Steal-kill, write-swing
In January of this year , a vulnerability was found in one of the ICQ services. It was associated with access to files that users once passed to each other. The vulnerability was eliminated, but such situations are by no means unique.
Below we will consider another service designed for file sharing between users.
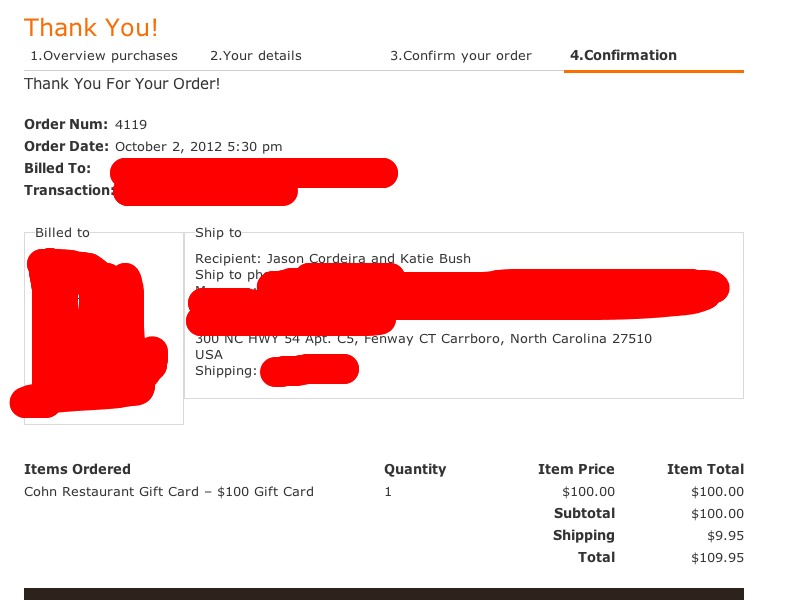
Today, one of the customers sent me a TK using the site droplr.com. The service is really convenient. I do not use all sorts of dropboxes and the like simply because of the low speed of the Internet. But I liked this service, everything is quite convenient, the interface, the clients for different platforms, but most importantly, you can download other people's files.
When I clicked on the link from the customer, it became clear that the droplr uses a link shortener. As a result, the page for downloading the file looks like this:
In the case of the first entry, only one lower case character is used, which, as time has shown, is completely indifferent to the system.
The second sequence 4 characters long can consist of lowercase, uppercase Latin characters and numbers.
Given that the service is used by a huge mass of people, we can assume that when bruteforcing the second parameter, we will often come across other people's files, because the total number of possible options is 14776336.
Usually, I write such tasks in PHP or the BASH goal, there is everything you need, right out of the box. But I need to develop, so I decided to stay with Python, since I already have some experience with it.
')
Judging by the task, we need to somehow access the service, in Python there are many implementations and interfaces for this, I decided to stop at requests , since this library has all the requirements that we need.
In case you have a pip, the installation will take only a few seconds.
To parse the page there is a powerful library called BeautifulSoup . Installation via pip is also elementary.
You can download the script on GitHub .
As I thought, after the first 5 minutes of work, about 10 images with personal data were found, and what else!
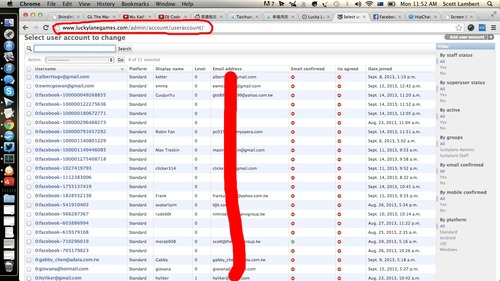
Admin site, including some data about users.
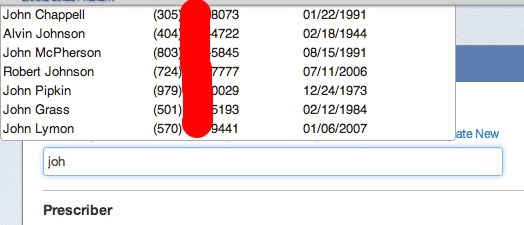
And here are the phone numbers
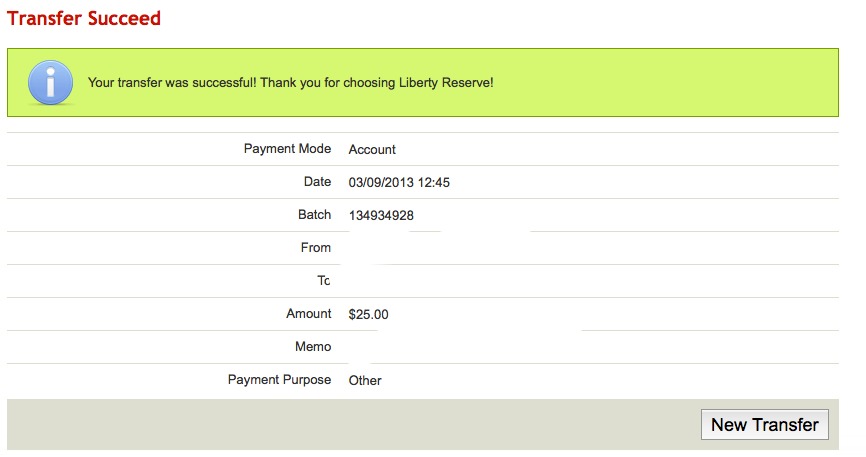
One day in the life of LR.

From the category, on the friend, buy at my expense.
I think this is enough to demonstrate 5 minutes of the script.
Be careful, do not publish personal and payment information to the network.
The site has absolutely no checks on the bot. We do not even need to send the user agent. Naturally, there is no ban for multiple requests.
A direct link to the file lives for about a minute, a new link can be obtained only after visiting the file download page.
Approximately 80% of random links point to files.
UP # 1 user lybin added multithreading support .
UP # 2 no more HEAD request, all in one GET, added User Agent, Referer and timeout.
Below we will consider another service designed for file sharing between users.

Today, one of the customers sent me a TK using the site droplr.com. The service is really convenient. I do not use all sorts of dropboxes and the like simply because of the low speed of the Internet. But I liked this service, everything is quite convenient, the interface, the clients for different platforms, but most importantly, you can download other people's files.
When I clicked on the link from the customer, it became clear that the droplr uses a link shortener. As a result, the page for downloading the file looks like this:
d.pr[az]{1}/[A-z0-9]{4}In the case of the first entry, only one lower case character is used, which, as time has shown, is completely indifferent to the system.
The second sequence 4 characters long can consist of lowercase, uppercase Latin characters and numbers.
Given that the service is used by a huge mass of people, we can assume that when bruteforcing the second parameter, we will often come across other people's files, because the total number of possible options is 14776336.
Usually, I write such tasks in PHP or the BASH goal, there is everything you need, right out of the box. But I need to develop, so I decided to stay with Python, since I already have some experience with it.
')
Judging by the task, we need to somehow access the service, in Python there are many implementations and interfaces for this, I decided to stop at requests , since this library has all the requirements that we need.
In case you have a pip, the installation will take only a few seconds.
pip install requestsTo parse the page there is a powerful library called BeautifulSoup . Installation via pip is also elementary.
pip install beautifulsoup4You can download the script on GitHub .
As I thought, after the first 5 minutes of work, about 10 images with personal data were found, and what else!

Admin site, including some data about users.

And here are the phone numbers

One day in the life of LR.

From the category, on the friend, buy at my expense.
I think this is enough to demonstrate 5 minutes of the script.
Be careful, do not publish personal and payment information to the network.
Some features
The site has absolutely no checks on the bot. We do not even need to send the user agent. Naturally, there is no ban for multiple requests.
A direct link to the file lives for about a minute, a new link can be obtained only after visiting the file download page.
Approximately 80% of random links point to files.
UP # 1 user lybin added multithreading support .
UP # 2 no more HEAD request, all in one GET, added User Agent, Referer and timeout.
Source: https://habr.com/ru/post/196672/
All Articles