EFF accuses NSA of violating Creative Commons license
Yesterday, The Guardian published a selection of NSA presentations on how the agency de-anonymizes Tor users ( presentation 1 , presentation 2, presentation 3 ). In short, the algorithm is to monitor several Tor nodes, as well as to recognize (fingerprinting) Tor clients in the place where traffic goes from a Tor node to a specific site, for example, Google. Such requests are intercepted by means of hidden servers of the NSA on the main communication channels. Then, on Tor users' computers, the FoxAcid exploit pack is applied, containing exploits for Firefox 10.0 ESR 0day vulnerabilities (this browser was used in the Tor Browser Bundle client software bundle at the time of the NSA presentations).
Interestingly, one of their presentations ( this ) NSA began with an explanation of what the Tor network is. And in this explanation they used illustrations from the site of the Foundation for Electronic Frontiers (under the cut).
Here are these illustrations.
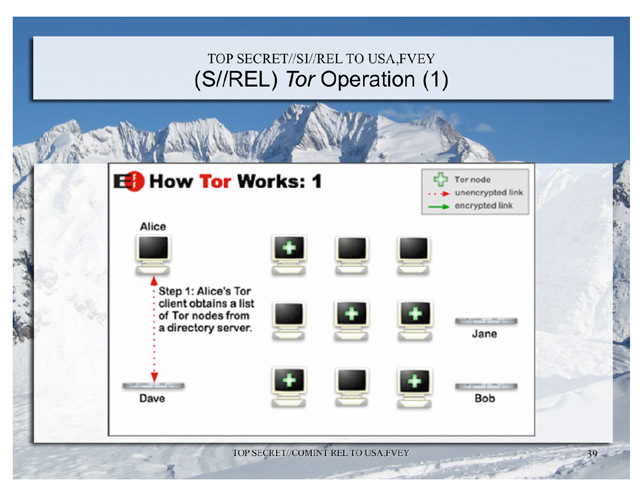
')
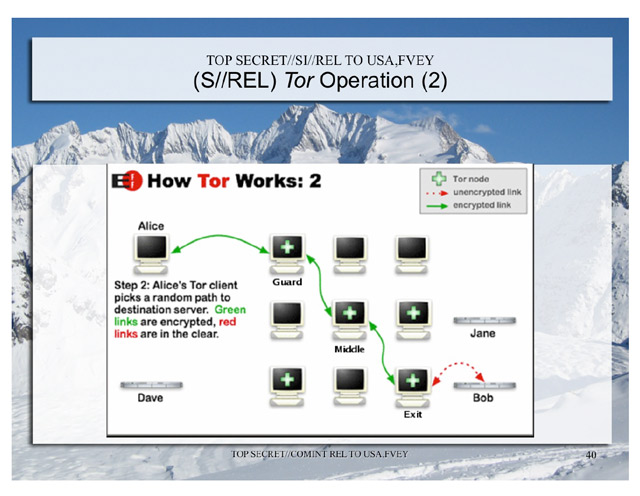
Actually, but the source from where they took the NSA.
Probably, the Electronic Frontier Foundation should be pleased that its materials are valued at the highest level, but still they decided to comment on the situation.
“It's good that the NSA uses our Tor manual. But they violate the CC license when they classify their derivative work as top secret, ”EFF says on Twitter.
Indeed, the terms of Creative Commons do not allow the author to prohibit the spread of his derivative work. And the status of “Top Secret” at the NSA presentation just implies a ban on the distribution and publication of the work.
The terms of the Creative Commons Attribution License (CC BY 3.0 US) also require the indication of the author of the original work. Here the NSA acted lawfully - the EFF logo is present in the presentation.
Interestingly, one of their presentations ( this ) NSA began with an explanation of what the Tor network is. And in this explanation they used illustrations from the site of the Foundation for Electronic Frontiers (under the cut).
Here are these illustrations.

')

Actually, but the source from where they took the NSA.
Probably, the Electronic Frontier Foundation should be pleased that its materials are valued at the highest level, but still they decided to comment on the situation.
“It's good that the NSA uses our Tor manual. But they violate the CC license when they classify their derivative work as top secret, ”EFF says on Twitter.
Indeed, the terms of Creative Commons do not allow the author to prohibit the spread of his derivative work. And the status of “Top Secret” at the NSA presentation just implies a ban on the distribution and publication of the work.
The terms of the Creative Commons Attribution License (CC BY 3.0 US) also require the indication of the author of the original work. Here the NSA acted lawfully - the EFF logo is present in the presentation.
Source: https://habr.com/ru/post/196472/
All Articles