Integrating clouds - create a site-to-site connection between Amazon Web Services and Windows Azure
This article demonstrates how to use Windows Azure virtual networks (Windows Azure Virtual Network, VNET) to create an IPsec tunnel to connect to the Virtual Private Cloud (VPC) environment located in Amazon Web Services (AWS). Using this guide, you can literally keep your work environments in each of the clouds with full network communication between the virtual machines they contain through a secure IPsec tunnel. This approach can easily be used to implement a fault tolerance scenario, backup, or even migration between cloud providers. The software VPN that is used in this article for testing is Open Swan .
Create a VPC in Amazon AWS
To begin with, on the Amazon side, create a virtual virtual cloud (VPC), which is equivalent to a virtual network in Windows Azure.
Create VPC - public subnet with internet gateway

')
I chose 10.0.0.0/16 address space for the Amazon VPC network.

Create an EC2 instance that will be used to host Open Swan and will be the entry point of the tunnel from Amazon.
Running Ubuntu 13.04 on a VPC subnet

Specify the subnet and I recommend increasing the size of the instance from Micro to Small.

Once the instance is created, switch to EC2 view and highlight the new Elastic IP. This will be your external IP address, which you will use to connect via SSH and when connecting to your Windows Azure virtual network.
Click Yes Allocate in the dialog box for selecting the new IP address.

Select an instance from the drop-down menu and click Yes Associate.

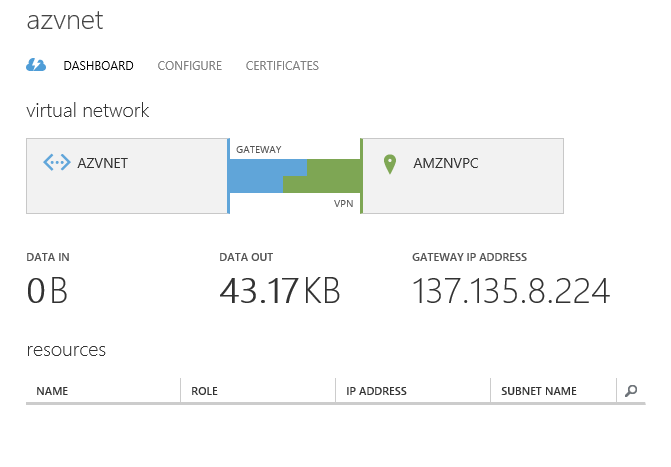
Creating a virtual network in Windows Azure
Before configuring the Open Swan service, we need to create the reverse side of the network in Windows Azure. To create an IPsec tunnel, the Open Swan service requires the IP address of the gateway and the authentication key to be obtained from the virtual network in Windows Azure.
Create a virtual network in Windows Azure

Specify Data Center Location and VNET / Affinity Group Name options

Select the site-to-site VPN option

Determine the network properties, which in our case are the parameters of Amazon VPC Address Space and Elastic IP server Open Swan Server

Determine the Windows Azure Address Space. Make sure you add a gateway subnet (gateway subnet).

Creating a Windows Azure Virtual Network Gateway
After creating the virtual network, open it and click “create gateway” -> select “static routing”.

After creating the gateway, you can get the IP address and authentication key and configure Open Swan on the Amazon side.

Configure Open Swan on Amazon Web Services
Connect to Open Swan VM
Switch to the instance view and select your instance, on the Actions menu, click Connect.
Select Connect with a standalone SSH client .

Copy the command for SSH (or use PuTTY) to connect via SSH.

Once connected, install and configure the Open Swan for the VPN solution on the Amazon side.
Install Open Swan
sudo apt-get install openswan
Select NO to install the certificate as we will use key-based authentication.

The following steps will require you to use a text editor to modify some configuration files.
Edit the ipsec.conf file
cd / etc
sudo vi ipsec.conf After opening, go to edit mode: * i
Replace the existing configuration with the following settings:
config setup
protostack = netkey
nat_traversal = yes
virtual_private =% v4: 10.0.0.0/16
oe = off include /etc/ipsec.d/*.conf Exit and save settings :: x
Change the ipsec.d directory and create a new amznazure.conf file.
cd ipsec.d sudo vi amznazure.conf
Content amznazure.conf
conn amznazure
authby = secret
auto = start
type = tunnel
left = 10.0.0.28
leftsubnet = 10.0.0.0 / 16
leftnexthop =% defaultroute
right = [WINDOWS AZURE GATEWAY IP]
rightsubnet = 172.16.0.0 / 16
ike = aes128-sha1-modp1024
esp = aes128-sha1
pfs = no Notes to these parameters:
- left = the local IP address of the Open Swan Server
- leftsubnet = local address space of servers in VPC
- right = IP address of the Windows Azure Gateway VNET Gateway (replace it with yours)
- rightsubnet = Windows Azure Virtual Network address space
After specifying the settings, you can specify the authentication key.
cd / etc sudo vi ipec.secrets
Add a line to the file in the following format (do not add []):
10.0.0.28 [WINDOWS AZURE GATEWAY IP]: PSK "[WINDOWS AZURE GATEWAY KEY]"
Next, enable IP forwarding in Open Swan VM:
sudo vi /etc/sysctl.conf
Uncomment the line:
net.ipv4.ip_forward = 1
Apply new settings:
sudo sysctl -p /etc/sysctl.conf
Next, disable source / destination checking in the Open Swan server.


Configure Security Groups to access traffic from Windows Azure
In the Amazon management console, select Security Groups and -> amzn-azure-group.
Add two additional UDP rules inbound rules - one for 500 and one for 4500 using Windows Azure GW IP with / 32 CIDR.

sudo service ipsec restart
Connect Windows Azure virtual network to Amazon AWS Virtual Private Cloud

Routing Setup
The reason for using the Amazon AWS VPN software solution is that the AWS network stack supports routing table configuration, while Windows Azure does not (yet) allow it.
In the Amazon control panel, go back to the VPC view and select the route tables. Select the route table associated with your VPC and add a new route to the 172.16.0.0/16 (Windows Azure Network) and this will allow traffic to be routed via the Open Swan server instance ID.
Update route information

Creating instances to test connectivity
Create an AWS instance on the VPC subnet.

Run an instance in Windows Azure on the previously created virtual network.

In each instance, you will need to enable ICMP rules for each VM in order to test communication with PING.
We ping Azure VM from Amazon VM through the IPsec tunnel

Pinging Amazon VM from Azure VM via IPsec tunnel

It's all!
Now you can host applications on Amazon AWS and Windows Azure and connect them to each other through a secure IPsec tunnel over the Internet.
Source: https://habr.com/ru/post/196798/
All Articles