Details of the targeted attack using Win32 / Exploit.CVE-2013-3906.A
Earlier, we indicated that Microsoft reported exploiting an open-ended RCE vulnerability CVE-2013-3906 by attackers through an exploit that is used to organize targeted attacks and install malicious code on victim systems. Attackers exploited a vulnerability in exploitable versions of Microsoft Word (2003-2007-2010 [2010 on Windows XP]) through a specially crafted .docx file. The attack was aimed at systems located in the Middle East and South Asia. The malicious .docx file was delivered via email, and the email itself contained a phishing message, according to which the user had to open the .docx file.

The vulnerability itself is the incorrect handling of TIFF code by the code that can be inserted into the document via ActiveX . To bypass the DEP & ASLR mitigation mechanisms on Windows Vista and Server 2008 (the latest versions of Windows 7+ are not exploitable), the exploit uses the familiar heap-spray methods to copy its code to a given address, using large heap memory and ROP backups to transfer control there bypassing the limitations of DEP for inaccessible memory. The difference in various modifications of exploits used in the attack is that the ActiveX environment itself was used for the heap-spray. We added this exploit to our databases as Win32 / Exploit.CVE-2013-3906.A . As in the case of other similar vulnerabilities, CVE-2013-3906 is of memory-corruption type, which indicates that the initial execution vector of the ROP chain will be initiated by passing a special argument to the function, which will lead to an overflow of the memory block and the start of the ROP execution. Before that, the shellcode itself will be placed in the memory via the spray when using the ActiveX framework.
')
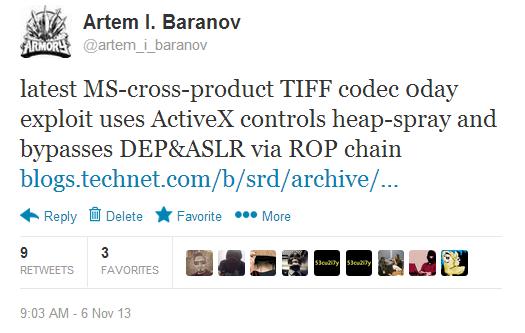
In the course of its work, the exploit connects to a remote C & C server to copy the payload from there, which is an archive with a Word document and malware. This document is used to divert the user's attention while malware is hidden in the system.
According to FireEye information from one of the C & C servers, most of the victims are located in Pakistan.
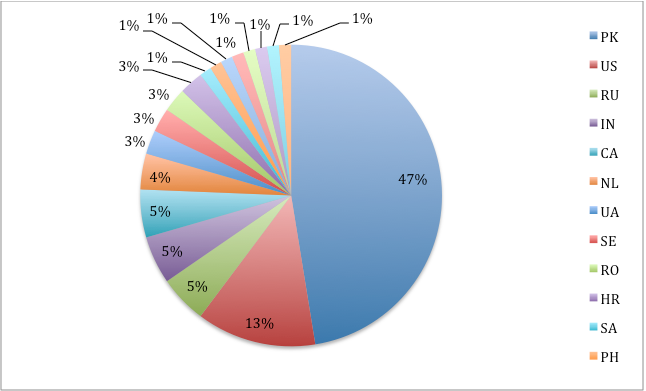
Fig. Regions to find victims of cyber attacks, according to FireEye.
The attackers chose the Citadel banking trojan as a payload for the attack.
Please note that the latest versions of Windows 7-8-8.1 are not vulnerable when using the latest versions of Office 2010-2013, which allow you to restrict various attachments of Word documents from executing through special settings that are active by default. File-> Options-> Trust Center-> Trust Center Settings-> ActiveX Settings.
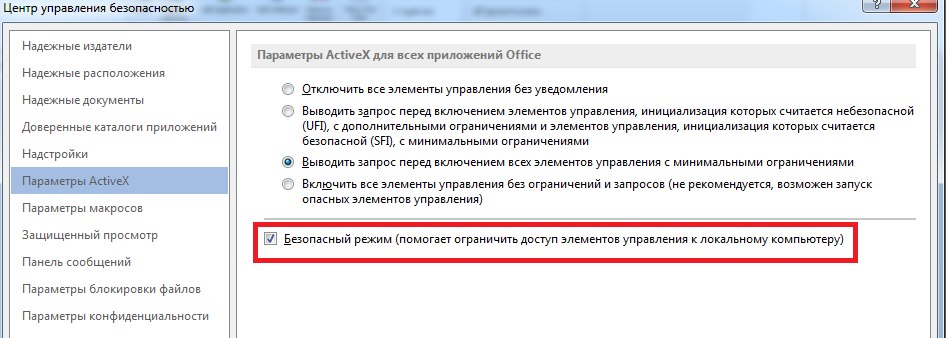
In addition, MS Outlook 2013 (Windows 7+) incorporates a sandboxing mechanism for .docx attachments, which isolates the Word viewer process that is launched.
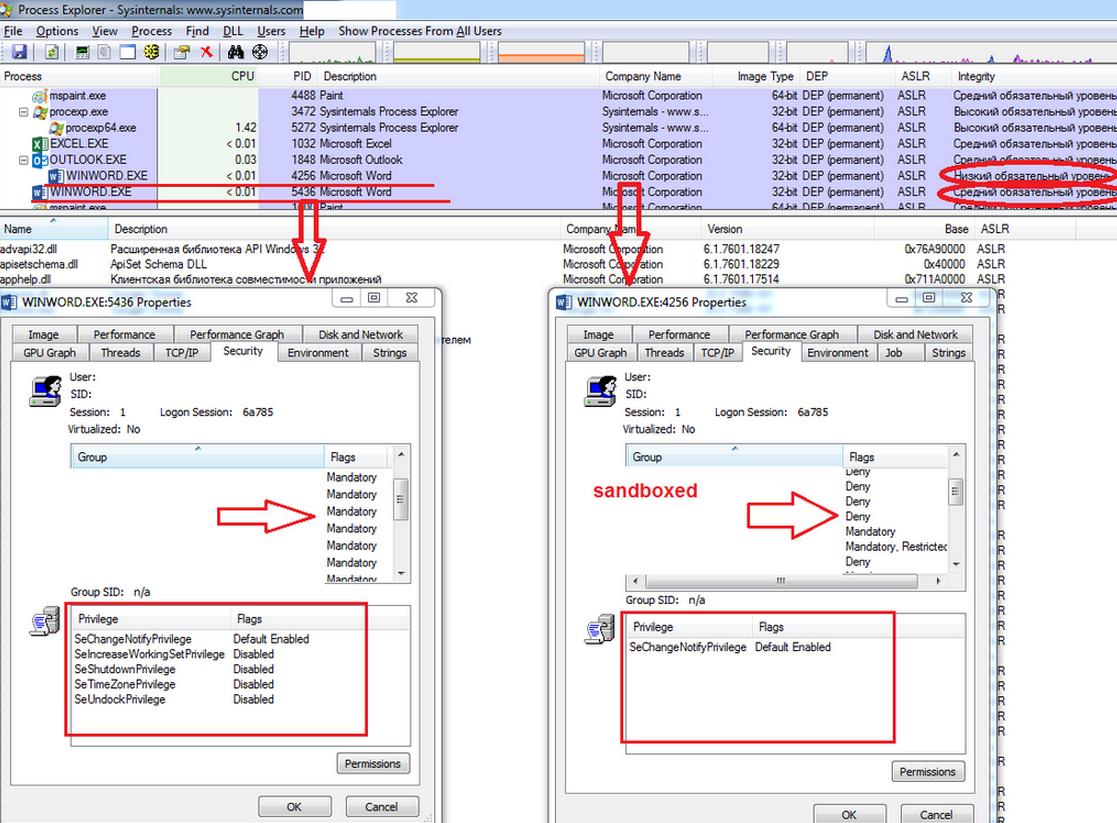
Fig. Isolation of the Word process, which occurs when viewing .docx files in emails via Outlook 2013. The process is assigned a low Integrity Level, groups in the token are denied and privileges are deleted.

The vulnerability itself is the incorrect handling of TIFF code by the code that can be inserted into the document via ActiveX . To bypass the DEP & ASLR mitigation mechanisms on Windows Vista and Server 2008 (the latest versions of Windows 7+ are not exploitable), the exploit uses the familiar heap-spray methods to copy its code to a given address, using large heap memory and ROP backups to transfer control there bypassing the limitations of DEP for inaccessible memory. The difference in various modifications of exploits used in the attack is that the ActiveX environment itself was used for the heap-spray. We added this exploit to our databases as Win32 / Exploit.CVE-2013-3906.A . As in the case of other similar vulnerabilities, CVE-2013-3906 is of memory-corruption type, which indicates that the initial execution vector of the ROP chain will be initiated by passing a special argument to the function, which will lead to an overflow of the memory block and the start of the ROP execution. Before that, the shellcode itself will be placed in the memory via the spray when using the ActiveX framework.
')

In the course of its work, the exploit connects to a remote C & C server to copy the payload from there, which is an archive with a Word document and malware. This document is used to divert the user's attention while malware is hidden in the system.
According to FireEye information from one of the C & C servers, most of the victims are located in Pakistan.

Fig. Regions to find victims of cyber attacks, according to FireEye.
The attackers chose the Citadel banking trojan as a payload for the attack.
Please note that the latest versions of Windows 7-8-8.1 are not vulnerable when using the latest versions of Office 2010-2013, which allow you to restrict various attachments of Word documents from executing through special settings that are active by default. File-> Options-> Trust Center-> Trust Center Settings-> ActiveX Settings.

In addition, MS Outlook 2013 (Windows 7+) incorporates a sandboxing mechanism for .docx attachments, which isolates the Word viewer process that is launched.

Fig. Isolation of the Word process, which occurs when viewing .docx files in emails via Outlook 2013. The process is assigned a low Integrity Level, groups in the token are denied and privileges are deleted.
Source: https://habr.com/ru/post/201304/
All Articles