Another software tab in D-Link routers

On the information portal devttys0.com, someone Craig Heffner - an experienced specialist in the field of reverse engineering - posted an article-study on another ( already found ) software tab in D-Link routers. This time the tab was revealed in the official firmware for the DIR-100 revA , but, in his opinion, is present in the routers of other series:
- DIR-100
- DI-524
- DI-524UP
- DI-604S
- DI-604UP
- DI-604 +
- TM-G5240
- Planex BRL-04UR
- Planex BRL-04CW
In short, if your browser has a User-Agent installed as “xmlset_roodkcableoj28840ybtide” , then you automatically get admin's access to the web control panel of the router without any authorization.
First of all, the author downloaded the official firmware firmware v1.13 for the DIR-100 (the same is used for its DI-524). Then I went through the binary with my binwalk utility and took out SquashFS with the system, from where I took the / bin / webs web server and uploaded it to IDA:

')
Judging by the lines, / bin / webs is a modified version of thttpd . The authors of the modification are Alphanetworks, a division of D-Link, all of the added methods begin with the alpha prefix:
alpha_auth_check
This feature seems the most interesting. A detailed analysis reveals that it compares strings — a string with an offset of 0xD0 in the http_request_t structure and the constant xmlset_roodkcableoj28840ybtide . If they match, then alpha_auth_check immediately returns 1 (successful authorization).
The author googled the xmlset_roodkcableoj28840ybtide constant and found the only mention in the Russian forum: http://forum.codenet.ru/q58748 . Messages are dated 2010, but no one mentioned how this line is used in the binary.
Continuing the study, Craig finds that at offset 0xD0 in the http_request_t structure , the data is written with the function httpd_parse_request .
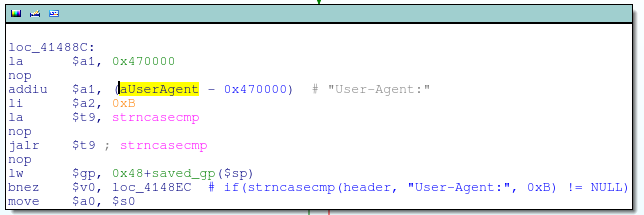

Gathering all the information received together, the author eventually compiles the following pseudo-code for the function alpha_auth_check :
#define AUTH_OK 1 #define AUTH_FAIL -1 int alpha_auth_check(struct http_request_t *request) { if(strstr(request->url, "graphic/") || strstr(request->url, "public/") || strcmp(request->user_agent, "xmlset_roodkcableoj28840ybtide") == 0) { return AUTH_OK; } else { // These arguments are probably user/pass or session info if(check_login(request->0xC, request->0xE0) != 0) { return AUTH_OK; } } return AUTH_FAIL; } You stay classy, D-Link.
UPD: In the comments report new finds:
- DIR-300NRU rev. B5 firmware 1.4.3
- DIR-120 H / W Ver .: A1 F / W Ver .: 1.02
Source: https://habr.com/ru/post/197314/
All Articles