As I did not hack "Habrahabr" or 10+ active XSS

Seeing how everyone rushed to look for XSS on a beautiful blue Habrahabr decided to try his luck. POST self-xss, useless in many contexts and vectors, starting with filtering in the most popular browsers (chrome / safari / ie etc) and ending with the complexity of their application and operation, it was decided to leave the rest of the pioneers and go in search of something more standing
Attempt number one
First, it was decided to check the authorization and registration. I missed that “wonderful” XSS found in this post , apparently being late for several days (and what would have happened if the thought came to search a little earlier?). I'm not a fan of abstruse XSS search and test tools, and I prefer the very convenient functionality built into Chrome, which allows you to copy all the headers in curl and use them through the console.
After playing with the parameters and finding nothing, out of habit, I checked how the 302 redirect works in the wrong way and it turned out that it was not at all like on the main domain.
Sending to the server:
')
curl 'https://auth.habrahabr.ru//%22%3E%3Ch1%3Etest'A very interesting answer was received:
<html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <title> !</title> </head> <body> <a href="http://habrahabr.ru/auth/"><h1>test/">http://habrahabr.ru/auth/"><h1>test/</a> </body> </html> As you can see from the request, the first insertion of uri is not filtered, the second is filtered, which at first glance causes XSS. However, having tried the attack through normal browsers and not seeing the promised XSS, I decided to dig deeper and saw that the tricky server not only adds slash to the end, because of which the server showed us 404 instead of a redirect (rather strange rule for a web server?), So also throws on habrahabr.ru/auth/%xss% before it has time to execute js from our bugs. The first problem was solved easily and quickly - all that had to be done was to put the "?", So that everything else would be “dropped” as the GET parameter:
curl 'https://auth.habrahabr.ru//%22%3E%3Ch1%3Etest?'Now the answer was:
<html> <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8"> <title> !</title> </head> <body> <a href="http://habrahabr.ru/auth/"><h1>test?/">http://habrahabr.ru/auth/"><h1>test?/</a> </body> </html> The second problem I did not manage to solve. The code stubbornly did not have time to execute, except on IE <8 or through the same Kurl.
What I just did not try with grief, for example, to remove the meta-refresh:
var mr = document.getElementById("meta-refresh"); mr.parentNode.removeChild(mr); But, unfortunately, the zero refresh time did not leave me any chances and I went on a further search, as I was not satisfied with such a lack of vulnerability.
Attempt number 2
After the first file, it was decided not to give up and try their hand at other parts of the site. Using the magical and timeless Google found several old and new pages of paid promo various companies. The latest promo pages resisted all attacks very seriously, the output data was escaped, in some places even twice. Remembering the various contests where Habr allows ordinary mortals to register, I went to habrahabr.ru/special/miss , tried to use a nickname with special characters in the registration:

Confirming the registration, I saw a long-awaited alert:
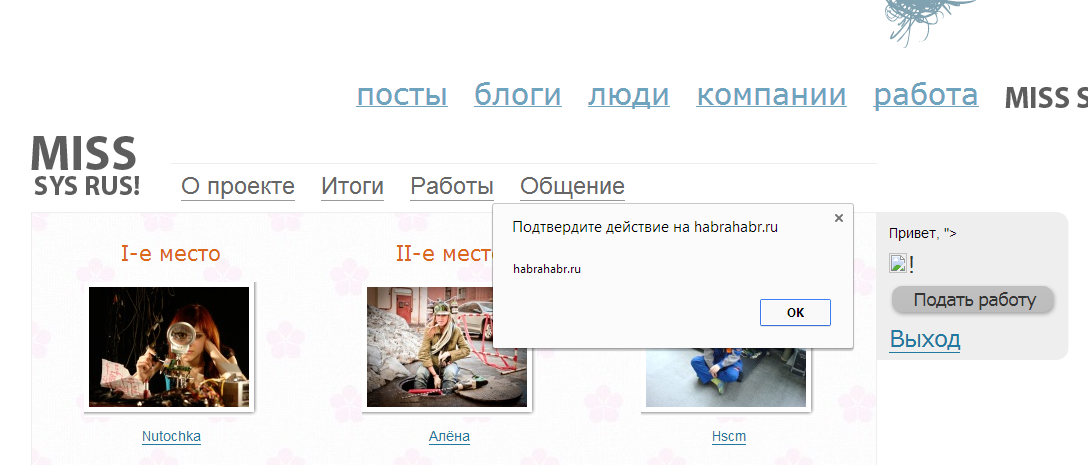
It was impossible to dwell on it, because it is displayed after authorization, in the block that the user sees. You could of course authorize the user through CSRF (it was just in the form of authorization), and then redirect him to our XSS, but these are not our methods.
Not finding my ID in any cookie or anywhere else, I began to search through the maximum profile id and found it:

Perhaps it was possible to stop at this and report to the administration, there is an active XSS, she is not afraid of any browser filters ... but ... but we wanted more!
Google power
habrahabr active xss dork:
site:.habrahabr.ru/special inurl:register
Google gave about 10+ results, of which the majority were, some were barely working at all, were partially covered, such as habrahabr.ru/special/panasonic/3d .
I tried to register and saw a bummer: the panel with the username did not open, the comments were not sent ... nothing worked. Nothing worked until I looked at the source of the page and saw a wonderful thing:
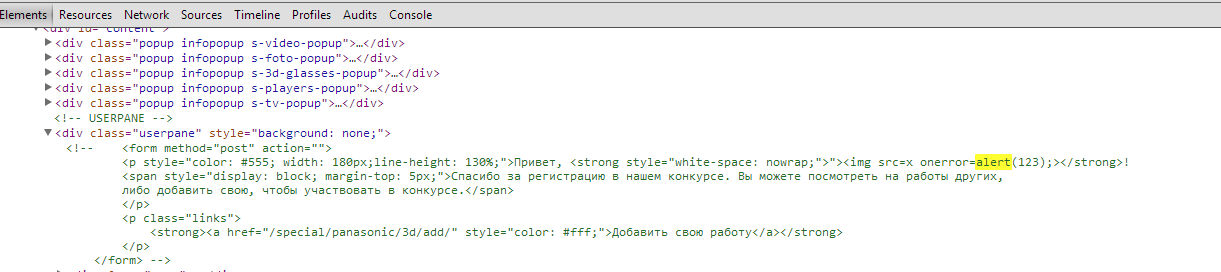
An attentive person would immediately add the nickname to the beginning when registering "->" and get a fully working website:
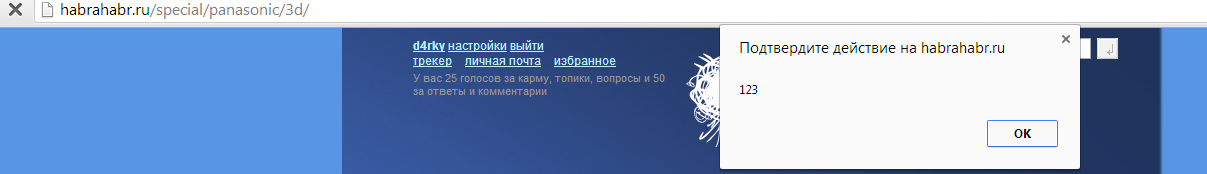
What in html-ke looked like:
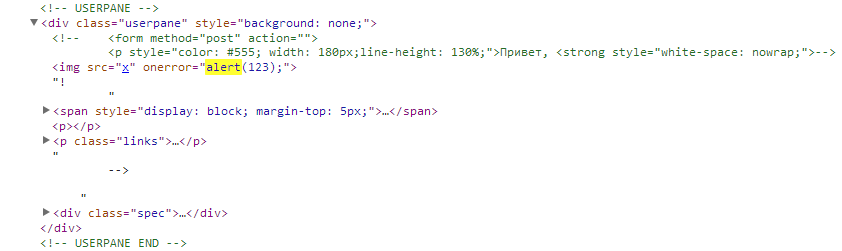
Then I walked through all sorts of hurry pages and collected screenshots for the administration and this article.
XSS in profile output in comments:
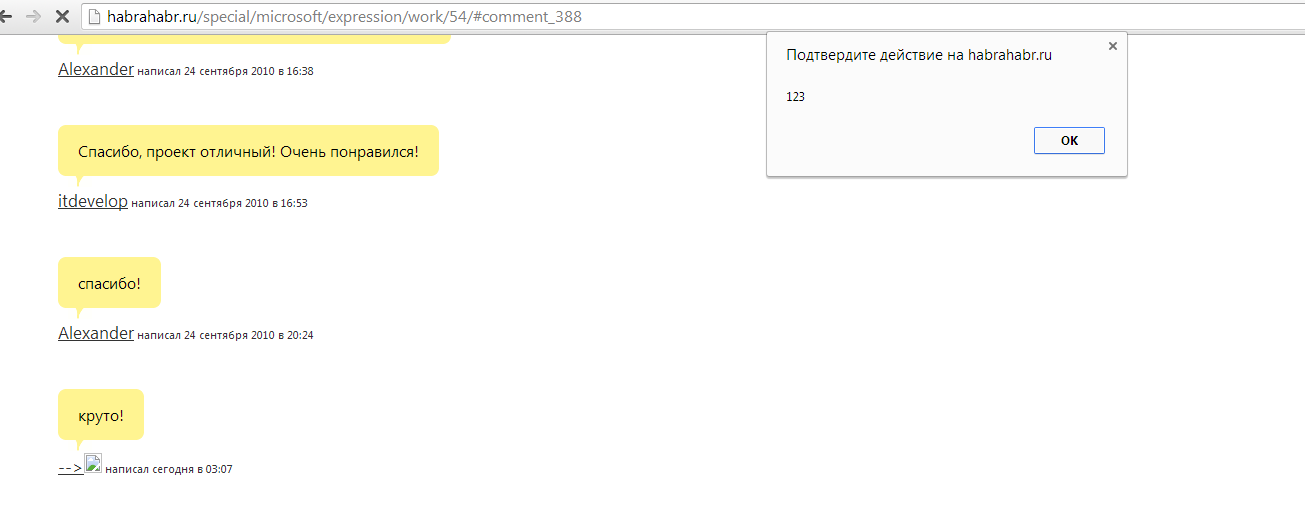
Similar XSS on a couple more projects:

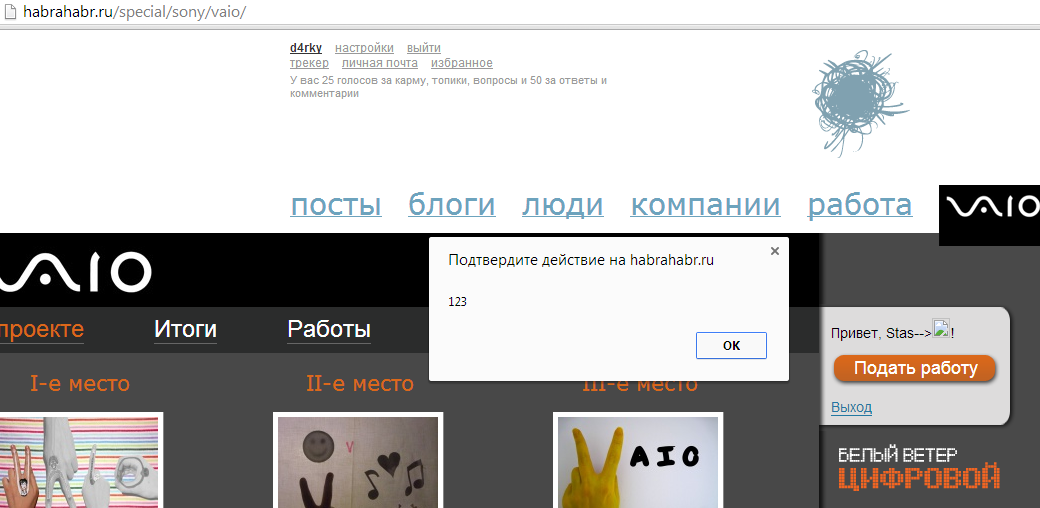
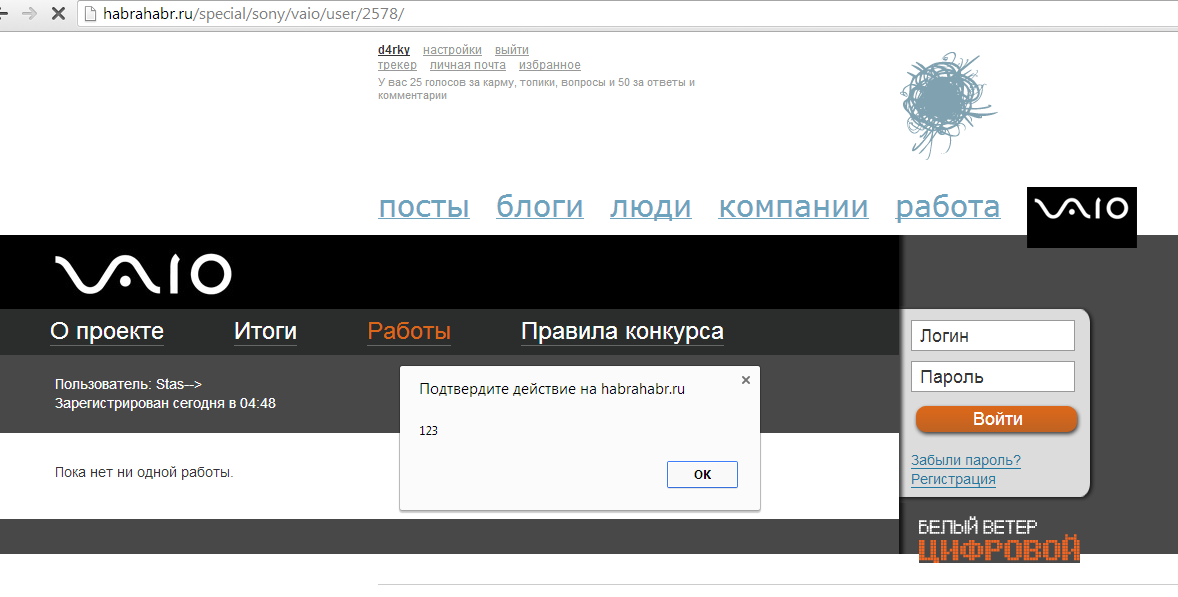




Results
As a result, more than 10 active XSSs were found (there were about three different types of truth, though, and one passive XSS under one, for which I received 100,500 gift invites!) Maybe I missed the non-indexed pages, or simply did not notice the unfiltered output of data in some places of these promo, but at the moment everything is promptly corrected by the administration, for which she thanks a lot!
Source: https://habr.com/ru/post/197672/
All Articles