Wireshark - taming a shark

Wireshark is a fairly well-known tool for capturing and analyzing network traffic, in fact, the standard for both education and tracing.
Wireshark works with the overwhelming majority of well-known protocols, has a clear and logical graphical interface based on GTK + and a powerful filter system.
Cross-platform, works in OS such as Linux, Solaris, FreeBSD, NetBSD, OpenBSD, Mac OS X, and, of course, Windows. Distributed under the GNU GPL v2 license. Available free of charge at wireshark.org .
Installing on a Windows system is trivial - next, next, next.
The latest version at the time of this writing is 1.10.3, and it will participate in the review.
Why do we need packet analyzers at all?
In order to conduct research of network applications and protocols, as well as to find problems in the network, and, importantly, find out the causes of these problems.
It is quite obvious that in order to make the most efficient use of sniffers or traffic analyzers, at least general knowledge and understanding of the operation of networks and network protocols are necessary.
I also remind you that in many countries the use of a sniffer without an explicit permission is equivalent to a crime.
')
We start swimming
To start capturing, just select your network interface and click Start.
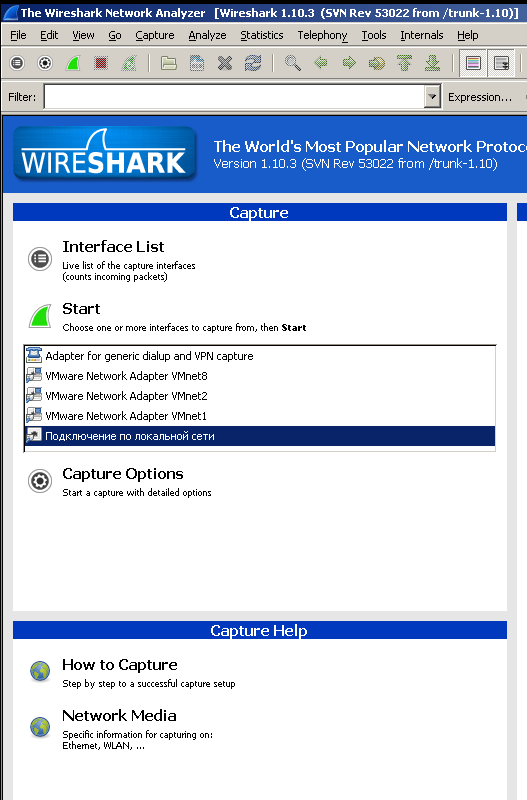
After that, the capture process will begin, with the arriving packets appearing in real time.
In the process of reviewing and examining packages, there are situations when you need to return to the previous package. There are two buttons for this (see screenshot).

And the button behind them allows you to make a quick transition to the package by specifying its number.
If the columns overlap and crawl on each other, you can click on the column with the right mouse button and select “Resize Column” .
There will be an automatic adjustment of the size under the current situation.
And besides, there is a “Resize all Columns” button that will put all the columns in order.
Using the View - Time Display Format menu, you can, for example, configure that the time count goes not from the beginning of the capture, but from the moment of receiving the previous packet ( Since Previous Captured Packet ).
The most important thing in each program ( Help - About Wireshark ) will show not only the version and the list of authors, but also contains the Folders tab, which will show how to place directories with configurations.
Studying the interface, you can choose, for example, the http packet, and see that HTTP is encapsulated in TCP (transport layer), TCP is encapsulated in IP (network layer), and IP in turn is encapsulated in Ethernet (even 802.1Q flashes before).
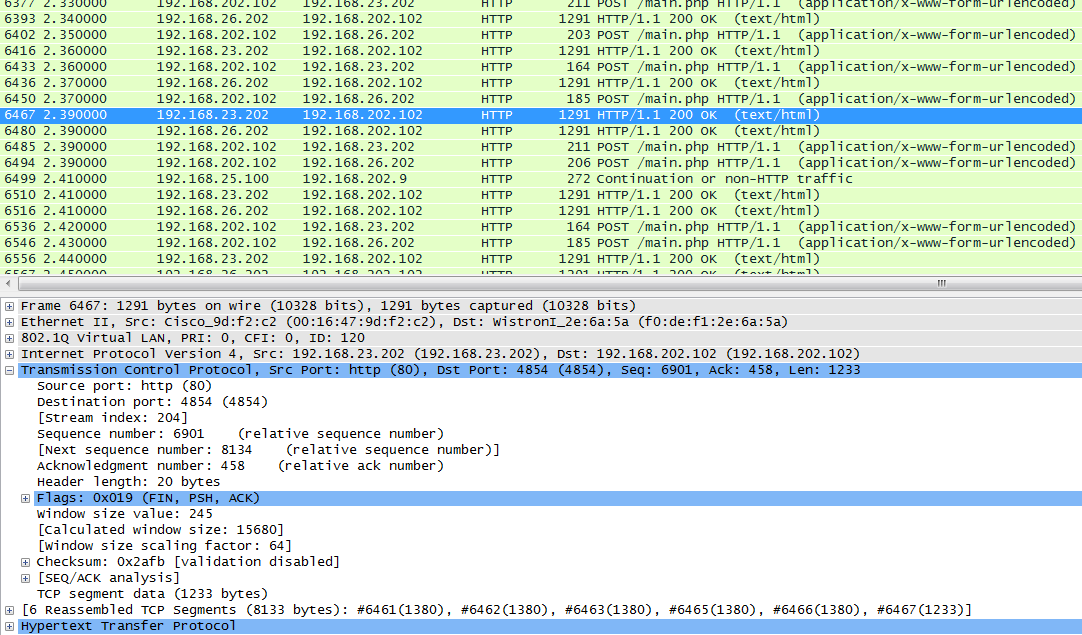
And at the very top is something like a small overview of the information collected about the frame.

We’ll talk about filters later, and at this stage, if you need to quickly filter out extra packages, just right-click on the package, select the menu Apply as Filter - Not selected and the changes will take effect immediately.
If you need to remove something else, then next time choose “and not Selected” , and the new rule will simply be added to the filter.
Remove burrs
Quite often, when working with Wireshark, an IP checksum offload error occurs - the checksum error of the IP packet header.
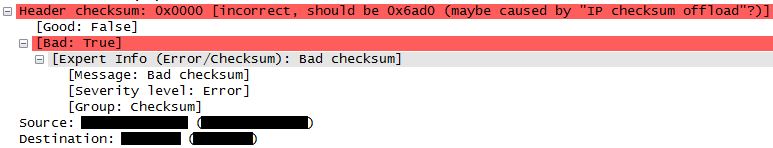
Modern network cards are so smart, what do they consider the checksum, why do it at the TCP / IP stack level programmatically, if it can be done hardwired.
And Wireshark naturally intercepts packets before they get into the network.
And before this amount was calculated and added to the package header.
Accordingly, there are two ways to solve this problem - turn off the offload function in the settings of the network card or in the settings of the sniffer to indicate that it does not pay attention to this value.
Hardwired functions are often better than software ones, mainly because of the processing speed (usually higher in hardware), so it is better to change the settings of the sniffer itself.
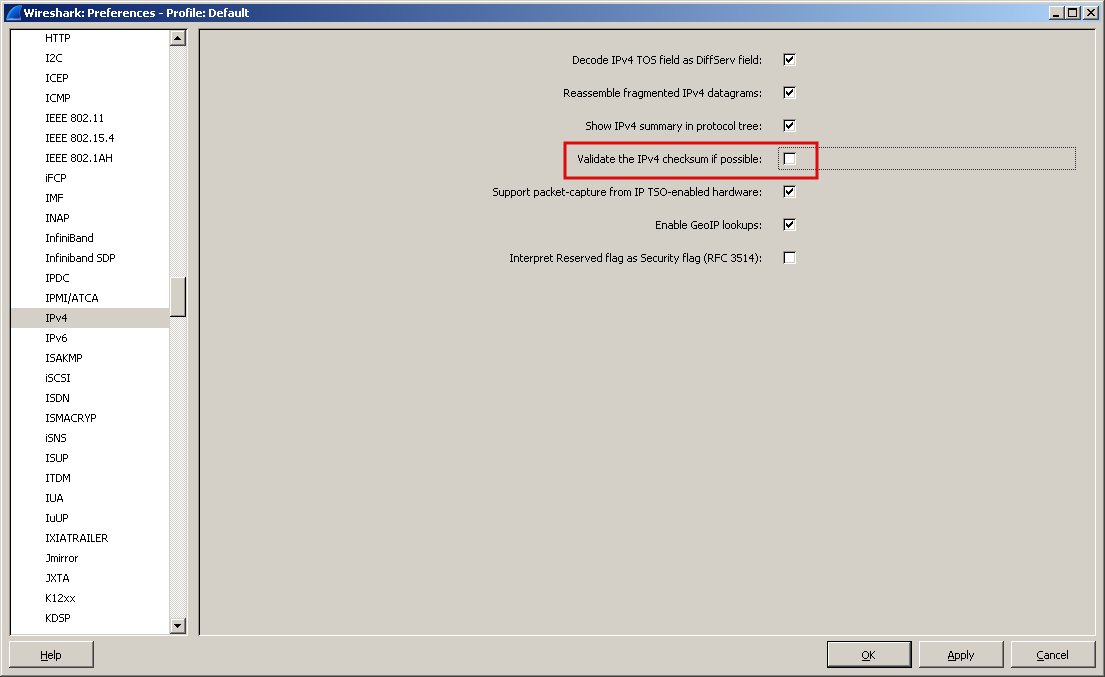
To do this, go to the settings ( Edit - Preferences ), then Protocols - IPv4 - and remove the flag from “Validate IPv4 checksum if possible” .
Before you capture traffic, you need to decide what actually needs to be captured.
You can post a traffic analyzer in several places:
- Locally on your host;
- To organize traffic mirroring on the switch;
- Connect directly to places of interest;
- or ARP poisoning (even more illegal than passive traffic listening)
Filter stream
Wireshark contains two types of filters - Capture Filters and Display Filters .
First, consider Capture Filters .
As you might guess from the name, they serve to filter even at the stage of traffic capture.
But in this case, of course, you can irrevocably lose some of the desired traffic.
A filter is an expression consisting of built-in values that can be combined by logical functions (and, or, not) if necessary.
In order to enable it, you need to go to the Capture menu, then Options , and in the Capture Filter field, type, for example, host 8.8.8.8 (or, for example, net 192.168.0.0./24 )
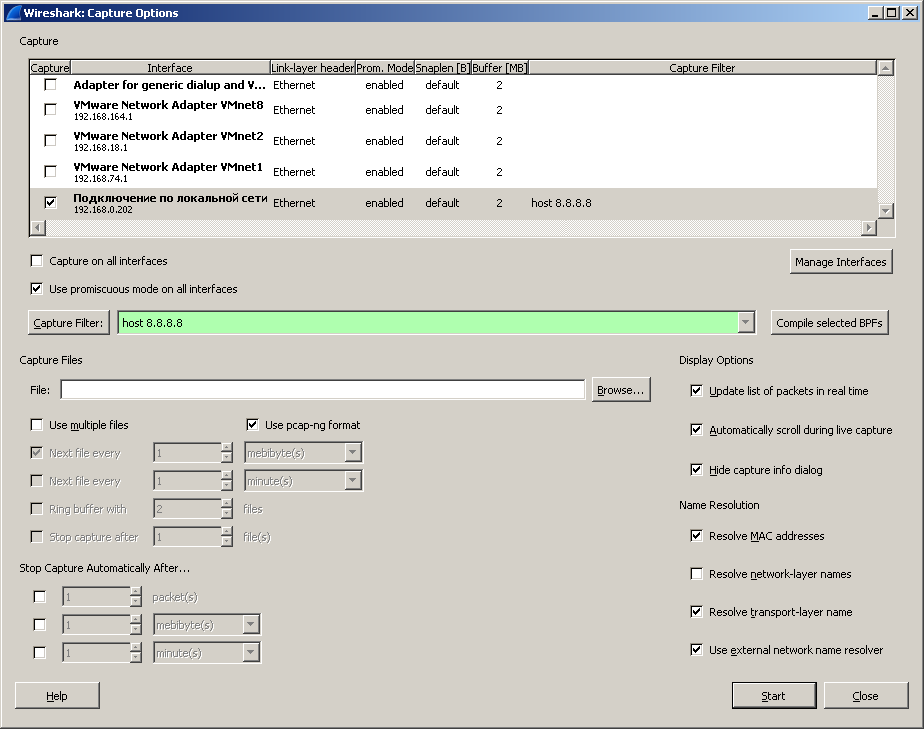
Also, of course, you can select a pre-created filter (the Capture Filter button is responsible for this).
In any of the options, the filter will appear near the interface, you can press Start.
We now turn to Display Filters .
They filter only already captured traffic.
What can be filtered?
- Almost everything - protocols, addresses, specific fields in the protocols.
Operations that can be used when building filters:
| Team | Value | Usage example |
|---|---|---|
| == | equality | ip.dst == 193.168.3.10 |
| ! = | Not equal | udp.dst! = 53 |
| < | less than | ip.ttl <24 |
| > | more than | frame.len> 10 |
| <= | less or equal | frame.len <= 0x20 |
| > = | more or equal | tcp.analysis.bytes_in_flight> = 1000 |
| matches | regular expressions | frame matches "[Pp] [Aa] [Ss] [Ss]" |
| contains | contains | dns.resp.name contains google |
As you probably noticed, in the table as examples there were a variety of expressions that are quite understandable and often speak for themselves.
For example, ip.dst is an IP field.
To see this field, you can simply look at the package, and at the bottom of the window you can see its value, which can then be used in any filter.
For example, we are interested in how to create a filter where the TTL value will be checked.
To do this, open the L3 part and stand on the appropriate field:
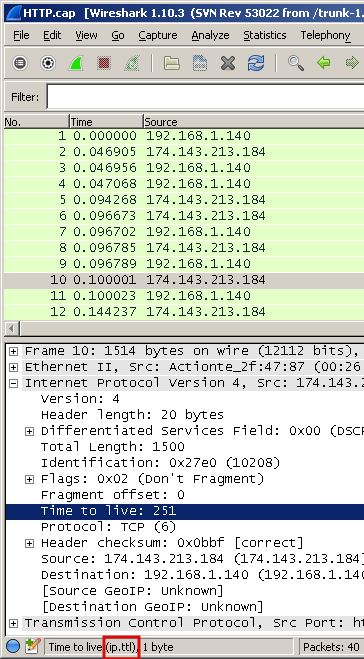
And we see that to build a filter, you need to use the expression ip.ttl.
If you start typing the filter, then after the point a list of possible values will automatically appear:
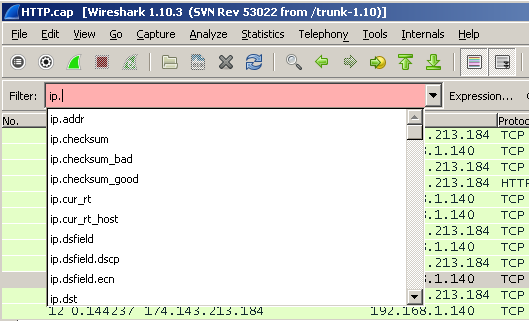
To apply the filter, just press enter or click Apply.
The filter entry field itself may change color depending on what was typed.
Green means everything is in order. Red - an error was made, yellow - an unexpected result was obtained, because there are other options for writing a filter (for example, you can write ip.dst! = 8.8.8.8 or ! Ip.dst == 8.8.8.8 , it is the second option that is more preferable).
Filters can be saved for future use by clicking the Save button, then enter a custom name.
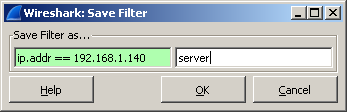
and after clicking on the OK button, the filter will appear as a button on the panel.
And if you click on the “Expression ...” button located nearby, then a sufficiently powerful expression constructor will open, using which you can almost learn the network protocols. The number of supported protocols is constantly increasing.
As mentioned earlier, you can select any package and select Apply as Filter in the context menu and select the selected or not selected mode from the submenu and, accordingly, the filter will immediately appear, which will show only the selected one or, on the contrary, remove the selected one from the screen.
Thus, you can flexibly choose what to see on the screen and what not.
It can be a specific ip-address, ttl, port, dns answer and more.
In addition, there are two options for such quick filters - Prepare as Filter and Apply as Filter.
As the name suggests, the difference is that in the first case it only appears in the Display Filter input field, but does not apply (it’s convenient, for example, to add several filters in this way, and then immediately apply the finished result), and in the second - immediately and apply.
Filters can be combined using logical operations familiar from Boolean algebra:
(dns) && (http) logical and(dns) || (http) (dns) || (http) is it logical orThus, you can build large and complex filters like:
(tcp.flags.syn==1) && (ip.src == 172.16.10.2) && (ip.dst == 172.16.10.1)Here we see that only TCP SYN segments are selected, only with a specific address of the sender and recipient. When compiling large filters, you need to remember that the filter is essentially a logical expression, and if it is true, the package will be displayed on the screen, if false, no.
We dive deeper
Quite a common situation when there are complaints about the slow work of the network, the reasons for this can be many.
Let's try to figure out what could be the reason, and consider two ways.
The first is to add a TCP delta column.
Open the package, find the Time field since the previous frame in this TCP frame , right click and select Apply as Column . A new column will appear.
You can right-click on it and select the sorting mode, for example, Sort Descending .
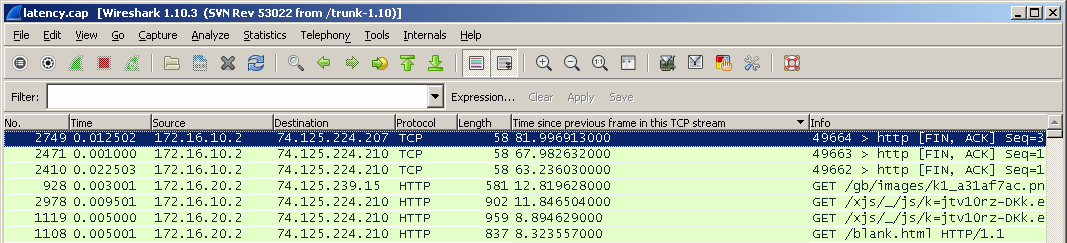
And immediately consider the second method.
Relatively recently (in version 1.10.0) a filter tcp.time_delta appeared, which, in fact, takes into account the time since the last request.
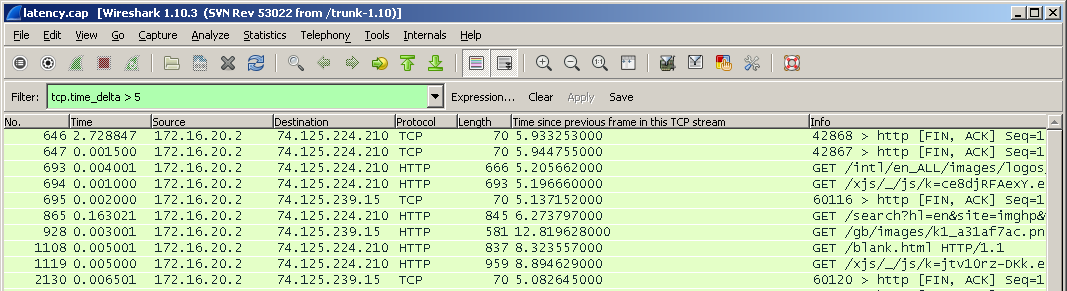
If the client makes a request and receives a response after 10 milliseconds, and the client says that everything is working slowly for him, then perhaps the problem is with the client himself.
If the client makes a request and gets an answer in 2-3 seconds, then already, perhaps, the problem lies in the network.
Even deeper
If you look at the TCP packet (or segment, to be exact), then you can see the Stream index there , which usually starts from zero.
The field itself will be called tcp.stream.

On it, you can make a right click and create a filter.
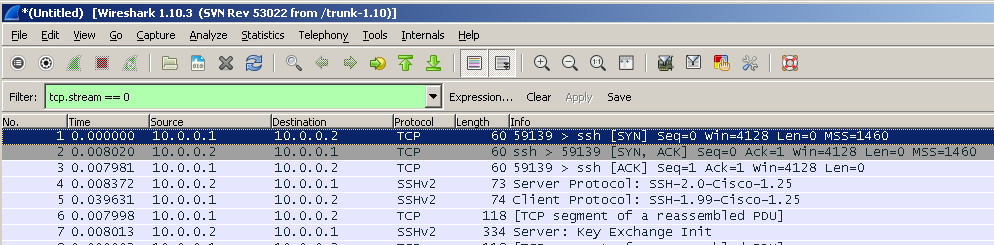
In this way, you can filter the desired compounds.
Another way is to right-click on the package itself, select the Conversation Filter and create a filter for the l2 l3 l4 level, respectively.
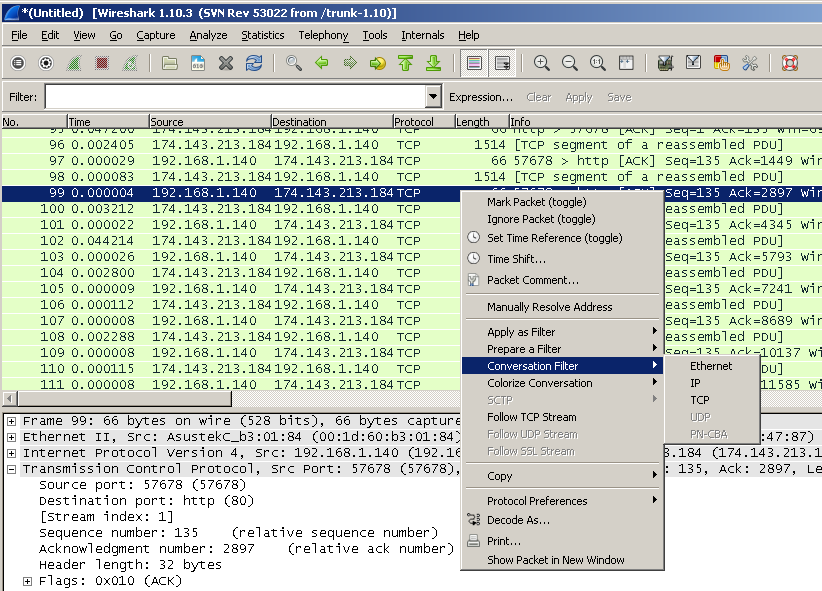
As a result, we will again see the interaction of the two hosts.
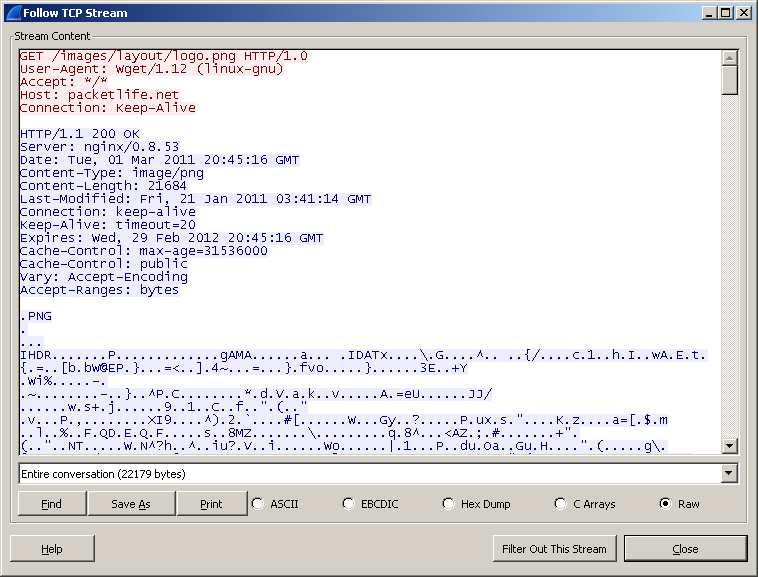
And the third option is one of the most interesting features - Follow TCP Stream .
In order to enable it, you must again right-click on the package and select “Follow TCP Stream” . A window will appear where the entire exchange between the two nodes will be clearly demonstrated.
If you go to the Statistics - Conversations menu, then by selecting bookmarks, you can see statistics on such “conversations” and different sessions, while you can sort them by different columns, for example, by the amount of data transferred.
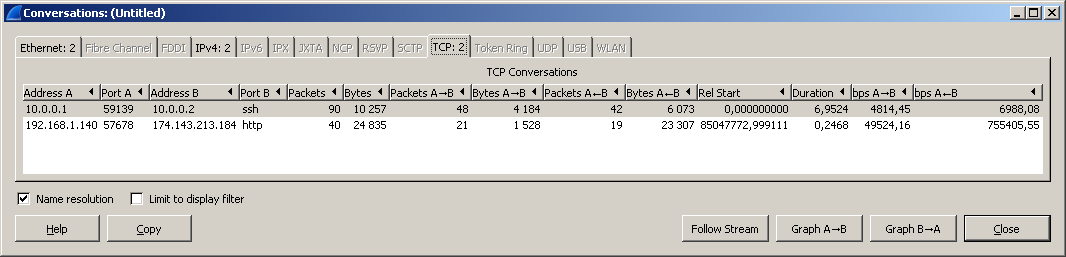
And right in this window, you can right-click to call the context menu and again apply as a filter.
With time comes experience
After some time spent on capturing a variety of traffic, you can notice some kind of spherical button in the lower left corner, which sometimes changes color.
Pressing this button will open the Expert Infos window.
The same result can be achieved by going to the Analyze - Expert Info menu.

This window will contain information on the found packages, divided into groups Errors, Warnings, Notes and Chats.
The color for these groups is as follows:
Errors - red color
Warnings - yellow
Notes - blue-green (cyan)
Chat - gray
Wireshark contains a powerful analyzer and is able to automatically detect a large number of problems arising in the network.
As you may have noticed, you can use filters literally everywhere and Expert Info is no exception.
In order to create such a filter, you need to use the expert.severity construction.
For example, expert.severity == error .
Rob traffic!
Is it possible to find out with the help of Wireshark what was downloaded?
Yes you can. And now we will see it.
First we take HTTP traffic.
We right-click on the HTTP package - Protocol Preferences - and we see here a lot of options that directly affect the extraction of files from web traffic.
In order to see what can be extracted from the current dump, go to the menu File - Export Objects - HTTP .
A window will appear that shows all captured http objects - text files, images, etc. In order to pull out any file from this list, simply select it and click Save As.
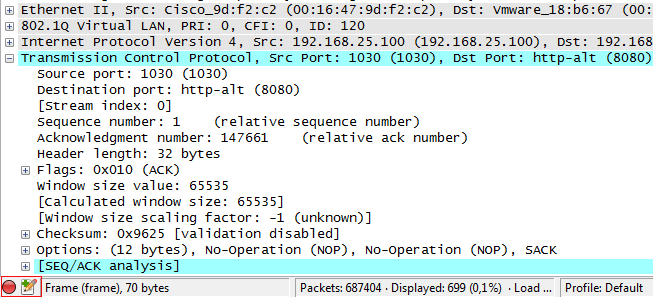
As you can see, the drawing was extracted without any problems.

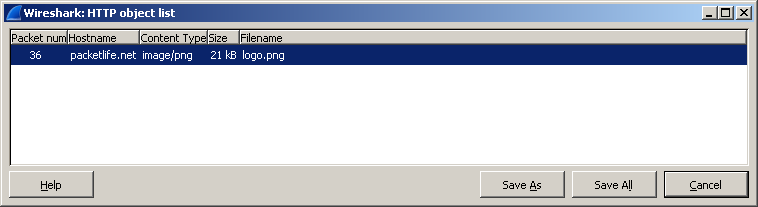
In the same way, you can extract and stream video / audio.
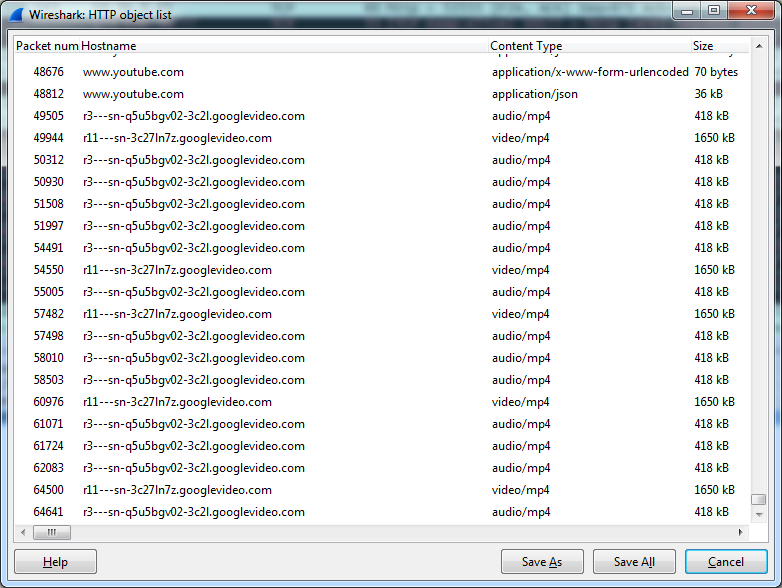
But this Wireshark opportunity does not end there!
He is able to pull out files and from the FTP protocol.
To do this, you can use the familiar already Follow TCP Stream.
As a result, only the exchange via FTP will be displayed, in which you will need to find the RETR line, which in fact will mean the transfer of the file.

Then we go down further, find the packets already directly with the file (FTP-DATA) and again select Follow TCP Stream, see the contents of the file, click Save As and save.
VoIP
Wireshark has several built-in functions for working with this technology.
It supports a lot of voice protocols - SIP, SDP, RTSP, H.323, RTCP, SRTP and others.
And, of course, it can intercept and save voice traffic for further listening.
This functionality is the best fit for troubleshooting in Voice over IP networks.
The Statistics - Flow Graph menu will show you a vivid picture of how the entire packet exchange took place.

In general, the whole Telephony menu is set aside to work with voice traffic.
For example, Telephony - RTP - Show All Streams will show in detail what happened with RTP, in particular jitter (a parameter that is probably the most important in a voice), which sometimes will immediately indicate the presence of problems.
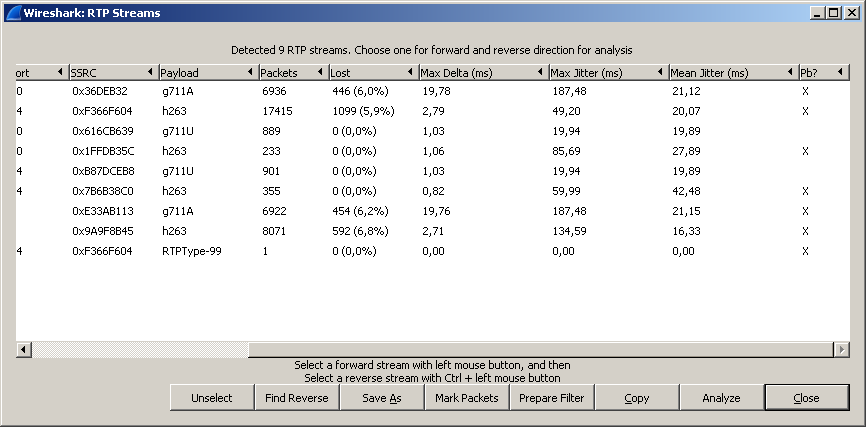
By clicking on the “Analyze” button, you can open the RTP stream Analysis window - and by selecting the stream there, you can even play it using the player button.
First, the player window opens, in which you first need to set an appropriate jitter value and use the decode button.
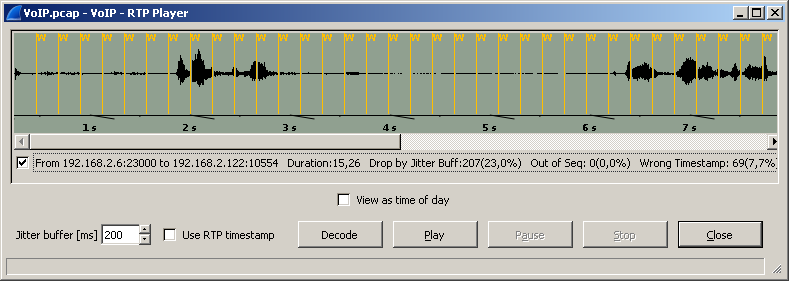
Something similar to the spectrum analyzer will appear in which you can mark the required conversation, and after that the Play button will become active.
There is also another way to listen to voice calls - you can go to the menu Telephony - VoIP Calls .
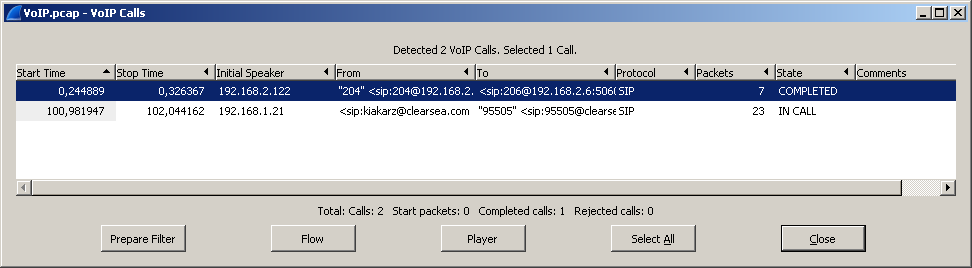
A window opens with a list of perfect calls, where again you can press the player button, cancel the desired conversations with flags and click play.
In order to achieve an acceptable sound quality, you will need to play with the value of the jitter buffer field, changing its value.
Small retreat
Some time ago, the site CloudShark.org appeared.
This is the same Wireshark sniffer, but implemented as an online service. Obviously, it will not be able to capture network traffic with it, but analyzing the traffic dump completely. By uploading a PCAP file for analysis there, it will be possible to obtain a clear sequence of packets, in which all data will be divided into clear fields depending on the protocol. In general, the same Wireshark, but a bit lightweight and accessible from any browser.
Final battle
Finally, let's look at how port scans look.
We look at the dump and see that an ARP request occurs first and then the scanning starts immediately. The address of our router is 192.168.10.11, the scan comes from the address 192.168.10.101

This is the so-called SYN scan when SYN packets are sent to a specified range of ports. Since most ports are closed, the router responds with RST and ACK packets.
Scrolling through below we see that telnet is open (tcp 23).

This is indicated by the fact that the router responded with a SYN, ACK packet.
By the way, to filter ports in the sniffer, you can use constructions of the form: tcp.srcport, tcp.dstport and tcp.port. For the UDP protocol, everything is the same - udp.srcport, udp.dstport, udp.port.
Results
We ran through the most basic parts of the best packet sniffer functionality.
It turned out somewhat messy, probably because I wanted to touch on as many of its features as possible and not to miss anything important.
It turned out that the packet sniffer, like a debugger and a disassembler, demonstrates the smallest details of the network and network protocols.
Using Wireshark and possessing the necessary knowledge (which can be learned by studying the series of networks for the smallest on the site linkmeup.ru) you can quite effectively find and diagnose various problems that arise in the network.
In the process of writing materials used the site wiki.wireshark.org
Dumps with traffic were taken from various sources, most of all from the site packetlife.net
Source: https://habr.com/ru/post/204274/
All Articles