Results of 2013: threats and exploitation of Windows
The global threat landscape is becoming richer and more active every year, every day there are many modifications of various existing malware, as well as new malware and other tools used by attackers. The past year has only consolidated the main trend of separating malware or using them into two types: used by hackers to extract personal material gains and used by attackers for targeted attacks, watering hole to compromise a certain company, industry or region of the globe.

Despite the fact that Remote Code Execution vulnerabilities in popular software (browsers) play a significant role in the remote delivery of malicious content that attackers are interested in (the main drive-by trend), they often resort to much simpler methods of installing malicious objects into the system using human factor. The use of double extensions in files, a convincing phishing message, targeting certain people (including intelligence), fake file icons, documents with convincing content, all this makes up the arsenal of attackers who are interested in installing malicious code into the system of the alleged victim.
')

Fig. A typical example of using a double extension in a file name with an MS Word document icon inserted into an executable file. A reliable way to mislead the victim, because in the default settings, Windows Explorer hides the extension of files known to it.
As the experience of attackers from the APT1 group and other attacking groups who were engaged in industrial espionage showed, it is initially necessary to conduct minimal intelligence to identify the alleged victim and obtain information about her, for example. e-mail address. In the future, a convincing phishing message will be sent to this address.

Fig. An example of a phishing message that can be sent to the user's corporate mailbox, in order to compromise corporate information. The first thing that catches your eye is the use of a gmail mail account instead of a corporate one by a company manager.
This type of attack can be used not only for industrial espionage, but also in more local attacks against a specific company, for example, in order to obtain important information from competitors using malicious code.
Windows threats
This is not to say that the past year brought something fundamentally new for Windows. Turning on a computer in a botnet, stealing account data and online banking data, getting remote access to a computer (backdoor), blocking a computer for ransom (extortioner) are the main goals of cybercriminals who are interested in gaining material gain from compromised users. Below we provide statistics on some families of malicious code that were active in the past year.
File viruses are still quite active. This year, the three Win32 / Sality , Win32 / Ramnit and Win32 / Virut families steadily fell into the top ten world threats according to statistics from our ESET Live Grid telemetry system. Viruses compromise executable files on a user's computer and violate their integrity, and can also threaten the entire enterprise network if one of the computers contains at least one malicious file, because they can infect network drives of other computers on the network.

For Russia, the most topical malware is Win32 / Qhost , besides that it is in itself, first of all, targeted at Russian users (see the geography of distribution below), which clearly hints at its domestic roots. The Qhost code itself is quite simple and modifies the system hosts file to redirect the user to the phishing, advertising and malicious resources needed by attackers. Such redirects (clicks) are later monetized and bring actual profits to the attackers.
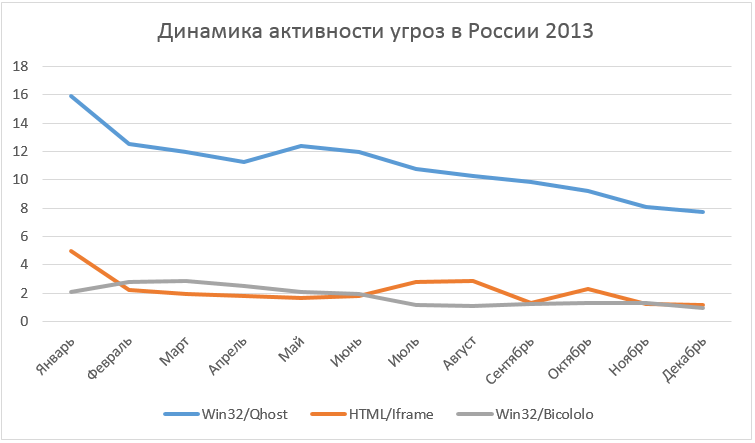
Generic HTML / IFrame detection is used to identify malicious elements of web pages. Often malicious iframes are used to redirect a user from a legitimate web page to malicious content or a set of exploits.
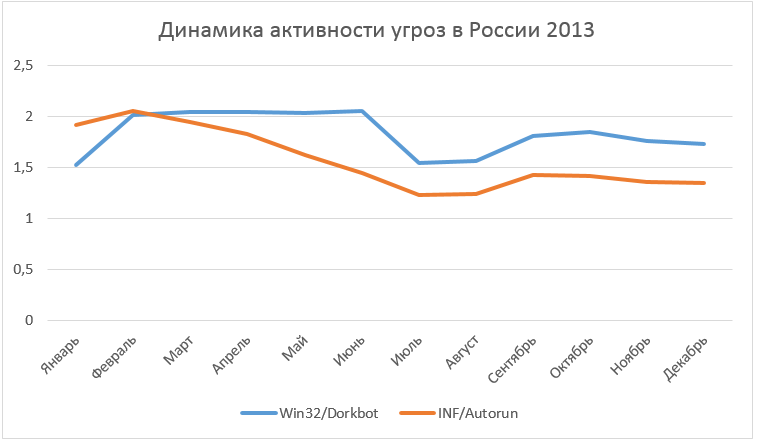
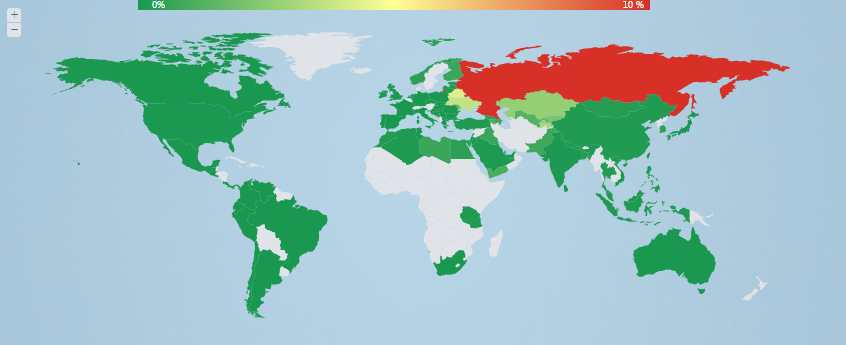
Fig. The geography of distribution of Qhost. Russia is the most affected region.
As can be seen in the diagram above, in Russia (and in the world) there is still a high activity of malicious programs that use .inf files to ensure their launch both from removable media and locally in the system. ESET antivirus products detect these malicious files under the general INF / Autorun family. Such an autorun mechanism is especially relevant for legacy OSs, since they have an autorun autorun mechanism enabled by default through Autorun files. For more information about disabling autorun using Autorun files on such OS see KB967715 .
The table below lists the vulnerabilities (0day at the time of operation), with which the attackers delivered malicious code. The past year 2013 can rightly be called the year of targeted attacks and watering hole attacks, for many of them the attackers specifically searched for a particular vulnerability and used it exclusively to attack a specific region or particular company. In particular, watering hole was used to compromise websites that were actively visited by alleged victims in different regions of the world. We believe that in 2014 this trend will become even more widespread.

This year, we repeatedly wrote about attacks on popular instant messengers such as Skype and Gtalk, as well as social networks, such as Facebook or Vkontakte. We will not repeat, but just note that attackers take advantage of persuasive phishing messages, supposedly trusted domains, in which there is a slip of the letter and a few link shortening services to lure users to follow a malicious link. To organize a large-scale spam mailing, attackers need to create auxiliary fake accounts in a particular service, use user accounts with reduced security settings, and also malicious code with the ability to inject their code into messengers ( Win32 / Rodpicom.C ) to send messages . Since the number of users of all these services is only increasing, we believe that we can expect this kind of attack in the next year.
Trends for Windows
More detailed information about the detected Cryptolocker modifications is given in the table below.

Mobile threats - the main trend of the year
In our last year's report, which was called “Overview of the main threats and trends in 2012”, we pointed to the rapid spread of malware for Android. For example, in 2012 compared to 2011, the number of malicious objects we detected increased 17 times.
We also predicted the rapid growth of new threats in 2013. Such a prediction really came true and this year we recorded the appearance of a large number of malicious programs for this platform.
It's no secret that Android is the most common platform for mobile devices. The statistics provided by Gartner for the second quarter of 2013 shows that Android has further strengthened its position in the mobile device market almost reaching 80%.
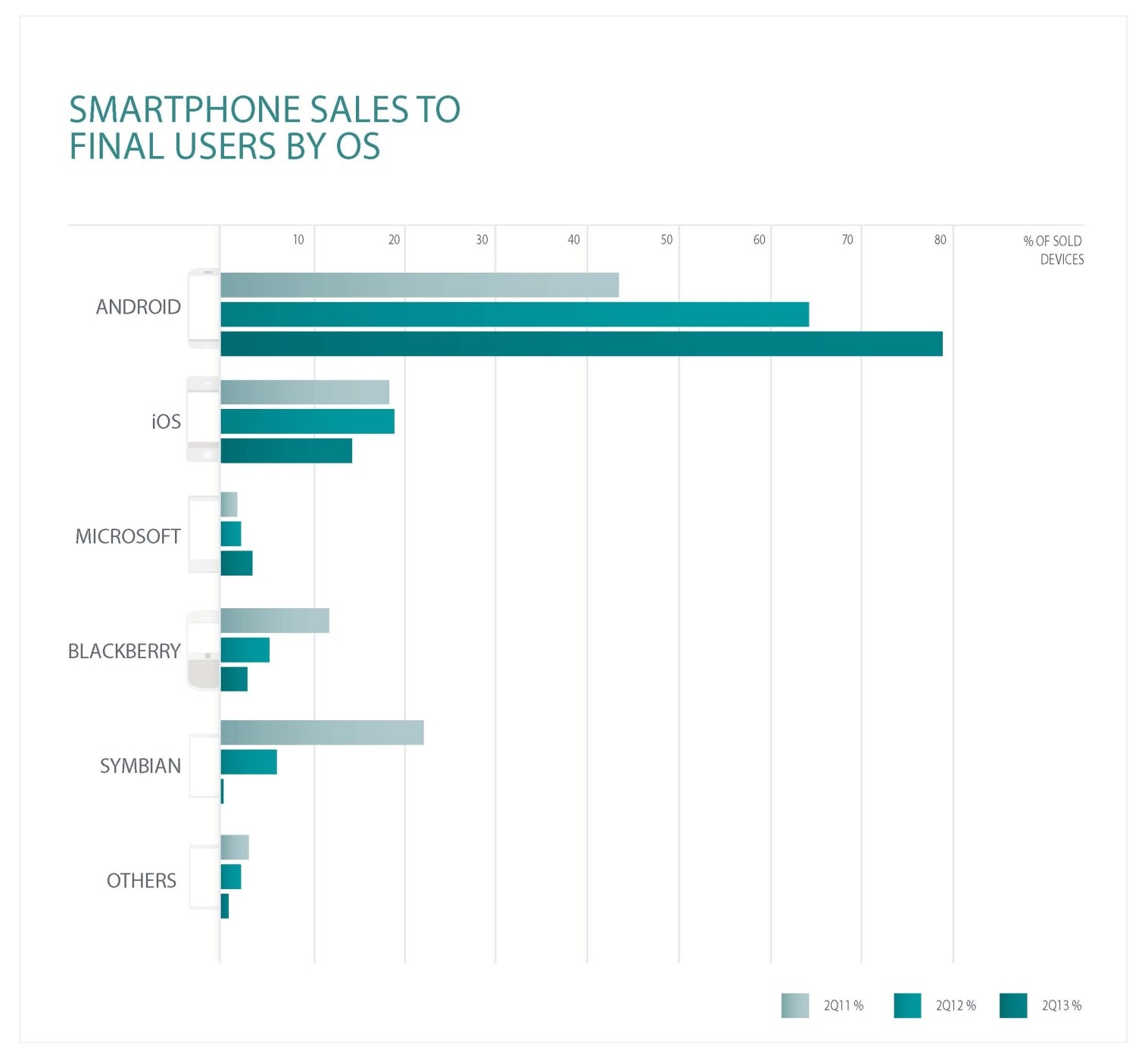
Fig. The percentage of mobile operating systems sold with corresponding devices in the second quarter of 2011, 2012 and 2013. (Gartner data).
Regarding Microsoft’s new mobile platforms - Windows RT (based on Windows 8, for example, Surface 2) and Windows Phone 8 (based on Windows NT / Windows 8, for example, Nokia Lumia), which are used on a number of smartphones and their the Surface's flagship tablet, then attackers, perhaps, it makes no sense to create such a highly specialized malicious code, despite the fact that the market for devices running these operating systems is very small (compared to Android). The same applies to iOS, but in this case, attackers are much more difficult to distribute malware, due to the limitations imposed by the App Store for iOS digital distribution center. No application can be downloaded to the App Store without a strict preliminary check.
Microsoft uses the Windows Store and Windows Phone Store approaches similar to Apple security of digital content. Windows Store is used as a platform for digital distribution of applications for Windows 8 / 8.1, and Windows Phone Store for Windows Phone 7 and 8. Applications hosted there must comply with certain security rules and be pre-tested. Thus, users of these platforms are more secure due to its novelty and safety rules.

According to the data in the diagram above, this year, the ESET Antivirus Lab detected a significant increase in the Android malware families, reaching 79 families. The malware family is a combination of various malware modifications that can be correlated into one group for some common features of the code base and behavior. We also recorded that the countries with the highest growth of threats are Iran, China and Russia.
It should be noted that for Android, the percentage of so-called potentially unwanted software (PUA or greyware) is large. And the absolute majority of these applications are located in third-party application stores. Such software is not possible to strictly classify as malware, rather, it simply exposes the user to a certain degree of risk, since it contains questionable functions, for example, is adware or spyware. Android application stores are trying to protect users from malicious applications by implementing special rules and filtering or removing such applications for incoming complaints. However, some malware can avoid such checks and ensure its presence in the lists of applications of a store.
Last year marked the emergence of new types of malware for Android. Previously, such threats were typical for personal computers, but now we are seeing them on mobile devices. Some of them were found before, but did not show high activity as this year.
We expect an increase in the number of threat modifications for each of these types in the future. This is especially true of banking malware, which has become increasingly active because of the possibilities for the user to conduct financial transactions directly through the device using special applications for working with the online banking system. Users can perform similar operations through a browser that may be compromised by malicious code. As a result, attackers may have access to the data entered in the forms.
This year, we observed the emergence of the Hesperbot banking Trojan program, which uses the compromise of the user's mobile device in order to gain access to SMS confirmations (mTAN), which are a two-factor authentication mechanism for user operations. Hesperbot infects the user's computer, but if two-factor authentication is present when working with the online banking system, its methods of obtaining funds will be useless. Therefore, cybercriminals use a mobile component for this purpose.

Fig. Through a web injection in a browser on a compromised system, attackers convince the user to install a mobile application that will allow them to bypass the two-factor mTAN authentication during the transaction. [The message is translated from English, used in Win32 / Hesperbot ].
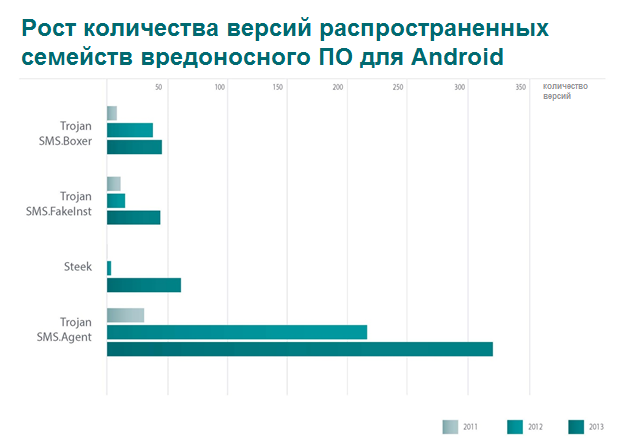
Above, the graph shows statistics on the growth in the number of versions or modifications of common malware families for Android. Still the most relevant family is the Trojan program SMS.Agent, attackers use it to covertly send paid SMS-messages and to sign the user to paid services. In 2013, this family underwent a significant increase in versions, with a total of 324 versions recorded. For comparison, in 2012, 214 versions of it were discovered. The dominant family of new versions is also the Steek family.
Remote code execution as the most effective method of malware delivery.
Last year, Microsoft fixed a large number of vulnerabilities for Windows and its components, as well as for Office. Some of these vulnerabilities were used by hackers to deliver malicious code before the fix was released. As a rule, most of them were focused on certain flaws in Internet Explorer.
The outgoing year was marked by the appearance of 0day vulnerabilities, which, first of all, were used in targeted attacks. This is a kind of trend of the past year, the attackers carry out the development of exploits not for the spontaneous spread of malicious code, but use them in attacks on specific users, while pursuing certain goals.
The following statistics show Microsoft patched vulnerabilities in patch tuesday for this year.

Vulnerabilities exploited at the time of closure are marked in red.
The table below provides more detailed information on vulnerabilities that were in-the-wild exploited in the past year (until the release of the corresponding patch, 0day).
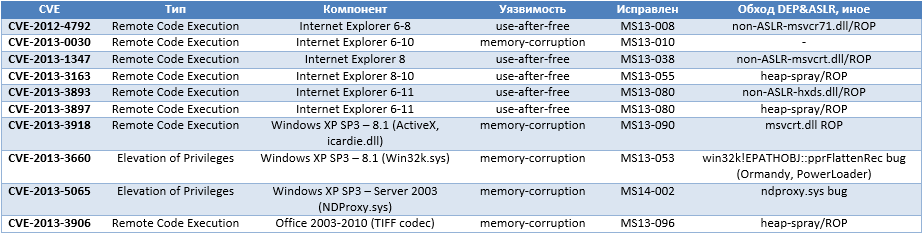
As we see, attackers can use some system libraries compiled without ASLR support to build stable ROP gadgets and bypass ASLR. One such example is the Office 2007-2010 hxds.dll library, which is compiled without ASLR support. As part of the December patch tuesday, the company closed this mistake (called Security Feature Bypass) using MS13-106 , providing Windows users who work with this version of Office with the proper level of protection.

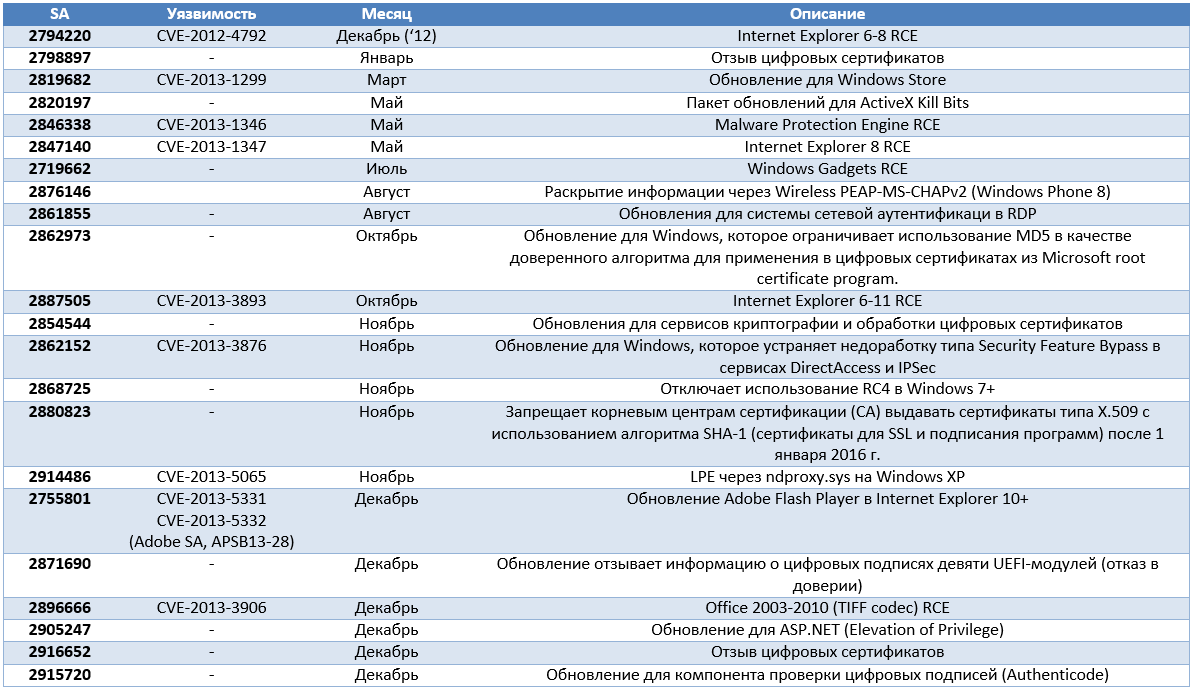
A list of Security Advisory issued last year.
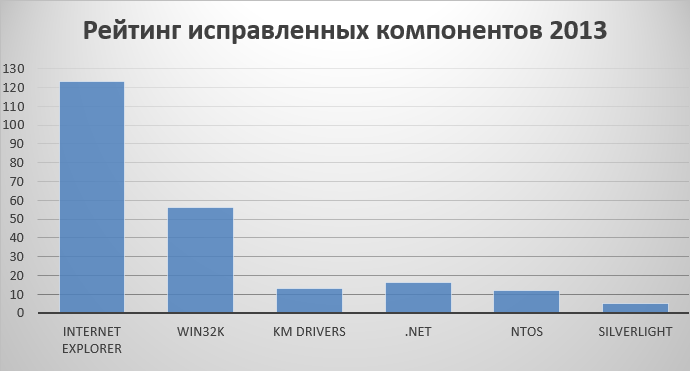
Below is the rating of the most fixable components in Windows for 2013. Note that the currently supported MS versions of the OS are Windows from XP SP3 / x64 XP SP2 to Windows 8.1 / RT 8.1.
The same in comparison with Office (2003 - 2013 for Windows).
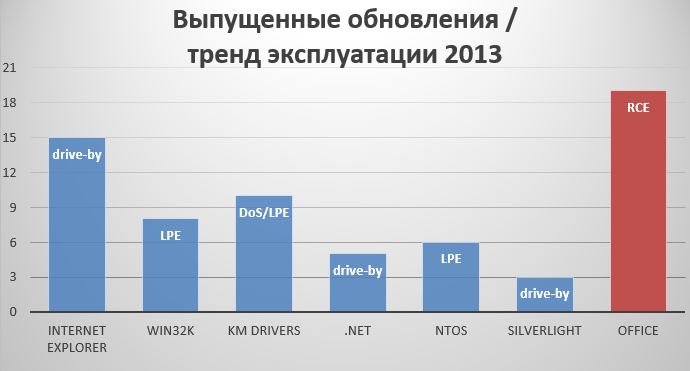
Drive-by download is the main method of stealthily delivering malicious code by redirecting the user to the pages of exploit kits.
Local Privelege Escalation (LPE, Elevation of Privelege) is a method of obtaining maximum system privileges, usually associated with running the kernel mode code bypassing the OS restrictions imposed on user-mode restriction.
Remote Code Execution (RCE) - remote code execution, used, for example, in drive-by, but in this case can be activated not only through a web page.
The trend by released updates shows that products such as the Internet Explorer browser, .NET components and the Silverlight browser plugin are used by attackers for remote code execution, and in most cases this can happen through the browser. The attackers use a specially prepared web page with malicious content to install this or that malicious code on the user's computer. In this scenario of using Internet Explorer, the use of the "Protected mode" technology of the browser, as well as the sandboxing technology "Advanced Protected Mode" is an important condition for ensuring your security for networking.
We note that the use of sandboxing technologies for browsers has long been a requirement for ensuring an appropriate level of security for users. It is extremely difficult to circumvent such a mode of operation of the browser and forces the attackers to use other methods to enhance their rights in the system. Other methods are the development of LPE-exploits that will work in conjunction with an exploit that causes remote code execution. Such an approach is necessary for attackers, since having entered the browser through the RCE vulnerability, the shell code remains powerless in performing any system operations, since the browser process runs at low Integrity Level and with many prohibited privileges. A good example of this practice is the demonstrated method of exploiting Google Chrome by MWR Labs on Pwn2Own 2013 , bypassing the restrictions of the sandbox mode through a vulnerability in win32k.sys.

Fig. Internet Explorer 11 with sandboxing mode settings (optimal use on Windows 8 / 8.1 x64).
Vulnerabilities in Office suite applications can also be used by attackers to remotely install malicious code. From the updates for Office released this year, it is clear that most of them were aimed at eliminating vulnerabilities such as Remote Code Execution. In this scenario, the attackers form a specially prepared Office file, for example, a .doc Word file and send it with a phishing email to the victim's address. The message must be convincing for the user to read it and go to the attachment and open it. After opening such a file, malware will be installed on the vulnerable version of Office.
Note that the latest version of Word 2013, as well as Outlook 2013, when working with Word (opening attachments), use persistent sandboxing mechanisms that prevent the application from performing potentially unsafe functions. For example, Outlook starts the Word process at low Integrity Level and with privileges disabled, which allows you to limit potential shellcode from performing system operations.
OS components that work in kernel mode: the Windows subsystem driver - win32k.sys, system drivers (KM drivers) and the ntoskrnl kernel (NTOS), are used by attackers to raise their privileges in the system, i.e., to execute code in the kernel mode bypassing the limitations of the OS. This year the win32k.sys driver was especially notable, in which more than fifty vulnerabilities were closed.
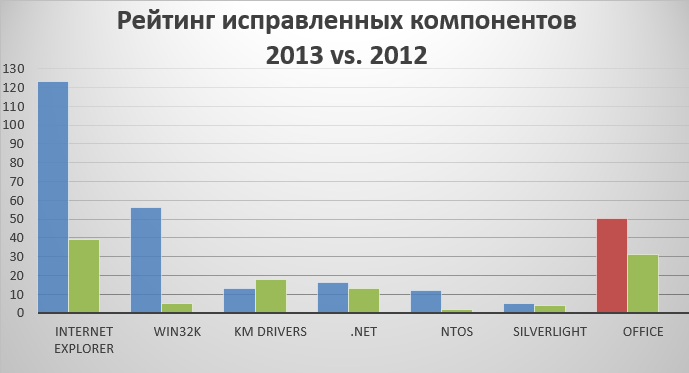
It is obvious that in 2013 the company closed many more vulnerabilities than in 2012. This trend is most clearly evident for the Windows subsystem driver Win32k.sys and Internet Explorer. In October, the company released a new Windows 8.1 operating system, as well as Internet Explorer 11.
OS Prevention
Last year showed that Microsoft paid attention to security technologies to counter the exploit. Three major innovations were aimed at protecting against memory allocation on a zero page, deleting pointers to different ntdll functions from PEB (ASLR bypass mitigation), and prohibiting the provision of information about kernel pointers for untrusted applications on Windows 8.1 (KASLR bypass mitigations).
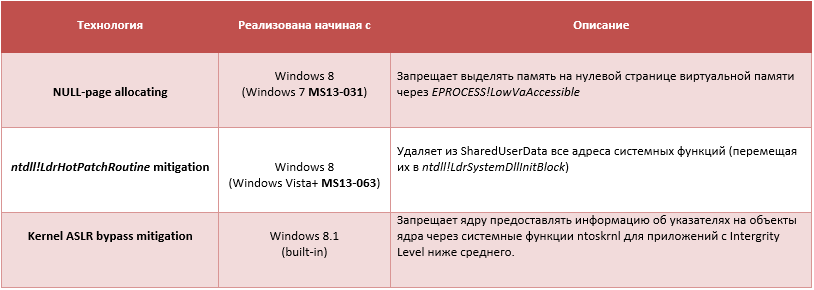
Allocating memory on a zero page (using ZwAllocateVirtualMemory ) made life easier for attackers, including if they are interested in increasing their privileges in the system. After allocating such a section of memory, you need a vulnerable driver that, when passing certain parameters to it, will be able to execute code at this address (bug).
The following features are available in Internet Explorer as protection against exploitation. The last point is the fact that all the system files compiled by MS for Windows 8 support the resistant HEASLR .

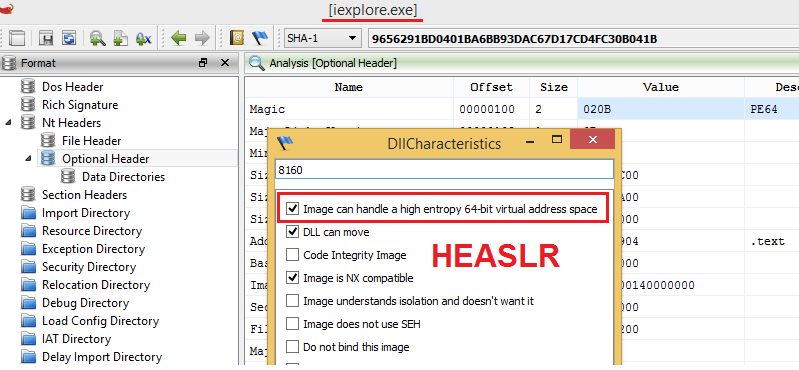
Fig. System files on Windows 8 x64 + are compiled with support for enhanced ASLR - High Entropy ASLR, to minimize the likelihood of its bypass.
Windows XP - the last chord
Last year was the last year in which Microsoft supported the latest editions of Windows XP SP3 and Windows XP x64 SP2. Despite the recommendations of Microsoft and various security specialists, who called on users to abandon this outdated and extremely insecure OS for a long time, today a large number of users still use it. According to Net Applications, Windows XP is used by almost 30% of computers.

Fig. Statistics of OS usage on computers according to Net Applications .
In April 2014, the company will abandon support for Windows XP SP3 and Windows XP x64 SP2 (support for Windows XP & SP1 & SP2, Windows XP x64 & SP1 has already been completed) and thus completely closes the cycle of supporting the code base and OS products that are based on Windows XP. For users, in the first place, this will mean the fact that they will lose security and other updates that Microsoft is guaranteed to issue every second Tuesday of the month (so-called patch tuesday) or unscheduled, as well as instructions in the Security Advisory (SA) or workaround in case of detection of exploited vulnerabilities in the OS (the company reserves the right to publish or not this information).
A good example of such a vulnerability for Windows XP, the fix of which the company postponed for 2014, is CVE-2013-5065. Due to the support of Windows XP until April, Microsoft fixes it in the January update set as the Important update MS14-002 (later, after April, such vulnerabilities will not be fixed).
CVE-2013-5065 became known at the end of November from SA 2914486 . The vulnerability is present in the version of the ndproxy.sys driver that comes with Windows XP and Windows Server 2003, it allows attackers to elevate their privileges to the system level and, through circumvention of user mode restrictions, execute their code in kernel mode (Local Privilege Escalation, LPE) through sending a specially crafted request (IOCTL) to the ndproxy.sys driver.
In order to protect users who still continue to use Windows XP SP3, Microsoft releases the free tool EMET (v 4.1 current version). EMET helps the user to protect the OS from various actions of exploits through which attackers try to compromise the system and run malicious code there. With reference to Windows XP SP3, EMET will help introduce the following features, which will greatly enhance the immunity of the system.
EMET mechanisms are applied to processes, so the user is free to select specific processes in the list in order to apply security features to them. By default, it protects the following processes that are critical to remote operation:

Fig. EMET main window with maximum settings, in the process list, Google Chrome browser as protected.
SA recommendations often contain a reference to EMET and its options for quickly remedying the situation and protecting against a particular vulnerability even before the official update. Most of these settings are available from the user interface of the tool, but there are also those that are not there. For example, exploits often use heap spraying as a means of bypassing ASLR. In this scenario, the attackers know what value a particular register can take in an erroneous situation in the execution of a code (bug). Then they can only reserve a certain number of memory blocks that are adjacent to this address (spraying). Later, when provoking a situation of exploitation, the erroneous code will transfer control to one of the addresses that the attacker needs. The list of such addresses is listed in the registry key HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ EMET \ _settings _ \ {GUID}.This list is updated according to the recommendations of the SA (eg, see SA 2887505 ).
Conclusion
The past year has shown a high activity of various malicious code and intruders who use it. As we mentioned above, the number of targeted attacks this year has only increased, and a similar way of spreading malicious code is becoming more and more important among intruders. Remote code execution through exploits specifically detected for a particular attack is also a significant trend of the past year.

Despite the fact that Remote Code Execution vulnerabilities in popular software (browsers) play a significant role in the remote delivery of malicious content that attackers are interested in (the main drive-by trend), they often resort to much simpler methods of installing malicious objects into the system using human factor. The use of double extensions in files, a convincing phishing message, targeting certain people (including intelligence), fake file icons, documents with convincing content, all this makes up the arsenal of attackers who are interested in installing malicious code into the system of the alleged victim.
')

Fig. A typical example of using a double extension in a file name with an MS Word document icon inserted into an executable file. A reliable way to mislead the victim, because in the default settings, Windows Explorer hides the extension of files known to it.
As the experience of attackers from the APT1 group and other attacking groups who were engaged in industrial espionage showed, it is initially necessary to conduct minimal intelligence to identify the alleged victim and obtain information about her, for example. e-mail address. In the future, a convincing phishing message will be sent to this address.

Fig. An example of a phishing message that can be sent to the user's corporate mailbox, in order to compromise corporate information. The first thing that catches your eye is the use of a gmail mail account instead of a corporate one by a company manager.
This type of attack can be used not only for industrial espionage, but also in more local attacks against a specific company, for example, in order to obtain important information from competitors using malicious code.
Windows threats
This is not to say that the past year brought something fundamentally new for Windows. Turning on a computer in a botnet, stealing account data and online banking data, getting remote access to a computer (backdoor), blocking a computer for ransom (extortioner) are the main goals of cybercriminals who are interested in gaining material gain from compromised users. Below we provide statistics on some families of malicious code that were active in the past year.
File viruses are still quite active. This year, the three Win32 / Sality , Win32 / Ramnit and Win32 / Virut families steadily fell into the top ten world threats according to statistics from our ESET Live Grid telemetry system. Viruses compromise executable files on a user's computer and violate their integrity, and can also threaten the entire enterprise network if one of the computers contains at least one malicious file, because they can infect network drives of other computers on the network.

For Russia, the most topical malware is Win32 / Qhost , besides that it is in itself, first of all, targeted at Russian users (see the geography of distribution below), which clearly hints at its domestic roots. The Qhost code itself is quite simple and modifies the system hosts file to redirect the user to the phishing, advertising and malicious resources needed by attackers. Such redirects (clicks) are later monetized and bring actual profits to the attackers.

Generic HTML / IFrame detection is used to identify malicious elements of web pages. Often malicious iframes are used to redirect a user from a legitimate web page to malicious content or a set of exploits.


Fig. The geography of distribution of Qhost. Russia is the most affected region.
As can be seen in the diagram above, in Russia (and in the world) there is still a high activity of malicious programs that use .inf files to ensure their launch both from removable media and locally in the system. ESET antivirus products detect these malicious files under the general INF / Autorun family. Such an autorun mechanism is especially relevant for legacy OSs, since they have an autorun autorun mechanism enabled by default through Autorun files. For more information about disabling autorun using Autorun files on such OS see KB967715 .
The table below lists the vulnerabilities (0day at the time of operation), with which the attackers delivered malicious code. The past year 2013 can rightly be called the year of targeted attacks and watering hole attacks, for many of them the attackers specifically searched for a particular vulnerability and used it exclusively to attack a specific region or particular company. In particular, watering hole was used to compromise websites that were actively visited by alleged victims in different regions of the world. We believe that in 2014 this trend will become even more widespread.

This year, we repeatedly wrote about attacks on popular instant messengers such as Skype and Gtalk, as well as social networks, such as Facebook or Vkontakte. We will not repeat, but just note that attackers take advantage of persuasive phishing messages, supposedly trusted domains, in which there is a slip of the letter and a few link shortening services to lure users to follow a malicious link. To organize a large-scale spam mailing, attackers need to create auxiliary fake accounts in a particular service, use user accounts with reduced security settings, and also malicious code with the ability to inject their code into messengers ( Win32 / Rodpicom.C ) to send messages . Since the number of users of all these services is only increasing, we believe that we can expect this kind of attack in the next year.
Trends for Windows
- Attackers are increasingly resorting to using the capabilities of the Tor anonymous network to work with remote C & C servers. This year there are several new threats with such capabilities. For example, Win32 / Atrax.A , Win32 / Agent.PTA , Win32 / Napolar . Using Tor allows an attacker to be more invisible because it allows you to hide C & C information (IP address or domain). This is especially useful for hiding information from traffic analysis systems that collect information about incoming / outgoing traffic on the network of an enterprise. Through such logs, the security service can quickly detect the true malicious URL.
- The use of a distributed architecture in extortionists-cryptographers. On the example of Cryptolocker ( Win32 / Filecoder.BQ ), it became obvious that if you use the RSA-type public-key encryption algorithm for files (to encrypt the key of the symmetric algorithm that files are encrypted with), then the user will not have another opportunity to pay attackers for or lose your files. In December, we reported on the discovery of its new modification, which is called Cryptolocker 2.0 ( MSIL / Filecoder.D , MSIL / Filecoder.E ), see the table below. In addition, at the beginning of this year, information appeared about the new coder who uses a similar approach called the Prison Locker (Power Locker), a malware blog was reported on.
- The most popular malicious code from cybercriminals are tools that are used to steal various confidential information from online service accounts, as well as online banking information. We call these types of malware tools, since they contain several components, for example, mobile, which is used to bypass two-factor authentication in the form of SMS confirmation codes (mTAN). Such tools are a professional means of stealing money from users. These include, for example, Win32 / Qadars and Win32 / Spy.Hesperbot .
- Complicated malware as a way to extract large profits. An example of the infamous ZeroAccess family ( Win32 / Sirefef , Win64 / Sirefef ) shows that hiding its code deep in the system, using non-standard approaches to infecting files and targeting the x64 platform, which is increasingly replacing x32, allows you to achieve the maximum possible material benefit for intruders. According to estimates by Microsoft Digital Crimes Unit, which were involved in gaining control over this botnet, ZeroAccess infected about 2 million computers with an estimated monthly profit of $ 2.7 million.
- 64-bit threats. This year, a modification of the widely known file virus Expiro, which can infect 64-bit files ( Win64 / Expiro.A and Win64 / Expiro.B ), was discovered. Win64 / Expiro has a portable cross-platform body (x32-x64) and can infect both 32-bit and 64-bit files. In addition, many malware already have a 64-bit payload. It is obvious that cybercriminals are guided by very practical goals, as 64-bit operating systems in the world are becoming more and more.
More detailed information about the detected Cryptolocker modifications is given in the table below.

Mobile threats - the main trend of the year
In our last year's report, which was called “Overview of the main threats and trends in 2012”, we pointed to the rapid spread of malware for Android. For example, in 2012 compared to 2011, the number of malicious objects we detected increased 17 times.
We also predicted the rapid growth of new threats in 2013. Such a prediction really came true and this year we recorded the appearance of a large number of malicious programs for this platform.
It's no secret that Android is the most common platform for mobile devices. The statistics provided by Gartner for the second quarter of 2013 shows that Android has further strengthened its position in the mobile device market almost reaching 80%.

Fig. The percentage of mobile operating systems sold with corresponding devices in the second quarter of 2011, 2012 and 2013. (Gartner data).
Regarding Microsoft’s new mobile platforms - Windows RT (based on Windows 8, for example, Surface 2) and Windows Phone 8 (based on Windows NT / Windows 8, for example, Nokia Lumia), which are used on a number of smartphones and their the Surface's flagship tablet, then attackers, perhaps, it makes no sense to create such a highly specialized malicious code, despite the fact that the market for devices running these operating systems is very small (compared to Android). The same applies to iOS, but in this case, attackers are much more difficult to distribute malware, due to the limitations imposed by the App Store for iOS digital distribution center. No application can be downloaded to the App Store without a strict preliminary check.
Microsoft uses the Windows Store and Windows Phone Store approaches similar to Apple security of digital content. Windows Store is used as a platform for digital distribution of applications for Windows 8 / 8.1, and Windows Phone Store for Windows Phone 7 and 8. Applications hosted there must comply with certain security rules and be pre-tested. Thus, users of these platforms are more secure due to its novelty and safety rules.

According to the data in the diagram above, this year, the ESET Antivirus Lab detected a significant increase in the Android malware families, reaching 79 families. The malware family is a combination of various malware modifications that can be correlated into one group for some common features of the code base and behavior. We also recorded that the countries with the highest growth of threats are Iran, China and Russia.
It should be noted that for Android, the percentage of so-called potentially unwanted software (PUA or greyware) is large. And the absolute majority of these applications are located in third-party application stores. Such software is not possible to strictly classify as malware, rather, it simply exposes the user to a certain degree of risk, since it contains questionable functions, for example, is adware or spyware. Android application stores are trying to protect users from malicious applications by implementing special rules and filtering or removing such applications for incoming complaints. However, some malware can avoid such checks and ensure its presence in the lists of applications of a store.
Last year marked the emergence of new types of malware for Android. Previously, such threats were typical for personal computers, but now we are seeing them on mobile devices. Some of them were found before, but did not show high activity as this year.
- Downloader (downloader): tries to download other malware files from the Internet and install them on the device.
- Dropper: installs other threats to the device when it starts, threats are in the file of the dropper itself.
- Clicker: designed to generate traffic to sites through an artificial increase in the number of clicks received on infected devices.
- Banking malware: specializes in stealing user confidential information that is used to conduct online banking transactions.
We expect an increase in the number of threat modifications for each of these types in the future. This is especially true of banking malware, which has become increasingly active because of the possibilities for the user to conduct financial transactions directly through the device using special applications for working with the online banking system. Users can perform similar operations through a browser that may be compromised by malicious code. As a result, attackers may have access to the data entered in the forms.
This year, we observed the emergence of the Hesperbot banking Trojan program, which uses the compromise of the user's mobile device in order to gain access to SMS confirmations (mTAN), which are a two-factor authentication mechanism for user operations. Hesperbot infects the user's computer, but if two-factor authentication is present when working with the online banking system, its methods of obtaining funds will be useless. Therefore, cybercriminals use a mobile component for this purpose.

Fig. Through a web injection in a browser on a compromised system, attackers convince the user to install a mobile application that will allow them to bypass the two-factor mTAN authentication during the transaction. [The message is translated from English, used in Win32 / Hesperbot ].

Above, the graph shows statistics on the growth in the number of versions or modifications of common malware families for Android. Still the most relevant family is the Trojan program SMS.Agent, attackers use it to covertly send paid SMS-messages and to sign the user to paid services. In 2013, this family underwent a significant increase in versions, with a total of 324 versions recorded. For comparison, in 2012, 214 versions of it were discovered. The dominant family of new versions is also the Steek family.
Remote code execution as the most effective method of malware delivery.
Last year, Microsoft fixed a large number of vulnerabilities for Windows and its components, as well as for Office. Some of these vulnerabilities were used by hackers to deliver malicious code before the fix was released. As a rule, most of them were focused on certain flaws in Internet Explorer.
The outgoing year was marked by the appearance of 0day vulnerabilities, which, first of all, were used in targeted attacks. This is a kind of trend of the past year, the attackers carry out the development of exploits not for the spontaneous spread of malicious code, but use them in attacks on specific users, while pursuing certain goals.
The following statistics show Microsoft patched vulnerabilities in patch tuesday for this year.

Vulnerabilities exploited at the time of closure are marked in red.
The table below provides more detailed information on vulnerabilities that were in-the-wild exploited in the past year (until the release of the corresponding patch, 0day).

As we see, attackers can use some system libraries compiled without ASLR support to build stable ROP gadgets and bypass ASLR. One such example is the Office 2007-2010 hxds.dll library, which is compiled without ASLR support. As part of the December patch tuesday, the company closed this mistake (called Security Feature Bypass) using MS13-106 , providing Windows users who work with this version of Office with the proper level of protection.

A list of Security Advisory issued last year.

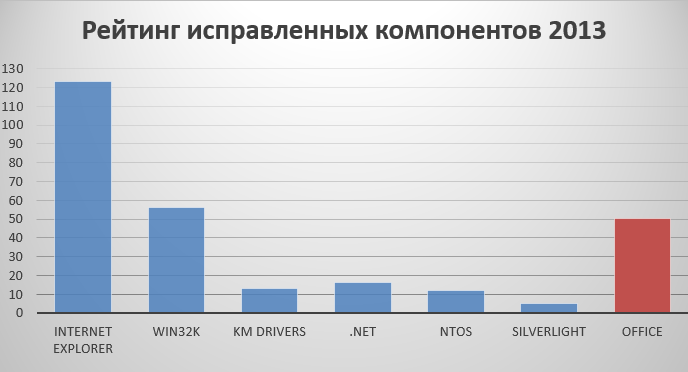
Below is the rating of the most fixable components in Windows for 2013. Note that the currently supported MS versions of the OS are Windows from XP SP3 / x64 XP SP2 to Windows 8.1 / RT 8.1.

The same in comparison with Office (2003 - 2013 for Windows).


Drive-by download is the main method of stealthily delivering malicious code by redirecting the user to the pages of exploit kits.
Local Privelege Escalation (LPE, Elevation of Privelege) is a method of obtaining maximum system privileges, usually associated with running the kernel mode code bypassing the OS restrictions imposed on user-mode restriction.
Remote Code Execution (RCE) - remote code execution, used, for example, in drive-by, but in this case can be activated not only through a web page.
The trend by released updates shows that products such as the Internet Explorer browser, .NET components and the Silverlight browser plugin are used by attackers for remote code execution, and in most cases this can happen through the browser. The attackers use a specially prepared web page with malicious content to install this or that malicious code on the user's computer. In this scenario of using Internet Explorer, the use of the "Protected mode" technology of the browser, as well as the sandboxing technology "Advanced Protected Mode" is an important condition for ensuring your security for networking.
We note that the use of sandboxing technologies for browsers has long been a requirement for ensuring an appropriate level of security for users. It is extremely difficult to circumvent such a mode of operation of the browser and forces the attackers to use other methods to enhance their rights in the system. Other methods are the development of LPE-exploits that will work in conjunction with an exploit that causes remote code execution. Such an approach is necessary for attackers, since having entered the browser through the RCE vulnerability, the shell code remains powerless in performing any system operations, since the browser process runs at low Integrity Level and with many prohibited privileges. A good example of this practice is the demonstrated method of exploiting Google Chrome by MWR Labs on Pwn2Own 2013 , bypassing the restrictions of the sandbox mode through a vulnerability in win32k.sys.

Fig. Internet Explorer 11 with sandboxing mode settings (optimal use on Windows 8 / 8.1 x64).
Vulnerabilities in Office suite applications can also be used by attackers to remotely install malicious code. From the updates for Office released this year, it is clear that most of them were aimed at eliminating vulnerabilities such as Remote Code Execution. In this scenario, the attackers form a specially prepared Office file, for example, a .doc Word file and send it with a phishing email to the victim's address. The message must be convincing for the user to read it and go to the attachment and open it. After opening such a file, malware will be installed on the vulnerable version of Office.
Note that the latest version of Word 2013, as well as Outlook 2013, when working with Word (opening attachments), use persistent sandboxing mechanisms that prevent the application from performing potentially unsafe functions. For example, Outlook starts the Word process at low Integrity Level and with privileges disabled, which allows you to limit potential shellcode from performing system operations.
OS components that work in kernel mode: the Windows subsystem driver - win32k.sys, system drivers (KM drivers) and the ntoskrnl kernel (NTOS), are used by attackers to raise their privileges in the system, i.e., to execute code in the kernel mode bypassing the limitations of the OS. This year the win32k.sys driver was especially notable, in which more than fifty vulnerabilities were closed.

It is obvious that in 2013 the company closed many more vulnerabilities than in 2012. This trend is most clearly evident for the Windows subsystem driver Win32k.sys and Internet Explorer. In October, the company released a new Windows 8.1 operating system, as well as Internet Explorer 11.
OS Prevention
Last year showed that Microsoft paid attention to security technologies to counter the exploit. Three major innovations were aimed at protecting against memory allocation on a zero page, deleting pointers to different ntdll functions from PEB (ASLR bypass mitigation), and prohibiting the provision of information about kernel pointers for untrusted applications on Windows 8.1 (KASLR bypass mitigations).

Allocating memory on a zero page (using ZwAllocateVirtualMemory ) made life easier for attackers, including if they are interested in increasing their privileges in the system. After allocating such a section of memory, you need a vulnerable driver that, when passing certain parameters to it, will be able to execute code at this address (bug).
The following features are available in Internet Explorer as protection against exploitation. The last point is the fact that all the system files compiled by MS for Windows 8 support the resistant HEASLR .


Fig. System files on Windows 8 x64 + are compiled with support for enhanced ASLR - High Entropy ASLR, to minimize the likelihood of its bypass.
Windows XP - the last chord
Last year was the last year in which Microsoft supported the latest editions of Windows XP SP3 and Windows XP x64 SP2. Despite the recommendations of Microsoft and various security specialists, who called on users to abandon this outdated and extremely insecure OS for a long time, today a large number of users still use it. According to Net Applications, Windows XP is used by almost 30% of computers.

Fig. Statistics of OS usage on computers according to Net Applications .
In April 2014, the company will abandon support for Windows XP SP3 and Windows XP x64 SP2 (support for Windows XP & SP1 & SP2, Windows XP x64 & SP1 has already been completed) and thus completely closes the cycle of supporting the code base and OS products that are based on Windows XP. For users, in the first place, this will mean the fact that they will lose security and other updates that Microsoft is guaranteed to issue every second Tuesday of the month (so-called patch tuesday) or unscheduled, as well as instructions in the Security Advisory (SA) or workaround in case of detection of exploited vulnerabilities in the OS (the company reserves the right to publish or not this information).
A good example of such a vulnerability for Windows XP, the fix of which the company postponed for 2014, is CVE-2013-5065. Due to the support of Windows XP until April, Microsoft fixes it in the January update set as the Important update MS14-002 (later, after April, such vulnerabilities will not be fixed).
CVE-2013-5065 became known at the end of November from SA 2914486 . The vulnerability is present in the version of the ndproxy.sys driver that comes with Windows XP and Windows Server 2003, it allows attackers to elevate their privileges to the system level and, through circumvention of user mode restrictions, execute their code in kernel mode (Local Privilege Escalation, LPE) through sending a specially crafted request (IOCTL) to the ndproxy.sys driver.
In order to protect users who still continue to use Windows XP SP3, Microsoft releases the free tool EMET (v 4.1 current version). EMET helps the user to protect the OS from various actions of exploits through which attackers try to compromise the system and run malicious code there. With reference to Windows XP SP3, EMET will help introduce the following features, which will greatly enhance the immunity of the system.
- Enable ASLR .
- Force DEP on for the entire system.
- Enable the ability to protect against rewriting pointers in SEH at the OS level - SEHOP.
- Use standard EMET features to protect against exploits.
EMET mechanisms are applied to processes, so the user is free to select specific processes in the list in order to apply security features to them. By default, it protects the following processes that are critical to remote operation:
- Adobe Reader (from PDF operation);
- MS Office (including Excel, Word, Access, Outlook and others from exploitation through email attachments);
- Java (from exploitation through the browser);
- Internet Explorer Browser.

Fig. EMET main window with maximum settings, in the process list, Google Chrome browser as protected.
SA recommendations often contain a reference to EMET and its options for quickly remedying the situation and protecting against a particular vulnerability even before the official update. Most of these settings are available from the user interface of the tool, but there are also those that are not there. For example, exploits often use heap spraying as a means of bypassing ASLR. In this scenario, the attackers know what value a particular register can take in an erroneous situation in the execution of a code (bug). Then they can only reserve a certain number of memory blocks that are adjacent to this address (spraying). Later, when provoking a situation of exploitation, the erroneous code will transfer control to one of the addresses that the attacker needs. The list of such addresses is listed in the registry key HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ EMET \ _settings _ \ {GUID}.This list is updated according to the recommendations of the SA (eg, see SA 2887505 ).
Conclusion
The past year has shown a high activity of various malicious code and intruders who use it. As we mentioned above, the number of targeted attacks this year has only increased, and a similar way of spreading malicious code is becoming more and more important among intruders. Remote code execution through exploits specifically detected for a particular attack is also a significant trend of the past year.
Source: https://habr.com/ru/post/209694/
All Articles