Overview Preliminary Cybersecurity Framework, or as Obama bequeathed to manage information security risks

On February 12, 2013, US President B. Obama signed Order No. 13636 (Executive Order 13636: Improving Critical Infrastructure Cybersecurity) to improve information security (a translation closer in spirit than the difficult word cybersecurity) of critical resources. This order, among other things, indicates the need to develop the Cybersecurity Framework. Let's see, what did Obama want us to do?
Next, let me reduce the “Cybersecurity Framework” to the simple word Framework, since I think that this Americanism has come into our everyday life quite tightly and everyone understands what is being said.
The development was taken over by the well-known NIST - National Institute of Standards and Technology. The organization is serious and in less than 10 months they have already developed a document that is not ashamed to show the general public. The essence of the Framework is to provide the organizations responsible for critical resources with a unified approach to information security risk management, based on prioritization, flexibility, reproducibility, productivity and economic efficiency.
This Framework is not yet final. The current 5th version was presented to the public on October 22, 2013. A week later, the start of the 45-day open discussion was given, which will last, respectively, until December 13, 2013.
I want to share with you a review of the preliminary version of this Framework.
Introduction
The framework should essentially be a common language for describing, understanding and managing information security risks, both external and internal. It can be used to facilitate the process of identifying and prioritizing information security risk compensation activities. As conceived by the creators, it can be used by various structural units, starting with departments and ending with organizations and even associations.
In general, the entire Framework is divided into 3 main parts:
1. The Core Core
2. Profiles (the Framework Profile)
3. Levels of Implementation (the Framework Implementation Tiers)
In addition, the following issues are covered:
4. Interaction in the process of implementation of the Framework
5. Application examples
Core (the Framework Core)
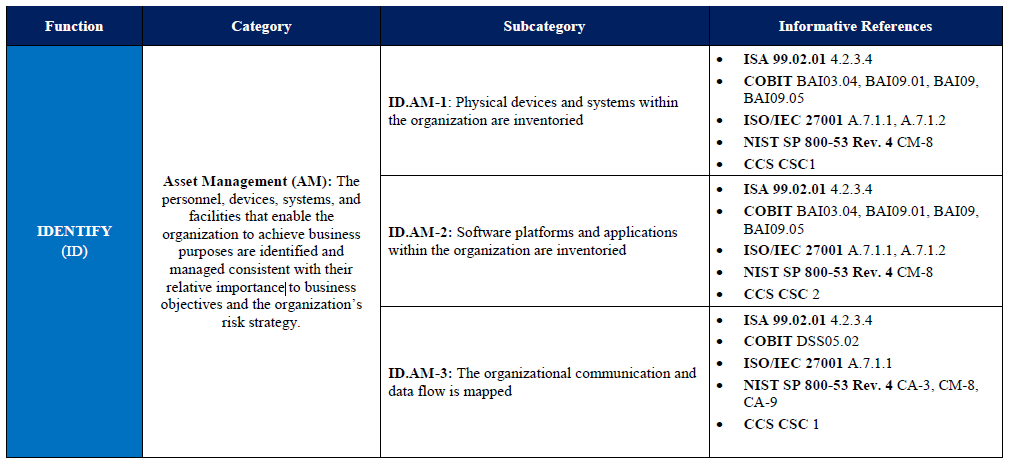
The kernel is a set of activities and informative links on information security, common to a certain set of critical resources. Conveniently displayed as a table:

The core elements of the Framework interact as follows:
Functions (left column highlighted) systematize the basic activities of information security at the highest level of abstraction. For example, as indicated in the figure: identification, protection, detection, response, and recovery. At the moment, only these basic Functions are defined. The inclusion of other important features is included in the framework development plan.
Categories are subsections of Functions closely related to practical needs and real events. For example: asset management, access control, intrusion detection.
Subcategories are a further division of the Categories, but are not an exhaustive set of activities of this Category. For example: “the physical assets of an organization are subject to inventory”, “the collection of alerts from all systems is performed centrally in a single system”.
Informative links point to specific sections of guidelines, practices, and standards illustrating methods for performing specific activities. For example, references to security controls from NIST SP 800-53 rev 4 or ISO / IEC 27001: 2013.
')
Profiles (the Framework Profile)
Profiles are a tool that allows an organization to determine the sequence of eliminating information security risks in accordance with the objectives of the entire organization and its individual structural units, taking into account the requirements of legislation, regulators and best practices, as well as reflecting the priorities of the risk management process. Profiles can be used to describe both current and target status of information security, which allows you to detect shortcomings to further eliminate the risks of information security. The target profile is created to reflect the requirements of information security requirements for business, and can be used in the interaction between organizations on information security issues.
An example of comparing profiles and identifying flaws is shown in the figure.

Implementation Levels (the Framework Implementation Tiers)
The framework implementation levels show how the organization manages information security risks. Levels begin with Partial (Level 1) and end with Adaptive (Level 4) and describe the severity and complexity of IS risk management practices and the extent to which IS risk management is integrated into the overall risk management process.
Level 1: Partial
The risk management process is not formalized and is carried out according to the situation, including in the manner of responding to IS incidents. There is no organization-wide approach to information security risk management. The organization may not participate in the coordination or interaction with other entities on IS issues.
Level 2: Risk Aware
Risk management is approved, but may not be organization-wide. Attention is paid to IS risk management, but there is no unified approach across the organization. The organization is aware of its role in the general ecosystem, but does not formalize the processes of interaction with other subjects on IS issues.
Level 3: Risk Informed and Repeatable
Risk management is approved and executed in the form of policies; regular analysis and review of the practices used is carried out. A unified approach to IS risk management is applied across the whole organization. The organization exchanges information with other entities.
Level 4: Adaptive
The organization updates its information security practices based on the experience of previous activities on information security, and, continuously improving the risk management process of information security, adapts to changes in the situation in the field of information security. A unified approach to IS risk management is applied across the whole organization, which turns this process into a part of corporate culture. The organization actively communicates with other entities to improve information security before the onset of incidents.
Interaction in the process of implementing the framework
The following figure describes the necessary directions for the movement of information and decisions in an organization between levels of leadership, business processes and implementation. The management level determines priorities, available resources and the overall level of risk acceptability and directs it to the level of business processes. At the business process level, this information is used to define the risk management process and together with the implementation level a Profile is created. The implementation level reports the level of business processes on the implementation of the requirements of the Profile. This information is required by the level of business processes to assess potential damage and further report to the level of management on the risk management process across the organization.

Application examples
1. Basic overview of the applied practices of information security
An organization can evaluate which measures of the five core functions defined in the core of the Framework are implemented. An organization should have at least basic measures in each of these areas.
2. Creation or improvement of an information security program
The following recommended recursive steps show how an organization can use the Framework to create a new information security program or improve an existing one.
Step 1. Identification
Step 2. Create a current profile
Step 3. Conduct a risk assessment
Step 4. Create a target profile
Step 5. Identify, analyze and prioritize deficiencies
Step 6. Implementation of the action plan
3. Communication with stakeholders on IS issues
The framework provides a common language for the exchange of information requirements between interdependent partners responsible for providing critical resources.
4. Identify opportunities for revising or creating new informative links.
The framework can be used to identify opportunities to create or revise standards, guidelines or practices, when additional informative links may be useful for organizations to address emerging threats.
Applications
1. The very core of the framework in the most detailed form. The example in the figure.
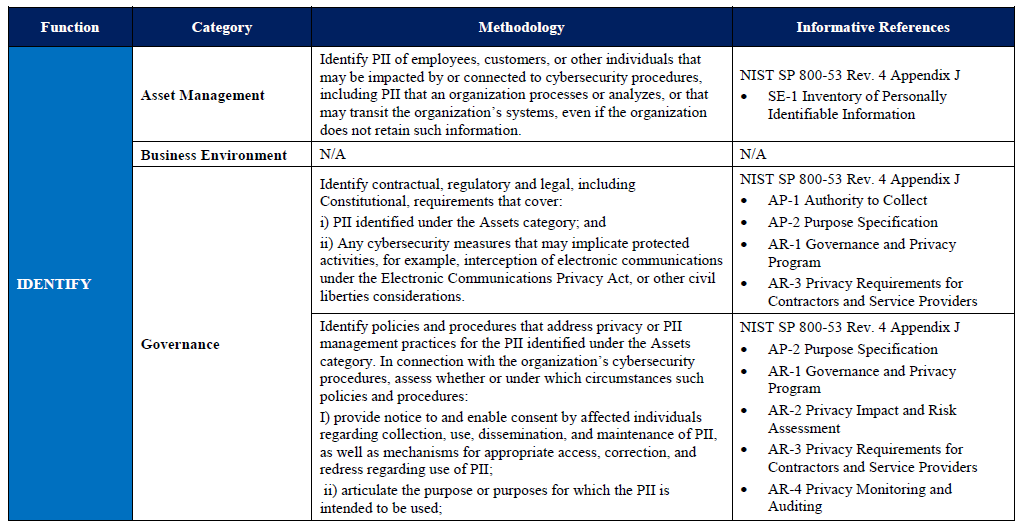
2. Methodology for ensuring privacy and freedoms of citizens in the process of implementing information security activities. Based on FIPP (Fair Information Practice Principles) and executed in accordance with the framework structure of the Framework.
3. Areas for further development of the Framework. The most critical high-level Functions are described, besides those already described 5, whose implementation in the Framework should take place in the first place. Topics included are: Authentication, Chain Risk Management, Data Analysis and others.
findings
Like all of NIST, this standard is primarily addressed to government or particularly important organizations whose information security is critical to US security. Hence, such frequent references to critical resources, which include such things as energy infrastructure, government infrastructure, communications infrastructure. These areas are strongly differentiated on the one hand, but must speak the same IB language on the other. Hence the need for a unified framework.
Also, much attention is paid to privacy and personal freedoms of citizens, which is typical for the United States. It can be seen that experts write the document not for themselves, but for everyone, paying attention to the protection of the freedoms of ordinary citizens. At a high level of abstraction, such IS activities are quite realizable, however, if they are concretely defined, we will most likely rest on local legislation.
Apparently, in future, the Framework will actively expand and include many other high-level information security functions, but I hope not all the list of security controls presented in NIST SP 800-53 rev 4.
In general, there is another interesting brick in the process of managing IS risks, the competent application of which will also depend on the form in which it will be finally adopted. The presence of open discussion and the participation of authoritative organizations gives us hope for a fully-fledged and practical document.
For those who are interested
Also, risk management processes for information security are described in the following documents:
- ISO 31000: 2009
- ISO / IEC 27005: 2008
- NIST Special Publication 800-39
- Electricity Sector Cybersecurity Risk Management Process (RMP) Guideline Octave
Source: https://habr.com/ru/post/203776/
All Articles