WordPress site hack, who needs all this and tips on how to avoid it
Hi habra User!
This story began about 2 months ago, when my good friend Alexander, who provides hosting services, when checking all virtual machines with antivirus, discovered a suspicious .js file in the root directory of my site, in the VDS that I maintain myself, then I did not give it value ... But I think any hosting administrator would immediately get worried.
Everything ended, only 2 months later, after the good corporation blocked my website:

According to the text, I want to tell you:
Summary:
Hacking, further interesting things began to happen with VDS: Spam mailing to several thousand recipients, installation of suspicious scripts, the appearance of strange files in the root of the main site. To be honest - it was scary ... But it seems I won the darkness).
')
Introduction:
I am writing this article, also as a notebook, so that it would be possible to return to it if problems recur. Who is interested in the process of combating malware, it will be described below. There will be a lot of letters, so who needs practical advice - leaf through to the end.
How my site was hacked on my own Debian Wheezy hosting or WordPress site hack and who needs it all
What problems did I encounter and how did I perceive them.
I calmed down immediately after I did not find the same js script on my site. Now I understand that this was a fatal mistake.
My site is running on Debian Wheezy, i-mscp hosting control panel (ispcp successor) is installed, there are several other sites that are also personal, so I’m the administrator and I don’t give anyone access to my VDS.
Everything was set up well, I thought, and so I wasn’t steaming about security, I used root ssh and put scripts of third-party writers on the site for experiments. WordPress site and for him just an incredible number of plugins. For which I did not spend time checking. The site grew and was replenished with all new plug-ins and scripts ...
Why do you need all these plugins \ extensions \ scripts?
I once asked my friend. I replied that I needed a “socialized” site and I like to experiment with various scripts, to see how they affect the functionality of the site and its appearance. I tried to improve something all the time ...
Problem number two
Two weeks passed after I did not respond to the first threat. I had the following problem.
I sit at work, and all of a sudden, to me in the gmail mail, the messages from my postfix mail server (where I’m set up for sending to personal mail) begin to fall into the spam folder, stating that such a message was not delivered. Approximately 50 messages about non-delivery, per second .
I go to the server and watch the log:
tail -f /var/log/mail.log And there just incredible speed of writing messages, stop the mailer:
/etc/init.d/postfix stop Spam stops, trying to figure out how the mailing is going, but due to lack of experience, I don’t understand anything.
Experimentally it is possible to find out that if you rename the root directory of the main (sysrtfm dot py) site or block the domain in the hosting control panel, the spam stops.
The realization comes that the main site was broken, but how?
I clear ALL the line mailer just:
postsuper -d ALL (~ 10,000 letters deleted)8 hours I checked the site directories for the presence of left-handed scripts, disconnected all the plug-ins, ran the mailer and received the mailing again (sad face
Then by chance, in the root directory of the site, I find the css folder with the file /css/sys0972500-1.php . Knowing the approximate structure of my CMS, I understand that its such file should not be. I download the backup for the last month, unpack it, and I see that the file should not be there exactly. How did he get there? This question is still unanswered, but it has the same rights as other files.
Read the Apache log:
tail -f /var/log/apache2/sysrtfm.ru.log and see there:
"POST /css/sys0972500-1.php HTTP/1.1" 404 55665 "-" "-" almost every 30 seconds.
Apparently someone runs this script from a distance, initiating a newsletter.
It would seem that blocking IP and everything, but it changes almost as often. Deleted the directory with the file, mailing stopped. Without taking, practically, no opposition, because I did not understand how the hacking occurred, left the problem as it is. Just changed the root password to a more complex one and by disconnecting plugins and scripts that I no longer use.
The next problem that was discovered was that, on so many popular WordPress engines, that everyone is trying to break it. Having read the Apache2 logs, I realized that there is a constant brute-force login attack on the login form to the administrative panel. But since I have long suspected about this, I have already installed the user lock plugin after several failed login attempts (User Locker).
tail -f /var/log/apache2/sysrtfm.ru.log see there:
"POST /wp-login.php HTTP/1.0" 200 6891 "http://sysrtfm.ru/wp-login.php" "Opera/9.80 (Windows NT 6.1; U; ru) Presto/2.8.131 Version/11.10" With a very high frequency. Protection against this method of attack, this is a topic for another conversation. Here I have put an additional plugin, blocking the attacker by ip address after several attempts to log in.
Problem number three
It took 3 weeks without spam and left scripts.
I went to VDS to check the logs and found that the same file was in the root of the site, and the distribution started again, but in much smaller volumes ... I took hold of my head.
I begin to scan the site online antivirus:
- vms.drweb.com/online - everything is ok
- 2ip.ru/site-virus-scaner - everything is OK
- www.virustotal.com/ru/#url - everything is ok
- antivirus-alarm.ru - everything is OK
- gimpel.comss.ru - everything is ok
Search forums result does not. But I find one little article that helped me a lot). Until now, I keep the tab open with it.
It describes the process of enabling advanced logging of the mail server in order to understand which script is launching the mailing list.
The original text of the article under the spoiler
So, we have a server based on Debian.
Complaint about outgoing spam from the server.
Task: clear the departure queue and find the cause.
Solution: of course, there are many options. Consider one of them.
1. Connect via SSH and watch the queue of letters:mailq
Yes, a lot of letters.
2. Disable the mail server (worth postfix)/etc/init.d/postfix stop
3. We look at the connections on port 25:netstat -apn | grep :25
If Established does not exist, it means that spam is not sent via a malicious script that sends mail bypassing the local mail server.
4. Clear the queue of letters
Exim:exipick -i | xargs exim -Mrm
Postfix:postsuper -d ALL
Sendmail:rm -rf /var/spool/mqueue/*
Of course, provided that we can do it (in the queue there can be real letters to real users).postsuper -d ALL postsuper: Deleted: 72849 messages
5. We try to enable extended mail logging:mv /usr/sbin/sendmail /usr/sbin/sendmail.org touch /usr/sbin/sendmail chmod +x /usr/sbin/sendmailecho -n '#!/bin/bash logger -p mail.info sendmail-ext-log: site=${HTTP_HOST}, client=${REMOTE_ADDR}, script=${SCRIPT_NAME}, pwd=${PWD}, uid=${UID}, user=$(whoami) /usr/sbin/sendmail.org -t -i' > /usr/sbin/sendmail
6. We start the mail server/etc/init.d/postfix start
7. Watch logstail -f /var/log/mail.info
We see something like:Jan 23 16:25:25 danma logger: sendmail-ext-log: site=, client=, script=send.php, pwd=/var/www/danma/data/www/site.ru, uid=33, user=www-data Jan 23 16:25:25 danma postfix/pickup[11520]: E3CD259403D: uid=33 from= Jan 23 16:25:25 danma postfix/cleanup[11522]: E3CD259403D: message-id=
Please note that this is one of the options.
If there is a letter ID in the complaint, it is worth looking at it in the departure logs.
It so happens that the server is openren.
And it also happens that they just picked up the password to the box - you should also pay attention to this!
Taken from here , thanks to the Author!
After enabling logging, I saw that spam mailing is started from this script (/css/sys0972500-1.php), but that was after the file with the css directory appeared for the third time ...
How did I get broken? Where? while I figured it out I was infected with something else ...
Problem number four
This time a friend wrote to me saying that my Kaspersky Anti-Virus does not allow it on my site
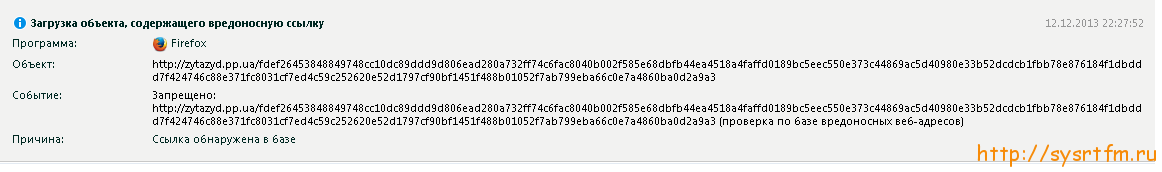
and from another computer it doesn’t allow Google Chrome to show that red cap from the cap of this article ... I was very disappointed to see that Google had banned my site by writing something like this in the webmaster’s toolbar:
“From your site, malware was installed on users' client PCs. Links from which the installation was made below:
A few links from the site ”
Yandex did not suspect anything ...
I must say, the problem turned out to win quickly enough. Here is what I did:
- Disabled the caching CMS plugin, so that the files are generated again, rather than malicious ones being taken from the cache.
- Once again, I checked the site against antivirus databases online, this antivirus-alarm really came in handy.
- because in this check it was written:
contains a dubious link according to Google: feeds feedburner com
contains a dubious link according to google: www facebook com
contains a dubious link according to google: www liveinternet en
Then again, I turned off a pack of third-party Wordpress plugins, social buttons, comments, etc. ...
The transition to social networking sites, where my posts were cross-posted, was also banned by Google, due to the fact that it contained materials from my site - Created a request for those who support Google to review the decision on blocking (on the same page where the reason for blocking is described, section “Security Issues”)
- I filled out a form to report an incorrect phishing warning .
- Since The last 2 points are considered 24 hours, I began to actively look for the cause of a possible hack. Here it comes to me that I did not check ftp!
- We read server proftpd log:
cat /var/log/proftpd/xferlog
We find there is very interesting:176.28.52.119 42278 /var/www/virtual/sysrtfm.ru/htdocs/css/sys0972500-1.php a _ ir admin@sysrtfm.ru ftp 0 * c
And then I understood everything .... (sad smiley (admin account broke@mysrtrtm.ru), I quickly changed my password and login. I also blocked all other ftp accounts. Having checked that they are not used anywhere.
Found another entry:31.7.234.34 0 /var/www/virtual/sysrtfm.ru/htdocs/css/c3x.php b _ or admin@sysrtfm.ru ftp 0 * c
This is all from the same opera, the files are deleted, but the reason for the blocking was not that. - Further I started a topic in the Google webmasters technical support forum here .
There are kind people who found interesting things in the scripts downloaded from the site)
What did the malware:
- Modified via ftp file wp-content / plugins / usernoise / js / usernoise.js by adding one more script to the very end: /wp-includes/images/smilies/skynet.js
It turned out that this script was executed only if the browser is not Google Chrome, downloading malware onto the user's PC.
- Then the file /wp-content/plugins/lazy-load/js/lazy-load.js was infected in which the script /wp-includes/images/crystal/gocubs.js was written - I downloaded the WinSCP website to my local disk, launched the total commander , moved to the downloaded directory, and ran an expression search for all the files:
cr"±"ipt skynet.js document.write
All found entries cleaned. And it seems that he didn’t delete anything extra. - I manually checked all the scripts that the browser loads for these occurrences. Nothing else found
After 12 hours, Google unblocked my site, but the statistics still slipped (
Now the problem has been solved , but now I have made a lot of conclusions ...
How it would be necessary to react in reality.
Now I understand that such problems cannot be allowed on sites of any level; not only your security and financial situation, but also the most important financial security of your clients depends on it ...
If I had responded correctly 2 months ago, to a message from my friend about a suspicious js file found in a folder with pictures. It would be different.
This has become a serious lesson for me and now I will take a more serious look at such things! What I advise all novice web programmers and not only!
Who helped me in solving problems and what was the help
- Alexander Kraynev - technical and moral support, tips and advice, hosting with protection from ddos ( itservices.su ) on which my site lies.
- Google analytics is not only a tool for SEO, but also a tool for finding vulnerabilities. There I looked where users are most often knocking, as well as in the more primitive statistics tool of the AWStats site. For example, for me, in the top 10 visited pages, the WP authorization page is in the first place)))) the brute force is not strange, you need to do something about it.
- The Google Webmaster Tools Forum is a very useful thing, it turned out, a piece! I advise everyone.
- Google Chrome debugging panel - without it, I wouldn’t do anything at all ... (click F12 on the page you are exploring and explore and explore and explore).
- Putty, WinSCP, TotalCommander - as without them) is always at hand!
What conclusions I made for myself, being on the verge of collapse
You can not bring the problem to such a state. The problems that have arisen with my site, and possible problems with clients' sites, are only my problem due to the lack of competence that I will be building up in an enhanced mode in the near future.
Who needs all this?
Who needs all this? All these attacks, viruses, spyware? Many people know the answer to these questions. I will describe my point of view:
There are a lot of people \ programmers \ malware who earn money by providing a resource for advertising sites or collecting information for its further use for the same advertising purposes. I think that the majority of attacks on sites and malicious programs exist for these purposes.
Advertising companies subsequently buy this resource in order to sell this advertising platform to their customers at a higher price.
Just imagine a network of 100,000 hacked sites on a free blog engine - a malicious programmer hacked them. I sold this resource to an advertising company, an advertising company prepares material or links for publication, and a programmer launches this whole company on hacked websites with a few clicks, this huge traffic brings huge money all over the Internet.
Naturally, possible applications can be a lot, from harmless schoolchildren who just learn to hack, before installing malware and stealing personal data of users (transferring credit card parameters, logins and passwords from social networks to 3 people). All this is global and programmers Malware is constantly looking for vulnerabilities of sites and popular resources.
Practical advice
There are a lot of such tips on the Internet, I will gather here really IMHO:
- Never, in any case, leave the standard and simple user names for authorization on your services (admin, user, login, administrator, etc.). This will increase security by 50% minimum. Plus, use a captcha or check for humanity;
- Always make a backup , there can be no questions here, there should always be a backup copy! For example, I do RK locally and once a night I merge the script onto a Yandex disk via Webda v, and from the disk I move everything to my home computer once a week:Bash script to mount the poison, copy the RC and send a notification:
#!/bin/sh # , STARTB="`date +%Y-%m-%d-%H:%M:%S`" # BACKUPDIR1="/var/www/virtual/sysrtfm.ru/backups/" # YDISK="/mnt/yandex.disk" # BTDIR="siteback" # TARGETDIR="${YDISK}/${BTDIR}/" DATETIME="`date +%Y-%m-%d-%H_%M_%S`" # LOGFILEDATE="`date +%Y%m%d`" # LOGFILE="/var/log/backupall-${LOGFILEDATE}.log" echo `date +%Y-%m-%d-%H:%M:%S`" " >> $LOGFILE # umount -f $YDISK >> $LOGFILE # echo `date +%Y-%m-%d-%H:%M:%S` " ${YDISK}" >> $LOGFILE mount -t davfs https://webdav.yandex.ru:443 $YDISK >> $LOGFILE # echo `date +%Y-%m-%d-%H:%M:%S` " ${TARGETDIR}${DATETIME}" >> $LOGFILE mkdir ${TARGETDIR}${DATETIME} >> $LOGFILE cd $BACKUPDIR1 >> $LOGFILE cp -r -f -p * ${TARGETDIR}${DATETIME} >> $LOGFILE umount -f $YDISK >> $LOGFILE # ENDB="`date +%H:%M:%S`" # STARTEND="Backup script Start of ${STARTB} End of ${ENDB}" mail -s "${STARTEND}" email@domain.com < $LOGFILE exit - However trite it may sound, but now I advise everyone to generate or invent a much more complex password . Passwords can be stored either in a notebook (ANIKIBeniki will not get there) or memorized 10 times. But in any case, it is easier than to restore access and solve problems due to information leakage;
- If you use popular web scripts or CMS , stay tuned to them because there are always holes. Try not to use untested scripts without reviews. Do not use old and not supported WEB scripts;
- It is always possible to protect the administrative WEB interface either by a plugin, or by setting up authorization via .httpasswd (a wizard for generating such files that you just need to put in the protected directory)
- If you can enable SSL access to your services - enable it ! SFTP , HTTPS ; Four steps to protect SSH ;
- Take care of your mail , which is all tied up! Strong password , two-step authorization mast hev!
Even more manic advice a lot. But I think the above are the first to implement. Then everyone decides for himself how far he can go in protecting his services.
PS:
And so, I conquered the darkness, and I am very happy) the experience has been gained, the site works, the system lives) it remains now only to discuss this with the respected community of habrahabr, but for the answer in the comments I need an invite, so I ask the UFO to post this article and give me New Year's invite)
And then, in my turn, I will register in the project of anonymous Santa Clauses and present the stale useful trifles to Habrayusers:
Sincerely, Ivan Levkin .
Source: https://habr.com/ru/post/206488/
All Articles









