NSA Spy Gadgets
 Among the documents published by Edward Snowden, a former employee of the CIA and the US National Security Agency, materials were found describing some of the details of the espionage technology used by the NSA. The list of software and hardware is designed in the form of a small catalog. A total of forty-eight pages are marked with “Secret” and “Top Secret”, with a brief description of this or that technology for surveillance. This list is not exhaustive. Presented techniques associated with obtaining covert access to computing and networks, as well as methods and devices for electronic intelligence related to mobile communications and equipment for surveillance. In this article I will talk about these methods of espionage, then there will be four dozen slides (carefully, traffic).
Among the documents published by Edward Snowden, a former employee of the CIA and the US National Security Agency, materials were found describing some of the details of the espionage technology used by the NSA. The list of software and hardware is designed in the form of a small catalog. A total of forty-eight pages are marked with “Secret” and “Top Secret”, with a brief description of this or that technology for surveillance. This list is not exhaustive. Presented techniques associated with obtaining covert access to computing and networks, as well as methods and devices for electronic intelligence related to mobile communications and equipment for surveillance. In this article I will talk about these methods of espionage, then there will be four dozen slides (carefully, traffic).The "originals" of documents describing spy techniques are hidden under spoilers. The names of the technologies are indicated in capital letters, but not all of the mentioned technologies are described in the slide texts. Hardware bookmark is a hidden technical device, a kind of bug, which allows you to access the target or information about it. The program bookmark refers to hidden programs that allow access to the target programmatically, as, for example, with the help of Trojan horses and backdoors.
Computers
GINSU is a technique that allows you to restore a software tab called KONGUR on target systems with a hardware tab BULLDOZZER on a PCI bus. For example, in the case of updating or reinstalling the operating system on the target computer. These technologies are designed to obtain remote access to a computer running Windows from 9x to Vista.
Hidden text

IRATEMONK allows you to ensure the presence of surveillance software on desktop and laptop computers using a bookmark in the firmware of the hard disk, which allows you to get the opportunity to execute your code by replacing the MBR. The method works on various drives Western Digital, Seagate, Maxtor and Samsung. File systems support FAT, NTFS, EXT3 and UFS. RAID systems are not supported. After implementation, IRATEMONK will launch its functional part each time the target computer is turned on.
Hidden text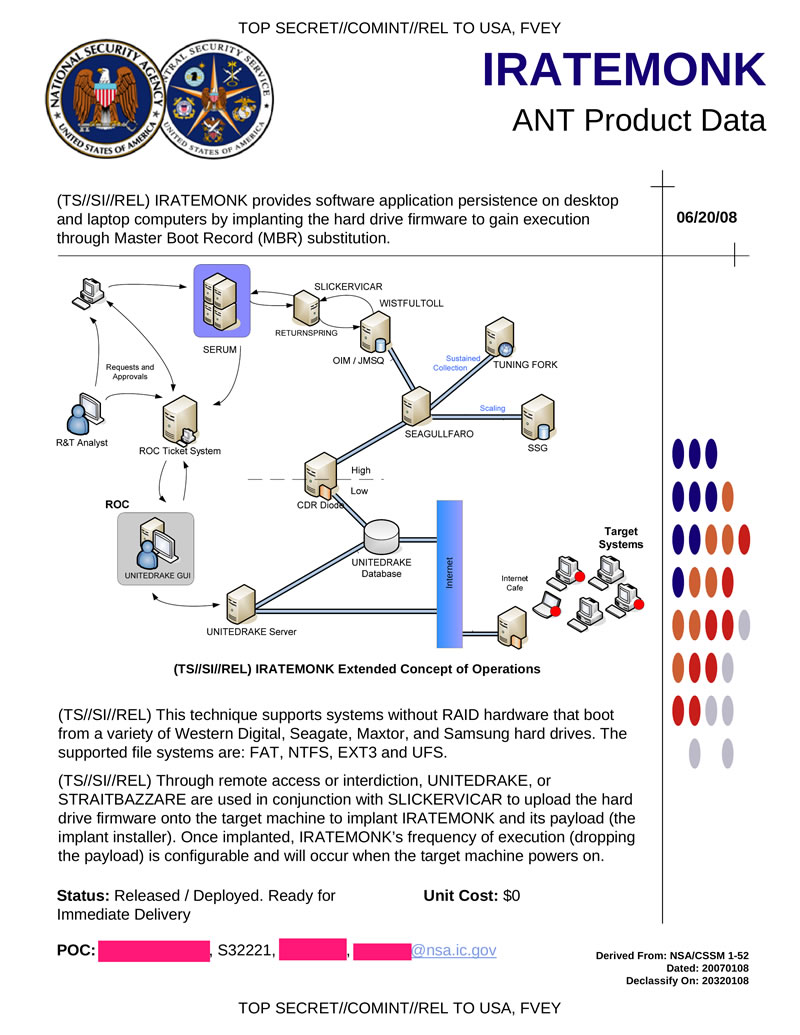

SWAP allows you to ensure the presence of espionage software by using the motherboard BIOS and the HPA hard disk area by executing the code before the operating system starts. This tab allows you to remotely access various operating systems (Windows, FreeBSD, Linux, Solaris) with different file systems (FAT32, NTFS, EXT2, EXT3, UFS 1.0). Two utilities are used for the installation: ARKSTREAM flashing the BIOS; TWISTEDKILT writes the SWAP disk area and its functional part to the HPA.
Hidden text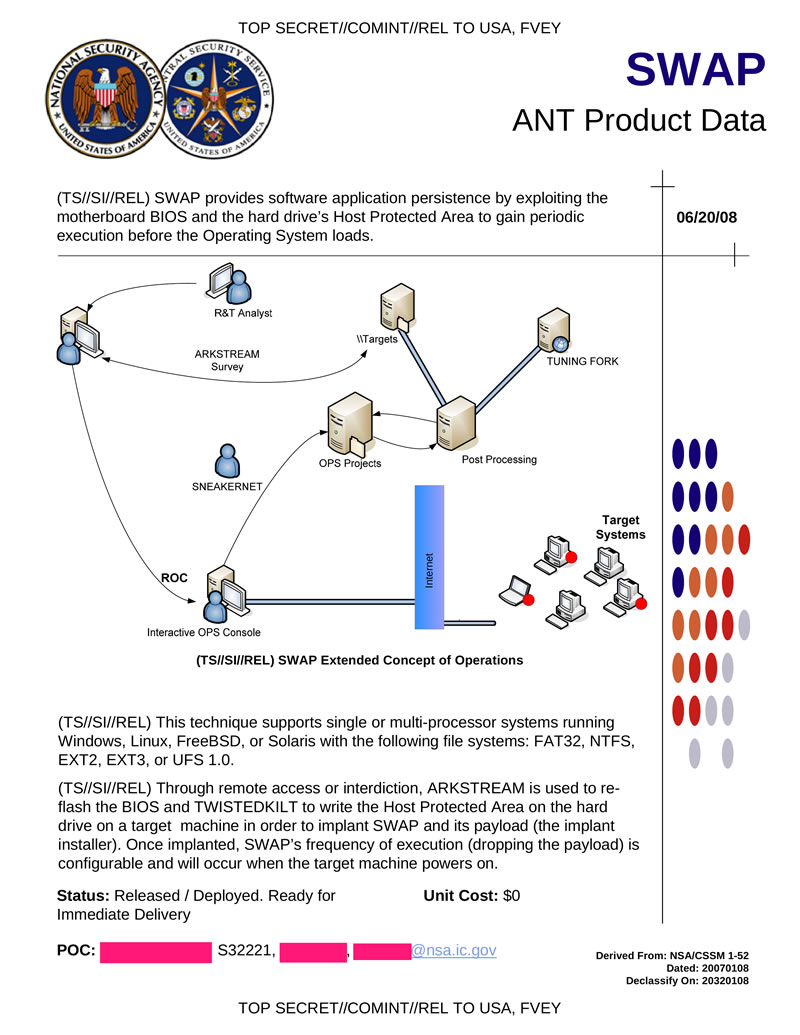

WISTFULTOLL is a plug-in to the UNITEDRAKE and STRAITBIZZARE programs to collect information on the target system, it uses WMI calls and registry entries. Work as an independent program is possible. If you have physical access to the system, it can reset the data received during the analysis to a USB drive.
Hidden text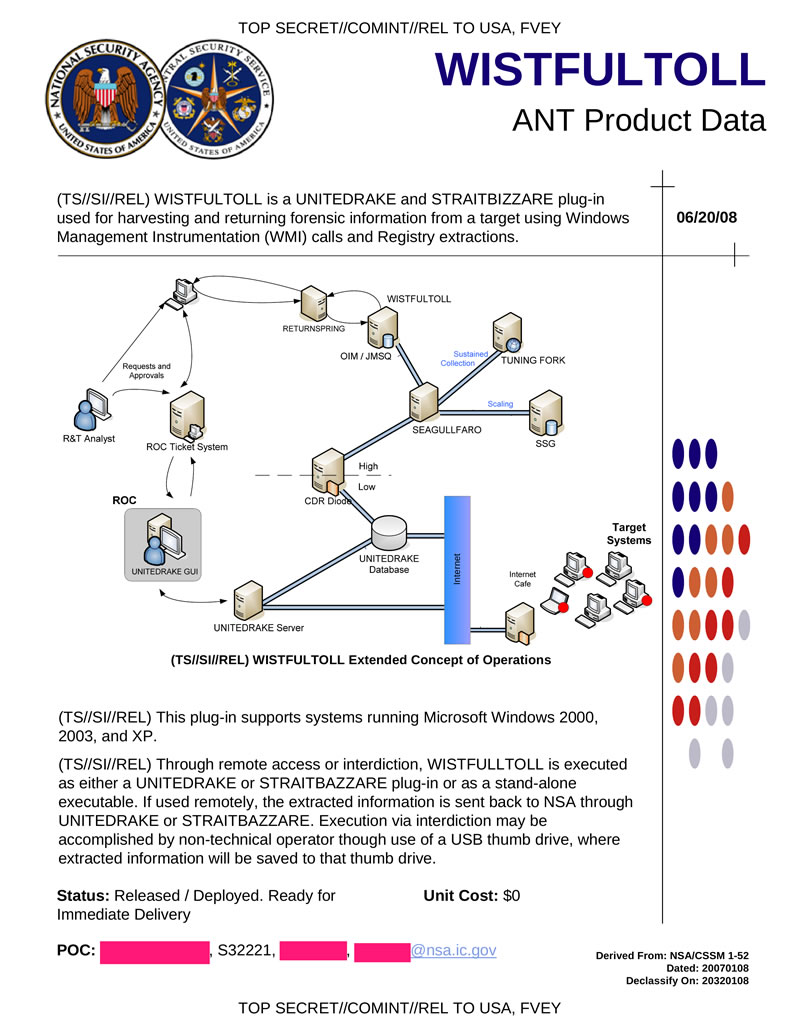

HOWLERMONKEY is a radio transmitter of small and medium radius. It is a special radio module for other hardware bookmarks. Used to retrieve data from bookmarks and provide remote access to them.

Hidden text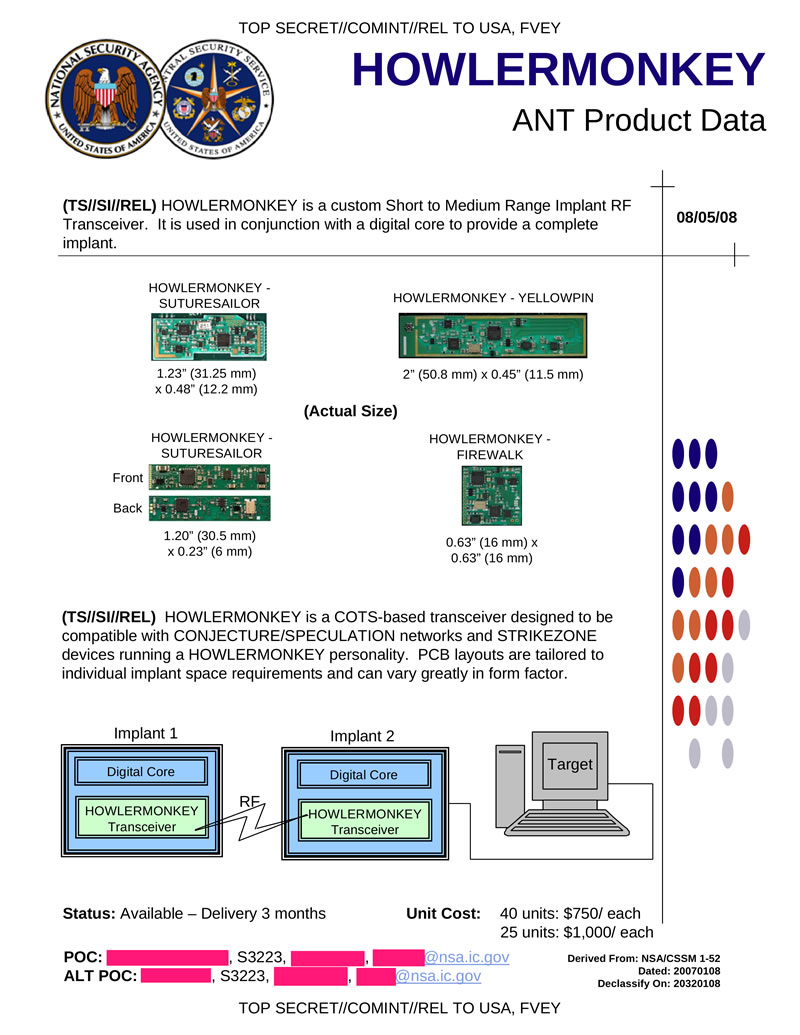

JUNIORMINT miniature hardware tab based on ARM-system, which can be configured for various tasks. For example, such a system may be part of other espionage devices. It has the following characteristics: ARM9 400MHz processor, 32MB flash, 64MB SDRAM, Vertex4 / 5 FPGA equipped with 128MB DDR2.
Hidden text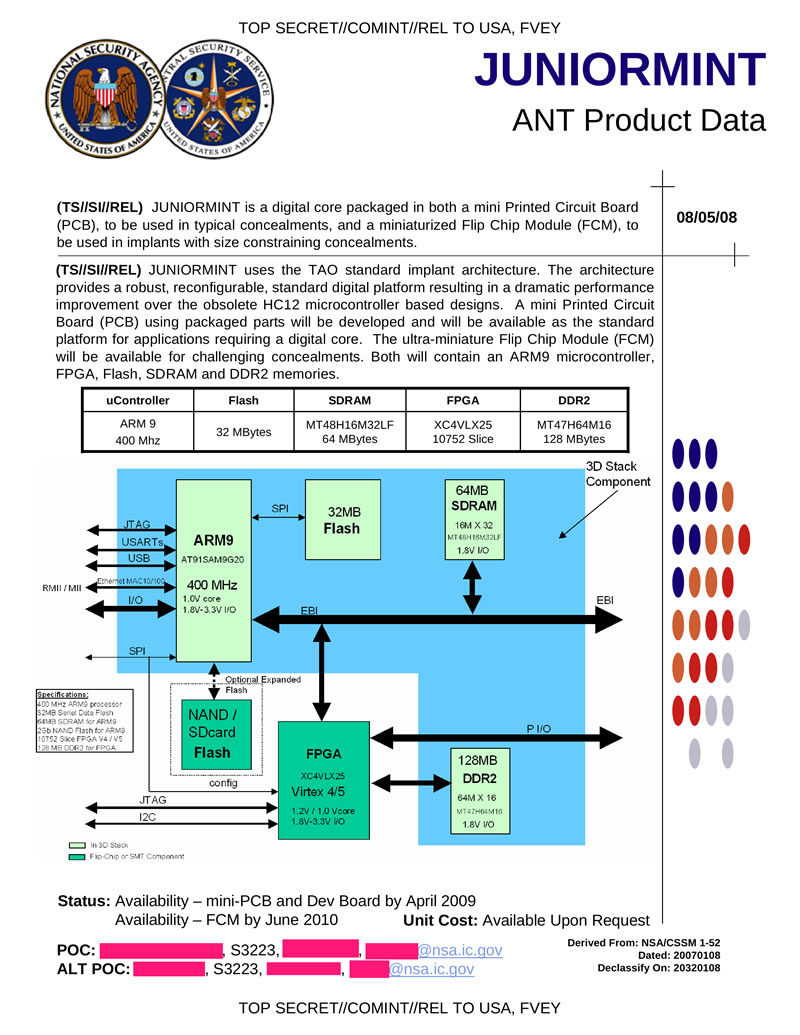

MAESTRO-II is a miniature hardware tab based on an ARM system, the size of a one-cent coin. The characteristics are rather modest: ARM7 66MHz processor, 8MB RAM, 4MB flash.
Hidden text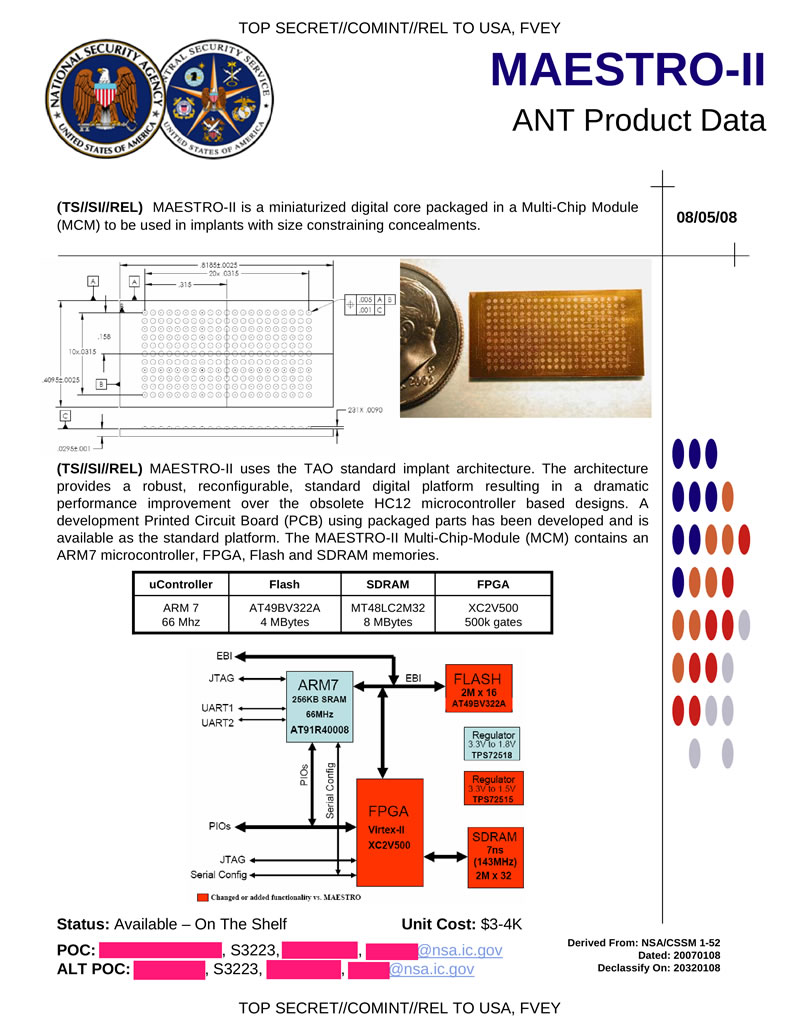

SOMBERKNAVE is a software tab running under Windows XP that provides remote access to the target computer. Uses unused Wi-Fi adapters when the user uses the SOMBERKNAVE adapter to stop data transfer.
Hidden text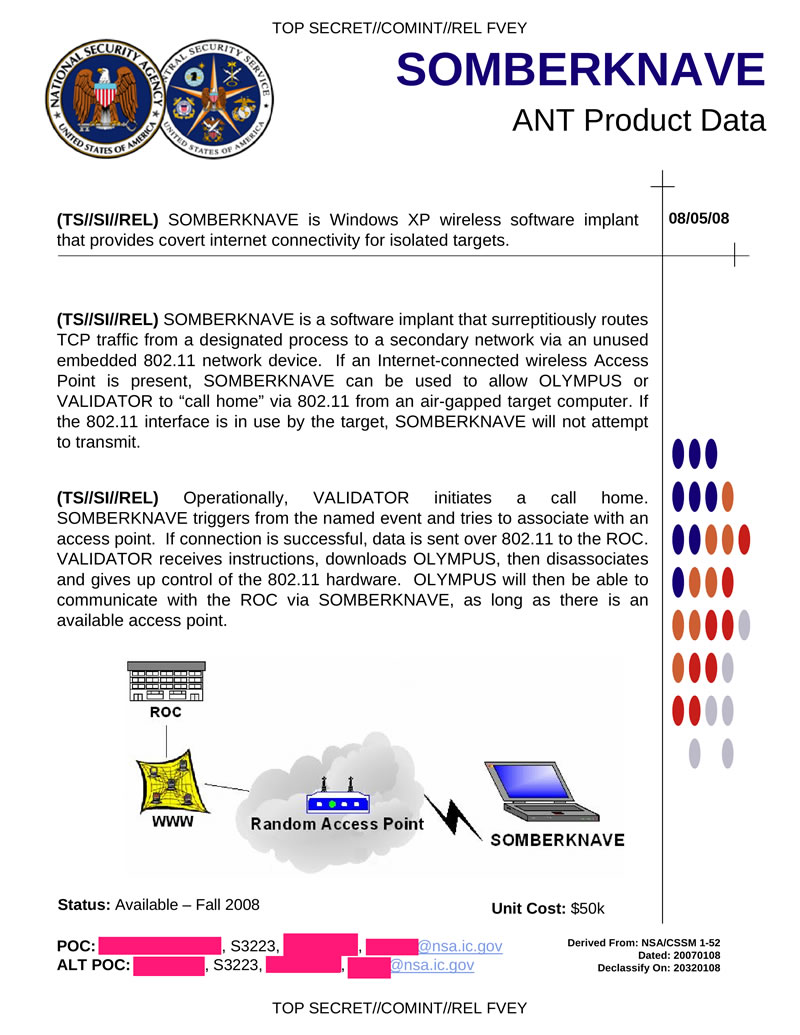

TRINITY is a miniature hardware tab based on an ARM system, the size of a one-cent coin. It has the following characteristics: ARM9 180MHz processor, 96MB RAM, 4MB flash. Used as part of other devices.
Hidden text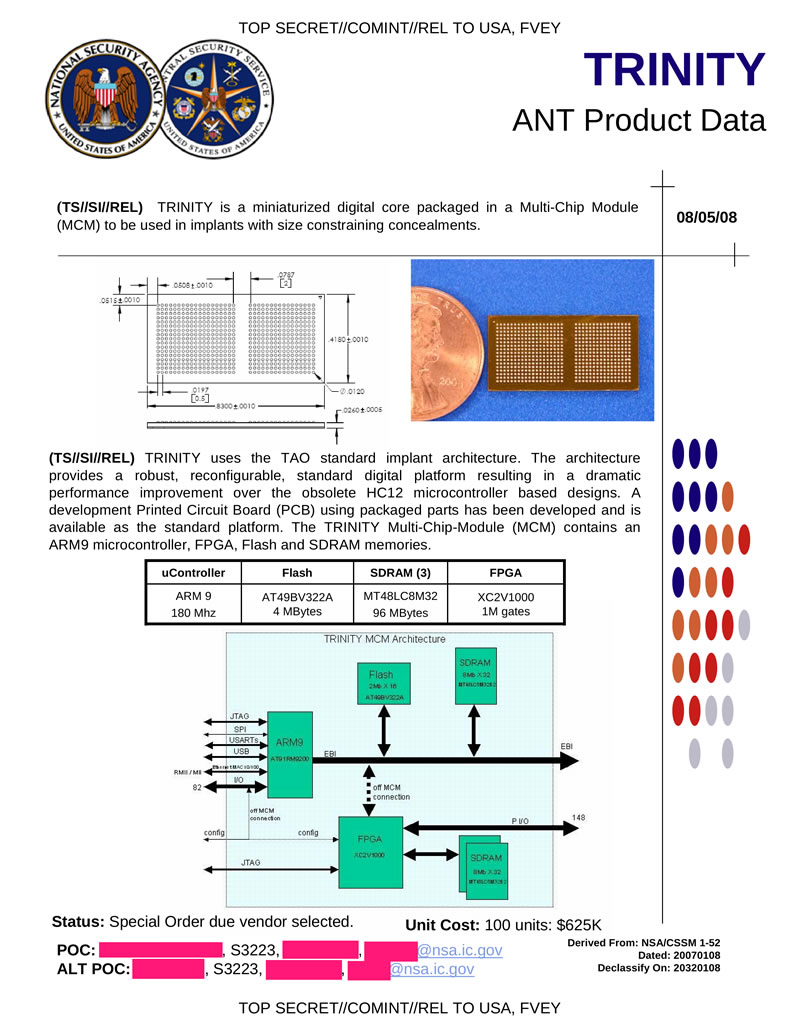

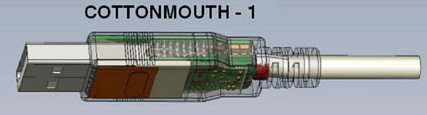
COTTONMOUTH-I hardware tab on USB, providing a wireless bridge to the target network, as well as loading exploits on the target system. It can create a hidden communication channel for transmitting commands and data between hardware and software tabs. With the help of a built-in radio transmitter, it can interact with other COMTONMOUTH. The basis is TRINITY element base, HOWLERMONKEY is used as a radio transmitter. There is a version called MOCCASIN, which is a bookmark in the USB keyboard connector.

Hidden text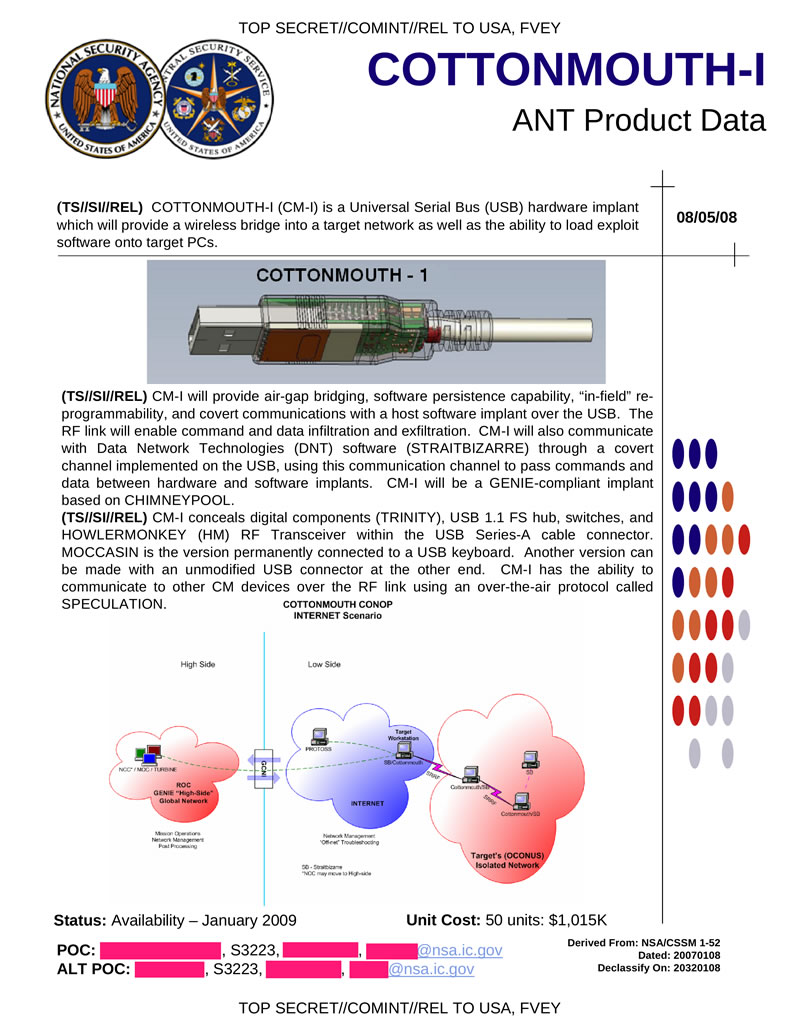

COTTONMOUTH-II USB hardware tab provides a hidden channel to access the target network. This tab is designed to work on the computer chassis and is a dual-port USB-connector to the board. It can create a hidden communication channel for transmitting commands and data between hardware and software tabs.

Hidden text

COTTONMOUTH-III hardware bookmark in USB providing a wireless bridge to the target network, as well as loading exploits on the target system. The basis is TRINITY element base, HOWLERMONKEY is used as a radio transmitter. It is a block of connectors (RJ45 and two USB) installed on the chassis, can interact with other COTTONMOUTH installed on the same chassis.

Hidden text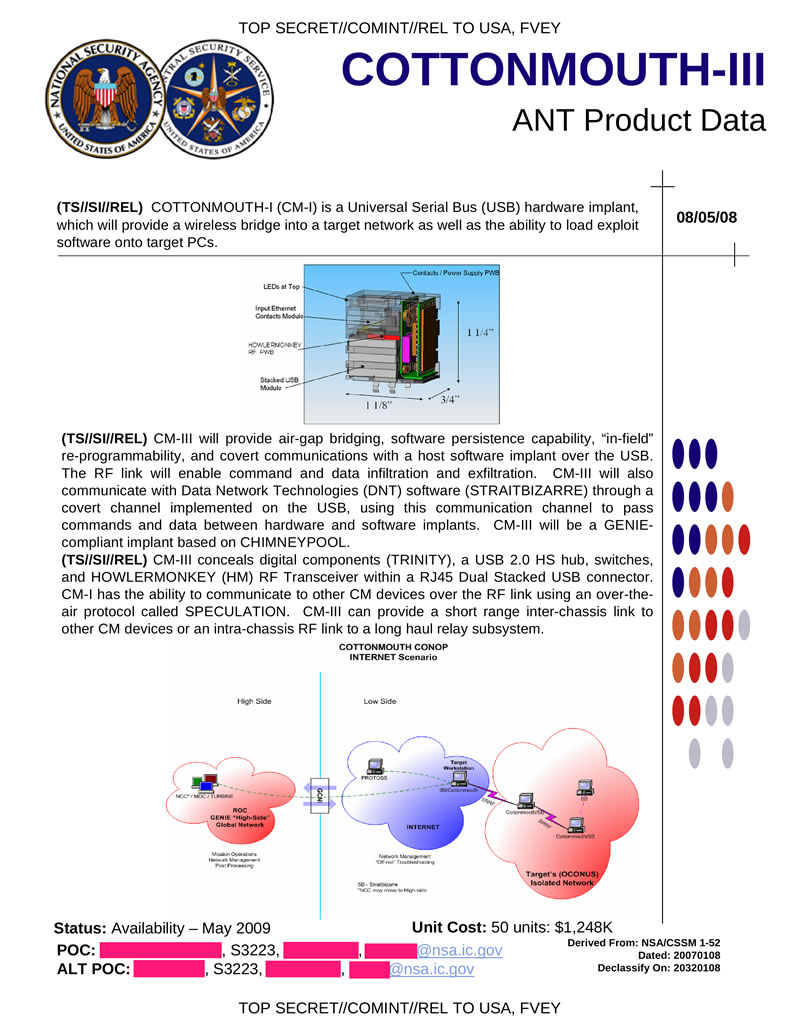

FIREWALK is a hardware-based network tab that can passively collect Gigabit Ethernet traffic and also make active Ethernet injection packets to the target network. Allows you to create a VPN tunnel between the target network and the center. It is possible to establish wireless communication with other HOWLERMONKEY-compatible devices. The execution of this tab is similar to COTTONMOUTH-III, the same block of connectors (RJ45 and two USB) on the chassis. The basis is TRINITY element base, HOWLERMONKEY is used as a radio transmitter.
Hidden text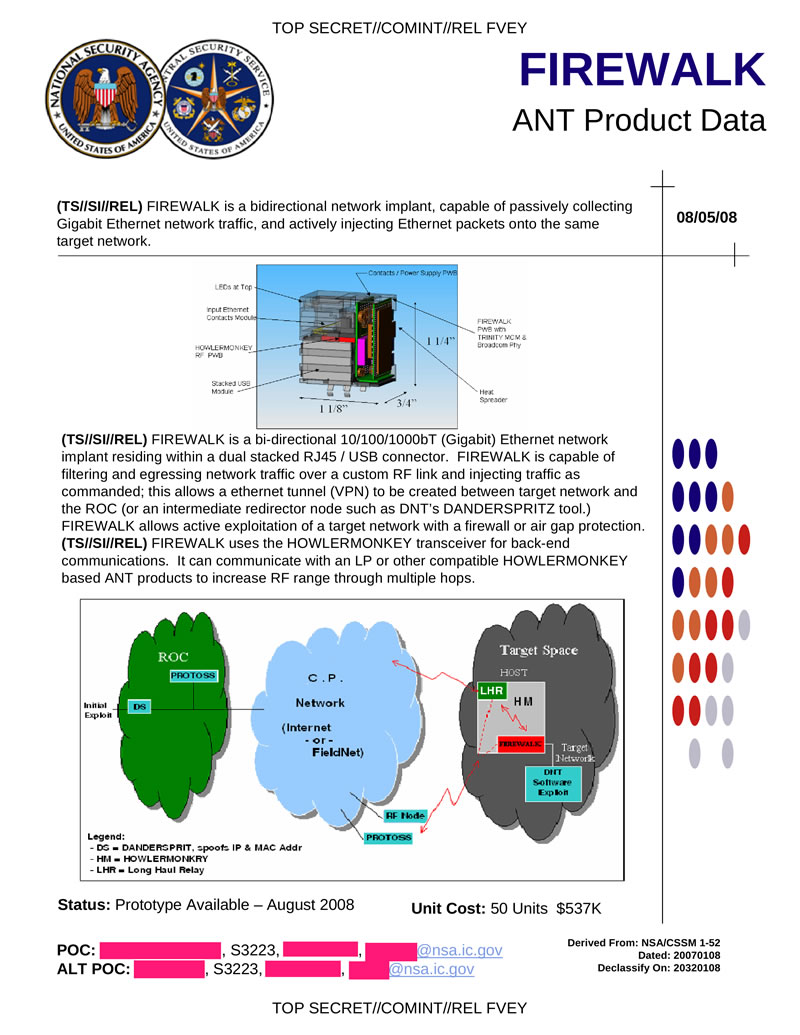

SURLYSPAWN is a hardware tab (keylogger) that allows receiving data from a target over a radio channel (keyboard, low-speed digital devices). The data is transmitted in the reflected signal; to activate, the bookmark is irradiated with a radio signal from a specialized transmitter. The keylogger is compatible with USB and PS / 2 keyboards, in the future we plan to add compatibility with laptop keyboards.
Hidden text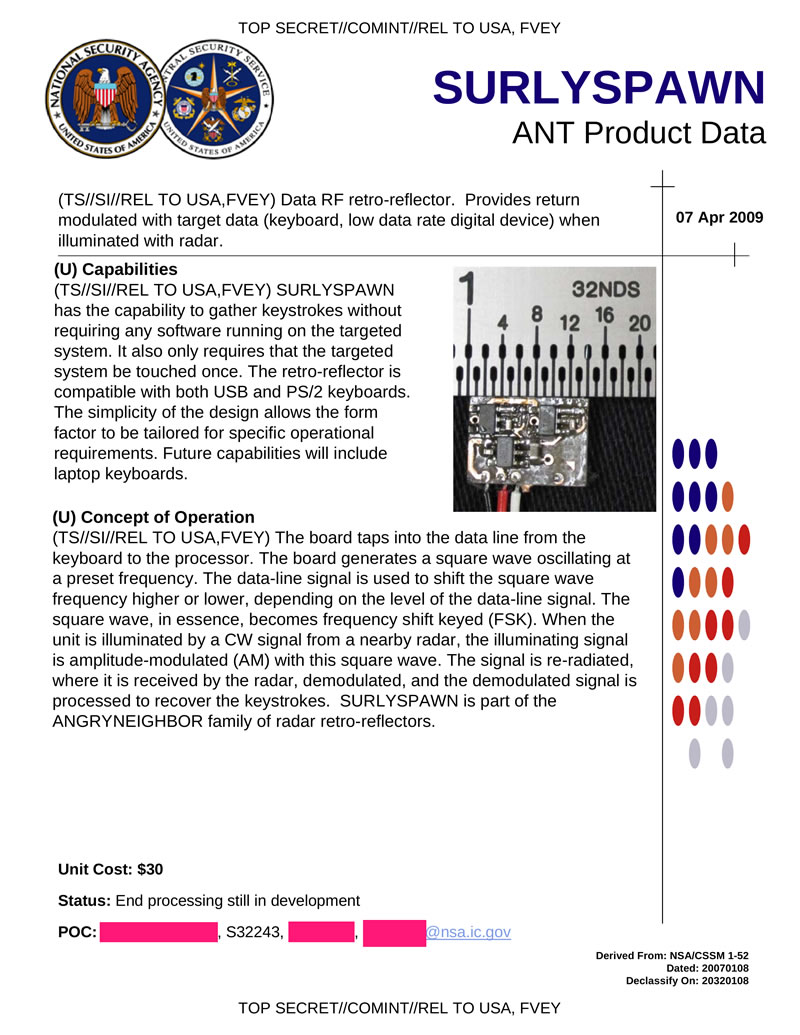

RAGEMASTER - hardware tab allows you to intercept the signal from the VGA monitor. The bookmark is hidden in a normal VGA cable connecting the video card and the monitor, installed, as a rule, in ferrite on the video cable. Implemented capture signal from the red color channel. It is a passive reflector, i.e. activated when irradiated with a radio signal from a specialized emitter.

Hidden text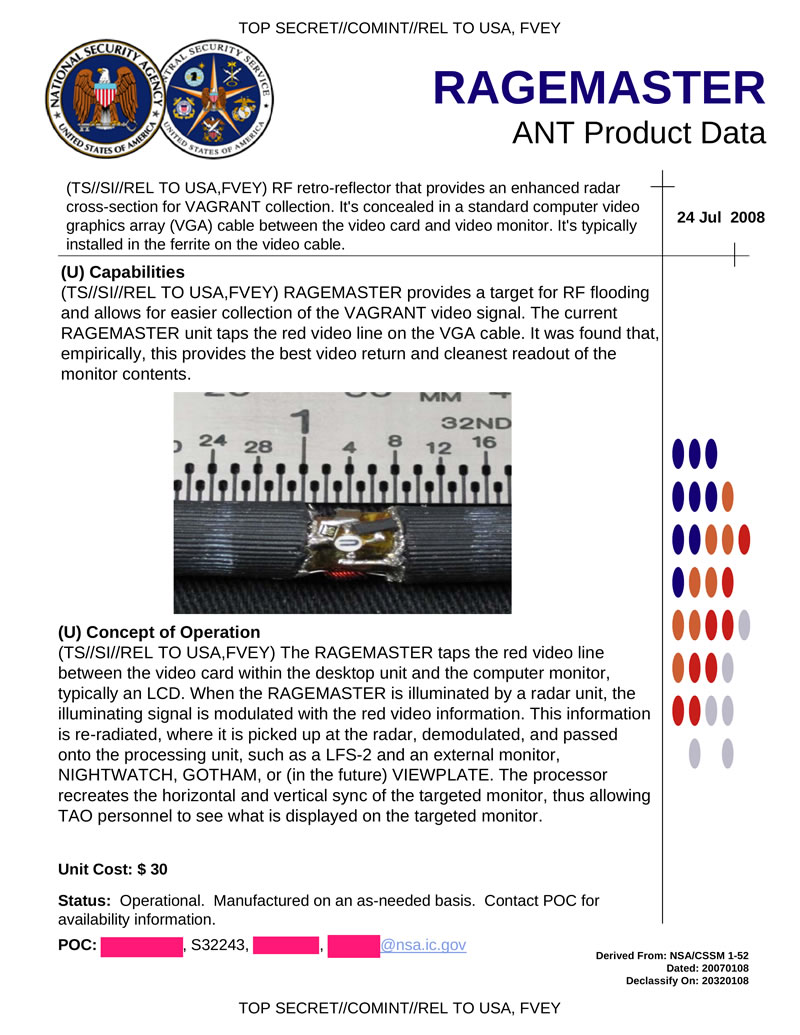

Wi-Fi networks
NIGHTSTAND is a mobile complex for carrying out active attacks on Wi-Fi networks, the targets are machines running Windows (from Win2k to WinXP SP2). Usually used in operations in which access to the target is impossible. The complex is implemented on the basis of a laptop running Linux and radio equipment. Together with external amplifiers and antennas, the range can reach 13 km.
Hidden text

SPARROW II is an embedded Linux computer system. This is a fully functional system for collecting data on wireless networks. To expand its functionality, it has four built-in Mini PCI slots that allow you to connect a GPS module and additional wireless network cards.
Hidden text

Servers
IRONCHEF provides access to target systems using the motherboard BIOS and using the SMM mode to communicate with a hardware tab that provides two-way radio communication. Apparently, this tab should be installed on the chassis of the system, like COTTONMOUTH-II. HP Proliant 380DL G5 servers are vulnerable to this technique.
Hidden text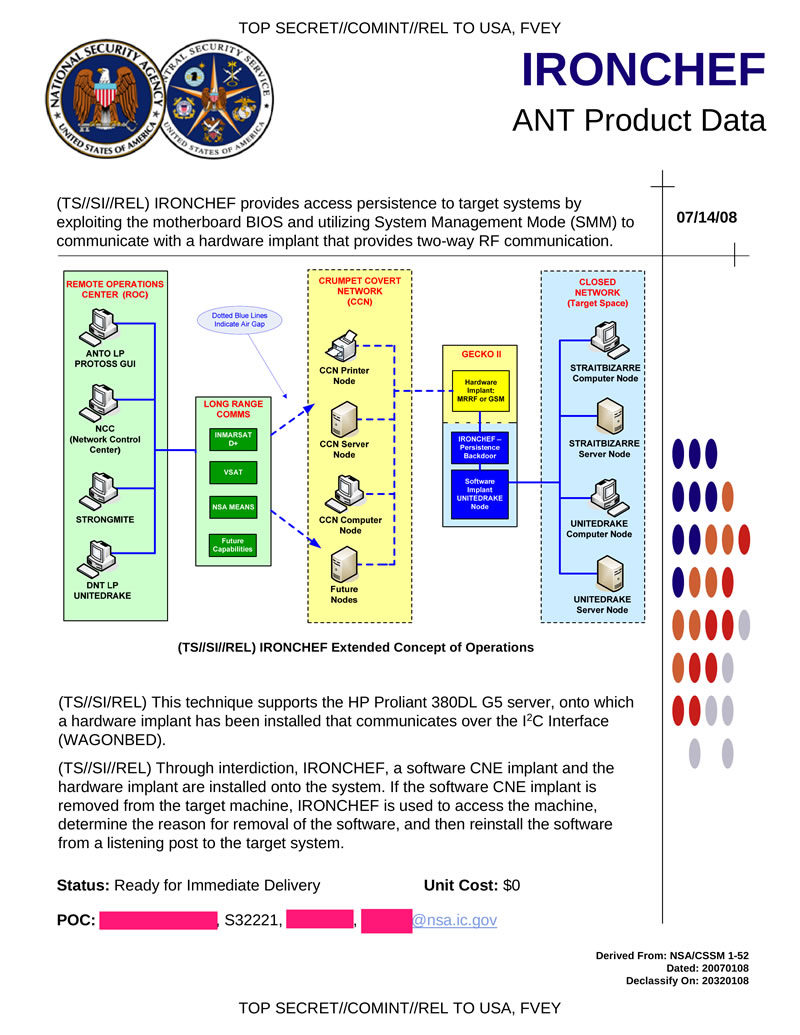

DEITYBOUNCE provides programmatic access to Dell PowerEdge servers using the motherboard BIOS and using SMM mode to enable it to run before the system boots. Installation can be done using ARKSTREAM, or using a USB flash. After installation will be performed every time you turn on the system. The targets can be Dell PowerEdge 1850/2850/1950/2950 with BIOS versions A02, A05, A06, 1.1.0, 1.2.0 or 1.3.7.
Hidden text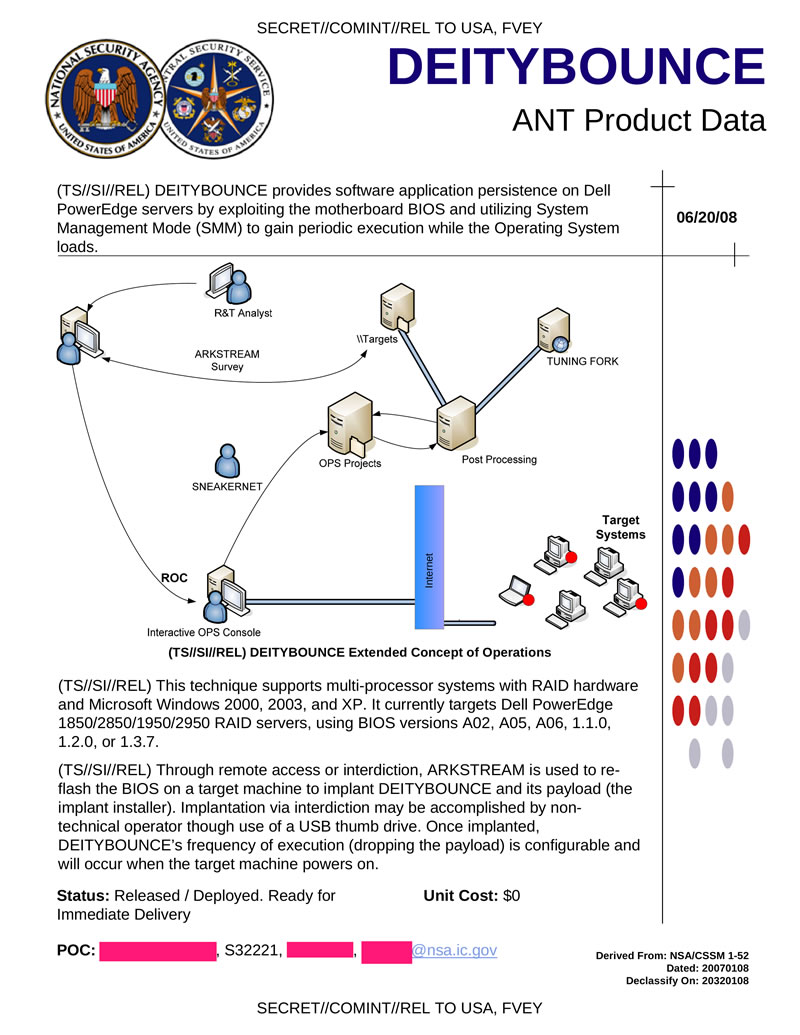

network hardware
JETPLOW is a tab for the Cisco PIX and ASA (Adaptive Security Appliance) firewall firmware. Saves the program bookmark BANANAGLEE and contains a backdoor. JETPLOW is able to work on the Cisco PIX 500 Series Firewalls and ASA (5505, 5510, 5520, 5540, 5550)
Hidden text

HALLUXWATER is a backdoor installed as an update to the bootloader in Huawei Eudemon firewalls. When the target is restarted, the bookmark installer finds the necessary points for the patch and backdoor in the incoming packet processing subroutine. This backdoor is saved when updating the operating system and automatic updates of the bootloader. HALLUXWATER can run on the Huawei Eudemon 200, 500 and 1000 series firewalls.
Hidden text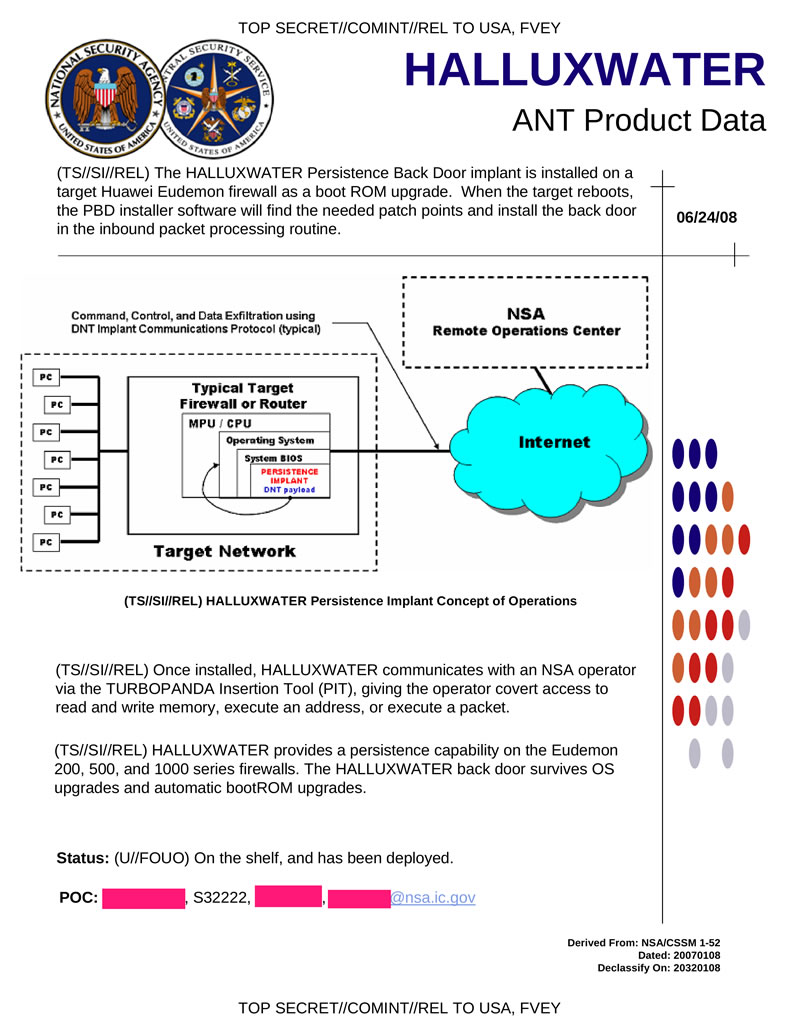

FEEDTROUGH is a technique for installing two software tabs BANANAGLEE and ZESTYLEAK against Juniper Netscreen firewalls. The following Juniper models are endangered: ns5xt, ns25, ns50, ns200, ns500 and ISG 1000. The method is processed when the firewall starts, if the operating system is in the database, bookmarks are set, otherwise the device is loaded in normal mode. FEEDTROUGH is saved when the firewall operating system is updated.
Hidden text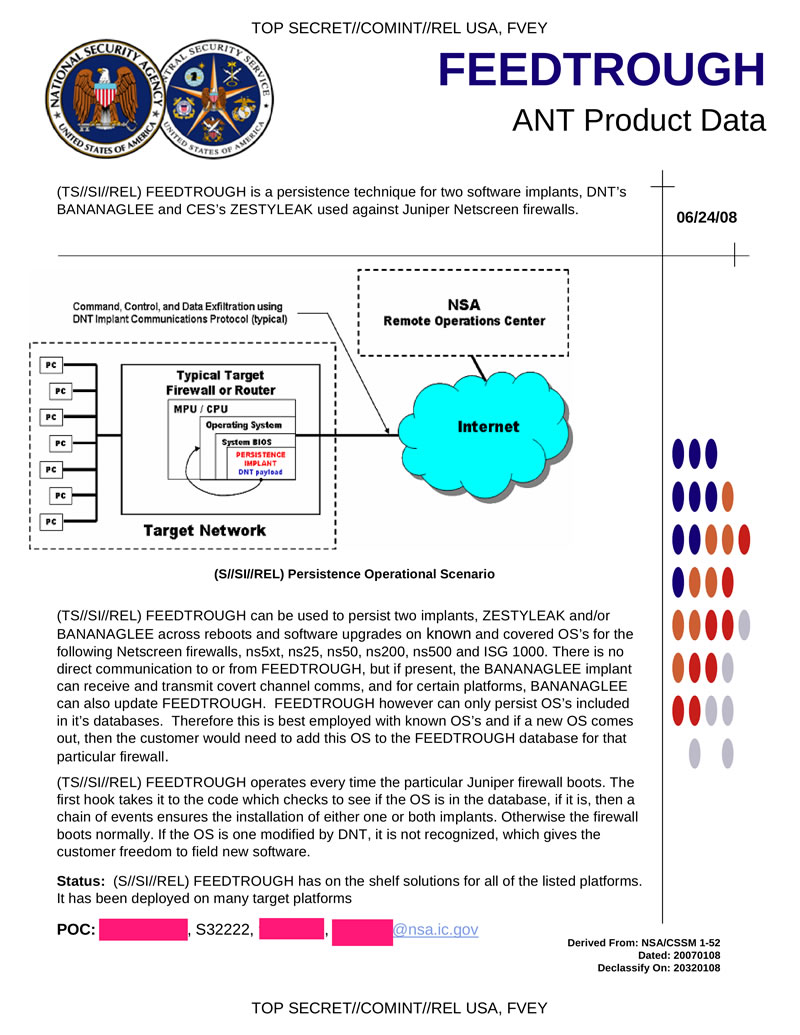

GOURMETTROUGH bookmark for some Juniper models, has custom settings. It hides the BANANAGLEE tab and allows you to save it after rebooting or updating the OS.
Hidden text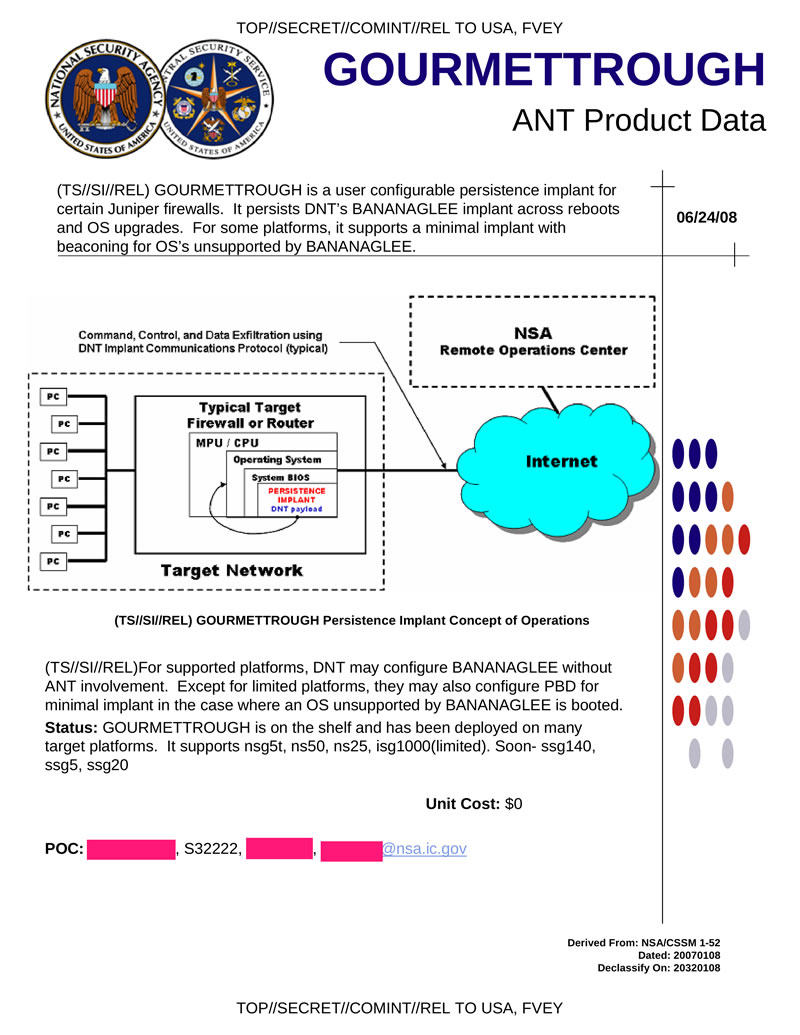

SOUFFLETROUGH tab for Juniper SSG 500 and SSG 300 series BIOS firewalls. It hides the BANANAGLEE tab, in case the device does not support adding BANANAGLEE, it opens the backdoor. Remote update and installation of SOUFFLETROUGH are possible.
Hidden text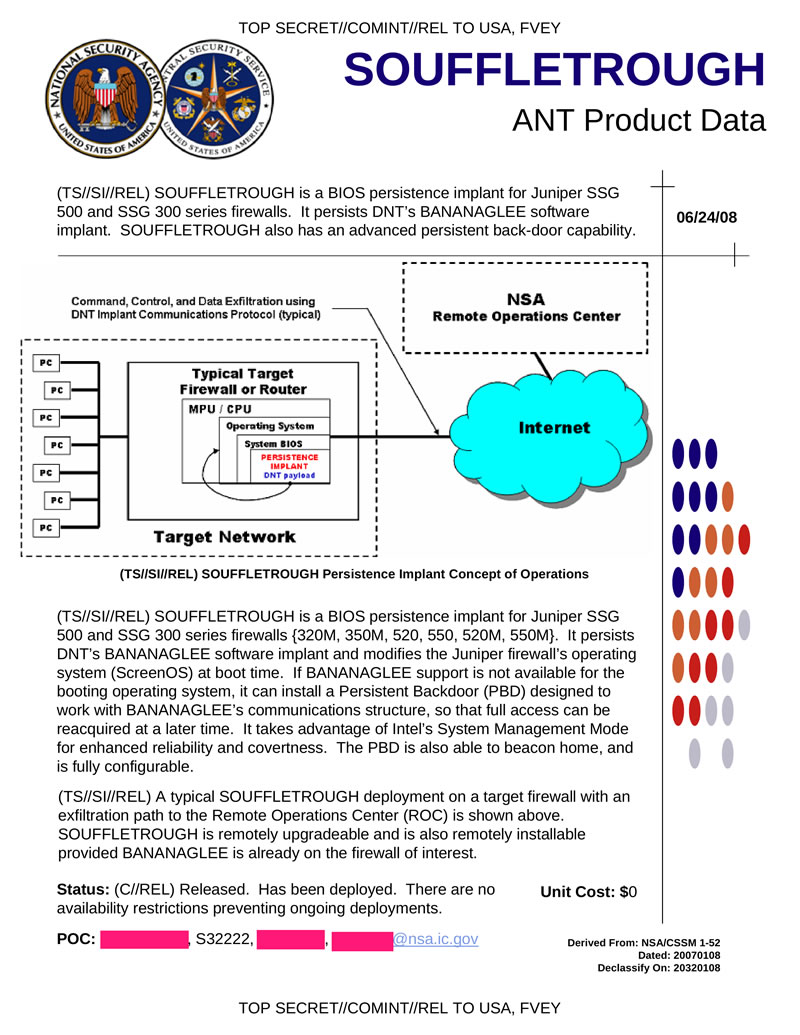

SCHOOLMONTANA provides the presence of network bookmarks. Allows you to save the tab when updating and replacing the operating system, including the physical replacement of the flash card of the router. The main attack vector is aimed at modifying the BIOS. Aimed at Juniper J-series routers running the JUNOS operating system. In fact, this is a backdoor designed for use under FreeBSD.
Hidden text

SIERRAMONTANA ensures the presence of network bookmarks in Juniper M-series routers. Features similar to SCHOOLMONTANA.
Hidden text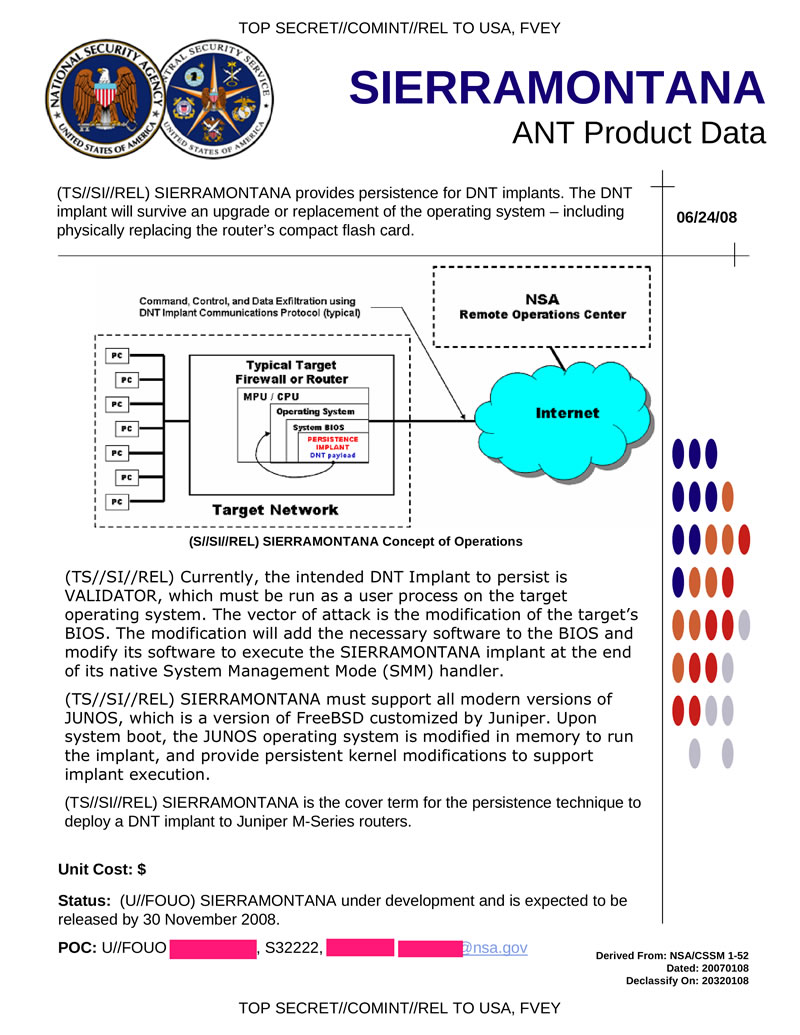

STUCCOMONTANA ensures the presence of network bookmarks in Juniper T-series routers. Features similar to SCHOOLMONTANA.
Hidden text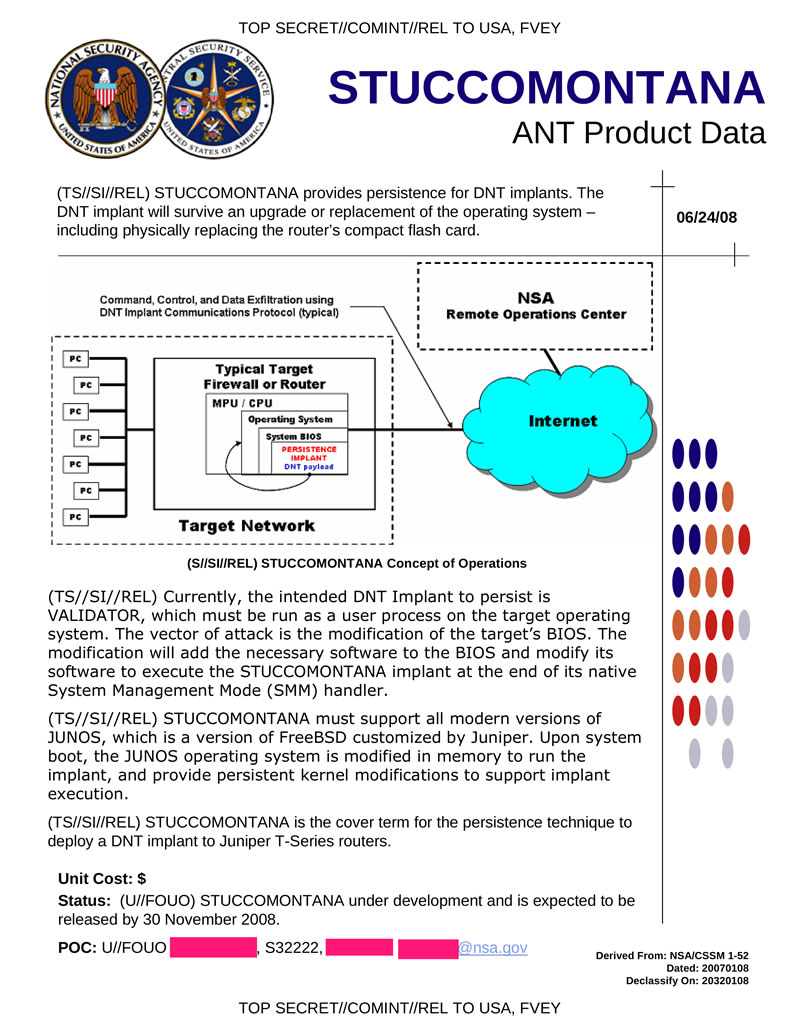

HEADWATER - backdoor for some models of Huawei routers. The backdoor is installed when the boot loader is updated. The general scheme of work is similar to other tabs for network equipment.
Hidden text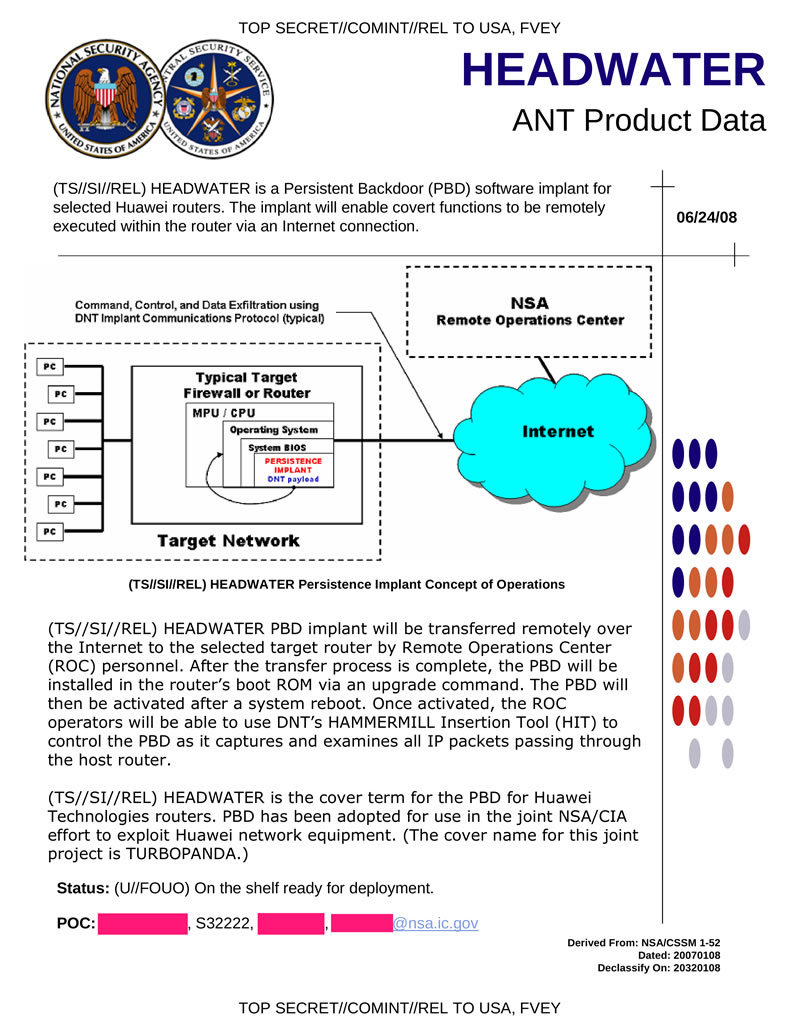

')
GSM networks
CROSSBEAM - tab in the form of a GSM module based on an embedded computer. It can intercept and record data transmitted in GSM networks.
Hidden text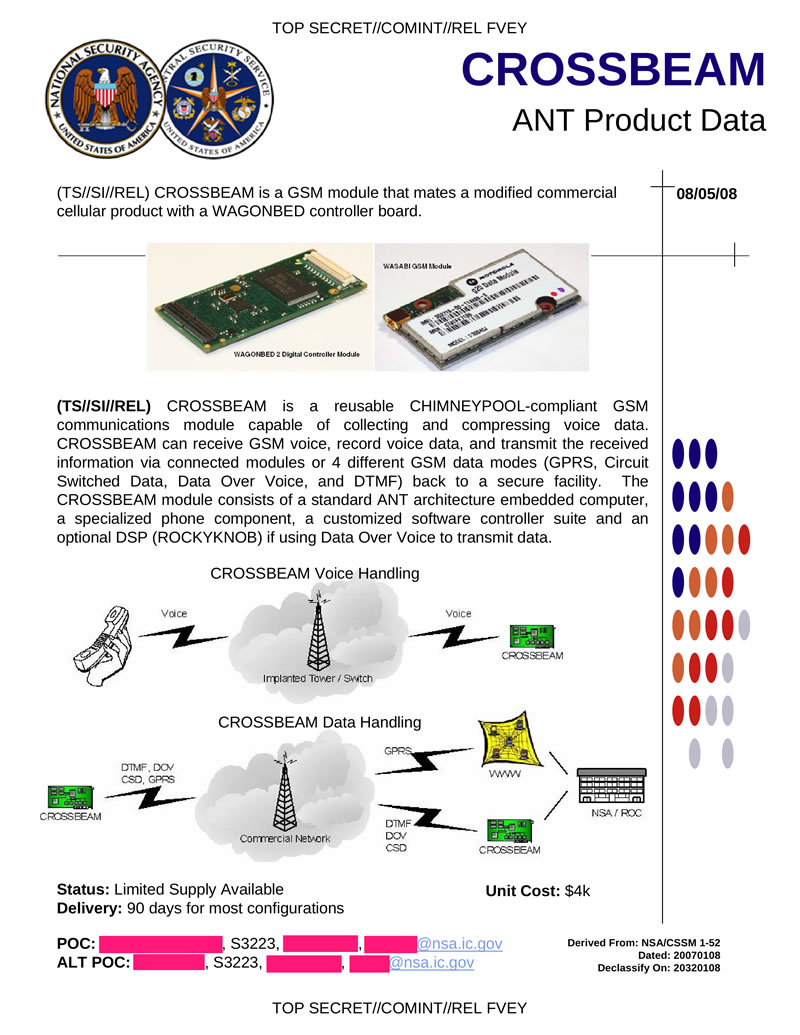

CANDYGRAM - GSM base station emulator (900, 1800, 1900), designed to track the location of the target cell phone. Every time the target phone enters the CANDYGRAM base station coverage area, the system sends an SMS via an external channel to the observer’s phone.
Hidden text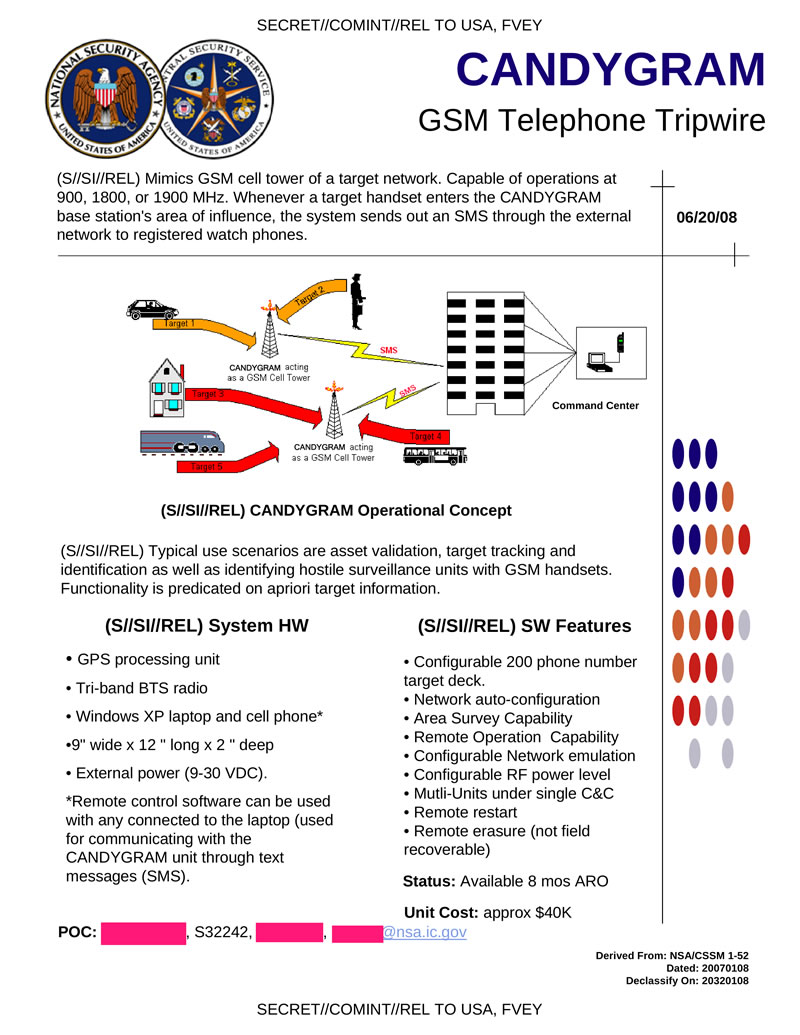

CYCLONE Hx9 is a GSM base station emulator designed for carrying out attacks on mobile phones of the GSM 900 standard. Allows you to listen to and intercept transmitted data. Range up to 32 kilometers.
Hidden text

EBSR is a multipurpose tri-band GSM active base station with low power consumption (1 W). Designed to listen to and intercept transmitted data. It is possible to combine several such devices into a macro network.
Hidden text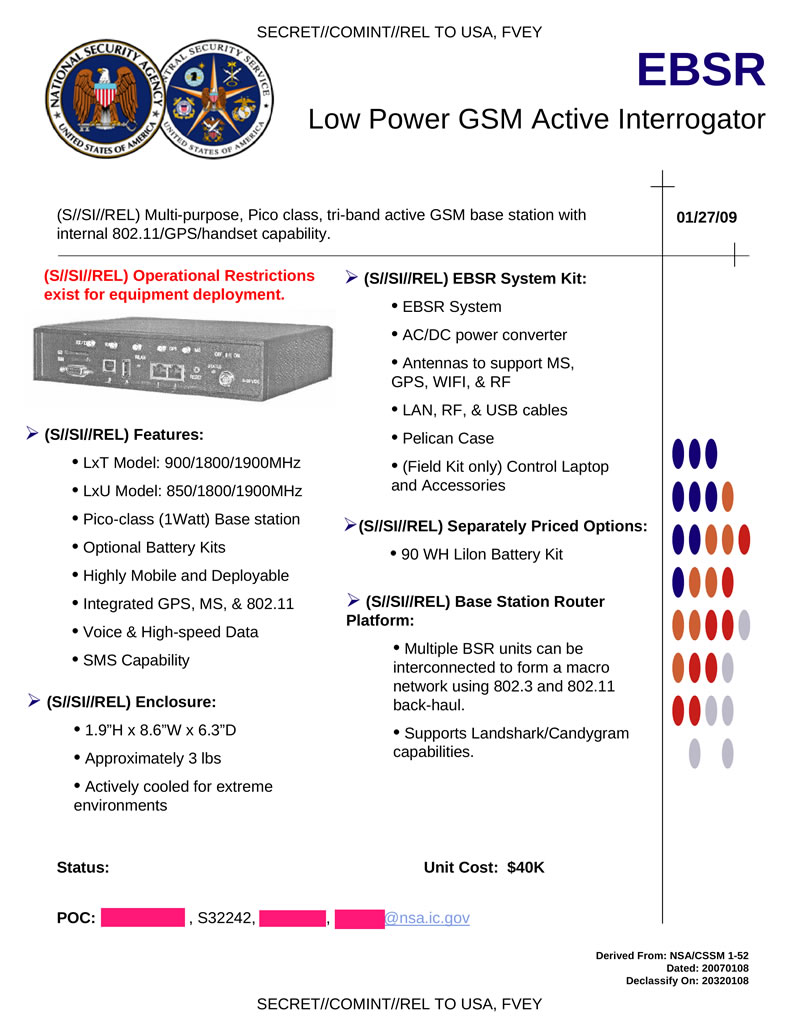

ENTOURAGE is a device for direction finding signals from mobile phones of GSM / UMTS / CDMA2000 / FRS standards. To use it, you need an antenna of the desired range and a laptop (for control).
Hidden text

GENESIS is a device for electronic intelligence based on a modified GSM cell phone. Designed for the search and analysis of cellular networks, as well as determining the location of phone targets. Has the ability to record the radio frequency spectrum in the internal memory, the amount of which is 16GB.
Hidden text

NEBULA is a portable base station for GSM, UMTS, CDMA2000 networks. Allows voice and data interception.
Hidden text

TYPHON HX is a portable base station for GSM networks (850/900/1800/1900). It has full support for GSM protocol and call control. Tactical element of electronic intelligence.
Hidden text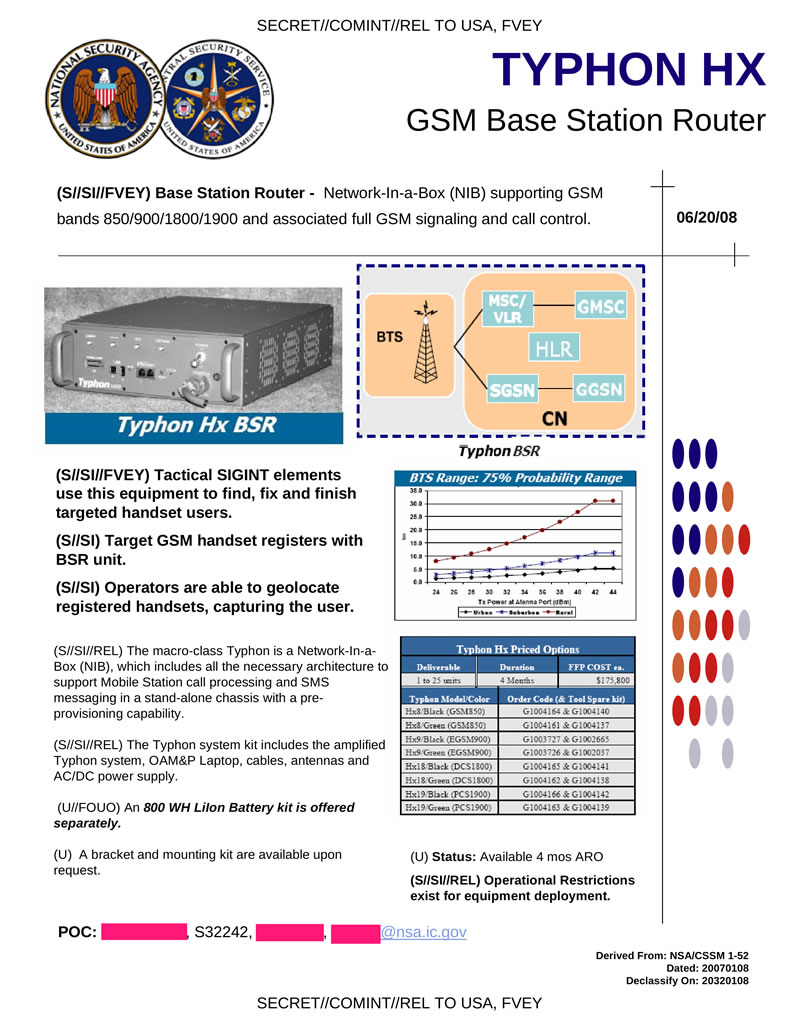

WATERWITCH is a portable device for determining the coordinates of target phones in range.
Hidden text

DROPOUTJEEP - software tab for Apple iPhone iOS allows you to remotely access the phone via SMS or GPRS connection. To install the backdoor you need physical access to the device, the possibility of remote installation is planned in future releases.
Hidden text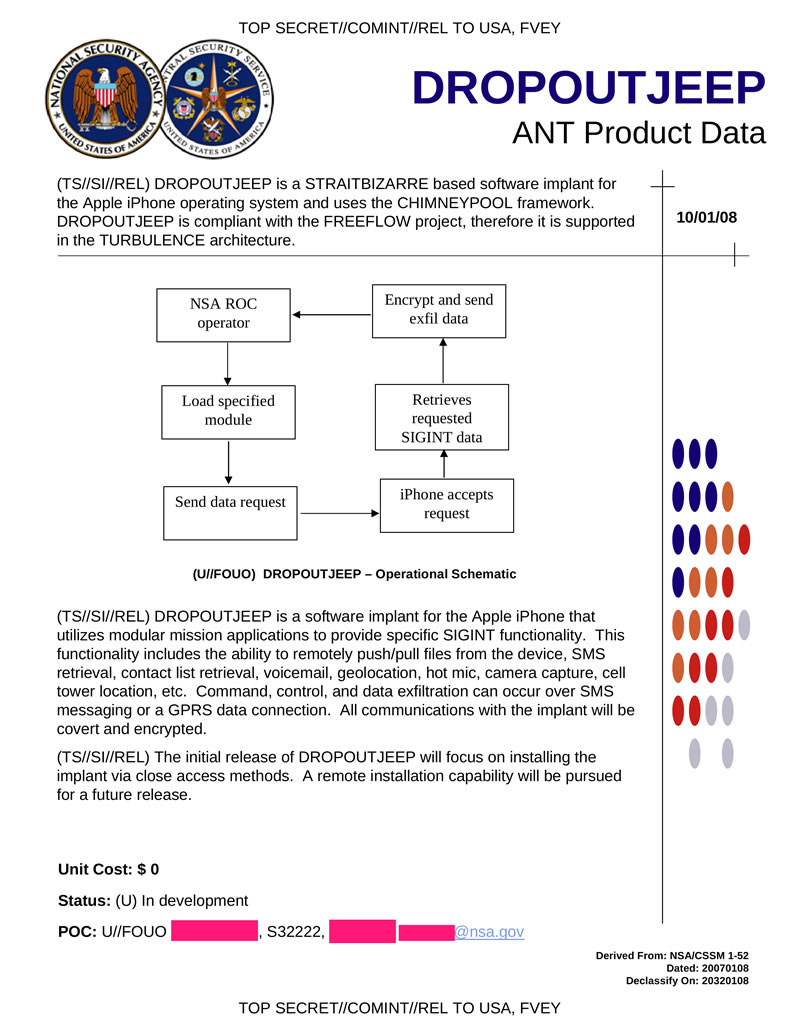

GOPHERSET is a software tab for GSM SIM cards. Allows you to send a phone book, SMS and call phone information of the target to a predefined SMS number. Downloading to the card is possible either via USB or over the air. In both cases, the installation may require keys to access the SIM-card used by the cellular operator.

Hidden text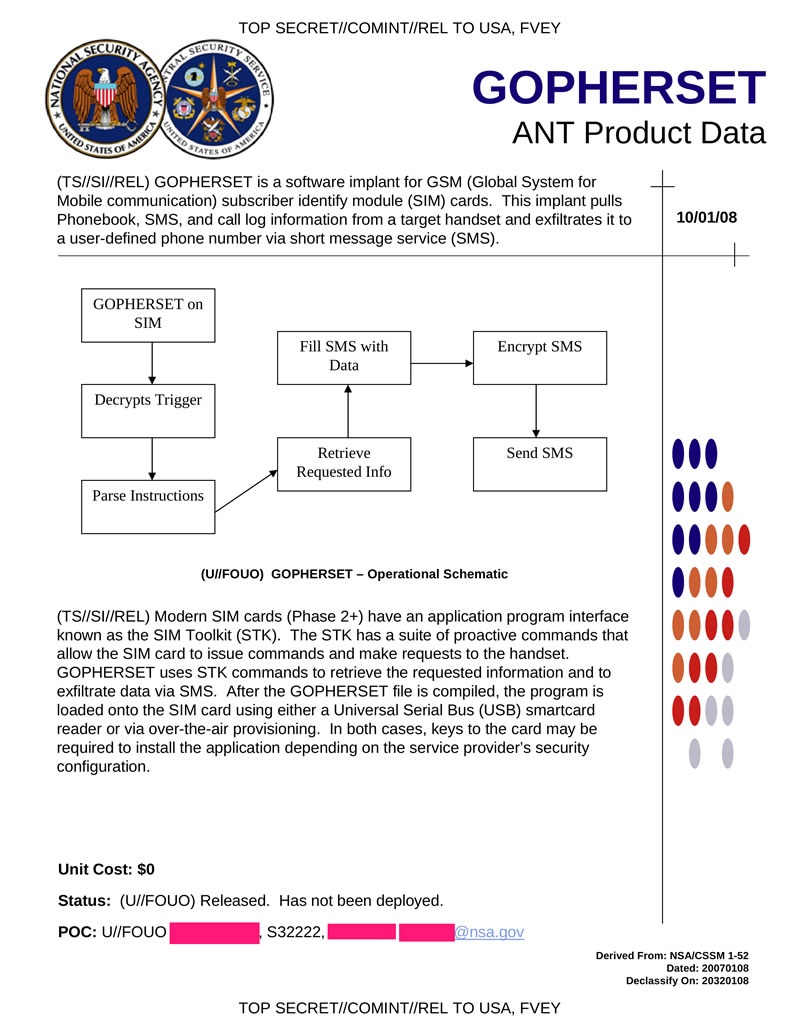

MONKEYCALENDAR- software tab for GSM SIM-cards. Sends the phone coordinates of the target to a predefined SMS number in encrypted form. Installation technology is similar to GOPHERSET.
Hidden text

PICASSO is a modified GSM phone designed for collecting user data, recording sound indoors and tracking (based on data from base stations). Manage and transfer data through SMS.
Hidden text

TOTECHASER - a software tab (under Windows CE) for a dual-band (satellite and GSM) phone Thuraya 2520. Allows you to receive user data from the target phone via hidden SMS via satellite or GSM channel.

Hidden text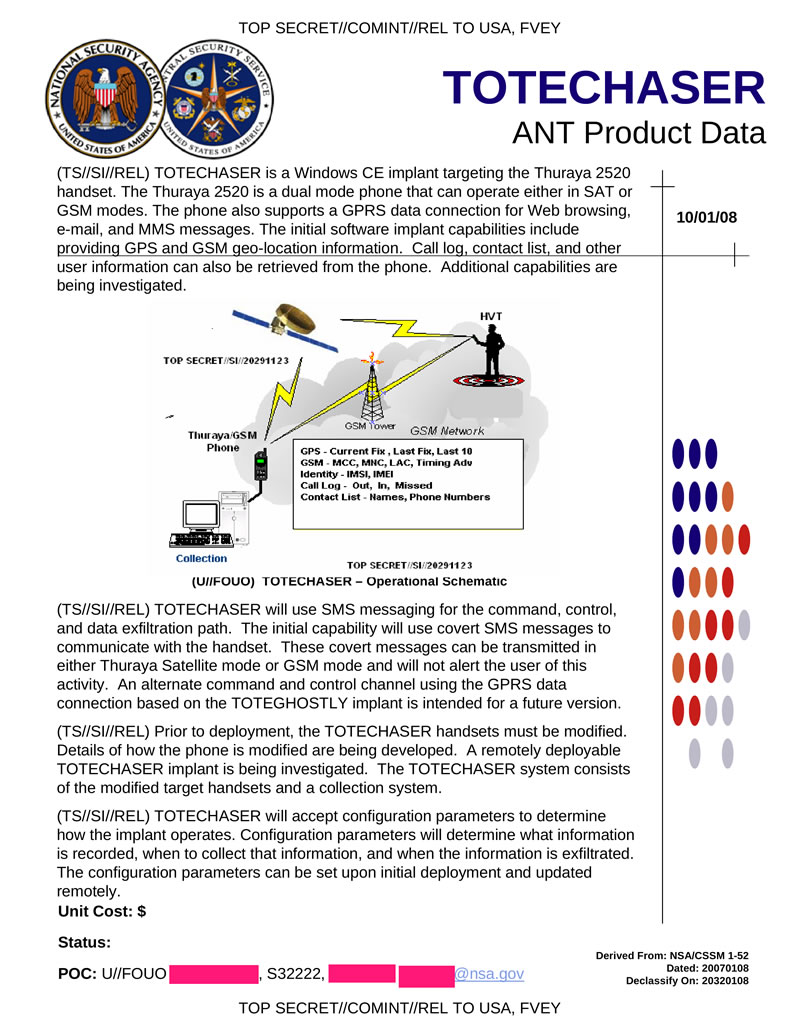

TOTEGHOSTLY 2.0 is a software tab for the Windows Mobile operating system. It has a rich functionality and allows you to get full access to the phone. Management is possible both via SMS and GPRS connection.
Hidden text

Indoor equipment
The CTX4000 is a portable continuous emitter designed to highlight target systems for receiving data from bookmarks installed there. Preceded by PHOTOANGLO.
Hidden text

LOUDAUTO - hardware bookmark. A “bug” is triggered when irradiated with a special signal, transmitting sound from the room in which it is installed in the reflected radio signal.
Hidden text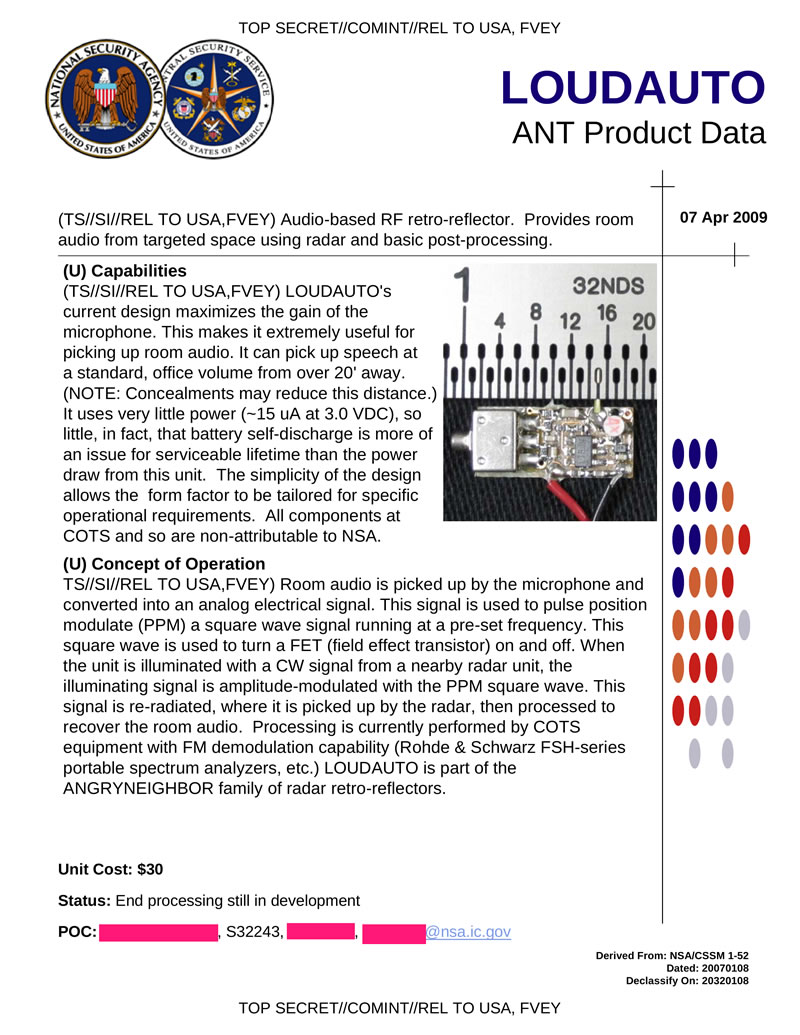

NIGTHWATCH is a portable computer based system designed to process signals from a target monitor. The signal can come from both information acquisition systems (for example, from a CTX4000 or PHOTOANGLO when the bookmark is lit in the RAGEMASTER video cable), or from a general-purpose receiver.
Hidden text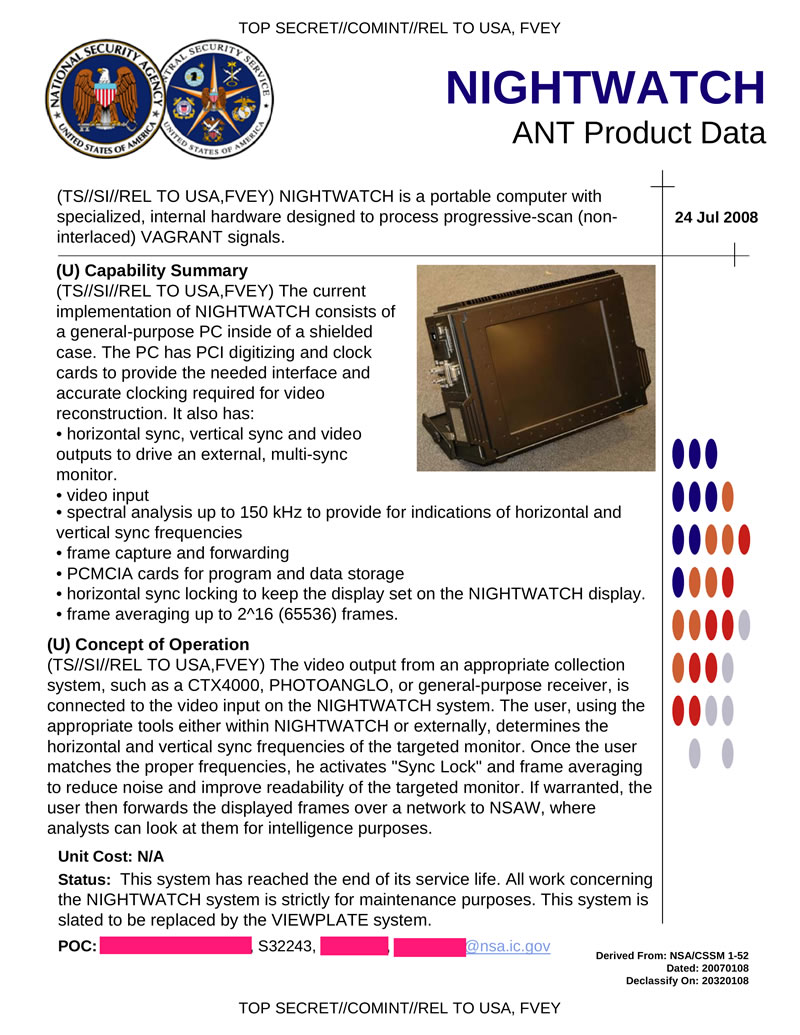

PHOTOANGLO is an improved continuous emitter designed to highlight target systems and receive data from bookmarks installed there. More portable than CTX4000.
Hidden text

TAWDRYYARD - a miniature radio beacon, triggered when receiving a radio signal from a specialized emitter. Used to search for installation locations of other bookmarks, such as, for example, RAGEMASTER.
Hidden text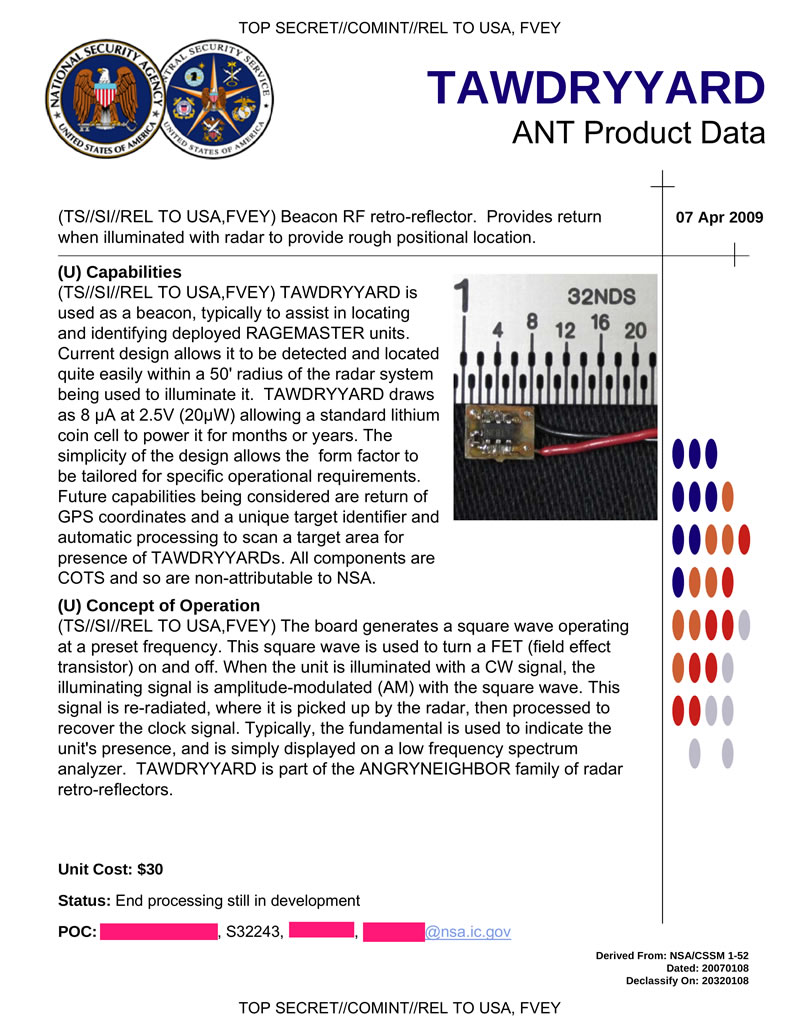

Based on FreeSnowden , LeakSource , Spiegel .
Source: https://habr.com/ru/post/209746/
All Articles