Configuring file server auditing: detailed instructions and cheat sheet (.pdf)
Hello!
We continue to publish cheat sheets for setting up auditing of various systems, last time we talked about AD habrahabr.ru/company/netwrix/blog/140569 , today we will discuss file servers. I must say that most often we perform exactly the settings of the audit of file servers - in the course of pilot installations with customers. There is nothing difficult in this task, just three simple steps:

')
If you have a large number of file balls, access to which is often required by employees - we recommend that you only monitor changes to audit objects. Keeping track of all events can result in a large amount of redundant data that is not of special importance.
In order to monitor changes on the file server, you need to configure an audit policy. Before setting the policy, make sure that your account is in the Administrators group or you have rights to manage auditing and event logs in the Group Policies snap-in.
or
In order to effectively control the changes, it is necessary to configure the event logs, namely, to set the maximum log size. If the size is insufficient, then the events can be overwritten before they get into the database that your change control application uses.
Finally, we would like to offer you a script that we ourselves use when setting up auditing on file servers. The script performs the audit setup on all the balls of each of the computers in a given OU . Thus, it is not required to include settings on each file resource manually.
Before running the script, you need to edit line 19 - enter the required values instead of “your_ou_name” and “your_domain”. The script must be run on behalf of an account that has domain administrator rights.
You can get the script in our knowledge base or save the following text to the .ps1 file:
Download cheat sheet (.pdf) for setting up file server auditing
____________
PS
You can manually configure and audit file servers using this algorithm, or using Netwrix Auditor . A trial version of the software is available here , online test drive is here.
We continue to publish cheat sheets for setting up auditing of various systems, last time we talked about AD habrahabr.ru/company/netwrix/blog/140569 , today we will discuss file servers. I must say that most often we perform exactly the settings of the audit of file servers - in the course of pilot installations with customers. There is nothing difficult in this task, just three simple steps:

')
- Set up file shares auditing
- Configure and apply general and detailed audit policies
- Change event log settings
If you have a large number of file balls, access to which is often required by employees - we recommend that you only monitor changes to audit objects. Keeping track of all events can result in a large amount of redundant data that is not of special importance.
Setting up auditing on file resources
- Open the properties of the balls, select the tab "Security" and click "Advanced"
- On the “Auditing” tab, select the “Everyone” user group and click the “Edit” button.
- Enable the following check boxes in the “Successfull” and “Failed” columns:
List Folder / Read Data;
Create Files / Write Data;
Create Folders / Append Data;
Write Attributes;
Write Extended Attributes;
Delete Subfolders and File;
Delete;
Change Permissions;
Take Ownership.
- Make sure that “This folder, subfolders and files” is selected in the “Apply onto” list, and the “Apply these auditing entries” check box is not selected.
- Click "OK", on this setting one file balls completed.
Setting up a general audit policy
In order to monitor changes on the file server, you need to configure an audit policy. Before setting the policy, make sure that your account is in the Administrators group or you have rights to manage auditing and event logs in the Group Policies snap-in.
- Open the Group Policy snap-in using the gpedit.msc command or via the menu
Start> Programs> Administrative Tools> Group Policy Management. - Expand the Domains node, right-click on the name of your domain and select the menu item “Create a GPO in this domain and Link it here”.
- Enter the name of the new policy in the Name field and click OK.
- Right-click on the new policy, select the item “Edit” in the menu, the group policy editor will open.
- Expand the Computer Configuration node, then expand Policies> Windows Settings> Security Settings> Local Policies> Audit Policy.
- In the right part of the window, double-click the “Audit object access” category.
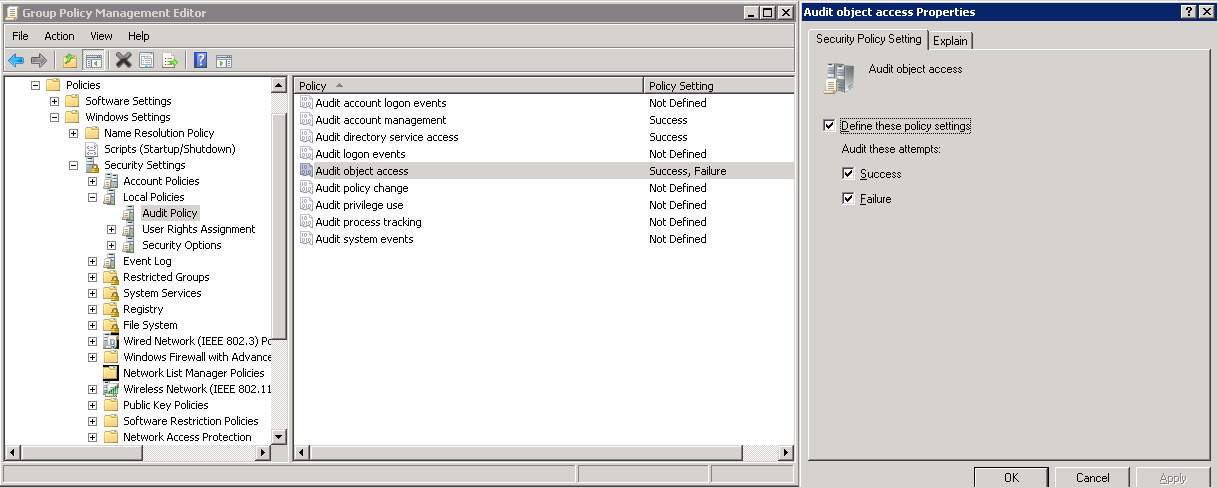
- Enable all checkboxes as shown in the screenshot, click OK.
or
Setting a detailed audit policy
- On the monitored file server, open the Local Security Policies snap-in using the secpol.msc command
- Expand Security Settings> Local Policies> Security Options and find the category Audit: Force audit policy subcategory settings (Windows Vista or later) policy in the right-hand part of the window

- Double-click this category and set it to Enabled, click OK.
- Now open the “Security Settings”> “Advanced Audit Policy Configuration”> “System Audit Policies”> “Object Access” node and configure the “Audit File System” and “Audit Handle Manipulation” categories for each of them to select the events you need (Success or Failure).
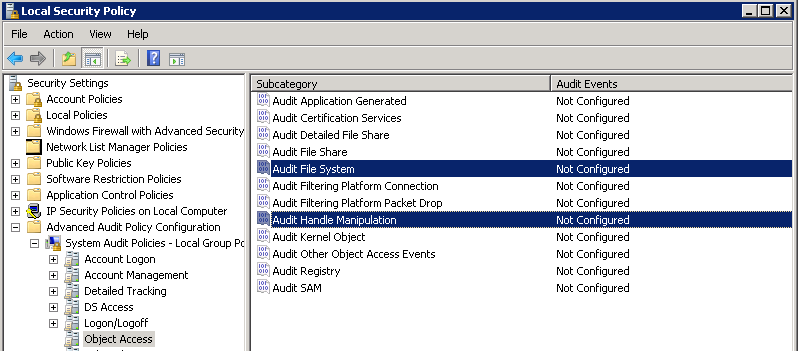
- Now it remains to apply the policy using the command line by typing gpupdate / force
- You can check whether the policy was applied using the auditpol / get / category command: “ObjectAccess”
Configuring Event Logs
In order to effectively control the changes, it is necessary to configure the event logs, namely, to set the maximum log size. If the size is insufficient, then the events can be overwritten before they get into the database that your change control application uses.
- Open Event Viewer: “Start”> “Programs”> “Administrative Tools”> “Event Viewer”
- Expand the Windows Logs node
- Right-click on the “Security” log, select the “Properties” menu item.
- Make sure the checkbox “Enable logging” is on.
- Set the values in the field Maximum log size: for Windows 2003 - 300MB, for Windows 2008 - 1GB.

- Set the log clearing method. You can use the methods of "Overwrite events as needed" or "Archive the log when full"
Finally, we would like to offer you a script that we ourselves use when setting up auditing on file servers. The script performs the audit setup on all the balls of each of the computers in a given OU . Thus, it is not required to include settings on each file resource manually.
Before running the script, you need to edit line 19 - enter the required values instead of “your_ou_name” and “your_domain”. The script must be run on behalf of an account that has domain administrator rights.
You can get the script in our knowledge base or save the following text to the .ps1 file:
#import-module activedirectory #$path = $args[0]; # \\fileserver\share\folder $account = "Everyone" # $args[1]; $flavor = "Success,Failure" #$args[2]; $flags = " ReadData, WriteData, AppendData, WriteExtendedAttributes, DeleteSubdirectoriesAndFiles, WriteAttributes, Delete, ChangePermissions, TakeOwnership " $inheritance = "ContainerInherit, ObjectInherit" $propagation = "None" $comps = Get-ADComputer -Filter * -SearchBase "OU=your_ou_name,DC=your_domain,DC=your_domain" | select -exp DNSHostName foreach ($comp in $comps) { $shares = get-wmiobject -class win32_share -computername $comp -filter "type=0 AND name like '%[^$]'" | select -exp name foreach ($share in $shares) { $path = "\\"+$comp+"\"+$share $path $acl = (Get-Item $path).GetAccessControl("Access,Audit") $ace = new-object System.Security.AccessControl.FileSystemAuditRule($account, $flags, $inheritance, $propagation, $flavor) $acl.AddAuditRule($ace) set-acl -path $path -AclObject $acl } } Download cheat sheet (.pdf) for setting up file server auditing
____________
PS
You can manually configure and audit file servers using this algorithm, or using Netwrix Auditor . A trial version of the software is available here , online test drive is here.
Source: https://habr.com/ru/post/208892/
All Articles