Microsoft started hunting for ZeroAccess
The company enlisted the support of the FBI and Europol launched an operation to disable one of the largest botnets to date, which brought a lot of money to attackers. More than 2 million computers have been compromised by the malicious code ZeroAccess (aka ZAccess , Sirefef ) and it is used by attackers to perform various fraudulent operations and extract material gain, one of the most well-known components of the clicker that allows you to generate clicks on advertising links on unsuspecting users. (with an estimated monthly cybercriminal profit of $ 2.7 million).

We wrote about one of the latest modifications of this malicious program in a blog. The current version of ZAccess uses stealth infection of the system services.exe file (aka SCM ). Moreover, the malicious code has in its arsenal components for the 64-bit version of Windows. Such a way to ensure its survival is quite effective, while it should be noted that the authors of this malware approached its development very seriously, since previous versions contained a special difficult-to-find rootkit that hid the components of the malicious program deeply. Last year, it became apparent that the attackers switched to developing an updated version that uses the services.exe modification. Obviously, this is due to the increasing dominance of 64-bit OSs and the impossibility of using 32-bit rootkit technologies on these OSs due to obvious limitations .
')
Despite the fact that Microsoft, together with other companies and ISPs, set themselves the goal of cleaning computers from malicious code, this operation is not aimed at eliminating the ZeroAccess code. The measures taken are used to destroy the profit infrastructure of cybercriminals. A botnet uses a distributed P2P architecture, which greatly complicates its elimination as a whole.
The company does not disclose details of the operation, but it is known that it received permission to block the operation of computers with identified IP addresses through which fraudulent schemes were carried out in Europe and the USA. Also, thanks to the efforts of the European Cybercrime Center, physical dismantling of the servers that were used to control the botnet was carried out.
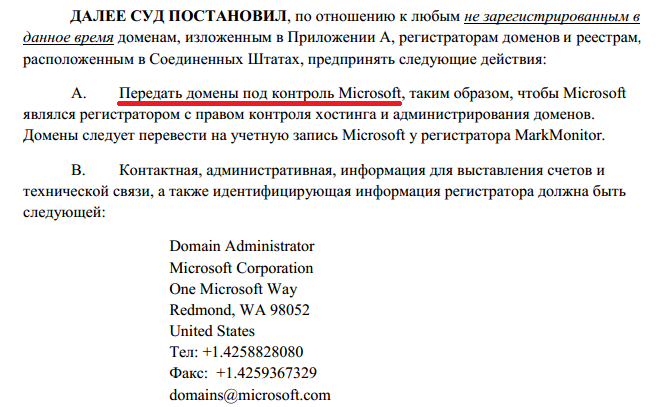
As in the case of Citadel (Zeus-based bot), the court granted the MS request to transfer the domains that were used by the attackers to their control.

Information on civil lawsuits and other legal acts are presented here .

We wrote about one of the latest modifications of this malicious program in a blog. The current version of ZAccess uses stealth infection of the system services.exe file (aka SCM ). Moreover, the malicious code has in its arsenal components for the 64-bit version of Windows. Such a way to ensure its survival is quite effective, while it should be noted that the authors of this malware approached its development very seriously, since previous versions contained a special difficult-to-find rootkit that hid the components of the malicious program deeply. Last year, it became apparent that the attackers switched to developing an updated version that uses the services.exe modification. Obviously, this is due to the increasing dominance of 64-bit OSs and the impossibility of using 32-bit rootkit technologies on these OSs due to obvious limitations .
')
Despite the fact that Microsoft, together with other companies and ISPs, set themselves the goal of cleaning computers from malicious code, this operation is not aimed at eliminating the ZeroAccess code. The measures taken are used to destroy the profit infrastructure of cybercriminals. A botnet uses a distributed P2P architecture, which greatly complicates its elimination as a whole.
The company does not disclose details of the operation, but it is known that it received permission to block the operation of computers with identified IP addresses through which fraudulent schemes were carried out in Europe and the USA. Also, thanks to the efforts of the European Cybercrime Center, physical dismantling of the servers that were used to control the botnet was carried out.

As in the case of Citadel (Zeus-based bot), the court granted the MS request to transfer the domains that were used by the attackers to their control.

Information on civil lawsuits and other legal acts are presented here .
Source: https://habr.com/ru/post/205248/
All Articles