DNS server spoofing. be careful
Hi, habrosoobschestvu.
I want to share with you the case that recently happened to me. I hope this article will be able to protect someone from the loss of private data and even money.
It all started with the fact that one of my friends complained that the mobile version of VKontakte was closed. I was very surprised, because I did not see any objective reasons for this, and I hurried to check whether this was true. The transition to m.vk.com dispelled my doubts - everything worked. During the inquiry of a friend, it turned out that he had m.vk.com reporting that the entire service had moved to a mobile application and offered to download this application. Obviously, this is naughty viruses, I thought, and asked a friend to give a look at his car.
First of all, I personally looked at this fake, everything looked very plausible: it was well designed and the URL was exactly m.vk.com. So, one could really think that the mobile version of the VC was closed.
Well what could it be? Of course, hosts! Opening it, I was ready to save a friend from a terrible misfortune, but ... there was nothing in the file, except for standard comments. There was also no other, hidden hosts, as is sometimes the case. A careful study of the running processes did not give anything interesting, absolutely like the googling of the application offered for download. I became thoughtful.
')
My thought processes were interrupted by an acquaintance, saying that the same story happens when I try to log in to the VC from the phone. It was a clue. The phone was connected to a home wi-fi point, the same as the problem computer. Asking a friend to log in to the VC from the mobile Internet, disconnecting from wi-fi, I dismissed the option of infecting the phone - the real version opened. There was only one conclusion - the router is infected.
Turning to 192.168.1.1, I asked a friend for the login and password from the router and heard in response ... admin: admin ! What?! How could you not change the password on the router distributing wi-fi? Striking irresponsibility! A friend shrugged.
Checking the DNS, I found the following:
The second address is well known to me, it’s Google’s DNS, but I’ve never met the first one. He was not even from our region.
Nothing, except to go to this address , did not occur. A fake QIWI appeared before me, with it, again, of excellent quality. (By the way, he is still there).
I deleted this address from DNS, replacing it with the standard one for our region, changed the password on the router and restarted it. After that, everything worked as expected. After listening to the thanks of a friend, I decided to tackle the fake more closely.
2ip.ru said that the address is Ukrainian and showed what range it is from. The range was small, so it would be logical to scan it. No sooner said than done. Half an hour of fuss and another interesting address was discovered. Here it is: 176.102.38.39 .
Now profanity is located there, but when I found it, there was a form called “Fake admin panel” and login and password fields. You never know? I thought, and entered admin: admin . What do you think happened?
I found myself in the admin, with logs of all entries in the fakes fakes scam! Amazingly, they got caught on their own method of infection.
I admit, at first I thought it was a hanipot, and tried to enter one of the QIWI wallets from the log. The data was correct, on the account of the wallet was about 1000 rubles. So this is not a hanipot. I went out of my wallet, and began to study the admin panel.
In the Stat section you could see how many entrances were logged. The situation is as follows:
Good results (not counting btc), right?
Separately, it is necessary to note the QIWI log, apparently, for the sake of it all that was done. The QIWI log displayed not only the login, password and IP, but also the balance at the time of entry, as well as whether the SMS confirmation for payments was turned on (which is amazing, in most of the accounts it was turned off). Such a log says that after logging in via a fake, a person was authorized on a real QIWI, and the poor fellow didn’t even suspect a trick.
In the upper right corner, the number of records that have not yet been archived is displayed (I note that these records were replenished very quickly).
And below (in the picture it is not visible), there were buttons for convenient export of non-archived logs to a txt file and a button for restoring all records from the archive.
Feeling that my time is running out, I restored all the records from the QIWI archive and downloaded them myself. I wanted to do the same with the rest of the services, but I could not. Because the next request I saw an error 403, and then what is there now.
I cleared the resulting file from identical records and checked if my friend’s wallet was there. A lucky friend, his wallet in the hands of scam did not get.
This file (without passwords, of course) can check if your wallet is there.
Be careful, evil, evil does not sleep!
PS: Apparently, I now have to give up the evening walks: D
I want to share with you the case that recently happened to me. I hope this article will be able to protect someone from the loss of private data and even money.
Outset
It all started with the fact that one of my friends complained that the mobile version of VKontakte was closed. I was very surprised, because I did not see any objective reasons for this, and I hurried to check whether this was true. The transition to m.vk.com dispelled my doubts - everything worked. During the inquiry of a friend, it turned out that he had m.vk.com reporting that the entire service had moved to a mobile application and offered to download this application. Obviously, this is naughty viruses, I thought, and asked a friend to give a look at his car.
First of all, I personally looked at this fake, everything looked very plausible: it was well designed and the URL was exactly m.vk.com. So, one could really think that the mobile version of the VC was closed.
Well what could it be? Of course, hosts! Opening it, I was ready to save a friend from a terrible misfortune, but ... there was nothing in the file, except for standard comments. There was also no other, hidden hosts, as is sometimes the case. A careful study of the running processes did not give anything interesting, absolutely like the googling of the application offered for download. I became thoughtful.
')
My thought processes were interrupted by an acquaintance, saying that the same story happens when I try to log in to the VC from the phone. It was a clue. The phone was connected to a home wi-fi point, the same as the problem computer. Asking a friend to log in to the VC from the mobile Internet, disconnecting from wi-fi, I dismissed the option of infecting the phone - the real version opened. There was only one conclusion - the router is infected.
All the fault of irresponsibility
Turning to 192.168.1.1, I asked a friend for the login and password from the router and heard in response ... admin: admin ! What?! How could you not change the password on the router distributing wi-fi? Striking irresponsibility! A friend shrugged.
Checking the DNS, I found the following:
176.102.38.70
8.8.8.8
The second address is well known to me, it’s Google’s DNS, but I’ve never met the first one. He was not even from our region.
Nothing, except to go to this address , did not occur. A fake QIWI appeared before me, with it, again, of excellent quality. (By the way, he is still there).
I deleted this address from DNS, replacing it with the standard one for our region, changed the password on the router and restarted it. After that, everything worked as expected. After listening to the thanks of a friend, I decided to tackle the fake more closely.
What a twist
2ip.ru said that the address is Ukrainian and showed what range it is from. The range was small, so it would be logical to scan it. No sooner said than done. Half an hour of fuss and another interesting address was discovered. Here it is: 176.102.38.39 .
Now profanity is located there, but when I found it, there was a form called “Fake admin panel” and login and password fields. You never know? I thought, and entered admin: admin . What do you think happened?
I found myself in the admin, with logs of all entries in the fakes fakes scam! Amazingly, they got caught on their own method of infection.
I admit, at first I thought it was a hanipot, and tried to enter one of the QIWI wallets from the log. The data was correct, on the account of the wallet was about 1000 rubles. So this is not a hanipot. I went out of my wallet, and began to study the admin panel.
In the rear of the enemy
Decorated admin was tastefully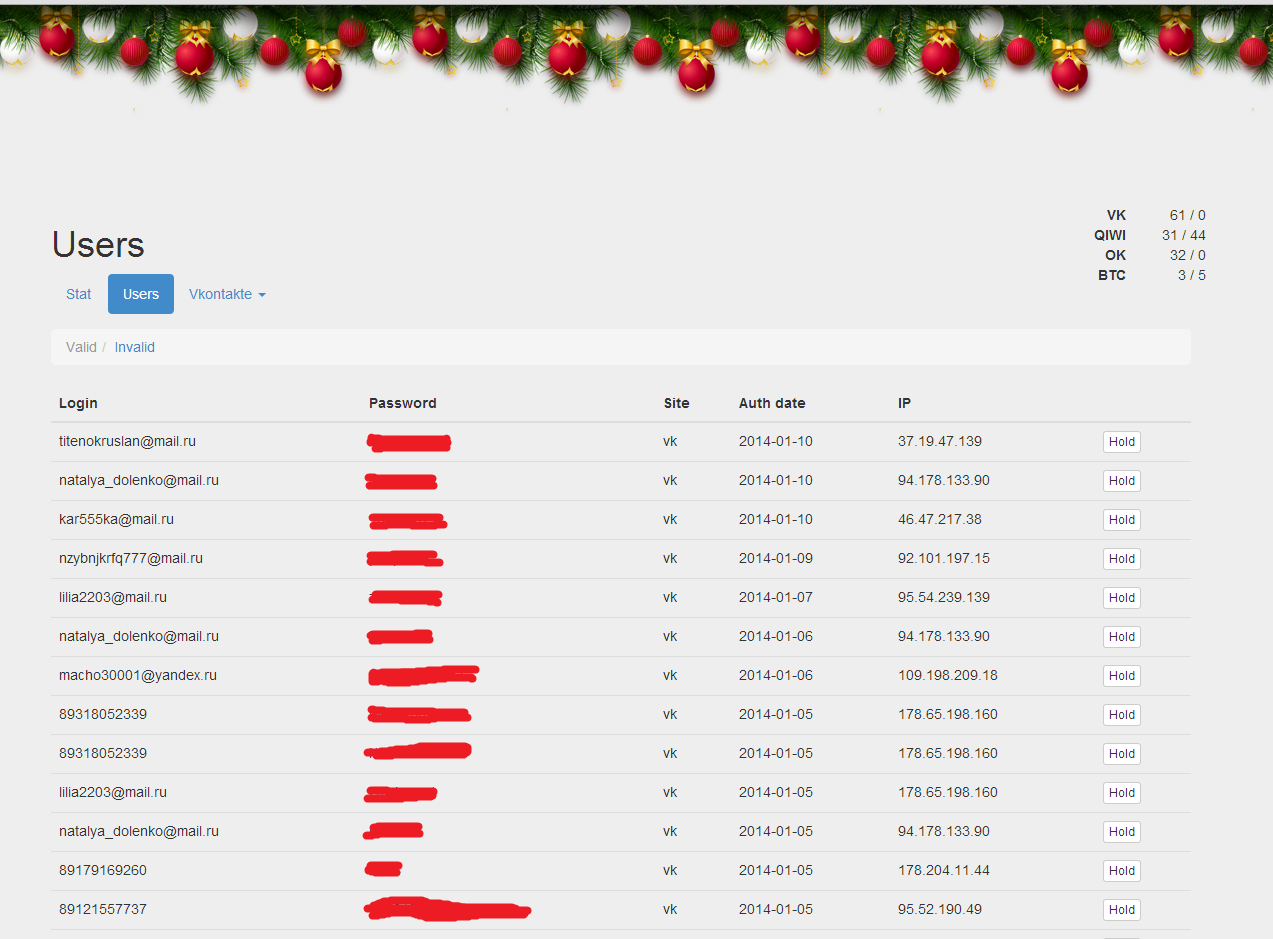
(these toys from above were moving when you put a rat on them, and they made a sound (and it was not a flash drive))

(these toys from above were moving when you put a rat on them, and they made a sound (and it was not a flash drive))
In the Stat section you could see how many entrances were logged. The situation is as follows:
VK ~ 72000
OK ~ 45000
QIWI ~ 9000
BTC - 5
Good results (not counting btc), right?
Separately, it is necessary to note the QIWI log, apparently, for the sake of it all that was done. The QIWI log displayed not only the login, password and IP, but also the balance at the time of entry, as well as whether the SMS confirmation for payments was turned on (which is amazing, in most of the accounts it was turned off). Such a log says that after logging in via a fake, a person was authorized on a real QIWI, and the poor fellow didn’t even suspect a trick.
In the upper right corner, the number of records that have not yet been archived is displayed (I note that these records were replenished very quickly).
And below (in the picture it is not visible), there were buttons for convenient export of non-archived logs to a txt file and a button for restoring all records from the archive.
Feeling that my time is running out, I restored all the records from the QIWI archive and downloaded them myself. I wanted to do the same with the rest of the services, but I could not. Because the next request I saw an error 403, and then what is there now.
results
I cleared the resulting file from identical records and checked if my friend’s wallet was there. A lucky friend, his wallet in the hands of scam did not get.
This file (without passwords, of course) can check if your wallet is there.
offtop
For the sake of experiment, scanned your subnet. I found 8 routers, 3 of which have a standard password.
Be careful, evil, evil does not sleep!
PS: Apparently, I now have to give up the evening walks: D
Source: https://habr.com/ru/post/209486/
All Articles