Commercial self-extracting archives: security, principles of operation
One of the major existing problems in the development and dissemination of information technologies is the protection of copyright on such intellectual property as software, audio, video materials and any other information that can be presented in electronic form. The owners of such objects have to resort to various means of protection against copying and unauthorized distribution, which often have sometimes more value than the objects of protection themselves.
However, in some cases there is a problem of commercial distribution of digital content, which has a fairly low cost, and therefore it is not economically feasible to use expensive remedies. In connection with this situation in the intellectual property market, relatively recently appeared affordable (in fact, free) for any user, including without any special skills, content protection tools that make it possible to profit from the distribution of intellectual property. The principle of operation of such tools is based on the creation of a self-extracting archive [1] (hereinafter CPA) (self-extracting archive, abbreviated as “SFX archive”), which requires payment for the extraction of files and subsequent input of a keyword (code). CPA is created using a special client program that uses the features of the format of executable files [2] (in fact, steganographic insertion of data).
The progenitor of the commercial CPA service was a program from the ZipCoin service, and it appeared in 2009. The projects following it picked up the idea and began to develop this direction.
CPA General Information
It should be noted that CPA is still not a means of protection against unauthorized distribution and copying of information, since, after a one-time payment and unpacking of intellectual property, packaged intellectual property items do not contain and, therefore, can be distributed uncontrollably. Therefore, when it comes to paid CPAs, first of all we mean a convenient, simple, practically free way of commercial information dissemination without the use of expensive security tools.
Payment for unpacking a commercial CPA can be made using all sorts of available ways for the user, such as transferring to electronic money (Webmoney, Yandex.Money, RBK-money, PayPal, Dengi@Mail.ru, Moneymail RUR, EasyPay, etc. [3]), payment by SMS, transfer to a bank card. Opportunities A variety of payment methods directly depends on the capabilities of the “intermediary” acting as an arbitrator in the calculations between the “owner of information” and the end user. As a rule, some commission is charged for mediation.
Often, such “intermediaries” use the services of services — payment systems [4], which provide their services for receiving and paying payments in virtually any electronic currency, using SMS messages, through various money transfer systems, payment terminals, and bank cards. An example of such services is Robokassa (http://robokassa.ru/), LiqPAY (http://liqpay.com), AvisoSMS (http://avisosms.ru/), a1pay (http: // a1pay. ru /).
Currently on the market there are the following services that provide services for CPA:
')
Functional diagram of the service of commercial self-extracting archives
Typical service support commercial CPA, as a rule, consists of the following elements:
The client program provides the ability to pack files of any format in the CPA, which later on, when unpacking, the mechanism for extracting the packed data after payment and entering the keyword.
The web service is necessary for registering partners who use a client program for packing files and their further commercial distribution. The web service should have the following functions:
The database of the service, as a rule, stores detailed information about the packaged archives, partner data, statistical and billing information.
The payment service performs using the payment system a set of procedures that ensure the transfer of money from the user to the web service with the subsequent redistribution of funds between the web services as a commission-fee for mediation and paying for the purchase of content to the partner.
A web directory is used to advertise and distribute relevant content. This may be a program catalog, a catalog of audio or video materials, file storages, etc.
Below, in Figure 1, a typical functional diagram of a commercial CPA service is presented:
The service operation algorithm can be divided into the following stages:

Fig.1 Functional diagram of the service commercial
At the stage of registering a partner on the web service, personal data and payment information about the partner are recorded and entered into the database. The partner is provided with a unique number and registration data for accessing the “personal account” on the web service.
After registration by a partner, steps 2-4 are carried out independently or through third parties. At the same time, at the stage of creating the archive, the partner specifies its cost, name, as well as additional information about the archive.
After a potential user downloads an archive, if he agrees to purchase content that is attached to the archive, the payment process is initiated. At this stage, the client program built into the archive sends a request to the web service indicated in Figure 1. The request specifies the unique characteristics of the archive.
The web service together with the payment service provides for the transfer and redistribution of funds:
After a successful transfer of money, the web service generates a keyword (code) and sends it to the client program. Purchase information is entered into the database and is subsequently displayed in the form of partner sales statistics and web service statistics.
The client program receives the code, checks its correctness and then initiates the process of unpacking the content, after which the user gets access to it.
Description of the approach to the protection of digital content in self-extracting archives.
A self-extracting archive is a file (computer program) that combines the archive and the executable code to unpack it. Such archives, unlike the usual ones, do not require a separate program for unpacking them (obtaining the source files from which they were created), if the executable code can be executed in the specified operating system.
As a rule, commercial CPAs use the features of PE format [5] - the format of executable files, object code and dynamic libraries used in 32-bit and 64-bit versions of the Microsoft Windows operating system, which allow embedding data at the end of the file. The generalized structure of a PE file presented in Figure 2. For example, the format of an executable EXE file allows you to write absolutely any data to the end of the program file, while the program will work as before. In fact, the possibilities of computer steganography and steganographic concealment of data in the format of an executable file are used [6]. These features are PE format and are used by some CPA services.

Fig. 2 Generalized PE File Format
Figure 3 shows a possible layout of the CPA.
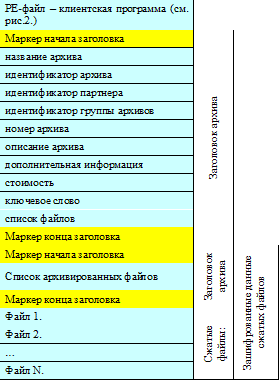
Fig. 3. Layout option CPA
Thus, the technology of the CPA boils down to the following stages:
1. Run the program and enter the partner's credentials for access via the client program to the CPA web service.
2. Select the required files with their parameters.
3. Packing selected in files in CPA.
3.1. Writing the source program code to the CPA target file.
3.2. Web service request for unique archive parameters (archive identifier, keyword).
3.3. Record in CPA of the marker of the beginning of the header of the embedded data after the code of the source program.
3.4. Generation and recording of embedded data header.
3.5. Digital content archiving.
3.6. Digital Content Encryption.
3.7. Record received data to the target file.
It should be noted that the selected encryption algorithm, the key length and the key generation algorithm significantly affect the cracking resistance of CPA. In addition, CPA is not without such a disadvantage as storing the key in the clear to the archive in the header of the archive.
As a rule, the simplest addition modulo 2 "" operation is used as encryption, the key length does not exceed 256 bits, and the encryption algorithm is reduced to calculating the hash sum on the web server using the MD5 algorithm depending on the unique characteristics of the CPA. Based on this, we can conclude that the use of commercial CPA is impractical for digital content with high value and cost and can be used only in limited cases when hacking does not lead to serious losses.
Publicly available sources already contain references to the hacking of similar commercial CPAs, (for example, “Hacking paid ZipCoin archives” - www.it-world.kz/?p=999 - the date of circulation February 23, 2011 ), which causes serious damage to the partners of these systems.
BIBLIOGRAPHY
1. Self-extracting archive. [Electronic resource]. URL: ru.wikipedia.org/wiki/SFX (appeal date 02/23/2011) ...
2. Electronic money [Electronic resource.] URL: ru.wikipedia.org/wiki/Electronic_money (appeal date 02/23/2011) ...
3. The format of executable files. [Electronic resource]. URL: www.intuit.ru/department/pl/cil/3 (appeal date 02/23/2011) ...
4. Payment system. [Electronic resource]. URL: ru.wikipedia.org/wiki/Payment_System (appeal date 23.02.2011) ...
5. Micheal J. O'Leary, The Portable Executable Format. Microsoft [Electronic resource]. URL: www.nikse.dk/petxt.html (appeal date 23.02.2011).
6. I. V. Nechta, Steganography in Portable Executable Format Files, SibSUTI Bulletin. 2009. № 1.
However, in some cases there is a problem of commercial distribution of digital content, which has a fairly low cost, and therefore it is not economically feasible to use expensive remedies. In connection with this situation in the intellectual property market, relatively recently appeared affordable (in fact, free) for any user, including without any special skills, content protection tools that make it possible to profit from the distribution of intellectual property. The principle of operation of such tools is based on the creation of a self-extracting archive [1] (hereinafter CPA) (self-extracting archive, abbreviated as “SFX archive”), which requires payment for the extraction of files and subsequent input of a keyword (code). CPA is created using a special client program that uses the features of the format of executable files [2] (in fact, steganographic insertion of data).
The progenitor of the commercial CPA service was a program from the ZipCoin service, and it appeared in 2009. The projects following it picked up the idea and began to develop this direction.
CPA General Information
It should be noted that CPA is still not a means of protection against unauthorized distribution and copying of information, since, after a one-time payment and unpacking of intellectual property, packaged intellectual property items do not contain and, therefore, can be distributed uncontrollably. Therefore, when it comes to paid CPAs, first of all we mean a convenient, simple, practically free way of commercial information dissemination without the use of expensive security tools.
Payment for unpacking a commercial CPA can be made using all sorts of available ways for the user, such as transferring to electronic money (Webmoney, Yandex.Money, RBK-money, PayPal, Dengi@Mail.ru, Moneymail RUR, EasyPay, etc. [3]), payment by SMS, transfer to a bank card. Opportunities A variety of payment methods directly depends on the capabilities of the “intermediary” acting as an arbitrator in the calculations between the “owner of information” and the end user. As a rule, some commission is charged for mediation.
Often, such “intermediaries” use the services of services — payment systems [4], which provide their services for receiving and paying payments in virtually any electronic currency, using SMS messages, through various money transfer systems, payment terminals, and bank cards. An example of such services is Robokassa (http://robokassa.ru/), LiqPAY (http://liqpay.com), AvisoSMS (http://avisosms.ru/), a1pay (http: // a1pay. ru /).
Currently on the market there are the following services that provide services for CPA:
- WebZipMoney (http://webzipmoney.ru/, 2010).
- ZipMonster (http://zipmonster.ru/, 2010).
- CashMagnat (http://cashmagnat.ru/, 2010).
- FILECASH (http://filecash.su/, 2009).
- ZIPS (http://zipseller.ru/, 2010).
- ZipCoin (http://zipcoin.ru/, 2009).
')
Functional diagram of the service of commercial self-extracting archives
Typical service support commercial CPA, as a rule, consists of the following elements:
- Client program.
- Web service for service partners.
- Database.
- Payment service.
- Web directory (file storage).
The client program provides the ability to pack files of any format in the CPA, which later on, when unpacking, the mechanism for extracting the packed data after payment and entering the keyword.
The web service is necessary for registering partners who use a client program for packing files and their further commercial distribution. The web service should have the following functions:
- provide detailed information about the rules, current rates, features of the system
- provide partner registration
- keep a statistical record of the number of requests / purchases of archives, their cost
- provide the client program with the necessary data for working with archives (information about a partner, archive, keywords, etc.)
- provide administrative functions such as adding, editing, deleting, locking archives and / or partners,
- to ensure the payment of money for the payment of archives, the accounting of settlement operations.
The database of the service, as a rule, stores detailed information about the packaged archives, partner data, statistical and billing information.
The payment service performs using the payment system a set of procedures that ensure the transfer of money from the user to the web service with the subsequent redistribution of funds between the web services as a commission-fee for mediation and paying for the purchase of content to the partner.
A web directory is used to advertise and distribute relevant content. This may be a program catalog, a catalog of audio or video materials, file storages, etc.
Below, in Figure 1, a typical functional diagram of a commercial CPA service is presented:
The service operation algorithm can be divided into the following stages:
- Registration partner.
- Download partner program.
- Creating archives.
- Publish archives.
- Download user archive.
- Initialization of the payment process.
- Support of the transfer of funds.
- Keyword Formation.
- Getting, entering a keyword and unpacking the archive.

Fig.1 Functional diagram of the service commercial
At the stage of registering a partner on the web service, personal data and payment information about the partner are recorded and entered into the database. The partner is provided with a unique number and registration data for accessing the “personal account” on the web service.
After registration by a partner, steps 2-4 are carried out independently or through third parties. At the same time, at the stage of creating the archive, the partner specifies its cost, name, as well as additional information about the archive.
After a potential user downloads an archive, if he agrees to purchase content that is attached to the archive, the payment process is initiated. At this stage, the client program built into the archive sends a request to the web service indicated in Figure 1. The request specifies the unique characteristics of the archive.
The web service together with the payment service provides for the transfer and redistribution of funds:
- reward web service in the amount of the stated commission;
- commission payment service;
- commission payment systems;
- partnership rewards for digital content.
After a successful transfer of money, the web service generates a keyword (code) and sends it to the client program. Purchase information is entered into the database and is subsequently displayed in the form of partner sales statistics and web service statistics.
The client program receives the code, checks its correctness and then initiates the process of unpacking the content, after which the user gets access to it.
Description of the approach to the protection of digital content in self-extracting archives.
A self-extracting archive is a file (computer program) that combines the archive and the executable code to unpack it. Such archives, unlike the usual ones, do not require a separate program for unpacking them (obtaining the source files from which they were created), if the executable code can be executed in the specified operating system.
As a rule, commercial CPAs use the features of PE format [5] - the format of executable files, object code and dynamic libraries used in 32-bit and 64-bit versions of the Microsoft Windows operating system, which allow embedding data at the end of the file. The generalized structure of a PE file presented in Figure 2. For example, the format of an executable EXE file allows you to write absolutely any data to the end of the program file, while the program will work as before. In fact, the possibilities of computer steganography and steganographic concealment of data in the format of an executable file are used [6]. These features are PE format and are used by some CPA services.

Fig. 2 Generalized PE File Format
Figure 3 shows a possible layout of the CPA.

Fig. 3. Layout option CPA
Thus, the technology of the CPA boils down to the following stages:
1. Run the program and enter the partner's credentials for access via the client program to the CPA web service.
2. Select the required files with their parameters.
3. Packing selected in files in CPA.
3.1. Writing the source program code to the CPA target file.
3.2. Web service request for unique archive parameters (archive identifier, keyword).
3.3. Record in CPA of the marker of the beginning of the header of the embedded data after the code of the source program.
3.4. Generation and recording of embedded data header.
3.5. Digital content archiving.
3.6. Digital Content Encryption.
3.7. Record received data to the target file.
It should be noted that the selected encryption algorithm, the key length and the key generation algorithm significantly affect the cracking resistance of CPA. In addition, CPA is not without such a disadvantage as storing the key in the clear to the archive in the header of the archive.
As a rule, the simplest addition modulo 2 "" operation is used as encryption, the key length does not exceed 256 bits, and the encryption algorithm is reduced to calculating the hash sum on the web server using the MD5 algorithm depending on the unique characteristics of the CPA. Based on this, we can conclude that the use of commercial CPA is impractical for digital content with high value and cost and can be used only in limited cases when hacking does not lead to serious losses.
Publicly available sources already contain references to the hacking of similar commercial CPAs, (for example, “Hacking paid ZipCoin archives” - www.it-world.kz/?p=999 - the date of circulation February 23, 2011 ), which causes serious damage to the partners of these systems.
BIBLIOGRAPHY
1. Self-extracting archive. [Electronic resource]. URL: ru.wikipedia.org/wiki/SFX (appeal date 02/23/2011) ...
2. Electronic money [Electronic resource.] URL: ru.wikipedia.org/wiki/Electronic_money (appeal date 02/23/2011) ...
3. The format of executable files. [Electronic resource]. URL: www.intuit.ru/department/pl/cil/3 (appeal date 02/23/2011) ...
4. Payment system. [Electronic resource]. URL: ru.wikipedia.org/wiki/Payment_System (appeal date 23.02.2011) ...
5. Micheal J. O'Leary, The Portable Executable Format. Microsoft [Electronic resource]. URL: www.nikse.dk/petxt.html (appeal date 23.02.2011).
6. I. V. Nechta, Steganography in Portable Executable Format Files, SibSUTI Bulletin. 2009. № 1.
Source: https://habr.com/ru/post/203494/
All Articles