Crossword based on password database stolen from Adobe
As is known, more than a month ago, Adobe announced a hacker attack on its servers, as a result of which a user database was stolen, including full name, encrypted passwords and bank card numbers, as well as the sources of its main products. Initially, it was said about 2.9 million compromised accounts, but the reality turned out to be much worse.
Soon the file with 130 324 429 unique records weighing 10GB was laid out in open access and anyone could download and delve into it.
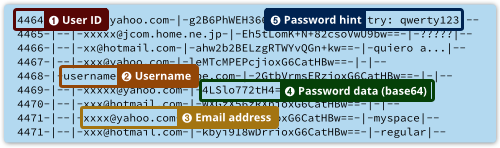
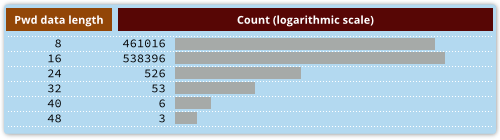
Each encrypted password in the database dump has a length of 8, 16, 24, 32, 40, or 48 characters in hexadecimal. Although Adobe assured that the data was securely encrypted, after careful study of the password database, it turned out that the 3DES block symmetric cipher was used in the Electronic Code Book (ECB) mode, while before encrypting, zero was added to each password (ASCII NUL).
')
The top 100 most popular passwords in the database were quickly compiled:

Using instead of hashing with salt, a rather ancient mechanism of symmetric encryption with a single key, for such a solid company seems unprecedentedly stupid. The large size of the database makes it easier to find the master key, and the one who calculates it will be able to fully decipher the entire dump. This Adobe epicameral has already spawned a myriad of sad jokes among the security men:

Inspired by the xkcd comic, the guys made a crossword based on 1000 of the most popular user passwords :)

As questions, an encrypted version is proposed, to answer, you must enter the password in plaitext. When you click in the white block displays up to 50 of the most popular hints for this password. No dull weekend!
Soon the file with 130 324 429 unique records weighing 10GB was laid out in open access and anyone could download and delve into it.

Each encrypted password in the database dump has a length of 8, 16, 24, 32, 40, or 48 characters in hexadecimal. Although Adobe assured that the data was securely encrypted, after careful study of the password database, it turned out that the 3DES block symmetric cipher was used in the Electronic Code Book (ECB) mode, while before encrypting, zero was added to each password (ASCII NUL).
')

The top 100 most popular passwords in the database were quickly compiled:

Using instead of hashing with salt, a rather ancient mechanism of symmetric encryption with a single key, for such a solid company seems unprecedentedly stupid. The large size of the database makes it easier to find the master key, and the one who calculates it will be able to fully decipher the entire dump. This Adobe epicameral has already spawned a myriad of sad jokes among the security men:

Inspired by the xkcd comic, the guys made a crossword based on 1000 of the most popular user passwords :)

As questions, an encrypted version is proposed, to answer, you must enter the password in plaitext. When you click in the white block displays up to 50 of the most popular hints for this password. No dull weekend!
Source: https://habr.com/ru/post/200272/
All Articles