ASLR bypass methods in the newest Zero-Day exploits
ASLR (Address Space Layout Randomization) is one of the most effective protection mechanisms in modern operating systems. But this method is not perfect. Many modern APT (advanced persistent threat) have already learned how to use innovative technologies to circumvent ASLR.
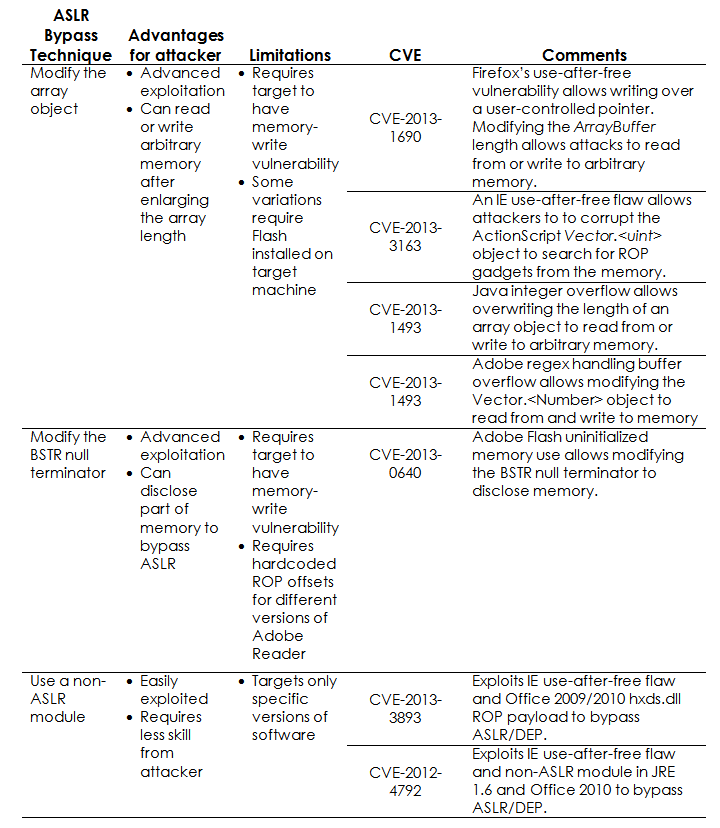
Consider the most well-known bypass methods that were discovered over the last year:
Below will be discussed in detail each of the techniques.
This method is the most popular and easy to use. Two popular non-ASLR modules that are used in IE are not protected by ASLR: MSVCR71.DLL and HXDS.DLL.
MSVCR71.DLL is used by JRE 1.6.x and comes from the Microsoft Visual C Runtime Library, which was compiled without the / DYNAMICBASE option. The library is loaded into the IE process space and has a permanent address in the following combinations of OS / browsers:
HXDS.DLL comes from MS Office 2010/2007, and is built without ASLR support. This vector was first described here , and is currently the main ASLR bypass method for IE 8/9 on Windows 7. This library is loaded when the browser contacts the address starting with “ms-help: //”.
')
This method has been used at least once in the following exploits: CVE-2013-3893 , CVE2013-1347, CVE-2012-4969 , CVE-2012-4792 .
The non-ASLR system requires modules that come with older versions of JRE 1.6 and Office 2007/2010, and are loaded only in IE8 and IE9. Updating programs to the latest versions makes this attack vector impossible.
For the first time this technique was covered in 2010 by Peter Vreudenhilom. It is applicable only to specific types of vulnerabilities associated with the possibility of memory rewriting: buffer overflow, random writing to memory, or the possibility of pointer manipulation make the attack possible.
When writing to memory there is no full control of EIP. Most of the time, the exploit overwrites critical program data, such as function pointers to execute arbitrary code. The main purpose of the attackers is damage to the length of the BSTR, which leads to an exit beyond the initial bounds of the allocated memory. In case of success, we can determine the addresses of other libraries and use them as a ROP repository. This can result in memory corruption and taking control of EIP.
Multiple vulnerabilities can be used to change the length of a BSTR. For example, some vulnerabilities allow modifying memory for one or two bytes. In this case, the attacker can change the null character in the BSTR to merge the string with the next object. With subsequent access to the modified BSTR there are chances to get information about the base addresses of the loaded libraries.
Adobe XFA zero-day exploit uses this technique to find the base address of AcroForm.api, after which the ROP chain is built and the ASLR and DEP traversal is possible. With this vulnerability, an exploit can monitor memory before calling a function from vftable:

Consider the memory allocation before the DEC operation:
After the DEC operation, the memory looks like this:
For more information, refer to the immunityinc's blog entry.
This method usually requires multiple manipulations of the memory for the disclosure of addresses, and for the operation a careful analysis of the heap is necessary to ensure that the part of the memory that is responsible for the separation of lines, and not other objects is damaged. Since Microsoft, when creating IE9, used Nozzle to prevent spraying / fengshui, sometimes an attacker has to use VBArray techniques to properly handle the heap.
Modifying the length of an array is similar to changing the length of a BSTR: they both require a certain class of “convenient” vulnerabilities. After some change in length, an attacker can achieve an arbitrary read or write to memory, or, as happens in most cases, full control over the program flow and the execution of arbitrary code.
Here is a list of known zirodeas using this technique:
This exploit is aimed at the Adobe Flash Player, in which the buffer overflow occurs during the processing of regular expressions. The attacker overwrites the length of the object's vector, and then reads the adjacent memory regions to search for the base address flash.ocx.
The exploit’s work is shown here:
Setting infinite memory allocation for new objects:
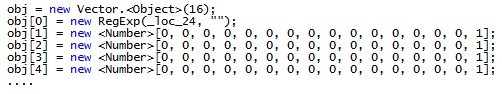
Release the
Consider the most well-known bypass methods that were discovered over the last year:
- Using non-ASLR modules
- Change BSTR Length / Zero End
- Modifying Array Objects
Below will be discussed in detail each of the techniques.
Non-ASLR modules
This method is the most popular and easy to use. Two popular non-ASLR modules that are used in IE are not protected by ASLR: MSVCR71.DLL and HXDS.DLL.
MSVCR71.DLL is used by JRE 1.6.x and comes from the Microsoft Visual C Runtime Library, which was compiled without the / DYNAMICBASE option. The library is loaded into the IE process space and has a permanent address in the following combinations of OS / browsers:
- Windows 7 and Internet Explorer 8
- Windows 7 and Internet Explorer 9
HXDS.DLL comes from MS Office 2010/2007, and is built without ASLR support. This vector was first described here , and is currently the main ASLR bypass method for IE 8/9 on Windows 7. This library is loaded when the browser contacts the address starting with “ms-help: //”.
')
This method has been used at least once in the following exploits: CVE-2013-3893 , CVE2013-1347, CVE-2012-4969 , CVE-2012-4792 .
disadvantages
The non-ASLR system requires modules that come with older versions of JRE 1.6 and Office 2007/2010, and are loaded only in IE8 and IE9. Updating programs to the latest versions makes this attack vector impossible.
BSTR modification
For the first time this technique was covered in 2010 by Peter Vreudenhilom. It is applicable only to specific types of vulnerabilities associated with the possibility of memory rewriting: buffer overflow, random writing to memory, or the possibility of pointer manipulation make the attack possible.
When writing to memory there is no full control of EIP. Most of the time, the exploit overwrites critical program data, such as function pointers to execute arbitrary code. The main purpose of the attackers is damage to the length of the BSTR, which leads to an exit beyond the initial bounds of the allocated memory. In case of success, we can determine the addresses of other libraries and use them as a ROP repository. This can result in memory corruption and taking control of EIP.
Multiple vulnerabilities can be used to change the length of a BSTR. For example, some vulnerabilities allow modifying memory for one or two bytes. In this case, the attacker can change the null character in the BSTR to merge the string with the next object. With subsequent access to the modified BSTR there are chances to get information about the base addresses of the loaded libraries.
CVE-2013-0640
Adobe XFA zero-day exploit uses this technique to find the base address of AcroForm.api, after which the ROP chain is built and the ASLR and DEP traversal is possible. With this vulnerability, an exploit can monitor memory before calling a function from vftable:

Consider the memory allocation before the DEC operation:
[string][null][non-null data][object]After the DEC operation, the memory looks like this:
[string][\xfe][non-null data][object]For more information, refer to the immunityinc's blog entry.
disadvantages
This method usually requires multiple manipulations of the memory for the disclosure of addresses, and for the operation a careful analysis of the heap is necessary to ensure that the part of the memory that is responsible for the separation of lines, and not other objects is damaged. Since Microsoft, when creating IE9, used Nozzle to prevent spraying / fengshui, sometimes an attacker has to use VBArray techniques to properly handle the heap.
Modifying an Array Object
Modifying the length of an array is similar to changing the length of a BSTR: they both require a certain class of “convenient” vulnerabilities. After some change in length, an attacker can achieve an arbitrary read or write to memory, or, as happens in most cases, full control over the program flow and the execution of arbitrary code.
Here is a list of known zirodeas using this technique:
CVE-2013-0634
This exploit is aimed at the Adobe Flash Player, in which the buffer overflow occurs during the processing of regular expressions. The attacker overwrites the length of the object's vector, and then reads the adjacent memory regions to search for the base address flash.ocx.
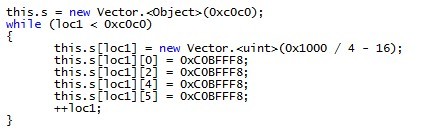
The exploit’s work is shown here:
Setting infinite memory allocation for new objects:

Release the
1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :
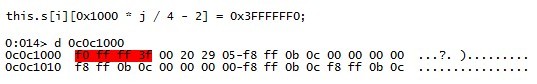
, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.
IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :
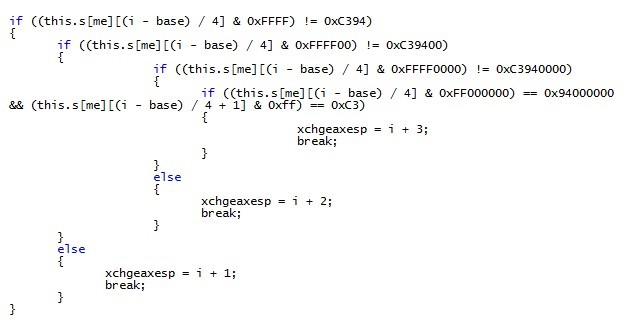
, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :
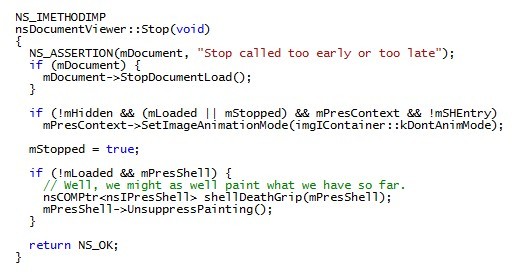
, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :
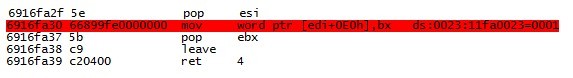
ArrayBuffer, . ArrayBuffer var2 0xff004.
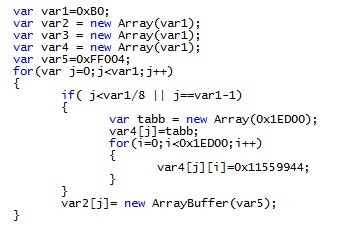
, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :
ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .
1:
obj[1] = null;RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h:
-
:
, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

,
flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .
1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .
1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .
1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .
1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .1:
obj[1] = null;
RegExp , :
boom = "(?i)()()(?-i)||||||||||||||||||||||||";
var trigger = new RegExp(boom, "");
, , obj[2]. , obj[2] , flash.ocx vftable .
CVE-2013-3163
use-after-free CBlockContainerBlock, IE. CVE-2013-0634, .
OR. :
or dword ptr [esi+8],20000h
:
- :

, . :

DWORD, 0x03f0, , .
ESI + 8 0x03f0, OR 0x0203f0, , .
0x3FFFFFF0.

IE. ASLR , DLL kernel32/NTDLL .
ZwProtectVirtualMemory API ROP , DEP :

, flash.Media.Sound(). vftable ROP .
CVE-2013-1690
use-after-free DocumentViewerImpl Firefox 0×0001 , :

, , "" . "IF", setImageAnimationMode(), . setImageAnimationMode() :

ArrayBuffer, . ArrayBuffer var2 0xff004.

, 0x010ff004. ArrayBuffer byteLength JavaScript. ArrayBuffer. NTDLL SharedUserData (0x7ffe0300) ROP .
CVE-2013-1493
JAVA CMM, .
0x7fffffff, SecurityManager . , .
Array . , .
APT 0day , :

ASLR 0day . IE non-ASLR Microsoft Office, Microsoft non-ASLR . , . , .
, , , .
ASLR, Dion Blazakis's JIT Yuyang's LdrHotPatchRoutine technique. . , ASLR, , .
. , 0day , .
Dan Caselden and Yichong Lin .Source: https://habr.com/ru/post/201768/
All Articles