Microsoft and Adobe released a set of updates, January 2014
Microsoft has released a series of updates for its products, which cover 6 unique vulnerabilities (4 fixes with the Important status). This is the first patch tuesday this year and we call it "light patch tuesday", because it does not contain any critical updates and no updates for the Internet Explorer browser. A detailed report on closed vulnerabilities, product components and their versions can be found on the corresponding page of security bulletins . The fixes are focused on the operating system, Office, and Microsoft Dynamics AX. You need a reboot to apply updates.

The MS14-002 update closes the vulnerability CVE-2013-5065 known from last year ( SA 2914486 ) in the ndproxy.sys driver version, which comes in Windows XP and Windows Server 2003. The attackers used a special request from the driver via the IOCTL interface for execute your code in kernel mode (user-mode restrictions). A special PDF document was used to deliver this exploit, which exploits the vulnerability in an outdated version of Adobe Reader and is used to overcome sandboxing limitations (Adobe Reader sandbox bypass). A malicious exploit document is detected by ESET as PDF / Exploit.CVE-2013-5065.A.
')
Update MS14-001 closes three vulnerabilities in all versions of Microsoft Word 2003-2007-2010-2013-2013 RT. Fixed vulnerabilities CVE-2014-0258, CVE-2014-0259, CVE-2014-0260 are of the Remote Code Execution (memory-corruption) type and can be used for remote code execution through a specially crafted .doc file. Exploit code likely .
The MS14-003 update fixes the CVE-2014-0262 vulnerability in the win32k.sys driver on Windows 7 and Windows Server 2008. The vulnerability is Elevation Of Privelege and can be used by attackers to elevate their rights to the system (code execution in kernel mode). . Exploit code likely.
Update MS14-004 fixes a vulnerability in CVE-2014-0261 in Microsoft Dynamics AX. Vulnerability is Denial of Service. Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has also updated its products, new versions of Adobe Flash Player, Adobe Reader and Acrobat have been released.
Current versions of Adobe Reader and Acrobat are listed below. The company has closed three vulnerabilities CVE-2014-0493 (memory-corruption), CVE-2014-0495 (memory-corruption), CVE-2014-0496 (use-after-free). All of them can be used to execute arbitrary code in the system through a specially prepared PDF file.

In the case of Flash Player, the company fixed two vulnerabilities CVE-2014-0491 and CVE-2014-0492. Current versions are listed below.
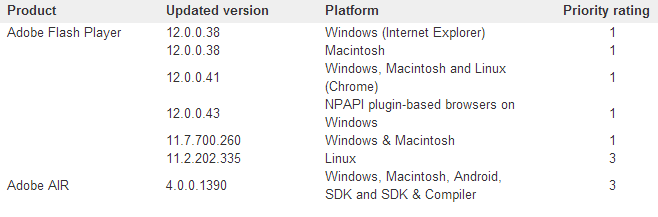
We recommend that users check the version of Flash Player used by your browser, for this you can use the official. adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10+ are automatically updated with the release of the new version of Flash Player. You can get information on updating Flash for your browser via this link .

be secure.

The MS14-002 update closes the vulnerability CVE-2013-5065 known from last year ( SA 2914486 ) in the ndproxy.sys driver version, which comes in Windows XP and Windows Server 2003. The attackers used a special request from the driver via the IOCTL interface for execute your code in kernel mode (user-mode restrictions). A special PDF document was used to deliver this exploit, which exploits the vulnerability in an outdated version of Adobe Reader and is used to overcome sandboxing limitations (Adobe Reader sandbox bypass). A malicious exploit document is detected by ESET as PDF / Exploit.CVE-2013-5065.A.
')
Update MS14-001 closes three vulnerabilities in all versions of Microsoft Word 2003-2007-2010-2013-2013 RT. Fixed vulnerabilities CVE-2014-0258, CVE-2014-0259, CVE-2014-0260 are of the Remote Code Execution (memory-corruption) type and can be used for remote code execution through a specially crafted .doc file. Exploit code likely .
The MS14-003 update fixes the CVE-2014-0262 vulnerability in the win32k.sys driver on Windows 7 and Windows Server 2008. The vulnerability is Elevation Of Privelege and can be used by attackers to elevate their rights to the system (code execution in kernel mode). . Exploit code likely.
Update MS14-004 fixes a vulnerability in CVE-2014-0261 in Microsoft Dynamics AX. Vulnerability is Denial of Service. Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has also updated its products, new versions of Adobe Flash Player, Adobe Reader and Acrobat have been released.
Current versions of Adobe Reader and Acrobat are listed below. The company has closed three vulnerabilities CVE-2014-0493 (memory-corruption), CVE-2014-0495 (memory-corruption), CVE-2014-0496 (use-after-free). All of them can be used to execute arbitrary code in the system through a specially prepared PDF file.

In the case of Flash Player, the company fixed two vulnerabilities CVE-2014-0491 and CVE-2014-0492. Current versions are listed below.

We recommend that users check the version of Flash Player used by your browser, for this you can use the official. adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10+ are automatically updated with the release of the new version of Flash Player. You can get information on updating Flash for your browser via this link .

be secure.
Source: https://habr.com/ru/post/209092/
All Articles