Research security sites on various CMS
Hi, Habr! Together with the SiteSecure service , we conducted a comprehensive study of the security of sites developed on various CMS systems, which resulted in quite interesting results.
According to the study, sites that use free CMS are, on average, four times more likely to become infected and are blacklisted than sites on commercial CMS.
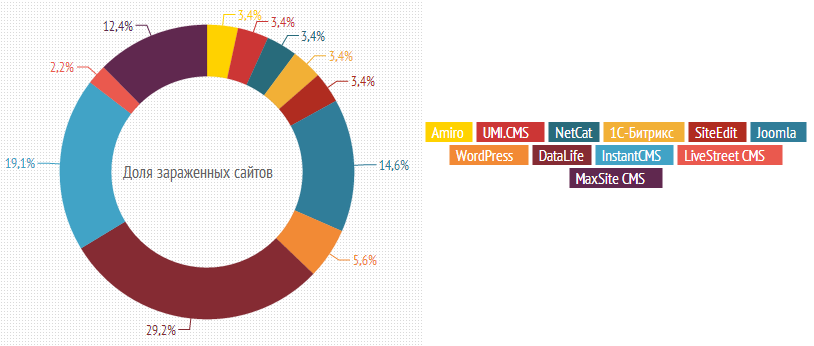
But the free CMS has a very different security situation. For example, every twentieth site on the Datalife Engine is blacklisted. At the same time, no infected site was found among the sites on CMS TYPO3. We attribute this to the fact that the TYPO3 development team pays considerable attention to improving the security of its CMS. In particular, only in September, 9 new vulnerabilities were published on the TYPO3 website, including one category of average danger in the CMS core and 8 critical vulnerabilities in third-party developers. Among the most common commercial CMS in RuNet, we could not single out a clear leader - they all had about the same number of sites with problems.
')
For the study were selected randomly 30,000 existing sites in the RU domain, created on different CMS. A selection of sites with the definition of CMS types was provided by iTrack .
The study was conducted in the period October 2013 - January 2014 by scanning the sites of the respondents with technical tools SiteSecure. The study analyzed the following site characteristics:
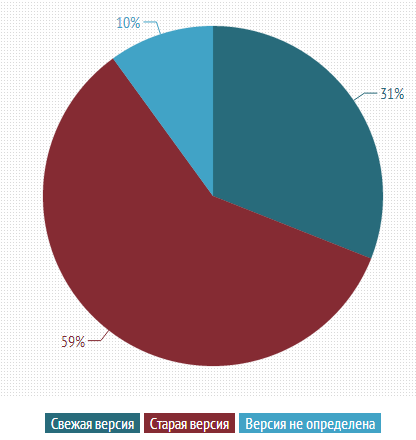
There is a noticeable correlation between the use of the most recent versions of CMS and the presence of problems on sites, both among commercial and among free CMS. Timely updated versions of CMS reduce the risk of problems on average by half. The most obvious advantage of switching to the latest versions is noticeable on the example of Joomla and WordPress.
The latest version of Joomla was used by only 3% of the sites on Joomla, and the latest version of WordPress was used by 15% of the websites. The share of problem sites on Joomla is three times higher than on WordPress. Obviously, timely updating of the CMS version increases the security of the site.
One of the hypotheses of the authors of the study is that websites on commercial CMS are more often developed by professional developers, who keep up to date with updated versions, which leads to a greater proportion of infected projects using free solutions.
The distribution of problem sites by type of web servers in general coincides with the popularity rating of web servers, and therefore we can say that the version of one or another web server is not a decisive factor in the security of a site.

Yandex blacklists sites more than Google. At the same time, the intersection of the Google and Yandex lists amounts to only 10% of the total number of blacklisted sites.

Conclusion: webmasters, seo-optimizer and other professionals who are responsible for website promotion should be sure to track the presence of the website in the blacklists of both search engines.
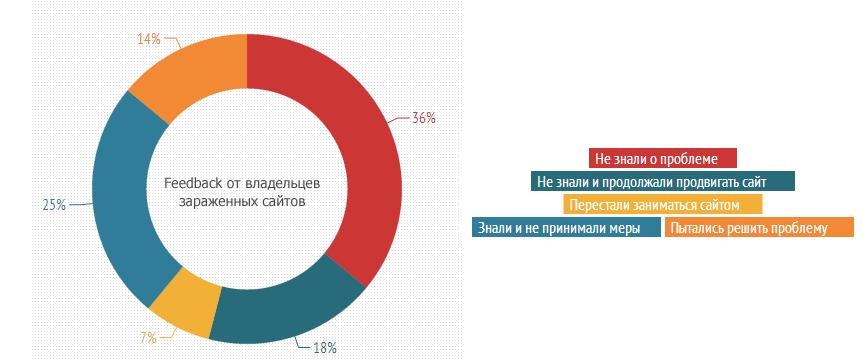
One of the key problems in the market is the low awareness of site owners about the emerging threats.
After the study was completed, an attempt was made to contact the owners of about 130 sites that were infected with viruses or were in the black lists of search engines. More than half of the owners, whose websites are actively used to promote a product or service, did not know that there were problems with their sites. At the same time, a third of them continued to spend money on the maintenance or promotion of the site.
In addition to the first part of the study, we checked all 30,000 commercial sites for blacklisting on the basis of spam from the IP address on which the site is located. We consider it important to tell about the scale of the problem that we discovered. Almost 15% of all checked sites are in one of the UCE PROTECT lists, that is, they are directly involved in spamming or are located next to sites that send spam. At the same time, 70% of sites are on the same subnet, and 28% are on the same IP address as the source of spam.
What this means for site owners. First of all, these are hidden problems that cannot be diagnosed without direct verification of blacklists. The result of these problems may be, depending on the configuration of the postal services of the site, the complete or partial inability to deliver outgoing mail, including sending letters to customers, as well as requests left by potential customers on the site.
For domain mail, dedicated ISP mail servers are more often used, and here the provider monitors the problem. But the sending of automated marketing letters and notifications, as well as customer requests, can be performed through other mechanisms from the same IP address where the site is located, and it often does not have the means to verify the success of the delivery. For 15% of sites tested by us, this may mean inefficient work or stopping marketing activity and receiving requests from potential customers, that is, direct losses to business.
- Owners of 4500 sites participating in the study are at risk of financial loss due to the problems on the site. This is almost every seventh site.
In conclusion, it should be said that website developers (web studios and agencies) often do not follow security issues, hoping for the reliability of the embedded tools in the CMS / framework. In the event of a problem of any kind, the client, however, blames just the developer. Therefore, the use of online services to monitor and protect sites like SiteSecure can close the problem area and avoid conflicts with the customer.
Comparison of security sites on free and commercial CMS
According to the study, sites that use free CMS are, on average, four times more likely to become infected and are blacklisted than sites on commercial CMS.

But the free CMS has a very different security situation. For example, every twentieth site on the Datalife Engine is blacklisted. At the same time, no infected site was found among the sites on CMS TYPO3. We attribute this to the fact that the TYPO3 development team pays considerable attention to improving the security of its CMS. In particular, only in September, 9 new vulnerabilities were published on the TYPO3 website, including one category of average danger in the CMS core and 8 critical vulnerabilities in third-party developers. Among the most common commercial CMS in RuNet, we could not single out a clear leader - they all had about the same number of sites with problems.
')
Research methodology
For the study were selected randomly 30,000 existing sites in the RU domain, created on different CMS. A selection of sites with the definition of CMS types was provided by iTrack .
The study was conducted in the period October 2013 - January 2014 by scanning the sites of the respondents with technical tools SiteSecure. The study analyzed the following site characteristics:
- CMS and web server version;
- The presence of viruses on the site;
- The presence of the site in the black lists of Google and Yandex;
- The presence of the site in the black lists Phishtank, DNSRBL, UCE PROTECT and others;
- Correlation between the CMS version and the presence of problems on the site.
Using updated CMS versions
There is a noticeable correlation between the use of the most recent versions of CMS and the presence of problems on sites, both among commercial and among free CMS. Timely updated versions of CMS reduce the risk of problems on average by half. The most obvious advantage of switching to the latest versions is noticeable on the example of Joomla and WordPress.
The latest version of Joomla was used by only 3% of the sites on Joomla, and the latest version of WordPress was used by 15% of the websites. The share of problem sites on Joomla is three times higher than on WordPress. Obviously, timely updating of the CMS version increases the security of the site.

One of the hypotheses of the authors of the study is that websites on commercial CMS are more often developed by professional developers, who keep up to date with updated versions, which leads to a greater proportion of infected projects using free solutions.
No impact of web server type
The distribution of problem sites by type of web servers in general coincides with the popularity rating of web servers, and therefore we can say that the version of one or another web server is not a decisive factor in the security of a site.

Comparison of black lists of search engines
Yandex blacklists sites more than Google. At the same time, the intersection of the Google and Yandex lists amounts to only 10% of the total number of blacklisted sites.

Conclusion: webmasters, seo-optimizer and other professionals who are responsible for website promotion should be sure to track the presence of the website in the blacklists of both search engines.
Awareness of site owners of problems
One of the key problems in the market is the low awareness of site owners about the emerging threats.
After the study was completed, an attempt was made to contact the owners of about 130 sites that were infected with viruses or were in the black lists of search engines. More than half of the owners, whose websites are actively used to promote a product or service, did not know that there were problems with their sites. At the same time, a third of them continued to spend money on the maintenance or promotion of the site.

Iceberg Underwater
In addition to the first part of the study, we checked all 30,000 commercial sites for blacklisting on the basis of spam from the IP address on which the site is located. We consider it important to tell about the scale of the problem that we discovered. Almost 15% of all checked sites are in one of the UCE PROTECT lists, that is, they are directly involved in spamming or are located next to sites that send spam. At the same time, 70% of sites are on the same subnet, and 28% are on the same IP address as the source of spam.
What this means for site owners. First of all, these are hidden problems that cannot be diagnosed without direct verification of blacklists. The result of these problems may be, depending on the configuration of the postal services of the site, the complete or partial inability to deliver outgoing mail, including sending letters to customers, as well as requests left by potential customers on the site.
For domain mail, dedicated ISP mail servers are more often used, and here the provider monitors the problem. But the sending of automated marketing letters and notifications, as well as customer requests, can be performed through other mechanisms from the same IP address where the site is located, and it often does not have the means to verify the success of the delivery. For 15% of sites tested by us, this may mean inefficient work or stopping marketing activity and receiving requests from potential customers, that is, direct losses to business.
- Owners of 4500 sites participating in the study are at risk of financial loss due to the problems on the site. This is almost every seventh site.
In conclusion, it should be said that website developers (web studios and agencies) often do not follow security issues, hoping for the reliability of the embedded tools in the CMS / framework. In the event of a problem of any kind, the client, however, blames just the developer. Therefore, the use of online services to monitor and protect sites like SiteSecure can close the problem area and avoid conflicts with the customer.
Source: https://habr.com/ru/post/209950/
All Articles