Authorization through Radius on Mikrotik with local group substitution
Good day to all! I work as a novice network administrator in a large federal company with a mixed network, cisco, mikrotik, juniper.
And once the next task appeared.
Initial data:
1. There is a regional system administrator who has several system administrators under his authority. Each system administrator has an RU - a regional node, where the head units are 2 Mikrotik 1100ahx2 and cisco c3550, for shopping - MikroTik RB751G-2HnD.
2. On each Mikrotika, a local group was established with the name coinciding with the city: Omsk - OMS, Kemerovo - KMR, with full rights to Mikrotik.
')
Task:
To make authorization of the regional administrator through Radius only within their area of responsibility, let's say OMS and KMR.
The task is, we try to perform.
Configure Radius on Mikrotik:
/ radius add service = login address = 10.0.x.10 secret = xxx disabled = no
/ user aaa set use-radius = yes
Install FreeRadius on Linux, I had Debian: apt-get install freeradius
I have a subnet on Mikrotika 172.16.0.0/12,
write in /etc/freeradius/clients.conf
client 172.16.0.0/12 {
secret = xxx
shortname = Network_Devices
}
Then, do not forget / etc / freeradius / dictionary
VENDOR Mikrotik 14988
BEGIN-VENDOR Mikrotik
ATTRIBUTE Mikrotik-Recv-Limit 1 integer
ATTRIBUTE Mikrotik-Xmit-Limit 2 Integer
ATTRIBUTE Mikrotik-Group 3 string
ATTRIBUTE Mikrotik-Wireless-Forward 4 integer
ATTRIBUTE Mikrotik-Wireless-Skip-Dot1x 5 integer
ATTRIBUTE Mikrotik-Wireless-Enc-Algo 6 integer
ATTRIBUTE Micro-Wireless-Enc-Key 7 string
ATTRIBUTE Micro-Rate-Limit 8 string
ATTRIBUTE Mikrotik-Realm 9 string
ATTRIBUTE Mikrotik-Host-IP 10 ipaddr
ATTRIBUTE Mikrotik-Mark-Id 11 string
ATTRIBUTE Mikrotik-Advertise-URL 12 string
ATTRIBUTE Mikrotik-Advertise-Interval 13 integer
ATTRIBUTE Mikrotik-Recv-Limit-Gigawords 14 integer
ATTRIBUTE Mikrotik-Xmit-Limit-Gigawords 15 integer
ATTRIBUTE Mikrotik-Wireless-PSK 16 string
ATTRIBUTE Mikrotik-Total-Limit 17 integer
ATTRIBUTE Mikrotik-Total-Limit-Gigawords 18 integer
ATTRIBUTE Micro-Address-List 19 string
ATTRIBUTE Mikrotik-Wireless-MPKey 20 string
ATTRIBUTE Mikrotik-Wireless-Comment 21 string
ATTRIBUTE Micro-Delegated-IPv6-Pool 22 string
# MikroTik Values
VALUE Mikrotik-Wireless-Enc-Algo No-encryption 0
VALUE Mikrotik-Wireless-Enc-Algo 40-bit-WEP 1
VALUE Mikrotik-Wireless-Enc-Algo 104-bit-WEP 2
VALUE Mikrotik-Wireless-Enc-Algo AES-CCM 3
VALUE Mikrotik-Wireless-Enc-Algo TKIP 4
END-VENDOR Mikrotik
Everything, now we need to create a user in / etc / freeradius / users:
regSA User-password: = 12345
Auth-Type = CHAP,
Mikrotik-Group: = OMS
Restart FreeRadius and try to access Omsk Mikrotik. Everything is working.
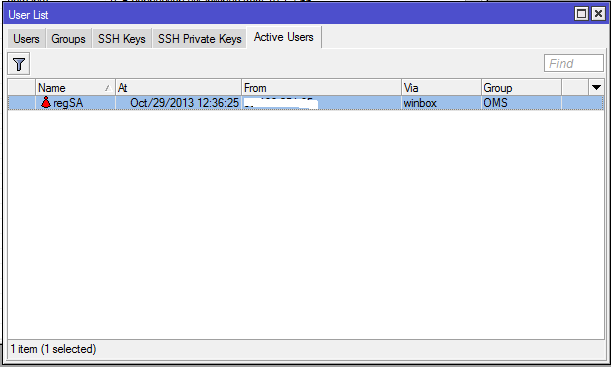
But now we try to go to Kemerovo. We get the group read, with read-only rights. What's the matter? We look at the log on Mikrotik and see:
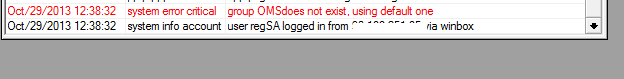
In active users:
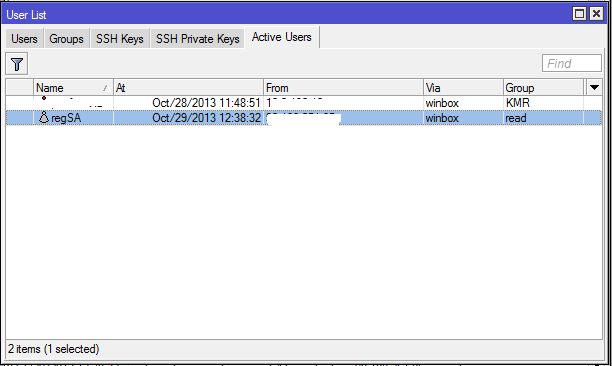
You forgot to register a group for Kemerovo, you say. Registering:
regSA User-password: = 12345
Auth-Type = CHAP,
Mikrotik-Group: = OMS, KMR
Restart freeradius. We try, we get the same thing. It turns out that for one user we can specify only one group. Because at authorization the first one is always taken. Dead end? No, a couple of Google hours, research FreeRadius and find a way out.
There is a post-auth handler in radiusd.conf, I decide to try using it.
We write:
post-auth {
if (User-Name == "regSA") {check the username
if (NAS-IP-Address = ~ /172\.22\.(2(2[4-9`[[-4-4[0-9 greet5 -9] | [1-9] [0-9] | 1 ([0-9] [0-9]) | 2 ([0-4] [0-9] | 5 [0-5])) /) {and check IP
update reply {
Mikrotik-Group: = “OMS” if everything came together, then we give out a group of microtics on it
}
}
if (NAS-IP-Address = ~ /172\.20\.(6 [a4-9 ]|[7-8rals [0-9 ]|9[0-5 [/ i] )\\.([0-9] | [1-9] [0-9] | 1 ([0-9] [0-9]) | 2 ([0-4] [0-9] | 5 [0-5])) /) {
update reply {
Mikrotik-Group: = "KMR"
}
}
}
} close the whole post-auth
NAS-IP-Address is the IP address from which the authorization request arrives. A regular schedule is used, but since I am with you, I used www.analyticsmarket.com/freetools/ipregex for generating
Now in / etc / freeradius / users: we remove the group as an absolutely unnecessary attribute for us
regSA User-password: = 12345
Auth-Type = CHAP
After the restart of FreeRadius, we understand that everything works for us, that the regional gets into Omsk microtics with the OMS group, and the Kemerovo ones with KMR.
Why it was impossible to put in users Mikrotik-Group: = "full"? It was possible, but then the regional sysadmin gained access to all Mikrotikam throughout Russia, which of course is not good. Only the elect have such rights.
And once the next task appeared.
Initial data:
1. There is a regional system administrator who has several system administrators under his authority. Each system administrator has an RU - a regional node, where the head units are 2 Mikrotik 1100ahx2 and cisco c3550, for shopping - MikroTik RB751G-2HnD.
2. On each Mikrotika, a local group was established with the name coinciding with the city: Omsk - OMS, Kemerovo - KMR, with full rights to Mikrotik.
')
Task:
To make authorization of the regional administrator through Radius only within their area of responsibility, let's say OMS and KMR.
The task is, we try to perform.
Configure Radius on Mikrotik:
/ radius add service = login address = 10.0.x.10 secret = xxx disabled = no
/ user aaa set use-radius = yes
Install FreeRadius on Linux, I had Debian: apt-get install freeradius
I have a subnet on Mikrotika 172.16.0.0/12,
write in /etc/freeradius/clients.conf
client 172.16.0.0/12 {
secret = xxx
shortname = Network_Devices
}
Then, do not forget / etc / freeradius / dictionary
VENDOR Mikrotik 14988
BEGIN-VENDOR Mikrotik
ATTRIBUTE Mikrotik-Recv-Limit 1 integer
ATTRIBUTE Mikrotik-Xmit-Limit 2 Integer
ATTRIBUTE Mikrotik-Group 3 string
ATTRIBUTE Mikrotik-Wireless-Forward 4 integer
ATTRIBUTE Mikrotik-Wireless-Skip-Dot1x 5 integer
ATTRIBUTE Mikrotik-Wireless-Enc-Algo 6 integer
ATTRIBUTE Micro-Wireless-Enc-Key 7 string
ATTRIBUTE Micro-Rate-Limit 8 string
ATTRIBUTE Mikrotik-Realm 9 string
ATTRIBUTE Mikrotik-Host-IP 10 ipaddr
ATTRIBUTE Mikrotik-Mark-Id 11 string
ATTRIBUTE Mikrotik-Advertise-URL 12 string
ATTRIBUTE Mikrotik-Advertise-Interval 13 integer
ATTRIBUTE Mikrotik-Recv-Limit-Gigawords 14 integer
ATTRIBUTE Mikrotik-Xmit-Limit-Gigawords 15 integer
ATTRIBUTE Mikrotik-Wireless-PSK 16 string
ATTRIBUTE Mikrotik-Total-Limit 17 integer
ATTRIBUTE Mikrotik-Total-Limit-Gigawords 18 integer
ATTRIBUTE Micro-Address-List 19 string
ATTRIBUTE Mikrotik-Wireless-MPKey 20 string
ATTRIBUTE Mikrotik-Wireless-Comment 21 string
ATTRIBUTE Micro-Delegated-IPv6-Pool 22 string
# MikroTik Values
VALUE Mikrotik-Wireless-Enc-Algo No-encryption 0
VALUE Mikrotik-Wireless-Enc-Algo 40-bit-WEP 1
VALUE Mikrotik-Wireless-Enc-Algo 104-bit-WEP 2
VALUE Mikrotik-Wireless-Enc-Algo AES-CCM 3
VALUE Mikrotik-Wireless-Enc-Algo TKIP 4
END-VENDOR Mikrotik
Everything, now we need to create a user in / etc / freeradius / users:
regSA User-password: = 12345
Auth-Type = CHAP,
Mikrotik-Group: = OMS
Restart FreeRadius and try to access Omsk Mikrotik. Everything is working.

But now we try to go to Kemerovo. We get the group read, with read-only rights. What's the matter? We look at the log on Mikrotik and see:

In active users:

You forgot to register a group for Kemerovo, you say. Registering:
regSA User-password: = 12345
Auth-Type = CHAP,
Mikrotik-Group: = OMS, KMR
Restart freeradius. We try, we get the same thing. It turns out that for one user we can specify only one group. Because at authorization the first one is always taken. Dead end? No, a couple of Google hours, research FreeRadius and find a way out.
There is a post-auth handler in radiusd.conf, I decide to try using it.
We write:
post-auth {
if (User-Name == "regSA") {check the username
if (NAS-IP-Address = ~ /172\.22\.(2(2[4-9`[[-4-4[0-9 greet5 -9] | [1-9] [0-9] | 1 ([0-9] [0-9]) | 2 ([0-4] [0-9] | 5 [0-5])) /) {and check IP
update reply {
Mikrotik-Group: = “OMS” if everything came together, then we give out a group of microtics on it
}
}
if (NAS-IP-Address = ~ /172\.20\.(6 [a4-9 ]|[7-8rals [0-9 ]|9[0-5 [/ i] )\\.([0-9] | [1-9] [0-9] | 1 ([0-9] [0-9]) | 2 ([0-4] [0-9] | 5 [0-5])) /) {
update reply {
Mikrotik-Group: = "KMR"
}
}
}
} close the whole post-auth
NAS-IP-Address is the IP address from which the authorization request arrives. A regular schedule is used, but since I am with you, I used www.analyticsmarket.com/freetools/ipregex for generating
Now in / etc / freeradius / users: we remove the group as an absolutely unnecessary attribute for us
regSA User-password: = 12345
Auth-Type = CHAP
After the restart of FreeRadius, we understand that everything works for us, that the regional gets into Omsk microtics with the OMS group, and the Kemerovo ones with KMR.
Why it was impossible to put in users Mikrotik-Group: = "full"? It was possible, but then the regional sysadmin gained access to all Mikrotikam throughout Russia, which of course is not good. Only the elect have such rights.
Source: https://habr.com/ru/post/199474/
All Articles