Why not use RJS
JQuery has a built-in feature - if the server responds with a content-type = text / javascript library will execute the answer automatically.
Therefore, the tactic of “answer with a line of Javascript instead of the correct JSON that will have to be processed” is quite common in the rails.
')
Those. The response from index.js.erb may look like this:
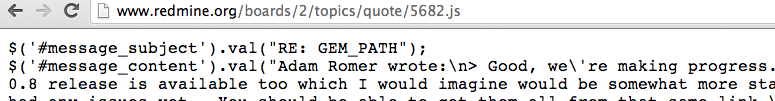
And here is the problem - if I insert a script tag with src = "/ profile.js" on a third-party server, then this request will return a valid javascript that will be executed in the context of my page. To steal data, you only need to redeclare the function $ = {html: function (data) {LEAK (data)}};
Bug was present for example at Gitlab, Basecamp, Redmine, Spree, Diaspora. He could merge the full form, which in turn stores input type = hidden name = authenticity_token (user csrf_token).
This bug is essentially a reincarnation of JSONP merging, but less obvious to developers. If you have * .js. * Files in the / app / views folder, you are most likely vulnerable. Bug fixed in new version of RoR.
jQuery.ajaxSetup({ accepts: { script: "text/javascript, application/javascript, application/ecmascript, application/x-ecmascript" }, contents: { script: /(?:java|ecma)script/ }, converters: { "text script": function( text ) { jQuery.globalEval( text ); return text; } } }); Therefore, the tactic of “answer with a line of Javascript instead of the correct JSON that will have to be processed” is quite common in the rails.
')
Those. The response from index.js.erb may look like this:
$('#content').html('Hello, id123123')

And here is the problem - if I insert a script tag with src = "/ profile.js" on a third-party server, then this request will return a valid javascript that will be executed in the context of my page. To steal data, you only need to redeclare the function $ = {html: function (data) {LEAK (data)}};
Bug was present for example at Gitlab, Basecamp, Redmine, Spree, Diaspora. He could merge the full form, which in turn stores input type = hidden name = authenticity_token (user csrf_token).
This bug is essentially a reincarnation of JSONP merging, but less obvious to developers. If you have * .js. * Files in the / app / views folder, you are most likely vulnerable. Bug fixed in new version of RoR.
Source: https://habr.com/ru/post/209618/
All Articles