New bug in Telegram
After getting acquainted with the post and another post.
I wanted to learn more about Telegram.
Automatically driving a Telegram hashtag into Twitter , I stumbled upon a blog of one IB company ...

A few days ago, Pavel Durov announced a campaign to correct bugs, for the protocol of decryption Telegram. Further it will be shown how personal data from the secret chat can be captured without any decryption methods due to "design failure".
')
First, let's install Telegram, and let's call the users, for example, Alice and Bob. After that, create Telegram accounts and add each other as a friend:

Now we create a secret chat:

We send a test message:
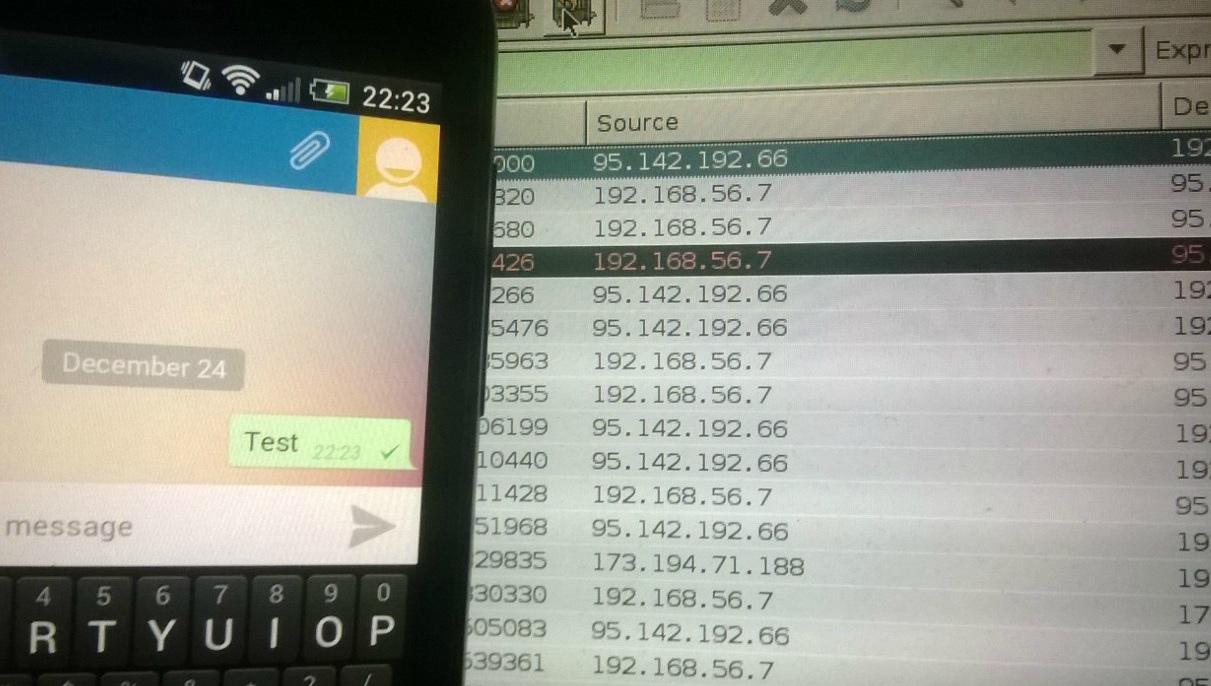
As we can see in Wireshark, all data passes through SSL and looks encrypted.
What if we try to send some attachment? For example, geolocation?

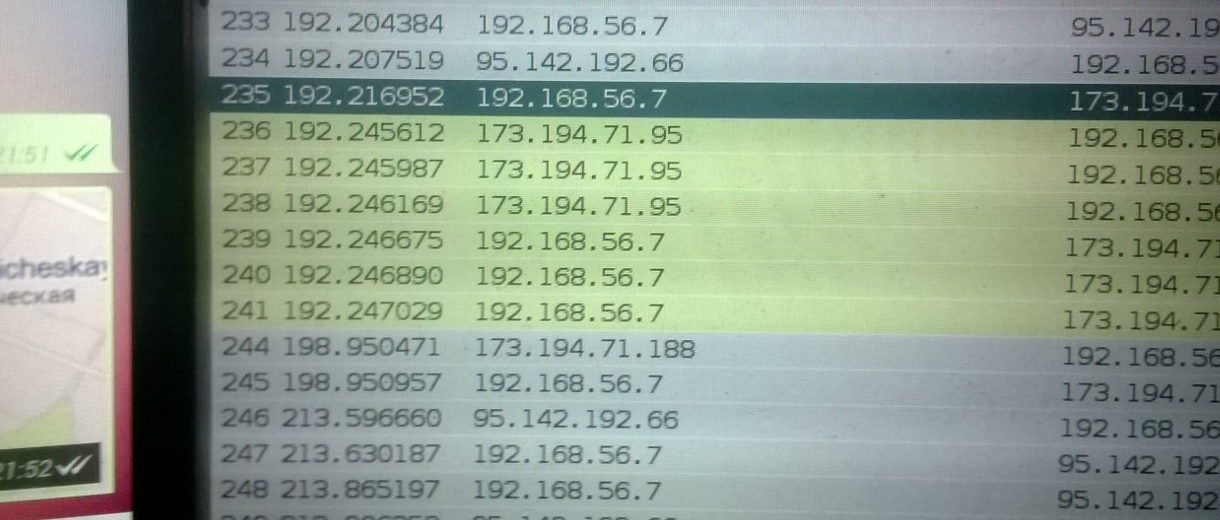
Aha Open unencrypted TCP session. Let's take a closer look:
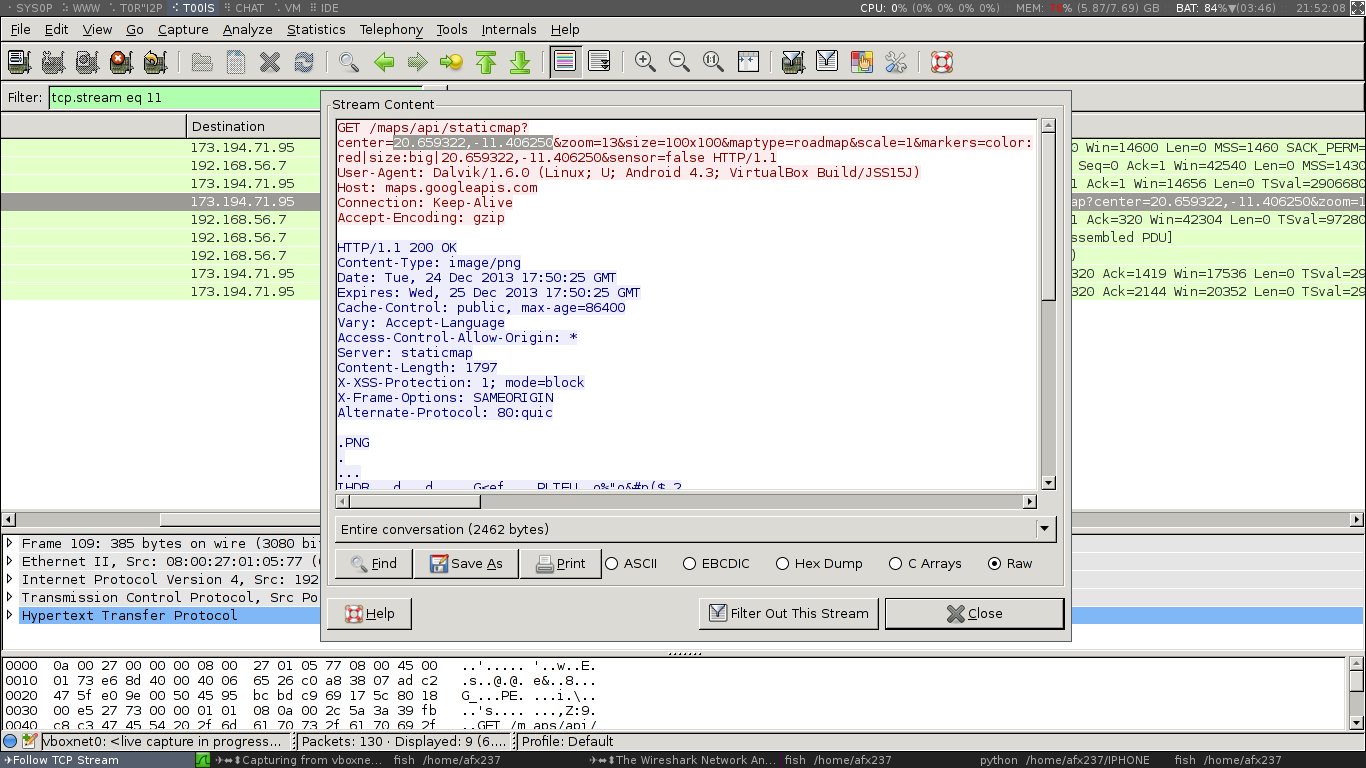
By default, Telegram uses the Google-Maps API in unencrypted form to download a map fragment.
In terms of security and anonymity, this is a complete failure ...
The person who controls the channel can intercept all geolocation attachments, bypassing the secret chat from two sides.
In practice, if Snowden sends someone who is tapped by the NSA , his geographical position through Telegrams ... the tomahawk will be enough to satisfy General Alexander .
The Security Council reacted relatively quickly to this incident and asked them to unsubscribe to the post office for a reward.
If I'm not mistaken, the fix looks like this .
It is curious how much the authors will be paid for the bug found.
A source.
I wanted to learn more about Telegram.
Automatically driving a Telegram hashtag into Twitter , I stumbled upon a blog of one IB company ...

How NOT to develop your application.
A few days ago, Pavel Durov announced a campaign to correct bugs, for the protocol of decryption Telegram. Further it will be shown how personal data from the secret chat can be captured without any decryption methods due to "design failure".
Test tools
Android 4.3 in Virtual Box
Wireshark running on the local machine.
HTC One with Android 4.0.3
Telegram 1.3.800 (in virtual box)
')
Technique
First, let's install Telegram, and let's call the users, for example, Alice and Bob. After that, create Telegram accounts and add each other as a friend:

Now we create a secret chat:

We send a test message:

As we can see in Wireshark, all data passes through SSL and looks encrypted.
But...
What if we try to send some attachment? For example, geolocation?


Aha Open unencrypted TCP session. Let's take a closer look:

By default, Telegram uses the Google-Maps API in unencrypted form to download a map fragment.
In terms of security and anonymity, this is a complete failure ...
The person who controls the channel can intercept all geolocation attachments, bypassing the secret chat from two sides.
In practice, if Snowden sends someone who is tapped by the NSA , his geographical position through Telegrams ... the tomahawk will be enough to satisfy General Alexander .
Bug fix.
The Security Council reacted relatively quickly to this incident and asked them to unsubscribe to the post office for a reward.
If I'm not mistaken, the fix looks like this .
It is curious how much the authors will be paid for the bug found.
A source.
Source: https://habr.com/ru/post/207380/
All Articles