Out-of-box intrusion prevention systems. Test Drive
Hi, Habrovchane! 
Today we want to talk about how intrusion detection / prevention systems do their job right after you get them out of the box, initialize them, and put them in your network. The following hardware platforms will participate in today's test drive:
• Cisco IPS 4240;
• IBM Proventia GX4004;
• StoneGate IPS 1060.
')
Based on our experience, approximately 80% of IPS organizations are not configured properly. This is due to the fact that there is simply no one to configure them or the system was installed only “for a tick” in order to comply with certain requirements of regulators. Therefore, we decided to compare the intrusion detection systems at the default settings.
In the article we want to share the results of our test drive with respected Habrazhiteli.
All interested are invited under the cat.
Here, in fact, our experimental:

To begin with, we will give a few dry numbers describing the performance characteristics of hardware platforms, taken from open information sources:


We will compare the work of three IPS under the same conditions: work in IDS mode (comparison was carried out in a real network), work in IPS mode and “very conditional” load testing (comparison was carried out in the laboratory). As a result, we get a summary table with data on the number of found and blocked vulnerabilities.
At once I would like to say that the comparison took place on the latest available software version and with the latest signatures at the time of testing, the default policies were used to detect and block threats.
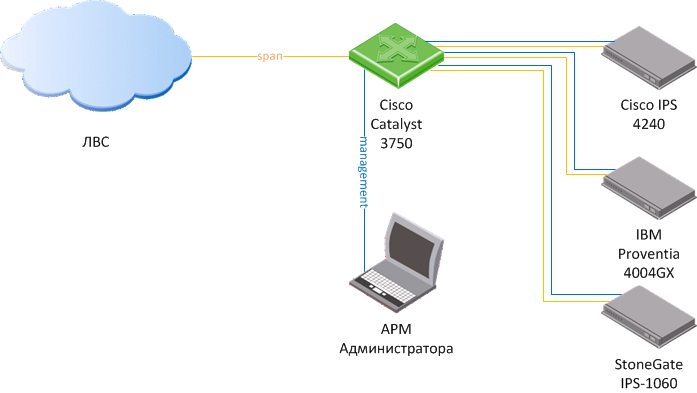
Testing of hardware platforms for intrusion detection systems in IDS mode (monitoring network activity) was carried out according to the scheme shown in the figure below by connecting all the hardware to the Cisco Catalyst 3750 switch ports, on which traffic from the organization’s real network was mirrored.
After three days of work in the monitoring mode of the IPS network, we found the following number of vulnerabilities / attacks (we took into account only vulnerabilities of the High, Medium and Low levels, the Info vulnerabilities were not taken into account):
• Cisco IPS 4240 - 17 vulnerabilities / attacks;
• IBM Proventia GX4004 - 32 vulnerabilities / attacks;
• StoneGate IPS 1060 - 103 vulnerabilities / attacks.
There are not so many common vulnerabilities / attacks that could detect all the glands:
• ICMP Network Sweep w / Address Mask;
• ICMP Network Sweep w / Timestamp;
• TCP_Port_Scan;
• UDP_Port_Scan;
• ICMP_Subnet_Mask_Request;
• ICMP_Timestamp_Request.
A summary table with a list of all found vulnerabilities / attacks and a breakdown by piece of hardware can be viewed under the spoiler.
It is worth noting that IPS in monitoring mode can not only detect attacks, but also find vulnerable services and applications on the network, for example, using the default settings of the SNMP community, using blank passwords, unpatched software.
Testing of hardware platforms for intrusion detection systems in IPS mode (monitoring network activity and blocking malicious traffic) was carried out according to the scheme shown below by alternately turning on all hardware platforms in Inline mode (in the gap) between the Attacker Workstation and the Victims (servers). The Victims had Microsoft Windows 2003 R2 installed and the following application software:
• Oracle express 10g;
• MySQL 5.2;
• Apache 2.2.26;
• WEB IIS 6 / FTP ISS 6;
• Filezilla FTP Server 0.9.41 beta;
• TFTPD 32 4.0;
• MSSQL Express 2005.
With the Attacker Workstation, the Victims were scanned using the Nessus security scanner and a list of vulnerable services running on them was determined. After scanning, attempts were made to exploit vulnerabilities (launch exploits) on the Victims using the Metasploit Framework exploit pack.
Below is a summary table of the IPS attack response:
It can be seen that IPS with default settings can block not all attacks, even those that do not use the latest vulnerabilities. Therefore, it is strongly recommended to customize the piece of hardware specifically for your needs and services.
This testing was performed using the hping3 utility (you can read about the utility here ) from the Backtrack 5 R3 distribution kit. The purpose of the testing was to test the “resistance” of IPS to flood attacks, i.e. we did not try to compare the performance of devices, but only investigated their response to overload.
Stand description:
IPS was established in the gap between the attacking node (OS Backtrack 5 R3) and the victim node (Windows Server 2003 R2). The hping3 utility was launched within 5 minutes with the “--flood” parameter; this key allows you to use the maximum possible packet generation rate.
Command example:
Below is a summary table with the results:
As we can see, none of the IPS systems (on the default settings) could protect the node from a flood attack. Cisco and IBM in the logs issued alerts and did not try to block the attack, StoneGate began to block the connections, but went into reboot, and the attack on the victim continued successfully. This is due to the fact that by default the mode of operation of inline-interfaces is chosen fail-open, i.e. all traffic passes freely between interfaces without inspection in case of failure of the hardware platform.

If you decide to put IPS in order to really protect your users or some important services from outside threats and to be aware of what is happening in your network, we recommend that you do fine-tune the hardware. Properly tuned IPS is able to close a very large number of “holes” in security, even if it is already old and weak. And on the default settings, none of the manufacturers showed results that could be called "impressive."
Thank you all for your attention!
Glebov Maxim, Selishchev Ivan

Today we want to talk about how intrusion detection / prevention systems do their job right after you get them out of the box, initialize them, and put them in your network. The following hardware platforms will participate in today's test drive:
• Cisco IPS 4240;
• IBM Proventia GX4004;
• StoneGate IPS 1060.
')
Based on our experience, approximately 80% of IPS organizations are not configured properly. This is due to the fact that there is simply no one to configure them or the system was installed only “for a tick” in order to comply with certain requirements of regulators. Therefore, we decided to compare the intrusion detection systems at the default settings.
In the article we want to share the results of our test drive with respected Habrazhiteli.
All interested are invited under the cat.
A couple of words about IPS
The Intrusion Prevention System is a software or hardware system for network and computer security that detects intrusions or security breaches and automatically protects against them.
IPS systems can be viewed as an extension of intrusion detection systems (IDS), since the task of tracking attacks remains the same. However, they differ in that IPS must monitor activity in real time and quickly implement actions to prevent attacks. Possible measures are blocking traffic flows in the network, dropping connections, and issuing signals to the operator. IPS can also perform packet defragmentation, TCP packet reordering to protect against packets with modified SEQ and ACK numbers, etc.
IPS systems can be viewed as an extension of intrusion detection systems (IDS), since the task of tracking attacks remains the same. However, they differ in that IPS must monitor activity in real time and quickly implement actions to prevent attacks. Possible measures are blocking traffic flows in the network, dropping connections, and issuing signals to the operator. IPS can also perform packet defragmentation, TCP packet reordering to protect against packets with modified SEQ and ACK numbers, etc.
Technical description of comparable IPS
Here, in fact, our experimental:

To begin with, we will give a few dry numbers describing the performance characteristics of hardware platforms, taken from open information sources:

Program test drive

We will compare the work of three IPS under the same conditions: work in IDS mode (comparison was carried out in a real network), work in IPS mode and “very conditional” load testing (comparison was carried out in the laboratory). As a result, we get a summary table with data on the number of found and blocked vulnerabilities.
At once I would like to say that the comparison took place on the latest available software version and with the latest signatures at the time of testing, the default policies were used to detect and block threats.
Our "racing track"
IDS operation
Testing of hardware platforms for intrusion detection systems in IDS mode (monitoring network activity) was carried out according to the scheme shown in the figure below by connecting all the hardware to the Cisco Catalyst 3750 switch ports, on which traffic from the organization’s real network was mirrored.

After three days of work in the monitoring mode of the IPS network, we found the following number of vulnerabilities / attacks (we took into account only vulnerabilities of the High, Medium and Low levels, the Info vulnerabilities were not taken into account):
• Cisco IPS 4240 - 17 vulnerabilities / attacks;
• IBM Proventia GX4004 - 32 vulnerabilities / attacks;
• StoneGate IPS 1060 - 103 vulnerabilities / attacks.
There are not so many common vulnerabilities / attacks that could detect all the glands:
• ICMP Network Sweep w / Address Mask;
• ICMP Network Sweep w / Timestamp;
• TCP_Port_Scan;
• UDP_Port_Scan;
• ICMP_Subnet_Mask_Request;
• ICMP_Timestamp_Request.
A summary table with a list of all found vulnerabilities / attacks and a breakdown by piece of hardware can be viewed under the spoiler.
Vulnerabilities found
| Signatures | Cisco IPS 4240 | IBM Proventia GX4004 | Stonegate IPS 1060 |
| ICMP Network Sweep w / Address Mask | + | + | + |
| ICMP Network Sweep w / Timestamp | + | + | + |
| Microsoft Windows CIFS Clientside Buffer Overflow (CVE-2011-0654) | + | - | - |
| SNMP Protocol Violation (CVE-2002-0012, CVE-2002-0013) | + | - | - |
| UPnP LOCATION Overflow | + | - | - |
| Invalid DHCP Packet (CVE-2004-1111) | + | - | - |
| TCP Segment Overwrite | + | - | - |
| DHCP Client DoS (CVE-2008-0084) | + | - | - |
| TCP MSS exceeds maximum | + | - | - |
| SQL Query in HTTP Request (CVE-2005-4643, CVE-2006-0581) | + | - | - |
| Email_Calendar_Code_Exec (CVE-2007-0039) | - | + | - |
| Email_Mime_Filename_Overflow (CVE-1999-0004) | - | + | - |
| Email_Mime_Name_Overflow | - | + | - |
| HTML_UTF8_Overflow (CVE-2006-2382) | - | + | - |
| HTTP_CheckPoint_FW1_FormatString (CVE-2004-0039) | - | + | - |
| Image_JPEG_IE_Component_Overflow (CVE-2005-2308) | - | + | - |
| OTF_Windows_Cmap_Table_Corruption (CVE-2010-3959) | - | + | - |
| PsExec_Service_Accessed | - | + | - |
| PsExec_Installed | - | + | - |
| Script_IE_Improper_Ref_Counting (CVE-2012-4787) | - | + | - |
| SMB_Empty_Password | - | + | - |
| BackOrifice_Ping (CVE-1999-0660) | - | + | - |
| Email_Executable_Extension | - | + | - |
| Flash_NavigateToURL_XSS (CVE-2007-6244) | - | + | - |
| HTTP_Connect_Proxy_Bypass_SMTP | - | + | - |
| HTTP_Field_With_Binary | - | + | - |
| HTTP_Proxy_Cache_Poisoning (CVE-2005-1215) | - | + | - |
| HTTP_URL_repeated_char | - | + | - |
| HTTPS_Proxy_Info_Disclosure (CVE-2005-2830) | - | + | - |
| ICMP_Flood | - | + | - |
| Ping_sweep | - | + | - |
| Smurf_Attack (CVE-1999-0513) | - | + | - |
| SNMP_Default_Backdoor (CVE-2000-0147) | - | + | - |
| TCP_Port_Scan | + | + | + |
| UDP_Port_Scan | + | + | + |
| DNS_Version_Request | - | + | - |
| HTTP_Authentication | - | + | - |
| HTTP_Microsoft_Error_Report | - | + | - |
| ICMP_Subnet_Mask_Request | + | + | + |
| ICMP_Timestamp_Request | + | + | + |
| ASN.1_Oversize-Block | - | - | + |
| HTTP_CRL-Excessively-Long-Options-Request-Argument (CVE-2010-0361) | - | - | + |
| SMTP_CS-Novell-Groupwise-Client-Img-Tag-Src-Parameter-Buffer-Overflow (CVE-2007-6435) | - | - | + |
| MSRPC-TCP_CPS-Samba-Spoolss-RPC-SmbIoNotifyOptionTypeData-Request-Handling-BOF (CVE-2007-2446) | - | - | + |
| SMB-TCP_Negotiate-Protocol-Smb2-Remote-Code-Execution (CVE-2009-3103) | - | - | + |
| File-OLE_Microsoft-Excel-File-Handling-Code-Execution-Vulnerability (CVE-2008-0081) | - | - | + |
| File-OLE_Microsoft-VBA6-Stack-Memory-Corruption (CVE-2010-0815) | - | - | + |
| File-OLE_Microsoft-WordPad-Text-Converter-CVE-2010-2563 | - | - | + |
| File-OLE_Microsoft-WordPad-Text-Converter-Buffer-Overflow (CVE-2010-1900) | - | - | + |
| File-OLE_Microsoft-Excel-Graphic-Object-Deref-Vulnerability-CVE-2011-0977 | - | - | + |
| File-OLE_Microsoft-Office-Word-Sprmcmajority-Record-Buffer-Overflow | - | - | + |
| File-OLE_Microsoft-Excel-Heap-Overflow-Vulnerability-CVE-2011-0098 | - | - | + |
| File-OLE_Microsoft-Excel-Style-Record-Data-Handling-Code-Execution (CVE-2008-0114) | - | - | + |
| File-OLE_Microsoft-Excel-Merge-Cell-Record-Pointer-CVE-2010-3237 | - | - | + |
| File-OLE_Microsoft-Office-Art-Property-Table-Memory-Corruption (CVE-2008-0114) | - | - | + |
| File-OLE_Microsoft-Office-Drawing-Exception-Handling-CVE-2010-3335 | - | - | + |
| File-OLE_Microsoft-Office-Excel-Table-Record-Parsing-Code-Execution (CVE-2010-3232) | - | - | + |
| File-OLE_Microsoft-Graphics-Rendering-Engine-Thumbnail-Stack-Buffer-Overflow (CVE-2010-3970) | - | - | + |
| File-OLE_Microsoft-Office-Excel-Malformed-Records-Stack-Buffer-Overflow (CVE-2009-0559) | - | - | + |
| File-OLE_Microsoft-Office-Excel-Unexpected-Field-Value-Memory-Corruption (CVE-2009-0560) | - | - | + |
| File-OLE_Microsoft-Excel-Version-Information-Handling-Code-Execution (CVE-2010-0262) | - | - | + |
| File-OLE_Microsoft-Word-File-Information-Memory-Corruption-MS09-068 (CVE-2009-2135) | - | - | + |
| File-OLE_Microsoft-Excel-Conditional-Formatting-Values-Handling-Code-Execution (CVE-2008-0117) | - | - | + |
| File-OLE_Autonomy-Keyview-Excel-File-Sst-Parsing-Integer-Overflow | - | - | + |
| File-OLE_Microsoft-Excel-Frtwrapper-Record-Buffer-Overflow (CVE-2008-3471) | - | - | + |
| File-OLE_Microsoft-Excel-Named-Graph-Record-Parsing-Stack-Overflow (CVE-2007-0215) | - | - | + |
| File-OLE_Microsoft-Office-Excel-Remote-Code-Execution-CVE-2009-3134 | - | - | + |
| File-OLE_Microsoft-Excel-Use-After-Free-WriteAV-Vulnerability (CVE-2011-1986) | - | - | + |
| File-OLE_Microsoft-Excel-Array-Indexing-Vulnerability-CVE-2011-1990 | - | - | + |
| File-OLE_Microsoft-Excel-Conditional-Expression-Parsing-Vulnerability (CVE-2011-1989) | - | - | + |
| File-OLE_Microsoft-Excel-Malformed-Fngroupcount-Value-Code-Execution (CVE-2006-1308) | - | - | + |
| File-OLE_Microsoft-Excel-Sst-Invalid-Length-Use-After-Free (CVE-2012-1887) | - | - | + |
| File-OLE_Microsoft-Excel-Memory-Corruption-CVE-2012-1886 | - | - | + |
| File-Binary_Oracle-Java-Runtime-CMM-Readmabcurvedata-Buffer-Overflow (CVE-2010-0838) | - | - | + |
| File-MPEG_Microsoft-DirectShow-QuickTime-Movie-Parsing-Code-Execution (CVE-2009-1537) | - | - | + |
| File-Binary_IBM-Lotus-Notes-1-2-3-Work-Sheet-File-Viewer-Buffer-Overflow | - | - | + |
| File-Text_Mozilla-Firefox-Multiple-URI-Handlers-Command-Execution (CVE-2007-4041, CVE-2007-3896) | - | - | + |
| File-Binary_Adobe-Reader-Security-Bypass-CVE-2013-0624 | - | - | + |
| File-Text_Microsoft-Internet-Explorer-Object-Reference-Count-Memory-Corruption (CVE-2007-3902) | - | - | + |
| File-Text_Microsoft-Internet-Explorer-Virtual-Function-Table-Memory-Corruption (CVE-2011-2001) | - | - | + |
| File-Text_Microsoft-Internet-Explorer-HTML-Layout-CVE-2012-0011 | - | - | + |
| HTTP_Reply-Chunked-Encoded-Chunk-Unparseable | - | - | + |
| TCP_Segment-Content-Conflict | - | - | + |
| TCP_Window-Shrinked | - | - | + |
| Shared_CS-x86-X41nop-Shellcode | - | - | + |
| Shared_SS-x86-X41nop-Shellcode | - | - | + |
| HTTP_CSU-Potential-Dot-Dot-Slash-Directory-Traversal | - | - | + |
| HTTP_CRL-Microsoft-ASP.NET-ViewState-Denial-Of-Service | - | - | + |
| HTTP_CRL-Php-Quot-Print-Encode-Heap-Buffer-Overflow | - | - | + |
| SMB-TCP_Samba-Authentication-Bypass | - | - | + |
| SMB-TCP_MS-Windows-Print-Spooler-Service-Format-String-Vulnerability (CVE-2010-2563) | - | - | + |
| SNMP-UDP_Default-Community-String-Accepted | - | - | + |
| MSRPC_SS-Sourcefire-Snort-Rule20275eval-Buffer-Overflow | - | - | + |
| File-OLE_Microsoft-Excel-Linked-List-Corruption-Vulnerability-CVE-2011-0979 | - | - | + |
| File-OLE_Microsoft-Excel-Memory-Heap-Overwrite-Vulnerability-CVE-2011-1275 | - | - | + |
| File-OLE_Microsoft-Office-PowerPoint-FB1h-Parsing-BOF-CVE-2010-2572 | - | - | + |
| File-OLE_Microsoft-Office-Excel-SxView-SXStreamID-CVE-2010-1245 | - | - | + |
| File-OLE_Microsoft-Office-Excel-Malformed-Object-Record-Parsing-Code-Execution (CVE-2009-0557) | - | - | + |
| File-OLE_Microsoft-Office-Excel-Malformed-LBL-Record-Memory-Corruption (CVE-2009-0558) | - | - | + |
| File-OLE_Microsoft-Excel-Colinfo-Record-Buffer-Overflow (CVE-2006-3875) | - | - | + |
| File-OLE_OpenOffice-OLE-File-Stream-Buffer-Overflow (CVE-2008-0320) | - | - | + |
| File-OLE_Microsoft-Excel-Malformed-Selection-Record-Code-Execution (CVE-2006-1301) | - | - | + |
| File-OLE_Microsoft-Office-Excel-File-Obj-Record-Memory-Corruption (CVE-2008-4264) | - | - | + |
| File-OLE_Microsoft-PowerPoint-OfficeArt-Shape-RCE-Vulnerability (CVE-2011-3413) | - | - | + |
| File-OLE_Microsoft-Excel-MergeCells-Record-Heap-Overflow-Vulnerability (CVE-2012-0185) | - | - | + |
| File-OLE_Microsoft-Office-Excel-Publisher-Record-Memory-Corruption (CVE-2010-1250) | - | - | + |
| File-Text_x86-X41nop-Shellcode | - | - | + |
| HTTP_Reply-Content-Type-Missing | - | - | + |
| UDP_Checksum-Mismatch | - | - | + |
| E-Mail_IMF-Multipart-Delimiter-Use-Invalid | - | - | + |
| E-Mail_IMF-Base64-Length-Inconsistency | - | - | + |
| IP_Checksum-Mismatch | - | - | + |
| DNS_Client-Name-Bad-Label-Type | - | - | + |
| DNS_Client-Class-Unknown | - | - | + |
| TCP_Segment-SYN-Unexpected | - | - | + |
| TCP_Segment-SYN-ACK-Unexpected | - | - | + |
| E-Mail_IMF-Too-Long-Header | - | - | + |
| E-Mail_IMF-Too-Long-Header-Field | - | - | + |
| POP3_Server-Syntax-Error | - | - | + |
| E-Mail_Message-Syntax-Error | - | - | + |
| E-Mail_Content-Transfer-Encoding-Duplicate | - | - | + |
| SMTP_Unknown-Command | - | - | + |
| HTTP_IIS-Unicode-Encoding | - | - | + |
| HTTP_Version-Varies | - | - | + |
| HTTP_Request-Extra-Data | - | - | + |
| TCP_Segment-SYN-ISN-Mismatch | - | - | + |
| DNS-UDP_Nameserver-Version-Query | - | - | + |
| HTTP_CS-Long-HTTP-Authorization-Negotiate-Token | - | - | + |
| HTTP_CSU-Windows-Style-Absolute-Path-In-URI | - | - | + |
| MSRPC-TCP_CPS-Windows-Local-Security-Authority-Username-Disclosure | - | - | + |
| SNMP-UDP_Linux-Kernel-SNMP-NAT-Helper-SNMP-Decode-DoS-2 | - | - | + |
| SNMP-UDP_Default-Community-String-Rejected | - | - | + |
| File-Binary_Windows-LNK-File-Transfer | - | - | + |
| HTTP_SHS-HTTP-0.9-Response-After-HTTP-1.0-Request | - | - | + |
| HTTP_SHS-Content-After-Zero-Content-Length | - | - | + |
| File-PNG_Conflicting-Content-Type-Text | - | - | + |
| File-PNG_Conflicting-Content-Type-Text-Plain | - | - | + |
It is worth noting that IPS in monitoring mode can not only detect attacks, but also find vulnerable services and applications on the network, for example, using the default settings of the SNMP community, using blank passwords, unpatched software.
IPS operation
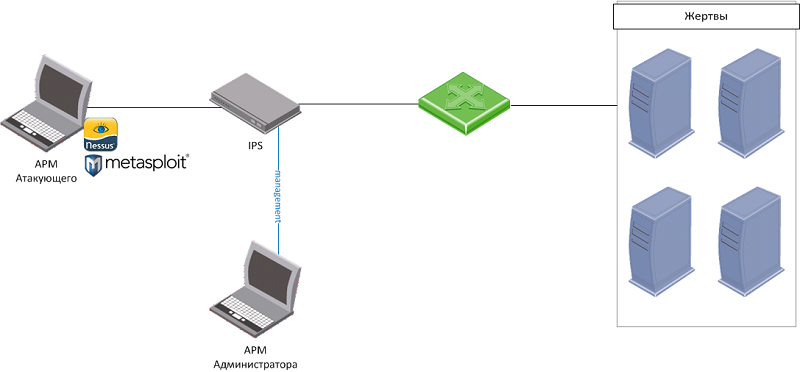
Testing of hardware platforms for intrusion detection systems in IPS mode (monitoring network activity and blocking malicious traffic) was carried out according to the scheme shown below by alternately turning on all hardware platforms in Inline mode (in the gap) between the Attacker Workstation and the Victims (servers). The Victims had Microsoft Windows 2003 R2 installed and the following application software:
• Oracle express 10g;
• MySQL 5.2;
• Apache 2.2.26;
• WEB IIS 6 / FTP ISS 6;
• Filezilla FTP Server 0.9.41 beta;
• TFTPD 32 4.0;
• MSSQL Express 2005.

With the Attacker Workstation, the Victims were scanned using the Nessus security scanner and a list of vulnerable services running on them was determined. After scanning, attempts were made to exploit vulnerabilities (launch exploits) on the Victims using the Metasploit Framework exploit pack.
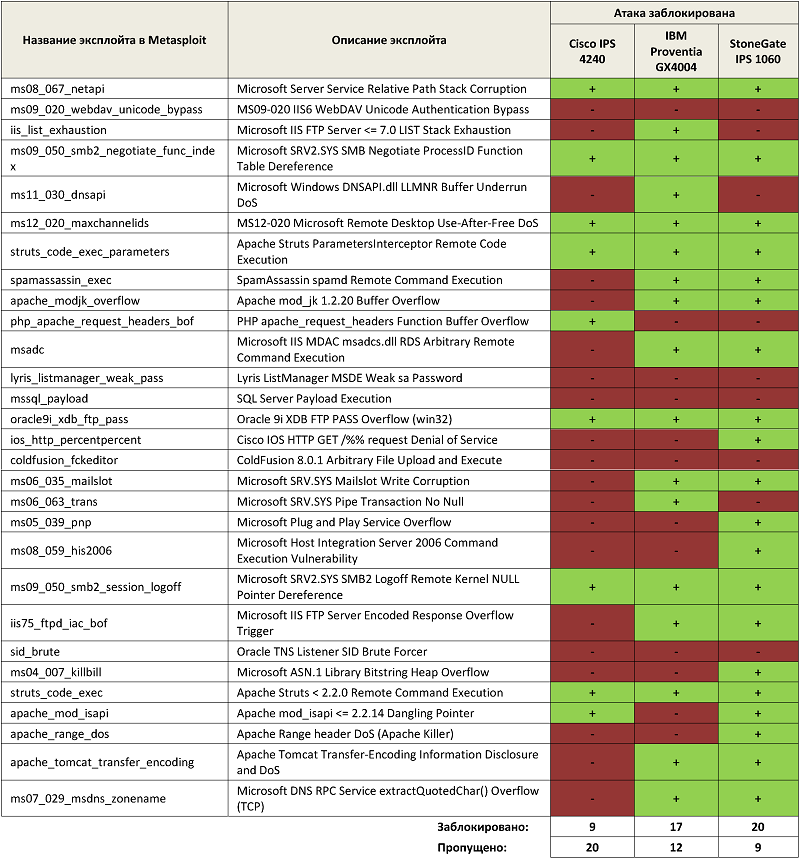
Below is a summary table of the IPS attack response:

It can be seen that IPS with default settings can block not all attacks, even those that do not use the latest vulnerabilities. Therefore, it is strongly recommended to customize the piece of hardware specifically for your needs and services.
"Very conditional" load testing
This testing was performed using the hping3 utility (you can read about the utility here ) from the Backtrack 5 R3 distribution kit. The purpose of the testing was to test the “resistance” of IPS to flood attacks, i.e. we did not try to compare the performance of devices, but only investigated their response to overload.
Stand description:
IPS was established in the gap between the attacking node (OS Backtrack 5 R3) and the victim node (Windows Server 2003 R2). The hping3 utility was launched within 5 minutes with the “--flood” parameter; this key allows you to use the maximum possible packet generation rate.
Command example:
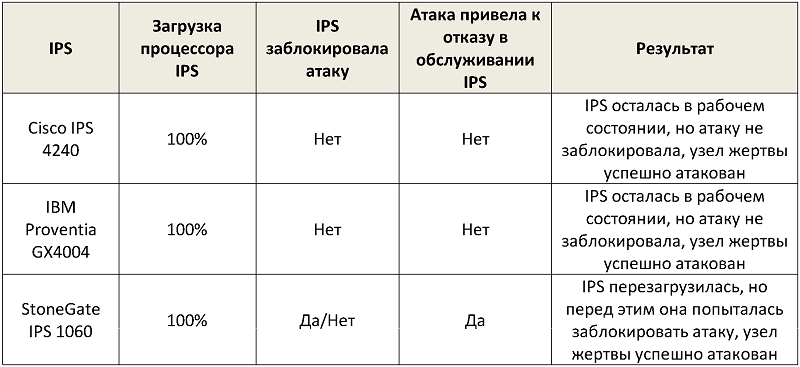
hping3 ip_address --floodBelow is a summary table with the results:

As we can see, none of the IPS systems (on the default settings) could protect the node from a flood attack. Cisco and IBM in the logs issued alerts and did not try to block the attack, StoneGate began to block the connections, but went into reboot, and the attack on the victim continued successfully. This is due to the fact that by default the mode of operation of inline-interfaces is chosen fail-open, i.e. all traffic passes freely between interfaces without inspection in case of failure of the hardware platform.
Conclusion

If you decide to put IPS in order to really protect your users or some important services from outside threats and to be aware of what is happening in your network, we recommend that you do fine-tune the hardware. Properly tuned IPS is able to close a very large number of “holes” in security, even if it is already old and weak. And on the default settings, none of the manufacturers showed results that could be called "impressive."
Thank you all for your attention!
Glebov Maxim, Selishchev Ivan
Source: https://habr.com/ru/post/209714/
All Articles