Exploit Protection for Windows Users
Exploits are a special kind of malware that is used by attackers to install various Trojans or backdoors on a user's computer. Such an installation operation using exploits is carried out unnoticed by the user, which gives attackers undeniable advantages. An exploit is trying to exploit a vulnerability in a particular component of the OS to conduct such an operation
For the user, the most dangerous scenario is the use of an exploit by hackers that allows you to remotely install the code in the OS. In this case, it is enough for a person to visit a compromised web resource for infection with a malicious code (drive-by). If a vulnerable version of the software is installed on your computer: the browser or plug-ins to it, then the probability that you will be able to get infected with malicious code is very high.

')
It is good practice to update the OS, as well as the installed software, since manufacturers regularly close the newly emerging vulnerabilities in it. Among the components through which the user is at particular risk are the following:
In case of special targeted attacks or watering hole attacks, attackers can exploit 0day vulnerabilities in software and OS. Vulnerabilities are of the same name, which at the time of their use by the attackers were not yet closed by the vendor.
Anti-virus products can detect exploits by signatures. Thus, it allows you to protect the user from malicious content on the fly by blocking the relevant web page with malicious content.
Modern editions of Microsoft Windows: Windows 7, 8 and 8.1 have built-in mechanisms that protect the user from the destructive actions of exploits. These features include:
PDF files
Files intended for opening in Adobe Reader, Acrobat are in PDF format and are quite dangerous, especially if they are obtained from unreliable sources. Adobe expanded the PDF to the maximum possible level, allowing you to embed all sorts of content there. One of the main advantages of using PDF documents is cross-platform, provided that the reader (Adobe Reader) is available for the platform you need.
In many cases, attackers use exactly malicious PDF files to deliver malware to the user. If the version of Adobe Reader used is vulnerable, there is a high probability of infecting the computer.
In view of the high risks of using PDF documents from unsafe sources, and also taking into account the sluggishness of users in matters of security, modern versions of Adobe Reader have a special "Protected mode" document viewing or "sandboxing" (Protection in an isolated software environment). When using this mode, the code from the PDF file is completely prohibited to perform certain potentially dangerous functions.

Fig. Sandbox settings in Adobe Reader.
By default, protected mode is in the disabled state. Despite the active checkbox “Enable Protected Mode at Startup”, it is disabled because the option to use this mode is in the “Disabled” state. Accordingly, after installing the program, it is highly recommended to transfer this setting to the mode “For files from potentially unsafe sources” or “All files”.
Please note that when you enable Protected Mode, Adobe Reader disables a number of functions that can be used in PDF files. Therefore, when you open the file, you can receive the following notification.

Fig. Tooltip indicating active protected viewing mode.
In case you are sure of the origin of this file, you can activate all its functions by pressing the corresponding button.
Adobe Flash Player
Attackers love Adobe Flash Player very much. Since its plugins for playing content are used in all browsers, searching for vulnerabilities in it and their subsequent use for malicious purposes is a top priority for attackers.
Like other software from Adobe, Flash Player is regularly updated as part of the company's update series (Adobe Security Bulletins). Most of these vulnerabilities are of the Remote Code Execution type, which means that attackers can use this or that vulnerability for remote code execution.
Web browser makers like Adobe do not sit still and embed special exploit protection mechanisms that use Flash Player plugins. Browsers such as MS Internet Explorer (v10 on Windows 8), Google Chrome and Safari OS X (the latest version) launch Flash Player in the context of a sandbox process (i.e., sandboxes), restricting access to this process to many system resources, sites in the file system and work with the network.
A very important feature is the timely update of the Flash Player plugin for the browser. Browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player, so the player for them will be updated automatically.
To check your version of Adobe Flash Player, use the official. adobe source here .
In addition, browsers support the ability to completely disable the plugin Flash Player, to prohibit the browser to play similar content. We have already written a detailed article on the problems of using the Java plugin in browsers here . Disabling the Flash Player plugin is done in the same way.
For Google Chrome.
“Settings” -> “Show advanced settings” -> “Content settings” -> “Disable individual modules”.

For Internet Explorer.
“Service” -> “Configure Add-ons”.

ESET Exploit Blocker
It is an add-on proactive protection in the latest versions of the seventh generation of antivirus products ESET Smart Security and ESET NOD32 Antivirus. Unlike regular static detection by signatures, the Exploit Blocker module analyzes the behavior of an application to perform suspicious actions and techniques used by the exploits. After detecting such actions, they are analyzed and the malicious process is immediately blocked. Some of these actions are subject to additional analysis in our cloud, which provides additional opportunities to protect users from targeted attacks and attacks with the use of 0day exploits.

MS Internet Explorer and Google Chrome
We have already written at the beginning of our material that the most preferred method of attacking users for attackers is remote execution of code through a browser (drive-by download). Anyway, regardless of the installed plugins, the browser itself may contain and, potentially, contains a certain number of vulnerabilities. If the vulnerability has already been investigated by developers and an update has been released for it, the user can install the update and not worry that the attackers will compromise its OS. On the other hand, if attackers exploit a yet unknown vulnerability, i.e., one that has not been closed (0day), the situation is complicated for the user.
Many modern web browsers and operating systems incorporate application process isolation technology, thus preventing any actions that the browser is not allowed to perform. In general, this technique is called sandboxing and allows you to impose restrictions on the actions performed by the process. One example of this isolation is the fact that modern browsers (for example, Internet Explorer and Chrome) execute their tabs as separate processes in the OS, thus allowing you to set permissions to perform certain actions on a particular tab, as well as ensuring the stability of the browser itself. . In case one of the tabs hangs up, the user can complete it without completing the others.
In modern versions of MS Internet Explorer (IE10 & 11), there is a special technology sandboxing called Enhanced Protected Mode. This mode allows you to limit the actions of the tab or plug-in process and thus impede browser exploitation for intruders.
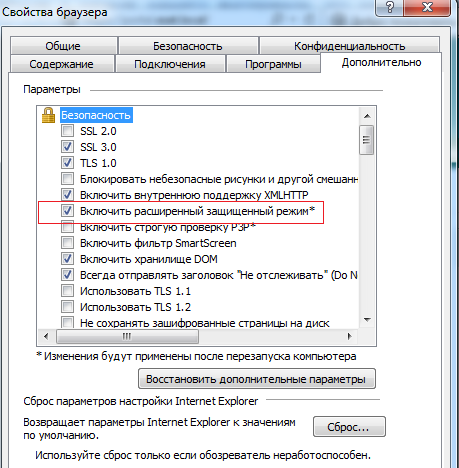
Fig. Sandboxing mode for Internet Explorer, which has been available since version 10.
Enhanced Protected Mode (EPM) was improved for Windows 8. If you use EPM in Windows 7 x64, then this feature allows the browser tabs to run as 64-bit processes (by default, IE runs its tabs as 32-bit processes). Note that EPM is disabled by default.

Fig. Demonstration of EPM on Windows 7 x64 [using MS Process Explorer ]. With this option enabled, browser tab processes are launched as 64-bit, which makes it difficult for them to use to install malicious code.
Starting with Windows 8, Microsoft introduced support for isolating process actions (sandboxing) at the OS level. The technology is called “AppContainer” and allows you to maximize the benefits of this mode for EPM. Internet Explorer tab processes with an active EPM feature work in AppContainer mode. In addition, in Windows 8, EPM is enabled by default.

Fig. Demonstration of EPM on Windows 8, AppContainer (aka sandboxing) is enabled for tabs.

Fig. Differences in EPM performance on Windows 7 & 8.
Google Chrome, like IE, also has special features to prevent drive-by download attacks. But unlike it, the sandboxing mode for Chrome works constantly and does not require additional actions for its inclusion by the user.
Sandboxing mode for Chrome means that tab processes start with reduced privileges, which prevents them from performing various system actions.

Fig. Sandboxing mode as implemented in Google Chrome. Almost all security identifiers of users of SID groups in the access token have Deny status, which prohibits the process from performing important system functions allowed for these groups.

Fig. Chrome uses a special job object to include all browser processes. The object allows you to limit the application's actions in relation to the resources of the OS, preventing exploitation of the browser by attackers.
In addition to this mode, Google Chrome has the ability to block malicious URLs or sites that have been blacklisted by Google as spreading malware ( Google Safe Browsing ). This feature is similar to the URL database in Internet Explorer SmartScreen.

Fig. Google Safe Browsing to Google Chrome in action.
Java
In relation to the browser and OS, it is a virtual machine (or JRE) for running Java applications. Platform independence of such applications makes Java very popular in use, today it is used on more than three billion devices.
Like other browser plugins, the Java plug-in is quite attractive to attackers, and given their previous experience using vulnerabilities, it can be said that Java is the most dangerous component of all other browser plug-ins.
In our previously published material about the problems of using Java on your system, we wrote how you can disable this plugin for different browsers in case you do not use Java applications and do not want to endanger yourself.
When you use Java on Windows, the security settings of this program can be adjusted using the control panel applet. In addition, its latest versions allow you to configure security settings in more detail, which allows you to run only trusted applications.

Fig. Update settings for Java. Check for updates is enabled by default, the user is notified before the operation to download them.
To completely disable Java in all browsers used in the system, remove the “Enable Java content in the browser” setting in the Java applet.

Fig. Removing the tick “Enable Java content in browser” completely disables the ability to use plug-ins in installed browsers.
EMET
Microsoft is releasing a free tool for users that will help protect the OS from attack methods used in exploits.

Fig. EMET interface.
The Enhanced Mitigation Experience Toolkit (EMET) tool uses proactive methods to block various exploit actions to protect applications from attacks. Despite the fact that modern Windows 7 and Windows 8 have built-in, enabled by default, DEP and ASLR capabilities aimed at mitigating the consequences of exploitation, EMET allows you to introduce new opportunities for blocking actions of exploits, as well as enable DEP or ASLR for the necessary processes (enhance the protection of the system on older versions of the OS).
EMET is configured separately for each application, i.e. to protect the application through this tool you need to set it in the appropriate list. In addition, there is a list of applications for which EMET is enabled by default, for example, Internet Explorer, Java, and Microsoft Office software.
For more information about using EMET and an overview of its features, see our corporate blog .
OS
Some components of Windows, which we did not pay special attention to above, can also be used by attackers for remote code execution or elevation of privileges.

Fig. Statistics of fixes for various components of Windows as part of monthly updates patch tuesday. The rating shows components that have been updated more frequently than others in the first half of 2013.
The rating above shows that the largest number of vulnerabilities were closed for Internet Explorer, over twelve updates closed more than fifty vulnerabilities, and six of them had is-being-exploited-in-the-wild status at the time of closure, i.e. were actively exploited by attackers.
The second most fixable component is the well-known driver of the windows subsystem - win32k.sys, which provides the operating system of the graphics system in kernel mode. Vulnerabilities in this component are used by hackers to elevate privileges in the system, for example. circumvention of restrictions imposed by UAC.
Please note that by default in Windows 7 & 8 it is possible to automatically deliver updates to the user. You can also check for updates via the control panel.


[1] The Security Architecture of the Chromium Browser link
[2] Understanding IE Enhanced Protected Mode link
For the user, the most dangerous scenario is the use of an exploit by hackers that allows you to remotely install the code in the OS. In this case, it is enough for a person to visit a compromised web resource for infection with a malicious code (drive-by). If a vulnerable version of the software is installed on your computer: the browser or plug-ins to it, then the probability that you will be able to get infected with malicious code is very high.

')
It is good practice to update the OS, as well as the installed software, since manufacturers regularly close the newly emerging vulnerabilities in it. Among the components through which the user is at particular risk are the following:
- Browsers (MS Internet Explorer, Google Chrome, Apple Safari OS X, Mozilla Firefox, etc.).
- Plugins for browsers (Adobe Flash Player, Oracle Java, MS Silverlight).
In case of special targeted attacks or watering hole attacks, attackers can exploit 0day vulnerabilities in software and OS. Vulnerabilities are of the same name, which at the time of their use by the attackers were not yet closed by the vendor.
Anti-virus products can detect exploits by signatures. Thus, it allows you to protect the user from malicious content on the fly by blocking the relevant web page with malicious content.
Modern editions of Microsoft Windows: Windows 7, 8 and 8.1 have built-in mechanisms that protect the user from the destructive actions of exploits. These features include:
- DEP & ASLR mechanisms that significantly impede the ability to exploit a particular vulnerability in software and OS by imposing restrictions on the use of non-executable memory and program placement in memory at arbitrary addresses. DEP & ASLR on Windows 7+ are used at the highest possible level.
- User Account Control, UAC , which has been finalized since Windows 7 and requires confirmation from the user to run programs that need to change system settings and create files in system directories.
- SmartScreen for OS filter (starting with Windows 8 for OS), which helps prevent a user from downloading malware from the Internet based on his Microsoft reputational information.
- Special “Enhanced Protected Mode” for Internet Explorer (starting with IE 10). On Windows 8, it allows you to launch browser tabs in the context of isolated processes that are limited in performing certain actions. For Windows 7, x64 allows launching browser tabs as separate 64-bit processes.
PDF files
Files intended for opening in Adobe Reader, Acrobat are in PDF format and are quite dangerous, especially if they are obtained from unreliable sources. Adobe expanded the PDF to the maximum possible level, allowing you to embed all sorts of content there. One of the main advantages of using PDF documents is cross-platform, provided that the reader (Adobe Reader) is available for the platform you need.
In many cases, attackers use exactly malicious PDF files to deliver malware to the user. If the version of Adobe Reader used is vulnerable, there is a high probability of infecting the computer.
In view of the high risks of using PDF documents from unsafe sources, and also taking into account the sluggishness of users in matters of security, modern versions of Adobe Reader have a special "Protected mode" document viewing or "sandboxing" (Protection in an isolated software environment). When using this mode, the code from the PDF file is completely prohibited to perform certain potentially dangerous functions.

Fig. Sandbox settings in Adobe Reader.
By default, protected mode is in the disabled state. Despite the active checkbox “Enable Protected Mode at Startup”, it is disabled because the option to use this mode is in the “Disabled” state. Accordingly, after installing the program, it is highly recommended to transfer this setting to the mode “For files from potentially unsafe sources” or “All files”.
Please note that when you enable Protected Mode, Adobe Reader disables a number of functions that can be used in PDF files. Therefore, when you open the file, you can receive the following notification.

Fig. Tooltip indicating active protected viewing mode.
In case you are sure of the origin of this file, you can activate all its functions by pressing the corresponding button.
Adobe Flash Player
Attackers love Adobe Flash Player very much. Since its plugins for playing content are used in all browsers, searching for vulnerabilities in it and their subsequent use for malicious purposes is a top priority for attackers.
Like other software from Adobe, Flash Player is regularly updated as part of the company's update series (Adobe Security Bulletins). Most of these vulnerabilities are of the Remote Code Execution type, which means that attackers can use this or that vulnerability for remote code execution.
Web browser makers like Adobe do not sit still and embed special exploit protection mechanisms that use Flash Player plugins. Browsers such as MS Internet Explorer (v10 on Windows 8), Google Chrome and Safari OS X (the latest version) launch Flash Player in the context of a sandbox process (i.e., sandboxes), restricting access to this process to many system resources, sites in the file system and work with the network.
A very important feature is the timely update of the Flash Player plugin for the browser. Browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player, so the player for them will be updated automatically.
To check your version of Adobe Flash Player, use the official. adobe source here .
In addition, browsers support the ability to completely disable the plugin Flash Player, to prohibit the browser to play similar content. We have already written a detailed article on the problems of using the Java plugin in browsers here . Disabling the Flash Player plugin is done in the same way.
For Google Chrome.
“Settings” -> “Show advanced settings” -> “Content settings” -> “Disable individual modules”.

For Internet Explorer.
“Service” -> “Configure Add-ons”.

ESET Exploit Blocker
It is an add-on proactive protection in the latest versions of the seventh generation of antivirus products ESET Smart Security and ESET NOD32 Antivirus. Unlike regular static detection by signatures, the Exploit Blocker module analyzes the behavior of an application to perform suspicious actions and techniques used by the exploits. After detecting such actions, they are analyzed and the malicious process is immediately blocked. Some of these actions are subject to additional analysis in our cloud, which provides additional opportunities to protect users from targeted attacks and attacks with the use of 0day exploits.

MS Internet Explorer and Google Chrome
We have already written at the beginning of our material that the most preferred method of attacking users for attackers is remote execution of code through a browser (drive-by download). Anyway, regardless of the installed plugins, the browser itself may contain and, potentially, contains a certain number of vulnerabilities. If the vulnerability has already been investigated by developers and an update has been released for it, the user can install the update and not worry that the attackers will compromise its OS. On the other hand, if attackers exploit a yet unknown vulnerability, i.e., one that has not been closed (0day), the situation is complicated for the user.
Many modern web browsers and operating systems incorporate application process isolation technology, thus preventing any actions that the browser is not allowed to perform. In general, this technique is called sandboxing and allows you to impose restrictions on the actions performed by the process. One example of this isolation is the fact that modern browsers (for example, Internet Explorer and Chrome) execute their tabs as separate processes in the OS, thus allowing you to set permissions to perform certain actions on a particular tab, as well as ensuring the stability of the browser itself. . In case one of the tabs hangs up, the user can complete it without completing the others.
In modern versions of MS Internet Explorer (IE10 & 11), there is a special technology sandboxing called Enhanced Protected Mode. This mode allows you to limit the actions of the tab or plug-in process and thus impede browser exploitation for intruders.

Fig. Sandboxing mode for Internet Explorer, which has been available since version 10.
Enhanced Protected Mode (EPM) was improved for Windows 8. If you use EPM in Windows 7 x64, then this feature allows the browser tabs to run as 64-bit processes (by default, IE runs its tabs as 32-bit processes). Note that EPM is disabled by default.

Fig. Demonstration of EPM on Windows 7 x64 [using MS Process Explorer ]. With this option enabled, browser tab processes are launched as 64-bit, which makes it difficult for them to use to install malicious code.
Starting with Windows 8, Microsoft introduced support for isolating process actions (sandboxing) at the OS level. The technology is called “AppContainer” and allows you to maximize the benefits of this mode for EPM. Internet Explorer tab processes with an active EPM feature work in AppContainer mode. In addition, in Windows 8, EPM is enabled by default.

Fig. Demonstration of EPM on Windows 8, AppContainer (aka sandboxing) is enabled for tabs.

Fig. Differences in EPM performance on Windows 7 & 8.
Google Chrome, like IE, also has special features to prevent drive-by download attacks. But unlike it, the sandboxing mode for Chrome works constantly and does not require additional actions for its inclusion by the user.
Sandboxing mode for Chrome means that tab processes start with reduced privileges, which prevents them from performing various system actions.

Fig. Sandboxing mode as implemented in Google Chrome. Almost all security identifiers of users of SID groups in the access token have Deny status, which prohibits the process from performing important system functions allowed for these groups.

Fig. Chrome uses a special job object to include all browser processes. The object allows you to limit the application's actions in relation to the resources of the OS, preventing exploitation of the browser by attackers.
In addition to this mode, Google Chrome has the ability to block malicious URLs or sites that have been blacklisted by Google as spreading malware ( Google Safe Browsing ). This feature is similar to the URL database in Internet Explorer SmartScreen.

Fig. Google Safe Browsing to Google Chrome in action.
Java
In relation to the browser and OS, it is a virtual machine (or JRE) for running Java applications. Platform independence of such applications makes Java very popular in use, today it is used on more than three billion devices.
Like other browser plugins, the Java plug-in is quite attractive to attackers, and given their previous experience using vulnerabilities, it can be said that Java is the most dangerous component of all other browser plug-ins.
In our previously published material about the problems of using Java on your system, we wrote how you can disable this plugin for different browsers in case you do not use Java applications and do not want to endanger yourself.
When you use Java on Windows, the security settings of this program can be adjusted using the control panel applet. In addition, its latest versions allow you to configure security settings in more detail, which allows you to run only trusted applications.

Fig. Update settings for Java. Check for updates is enabled by default, the user is notified before the operation to download them.
To completely disable Java in all browsers used in the system, remove the “Enable Java content in the browser” setting in the Java applet.

Fig. Removing the tick “Enable Java content in browser” completely disables the ability to use plug-ins in installed browsers.
EMET
Microsoft is releasing a free tool for users that will help protect the OS from attack methods used in exploits.

Fig. EMET interface.
The Enhanced Mitigation Experience Toolkit (EMET) tool uses proactive methods to block various exploit actions to protect applications from attacks. Despite the fact that modern Windows 7 and Windows 8 have built-in, enabled by default, DEP and ASLR capabilities aimed at mitigating the consequences of exploitation, EMET allows you to introduce new opportunities for blocking actions of exploits, as well as enable DEP or ASLR for the necessary processes (enhance the protection of the system on older versions of the OS).
EMET is configured separately for each application, i.e. to protect the application through this tool you need to set it in the appropriate list. In addition, there is a list of applications for which EMET is enabled by default, for example, Internet Explorer, Java, and Microsoft Office software.
For more information about using EMET and an overview of its features, see our corporate blog .
OS
Some components of Windows, which we did not pay special attention to above, can also be used by attackers for remote code execution or elevation of privileges.

Fig. Statistics of fixes for various components of Windows as part of monthly updates patch tuesday. The rating shows components that have been updated more frequently than others in the first half of 2013.
The rating above shows that the largest number of vulnerabilities were closed for Internet Explorer, over twelve updates closed more than fifty vulnerabilities, and six of them had is-being-exploited-in-the-wild status at the time of closure, i.e. were actively exploited by attackers.
The second most fixable component is the well-known driver of the windows subsystem - win32k.sys, which provides the operating system of the graphics system in kernel mode. Vulnerabilities in this component are used by hackers to elevate privileges in the system, for example. circumvention of restrictions imposed by UAC.
Please note that by default in Windows 7 & 8 it is possible to automatically deliver updates to the user. You can also check for updates via the control panel.


[1] The Security Architecture of the Chromium Browser link
[2] Understanding IE Enhanced Protected Mode link
Source: https://habr.com/ru/post/200156/
All Articles