Cryptodisks vulnerabilities and how to deal with them
One of the most convenient solutions for encrypting files and folders today is the creation of encrypted virtual volumes, which are also called cryptodisks or cryptocontainers . However, not everyone is aware of the disadvantages of this method, as well as the fact that their inept use can do more harm than good. Therefore, in this article we will talk about the vulnerabilities of cryptodisks, as well as methods to cope with these vulnerabilities.
In fact, a cryptodisk is a regular file, except that it stores encrypted information, access to which can only be obtained by knowing the password to it. A cryptodisk connected using encryption software is recognized by the operating system as an additional local disk. You can save or copy any information on it, as well as work with files on this disk from any application. When working with files, their encryption / decryption occurs on the fly , transparent to the user, which is undoubtedly very convenient. Cryptodisk is a kind of digital safe on our computer to store confidential information. However, such a disc has its “Achilles heel,” or even several.
Without the use of additional measures, the cryptodisk file can be seen, copied and even deleted by any user who has access to your computer. And if copying does not give the attacker or the curious absolutely nothing (all that he receives is only a collection of meaningless bytes), then deletion can seriously hurt and you will be left without all the information you have so protected.
')
The solution is to back up the cryptocontainer file, or to hide it from outsiders and the operating system itself (more on this below). Better yet, both.
Another disadvantage is the ability to connect to any logical drive over the network. Even if the disk is not shared, there are still ways to connect to it, if that disk is used in a network environment.
The same applies to remote connection to a computer using TeamViewer, Radmin, VNC and other similar programs.
Cryptodisks are separate large files on the hard disk of a computer (from hundreds of MB to tens of GB), which leave a non-two-valued opinion that these files are cryptocontainers. Thus, the basic principle of protection - the concealment of the fact of protection - is fundamentally collapsing.
And if suddenly someone is really interested in you and information on your PC, then in practice no one will break into a cryptodisk - it is much easier to get your password to it in one way or another.
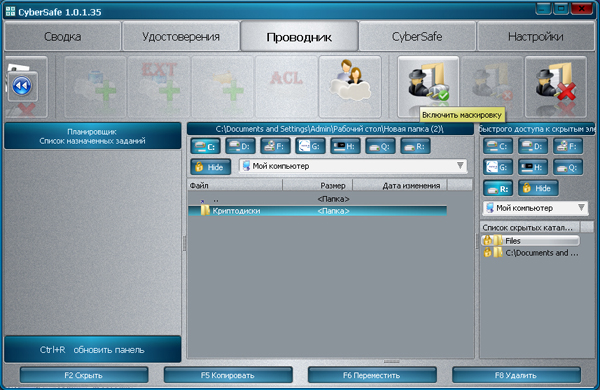
In CyberSafe, we use the disguise of cryptodisks , which significantly complicates their detection. After masking is used, cryptodisks are hidden from Windows; they are not visible on the network or using remote PC access programs.
The use of a cryptodisk implies its connection (mounting) for working with files and disabling (unmounting) after completion of work. As long as the cryptodisk is not connected, the information stored on it is not available for reading or editing.
However, when a cryptodisk is connected, its entire workspace becomes open. For example, a cryptodisk stores 1000 files, and for work you need only one of them - * .doc. While you are working with this file, the remaining 999 are also decrypted and vulnerable to an attacker, for example, when carrying out a remote attack on a computer. Or, more likely, you will leave the computer with the cryptodisk connected unattended - in this case, anyone will be able to access your confidential data.
Therefore, when dealing with a CD player, you need to be extremely careful, connect it only while working with encrypted files and disconnect immediately after the work is completed. Sometimes they even recommend creating several cryptodisks of small sizes for storing data of different types on them.
In CyberSafe , as an alternative to cryptodisks , we recommend using separate encrypted folders with assignment of different security levels to them - DSP, Secret and Sov. Secret (depend on encryption algorithm and key size). All files in folders are not only encrypted, but also hidden from Windows.

The advantage over cryptodisks here is that when working with one of the files stored in such a folder, all the others are not endangered. Working with files is carried out through the CyberSafe Explorer in transparent mode - with a double click the file will be automatically opened and decrypted, and when closed, it will be automatically encrypted. All other files in the folder at this time remain encrypted and hidden.
That's all, thank you for your attention, we hope this material was useful to you.
Intro Briefly about cryptodisks
In fact, a cryptodisk is a regular file, except that it stores encrypted information, access to which can only be obtained by knowing the password to it. A cryptodisk connected using encryption software is recognized by the operating system as an additional local disk. You can save or copy any information on it, as well as work with files on this disk from any application. When working with files, their encryption / decryption occurs on the fly , transparent to the user, which is undoubtedly very convenient. Cryptodisk is a kind of digital safe on our computer to store confidential information. However, such a disc has its “Achilles heel,” or even several.
Cryptodisks Disadvantages
1. Ability to delete by third parties
Without the use of additional measures, the cryptodisk file can be seen, copied and even deleted by any user who has access to your computer. And if copying does not give the attacker or the curious absolutely nothing (all that he receives is only a collection of meaningless bytes), then deletion can seriously hurt and you will be left without all the information you have so protected.
')
The solution is to back up the cryptocontainer file, or to hide it from outsiders and the operating system itself (more on this below). Better yet, both.
2. Online availability
Another disadvantage is the ability to connect to any logical drive over the network. Even if the disk is not shared, there are still ways to connect to it, if that disk is used in a network environment.
The same applies to remote connection to a computer using TeamViewer, Radmin, VNC and other similar programs.
3. Lack of secrecy
Cryptodisks are separate large files on the hard disk of a computer (from hundreds of MB to tens of GB), which leave a non-two-valued opinion that these files are cryptocontainers. Thus, the basic principle of protection - the concealment of the fact of protection - is fundamentally collapsing.
And if suddenly someone is really interested in you and information on your PC, then in practice no one will break into a cryptodisk - it is much easier to get your password to it in one way or another.
In CyberSafe, we use the disguise of cryptodisks , which significantly complicates their detection. After masking is used, cryptodisks are hidden from Windows; they are not visible on the network or using remote PC access programs.

Video Tutorial. Disguise Cryptodisks with CyberSafe Top Secret
4. Connection Vulnerability
The use of a cryptodisk implies its connection (mounting) for working with files and disabling (unmounting) after completion of work. As long as the cryptodisk is not connected, the information stored on it is not available for reading or editing.
However, when a cryptodisk is connected, its entire workspace becomes open. For example, a cryptodisk stores 1000 files, and for work you need only one of them - * .doc. While you are working with this file, the remaining 999 are also decrypted and vulnerable to an attacker, for example, when carrying out a remote attack on a computer. Or, more likely, you will leave the computer with the cryptodisk connected unattended - in this case, anyone will be able to access your confidential data.
Therefore, when dealing with a CD player, you need to be extremely careful, connect it only while working with encrypted files and disconnect immediately after the work is completed. Sometimes they even recommend creating several cryptodisks of small sizes for storing data of different types on them.
In CyberSafe , as an alternative to cryptodisks , we recommend using separate encrypted folders with assignment of different security levels to them - DSP, Secret and Sov. Secret (depend on encryption algorithm and key size). All files in folders are not only encrypted, but also hidden from Windows.

The advantage over cryptodisks here is that when working with one of the files stored in such a folder, all the others are not endangered. Working with files is carried out through the CyberSafe Explorer in transparent mode - with a double click the file will be automatically opened and decrypted, and when closed, it will be automatically encrypted. All other files in the folder at this time remain encrypted and hidden.
Video Tutorial. Using necks in CyberSafe Top Secret
That's all, thank you for your attention, we hope this material was useful to you.
Source: https://habr.com/ru/post/208824/
All Articles