Hideninja VPN application launch history for Android (Part 1): First prototype, first hacking In-App Purchase
We got hacked! We got hacked!- my reaction to the in-app purchase of my “Hideninja VPN” application for Android did not differ in originality. But I wrote about this only in the penultimate paragraph. And before it there are a few more lines about what kind of project this “Hideninja VPN” is. I will also talk about how the path from the first prototype was covered, how the project came out in top-5 at the request of “vpn” in English-language Google Play, how the redesign influenced the users' perception of the application, the collection of rakes and, finally, about hacking In-App Purchase . Of course, I divided this material into several parts, otherwise it would be absolutely tiring to read it. So, Part 1.
Here it is, hacked “Version 3.3 PRO”.
')
What are we talking about?
I am sure that you already have a question, what kind of project is this “Hideninja VPN”. If you are familiar with what VPN is , then you already know what kind of service and user value we are talking about: this is a VPN service for Android, today offering the user to connect to one of 20 own servers around the world . When you connect your device to “Hideninja VPN”, all your traffic is encrypted on your device, passes through the server you selected in “Hideninja VPN”, at the output c from which your real IP address changes to a server IP address that is different from your real one.
In Russia, for the present, we are practically unlimited in our movement on the Internet, whereas in the West, and especially in the countries of the East, the problem of censorship on the Internet is very acute, which is confirmed by our statistics, which will be discussed below. In the most neglected cases, people without VPN do not have access to Facebook, YouTube, Skype and other popular services, you can not even mention the problem of accessing torrent sites and avoiding the risk of being caught downloading illegal content - this problem fades before the pain of not being able to log in on Facebook.
So, statistics. The application “Hideninja VPN” was launched on Google Play in January 2013, as of September 2013: it has been downloaded more than 300,000 times, has more than 135,000 regular active users, both indicators are growing.

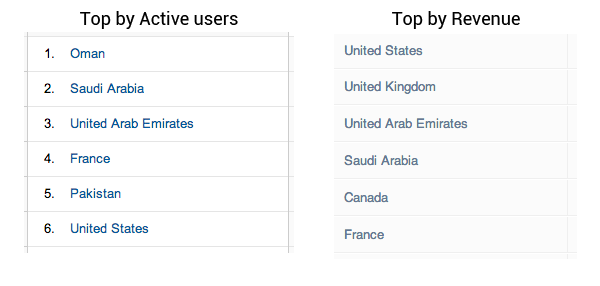
The application is especially popular in the countries of the East, but - I won’t be surprised - the main paying users are from the USA, Great Britain - compare the top countries of active users (left) and the top countries by income (right):
How it all began
In January 2013, I conducted a study and saw that in the VPN market for Android, among more than 1000 applications, there is not one that would suit me with its UI and UX, price, speed, but especially - UI and UX. Rereading user reviews from top-5 VPN applications, I realized that I was not alone.
Looking at the number of downloads on Google Play among the leaders of VPN applications (over 7 million in total among players from top-3 on the query “vpn”), I formulated the following simple hypothesis: once users download and use products with low quality UI and UX, with slow connection speeds and annoying advertisements or restrictions, and besides, they also buy paid functions and subscriptions in these applications, they will have to download and use a much more convenient application, while developing all knowledge about competitors' shortcomings will be taken into account.
If there is a hypothesis - it is necessary to prove it. And the solution is better than going along the path of creating an MVP (Minimum Viable Product) and releasing it on Google Play, I have not found.
First prototype
Testing the idea of launching a prototype with a minimum set of functions (MVP) for real users, from a business and marketing point of view, is a quick and cheap way to test and collect first opinions about the idea of a product; To do this without a prototype is much more difficult. From a technical point of view, MVP is a set of crutches, glued together, and working on an honest word, and that is exactly what the first prototype of “Hideninja VPN” looked inside (and also outside).
So, what I had at the time of the creation of the first prototype:
- irresistible desire to make some convenient application
- understanding how to implement VPN based on fresh Android API
Yes, in fact, nothing more was available, the lack of those or other necessary resources, as well as knowledge and skills in bringing mobile applications to the market, was covered with energy from an irresistible desire to do something of their own, necessarily cool and useful to people.
By a short search, a suitable implementation variant of the OpenVPN protocol for Android was found, although only for version 4 and higher, but at the beginning of 2013 it did not seem such a big problem - the total share of downloads of applications from the Tools category, most suitable for VPN on Google Play, from all versions 4ki has already strived with a good pace to 50%, which proved that support for versions 2.x would not be profitable.
I made the simplest UI of the first prototype myself by adding one Connect / Disconnect button, displaying the IP and country of the VPN server to which you are connecting to, and also several suggestions for at least some empty space:
Looking ahead, I’ll say that only the 3rd major version of the application came to me with an understanding of which UI & UX would be really convenient for the user. Read this in the next section.
The first prototype was able to connect a user to only one server (there was no possibility to select a server) and display the status of connected / disconnected.
Of course, this was not yet the most convenient and fast application I was aiming for, but the first prototype showed me that there is still room for new players on the Android VPN market, which means that it makes sense to continue testing our hypothesis.
Is it really scary hacking in-app purchase
And again I am running ahead: in the next part of the article I will talk about how we entered the market, how we started monetization. Here I will only say that the option In-App Purchase was chosen, which, as it turned out, is ridiculously easy to crack!
September, rain, 3 o'clock in the morning, accidentally stumble upon a branch about my project at w3bsit3-dns.com, to which I was very surprised, as the Russian-language Google Play was never in our priority, and we didn’t show any marketing activity aimed at Russian-speaking users.
I start reading the first post, I reach the attached files and I see that two files are attached - the free version and the PRO version, which can be obtained only by paying 49.99 rubles. (price for Russia) through the mechanism of in-app purchase.

My first reaction - oh well, of course, this is how PRO lies for everyone. But after I installed the hacked version on an absolutely clean smartphone with a fresh Google Account, everything fell into place, and I was literally furious!
I note that until that moment I did not study the topic of hacking applications, otherwise I would immediately understand everything, moreover, I would insist on the introduction of at least standard protection tools - ProGuard and License Verification Library (but they are also successfully cracked by simple methods). It is especially important to protect yourself from hacking if you use the built-in Google Play tools (In-app Billing Version 3 API) to control and manage purchases and subscriptions, and not your own server.
But do not be sensitive to hacking. Where better to start working with the audience, which we did. We launched a campaign on w3bsit3-dns.com where we offer users to get PRO for free: absolutely legally and without the use of hacking. This gave us loyal users, with whom we now constantly keep in touch and ask to help us if we need to test new versions.
Experience
Be sure to explore competitors and the market; as soon as the application has basic functionality, albeit less than that of the competitors, it should be laid out on the platform for testing.
It is not necessary to rush in blind rage at those who hacked you, it is much wiser to see in this the advantages for the project and use them for good.
What's next in the story
I will talk about how we have done even from the first prototype to the current version of the application. For now, here's what all 3 versions look like, which were released, as they say, feel the difference (the first prototype, 2.0, 3.0, respectively):

Source: https://habr.com/ru/post/196238/
All Articles