IT systems of large companies can even be hacked by a novice hacker.
Although the problems of information security are widely discussed in recent years and more and more people are learning about their importance, the corporate systems of many companies are still not sufficiently protected. Moreover, as shown by a statistical study conducted by Positive Technologies experts, these systems can often be hacked even by a not particularly qualified cybercriminal.
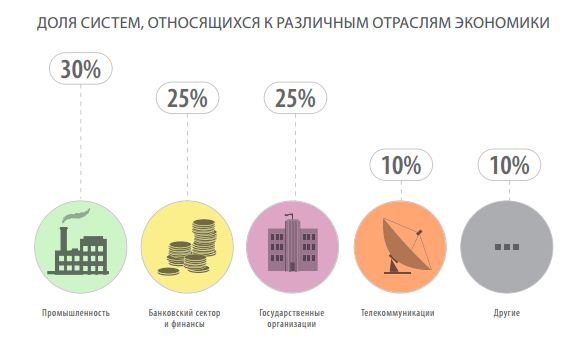
The study used data from penetration testing conducted in 2011 and 2012 (10 systems for each year). The objects of the study were the largest government organizations and commercial companies from the telecommunications, banking, financial, industrial, construction and commercial sectors of the economy (including those included in the top 400 according to the Expert agency).
')
The corporate systems caught in the report consist of thousands of nodes, often distributed geographically and have dozens of branches.
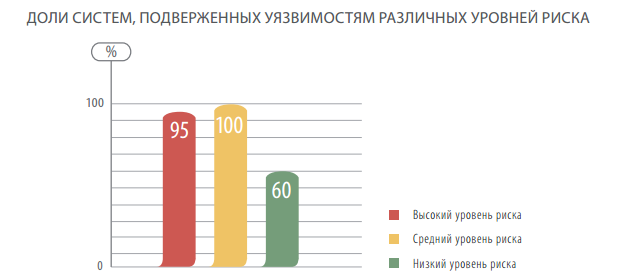
Absolutely all the systems studied were exposed to medium-risk vulnerabilities. High risk vulnerabilities were found in 95% of systems
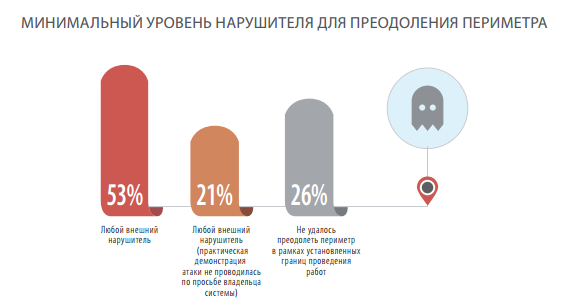
An attacker who is outside the organization, who does not have any privileges and data about the network, can overcome the network perimeter and penetrate the internal network in 74% of cases. At the same time, to overcome the network perimeter in most cases it is enough for a cybercriminal to have a medium or low level of skill.
The data for 2012 suggests that banking systems are still better protected than systems of other companies. Any external violator can penetrate into the internal systems of banks in 20% of cases, while in other sectors this figure is 80%.
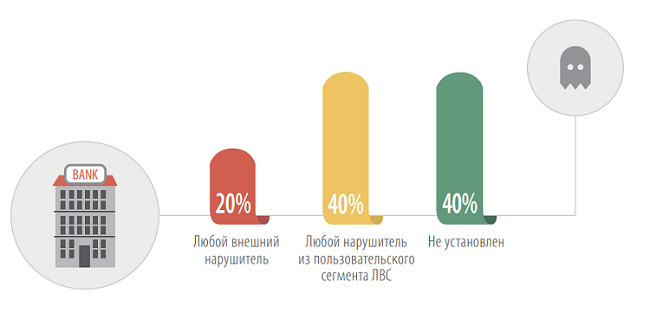
Category of the offender, on behalf of which you can get full control over critical resources in banking systems
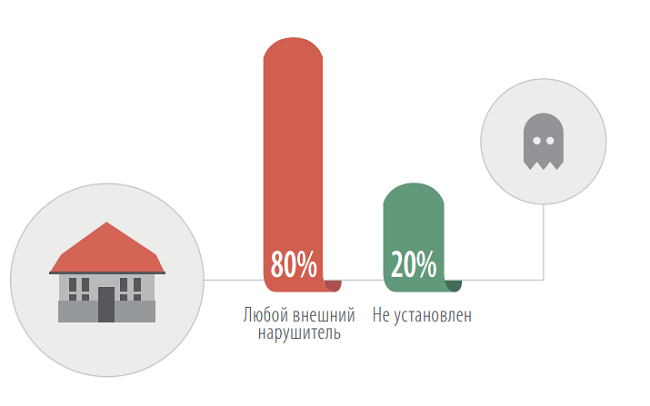
The category of the offender, on behalf of which you can get full control over critical resources in the systems of companies in other industries
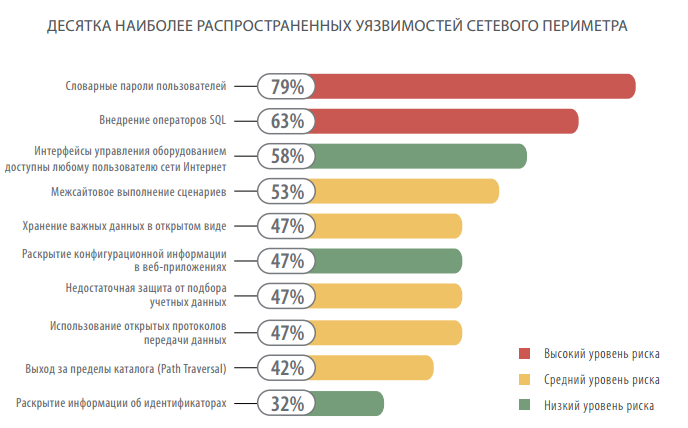
On average, to overcome the network perimeter requires the sequential operation of three different vulnerabilities. In 47% of cases, the first step is the selection of user vocabulary passwords, then the privileges are expanded and control is obtained over a resource related to the internal network.
In every third system, access to the internal network was obtained through web application vulnerabilities. Such deficiencies are found in all investigated systems. Suffice it to say that the dangerous vulnerability "The introduction of SQL statements" occurs in 63% of cases. The most comprehensive review of such security issues is given in the report “ Web Application Vulnerability Statistics (2012) ”.
Many attacks are possible due to the availability of server and network equipment management interfaces (SSH, Telnet, RDP, web interfaces) from external networks.
In a third of cases, the external intruder, after gaining access to the internal network, has the ability to develop an attack and gain complete control over the entire IT infrastructure of the company. In general, for 84% of the systems studied, as a result of external penetration testing by the Internet, it was possible to gain unauthorized access to resources with different privileges.
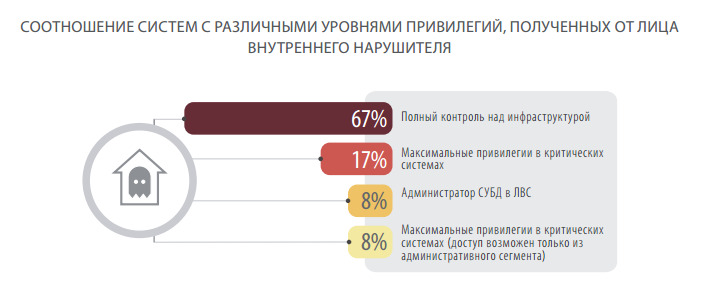
If an attacker managed to gain access to the network, then, according to statistics, he has every chance to increase his privileges and gain access to critical resources. With access to the network, Positive Technologies specialists managed to gain unauthorized access to critical resources in all the systems studied, and in 67% complete control over the entire infrastructure was obtained.
On average, if you have access to the internal network, an attacker needs to exploit 7 vulnerabilities to gain control over critical resources.
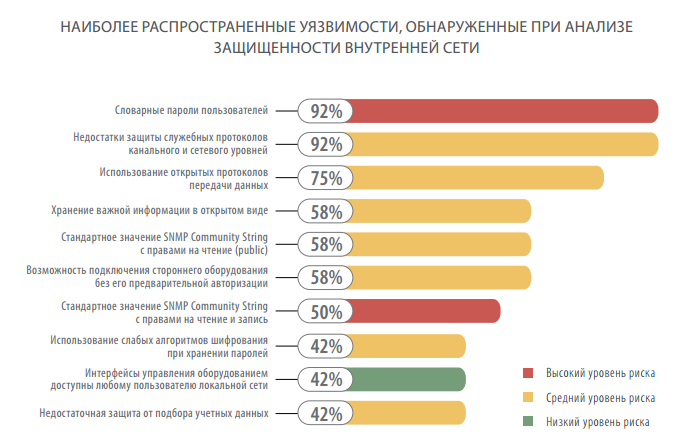
The most common vulnerabilities of internal network resources are the use of weak passwords and weaknesses in filtering and protecting channel and network layer service protocols (ARP, STP, DHCP, CDP): they are found in 92% of systems. Next is the use of open data transfer protocols (Telnet, FTP, HTTP) - 75% of cases.
Vulnerabilities in hardware and software configurations are far from the only security issue that could allow an attacker to access the corporate network. Low awareness of company employees in information security matters makes social engineering a dangerous weapon in the hands of cybercriminals.
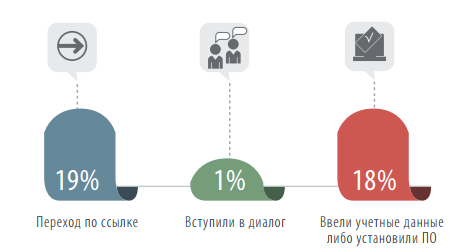
On average, over two years of research, every fifth recipient of a phishing attack emulation made the transition to the proposed address, 18% entered their data or launched the software attached to the letter, and 1% of users even tried to enter into dialogue with the author of the unsafe letter.
In general, the most significant problems were identified in centralized infrastructure-level systems (such as Microsoft Active Directory), server components, DBMS and web applications. It was through these systems that, in most cases, it was possible to gain access to critical resources, as well as to overcome the external perimeter of the network.
Despite large-scale measures to ensure information security in the surveyed companies, the obtained practical results testify to their low efficiency. Thus, multiple errors in web applications indicate the inefficiency of the process of auditing information security in the field of web applications, and updates that are not installed for several years indicate the absence of a process to manage vulnerabilities and updates.
The full version of the research report can be found on the website of Positive Technologies .
Data for research
The study used data from penetration testing conducted in 2011 and 2012 (10 systems for each year). The objects of the study were the largest government organizations and commercial companies from the telecommunications, banking, financial, industrial, construction and commercial sectors of the economy (including those included in the top 400 according to the Expert agency).

')
The corporate systems caught in the report consist of thousands of nodes, often distributed geographically and have dozens of branches.
Vulnerable all
Absolutely all the systems studied were exposed to medium-risk vulnerabilities. High risk vulnerabilities were found in 95% of systems

Common Network Perimeter Vulnerabilities
An attacker who is outside the organization, who does not have any privileges and data about the network, can overcome the network perimeter and penetrate the internal network in 74% of cases. At the same time, to overcome the network perimeter in most cases it is enough for a cybercriminal to have a medium or low level of skill.

The data for 2012 suggests that banking systems are still better protected than systems of other companies. Any external violator can penetrate into the internal systems of banks in 20% of cases, while in other sectors this figure is 80%.

Category of the offender, on behalf of which you can get full control over critical resources in banking systems

The category of the offender, on behalf of which you can get full control over critical resources in the systems of companies in other industries
On average, to overcome the network perimeter requires the sequential operation of three different vulnerabilities. In 47% of cases, the first step is the selection of user vocabulary passwords, then the privileges are expanded and control is obtained over a resource related to the internal network.
In every third system, access to the internal network was obtained through web application vulnerabilities. Such deficiencies are found in all investigated systems. Suffice it to say that the dangerous vulnerability "The introduction of SQL statements" occurs in 63% of cases. The most comprehensive review of such security issues is given in the report “ Web Application Vulnerability Statistics (2012) ”.
Many attacks are possible due to the availability of server and network equipment management interfaces (SSH, Telnet, RDP, web interfaces) from external networks.

Intranet Resource Security
In a third of cases, the external intruder, after gaining access to the internal network, has the ability to develop an attack and gain complete control over the entire IT infrastructure of the company. In general, for 84% of the systems studied, as a result of external penetration testing by the Internet, it was possible to gain unauthorized access to resources with different privileges.
If an attacker managed to gain access to the network, then, according to statistics, he has every chance to increase his privileges and gain access to critical resources. With access to the network, Positive Technologies specialists managed to gain unauthorized access to critical resources in all the systems studied, and in 67% complete control over the entire infrastructure was obtained.

On average, if you have access to the internal network, an attacker needs to exploit 7 vulnerabilities to gain control over critical resources.
The most common vulnerabilities of internal network resources are the use of weak passwords and weaknesses in filtering and protecting channel and network layer service protocols (ARP, STP, DHCP, CDP): they are found in 92% of systems. Next is the use of open data transfer protocols (Telnet, FTP, HTTP) - 75% of cases.

Human factor
Vulnerabilities in hardware and software configurations are far from the only security issue that could allow an attacker to access the corporate network. Low awareness of company employees in information security matters makes social engineering a dangerous weapon in the hands of cybercriminals.
On average, over two years of research, every fifth recipient of a phishing attack emulation made the transition to the proposed address, 18% entered their data or launched the software attached to the letter, and 1% of users even tried to enter into dialogue with the author of the unsafe letter.

findings
In general, the most significant problems were identified in centralized infrastructure-level systems (such as Microsoft Active Directory), server components, DBMS and web applications. It was through these systems that, in most cases, it was possible to gain access to critical resources, as well as to overcome the external perimeter of the network.
Despite large-scale measures to ensure information security in the surveyed companies, the obtained practical results testify to their low efficiency. Thus, multiple errors in web applications indicate the inefficiency of the process of auditing information security in the field of web applications, and updates that are not installed for several years indicate the absence of a process to manage vulnerabilities and updates.
The full version of the research report can be found on the website of Positive Technologies .
Source: https://habr.com/ru/post/207004/
All Articles