flaw and the program can be effectively used to transparently encrypt folders in the corporate space, where there is a need to provide access to the same encrypted folder to several employees of the company. More information about encrypting network folders will be discussed in the next topic.
In EFS, any user who has access to your account can delete a folder with encrypted data. If you do not have a backup copy of the encrypted files, you will lose all the valuable information. In CyberSafe, after disabling the folder with encrypted files, it is additionally protected from being deleted from the computer’s hard disk by other users.
As mentioned above, the transparent file encryption functions in CyberSafe are performed by a special file system driver. While reading / writing files, it performs encryption / decryption operations, and does so at a very high speed.
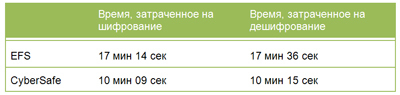
To compare the encryption speed in EFS and CyberSafe, I conducted a small test by encrypting the same folder in each of the programs and measuring the time spent on encrypting each of them. OS: Windows XP SP3. Folder weight: 1.6 GB, content: 26 files with extensions avi, jpg, png, bmp, pdf, docx, txt, cdr, psd, ppt. The results of the texts are shown in the table below:
In the event that spyware gets onto your computer, confidential information protected by EFS will be under threat of theft. In CyberSafe, this disadvantage is solved through the use of a system of trusted applications - only those programs that you define yourself will be able to access the protected folder and the confidential data stored in it.
How transparent encryption works
Transparent encryption functions in CyberSafe are performed by a special file system driver that decrypts files when certain applications access them and encrypts them after working with files. Also, the driver encrypts all new files added to the protected folder.
The encryption process is as follows:
')

- The source file is encrypted using the AES algorithm and a 256-bit symmetric key randomly generated by the program;
- The symmetric key is protected by RSA encryption using a user's public key up to 8192 bits in length and stored in an alternative NTFS data stream.
When a user works with a file when the corresponding application is addressed to it, the file is automatically decrypted as follows:
- using the user's private key, the symmetric key stored in the ADS is decrypted;
- using the symmetric key decrypts the source file.

The main advantage of “transparent encryption” is the convenience of working with protected files. Encryption / decryption processes occur automatically (transparently for the user) and do not require any additional actions from it.
Since CyberSafe uses alternate streams to store the encrypted symmetric key, transparent encryption using the program is possible only in the NTFS file system.
Work with encrypted folders in CyberSafe
All files protected with transparent encryption are stored in folders.
In order to create such a folder, open the program and select File Encryption> Transparent Encryption and add any empty previously created folder on the computer. In order to assign a pair of public / private key that will be used to encrypt and decrypt files, use the Keys button.

To work with existing files or to add new ones, the folder must be Enabled (you will need to enter the password to your private key).
All files added to the included folder are automatically encrypted. When working with files, the process of encrypting and decrypting them automatically (transparently).
When you finish working with the folder, it turns off. After that, access to encrypted files is closed for all applications: no one can view, edit or delete such files. This is also true even if CyberSafe is not functioning.
After encrypting files using CyberSafe on Windows, their cached copies may remain, so sometimes files in a protected folder may appear as unencrypted, but this is not the case. In fact, they are encrypted, but Windows shows their cached copies. Therefore, when using transparent encryption in the current version of CyberSafe 2.1.34, additional cache cleaning is required by restarting the computer. In the future, this deficiency will be eliminated.

The Applications tab allows you to define trusted applications that will be allowed to work with encrypted files. By default, all applications are trusted. This means that no matter which application requests access to the files in the included folder, these files will be decrypted by the driver and available to the application for editing, copying, or deletion.
However, in order to limit access to confidential information of unwanted programs, you can make a list of trusted applications. In this case, only trusted applications will be able to access files in the encrypted folder, and all others will not. After compiling a trusted list, the rest of the applications automatically fall into the forbidden ones and do not have access to the files.
For example, in your protected folder you store only text documents. Then, it will be logical to allow access to these documents only to those applications that you use to work with them, for example Word, Excel, Notepad ++ or other text editors, and to forbid everyone else by defining them as prohibited.
Banned applications will not be able to access confidential information even while the trusted application is working with the file, that is, when the file is decrypted and vulnerable. Thus, we restrict access to confidential information for spyware, unwanted and malicious software.
Additionally, you can make a list of applications that will only be allowed to copy protected files.

Functions for working with trusted and prohibited applications are assigned to the driver of transparent encryption. The driver works with protected files and allows or denies access to them to one or another application in accordance with the settings (rules) specified to it. Schematically, the algorithm of the driver is illustrated below:

Advantages over EFS
Using tokens as an extra measure of protection
By and large, the entire protection of encrypted files in EFS comes down to knowing the account password in the system. Any user who knows this password will be able to access all encrypted files. As you know, today password protection is not effective enough. If it is weak - you can pick it up, there are ways to track the password typed from the keyboard. In CyberSafe, we introduce a system of tokens (any flash drive can be used as a token), so even if an attacker somehow manages to get your password, the files encrypted using the program will still not be accessible to him.
“Transparent Encryption” Network Folders
As you know, EFS does not support encryption of files transmitted over the network, and to protect the information transmitted, the use of additional security protocols, such as IPsec or WebDAV, is required. In CyberSafe, there is no such flaw and the program can be effectively used to transparently encrypt folders in the corporate space, where there is a need to provide access to the same encrypted folder to several employees of the company. More information about encrypting network folders will be discussed in the next topic.
Protect folders from deletion
In EFS, any user who has access to your account can delete a folder with encrypted data. If you do not have a backup copy of the encrypted files, you will lose all the valuable information. In CyberSafe, after disabling the folder with encrypted files, it is additionally protected from being deleted from the computer’s hard disk by other users.
Work speed
As mentioned above, the transparent file encryption functions in CyberSafe are performed by a special file system driver. While reading / writing files, it performs encryption / decryption operations, and does so at a very high speed.
To compare the encryption speed in EFS and CyberSafe, I conducted a small test by encrypting the same folder in each of the programs and measuring the time spent on encrypting each of them. OS: Windows XP SP3. Folder weight: 1.6 GB, content: 26 files with extensions avi, jpg, png, bmp, pdf, docx, txt, cdr, psd, ppt. The results of the texts are shown in the table below:

The presence of a system of trusted applications
In the event that spyware gets onto your computer, confidential information protected by EFS will be under threat of theft. In CyberSafe, this disadvantage is solved through the use of a system of trusted applications - only those programs that you define yourself will be able to access the protected folder and the confidential data stored in it.
Source: https://habr.com/ru/post/210458/
All Articles