Stealing a password from your Gmail account

The day before yesterday, Oren Hafif, a known bughanter, discovered a vulnerability in Gmail. More precisely, not a single vulnerability, but a whole chain that allows you to hijack the password from your account.
For those who do not want to read, but likes to watch the video can immediately look at the result .
The first step was to send the victim a phishing link that looked like a real one:
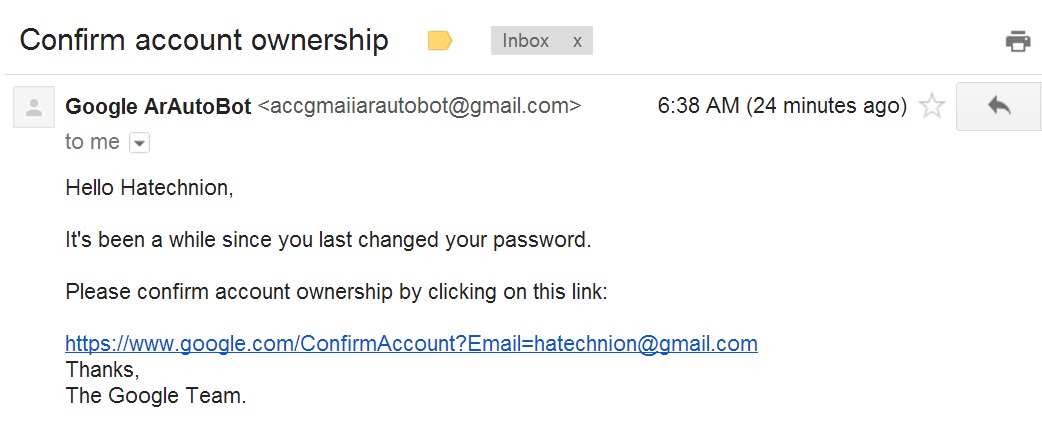
After clicking, the client sends to a specially formed page with JavaScript code, which, thanks to CSRF, sends a request to
www.google.com/accounts/recovery/verifyuser?jsEnabled=False&preoption=1&Email=' + location.hash.split("Email=")[1] + '&Email2= www.google.com/accounts/recovery/verifyuser?jsEnabled=False&preoption=1&Email=' + location.hash.split("Email=")[1] + '&Email2= , then take the email received from the parameters and redirect to the desired view link: google.com/accounts/recovery/ktpass?rpu=EVIL_JS google.com/accounts/recovery/ktpass?rpu=EVIL_JS . The vulnerable parameter is rpu , which allows you to execute arbitrary JS code. Next, the password entry form is drawn.')

By passing the necessary JS to us in the rpu parameter, you can track the result of entering the password, and then transfer the data to the sniffer.

For this vulnerability, Google paid Oren $ 5,100 for a reward program for found vulnerabilities. I think a worthy reward.
There are always vulnerabilities, even for a giant like Google. Just look.
Source: https://habr.com/ru/post/203338/
All Articles