The history of the pirate scene

Over the past year I have published on Habré about a dozen articles about the scene . This is a pirate underground, thousands and tens of thousands of enthusiasts around the world who compete with each other in speed, making releases only inside - on the stage, while not extracting any financial gain. In 2007–2008, there was an aboutthescene site, where the main information about the structure, mechanisms and rules of the scene, as well as the history of its origin and development, was published. Now site materials are available only in the online archive .
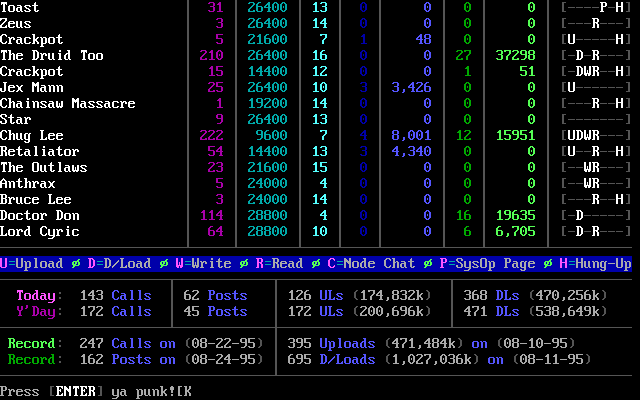
I started the translation from the scene history. The article was without illustrations, so I added to it historical screenshots of 1995 with the largest in New York BBS "Park Central", which shows how up to 16 users simultaneously connect to it using modems at speeds from 9600 to 28800 baud.
1. The origin of the PC scene
Ever since it became possible to store data on computers and sell commercial programs, there have always been pirates. The pirate scene dates back to the late 70s, and maybe even earlier. By the early 1980s, some computers (for example, BBC Micro in Europe) were so occupied by pirates that software companies gave up. They stopped making programs for these computers, because they could not earn money at all. But this article only concerns the PC scene.
')
In the early 80s there was a huge number of different 8-bit computers, this time was called the Golden Era. Most people agree that at the time the best scene was the Commodore 64 scene. But this was not the first organized international pirate scene. The first analogue of the modern cut-out Internet scene can be called the Apple II pirates at the very end of the 70s.
It was the pirate scene Commodore and Apple introduced many of the standards that we see today, and the first IBM PCs were released in mid-1981. The PC scene was then small and fragmented. There were several small groups and individuals who opened the programs and released them. However, these releases usually remained only within local communities. The national and then the international PC scene started only in 1987. Then people began to exchange data through long-distance lines and across the ocean. This event led to the formation of the now-history PC scene of the BBS PC ( Bulletin Board System ).
2. The era of the BBS
The first BBS program, CBBS (Community Bulletin Board System), was written for the Altair 8080 computer in 1987. It was slow, buggy, and purely textual. Gradually, it developed and gained popularity, but the main breakthrough came when it became possible to transfer files using a specially developed protocol X-Modem. This protocol was created by Ward Christenson and Randy Suess (authors of CBBS). It provided error-free data transfer between users of most of the then existing systems. Then the exchange of “illegal” programs began, which ultimately devoted BBS to piracy.
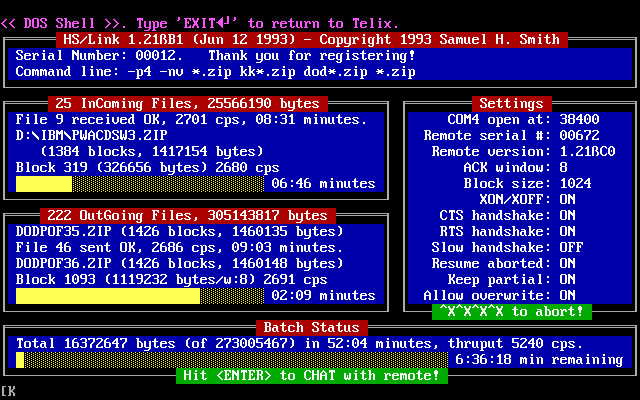
BBS-ki began to appear in different cities and countries. Users who have bothered the local archives began to try to call other sites on the intercity. Unfortunately, such calls led to huge phone bills, so resourceful people quickly found ways to call for free. For this purpose, special electronic devices, known as “box”, were used .
These first telephone hackers were called phreakers. Most of them were mainly engaged in HPAV (Hacking, Phreaking, Anarchy, Virus), and piracy for them was in the background. Because of this, the IBM PC scene was slow and fragmented; release distribution across North America could take weeks. In the 1980s, the IBM PC and Commodore 64 were common in ordinary American homes, while Amstrad, Spectrum, Commodore, and Atari dominated Europe instead, and the IBM PC was rare.
The problem was that not many pirates knew what phreaking was, and it was very expensive to pay for intercity. However, around 1988 a group of a new type appeared - NAP / PA. It was the North American Pirate Phreak Alliance (North American Pirate Alliance) and its goal was to spread the knowledge of phreaking among pirates. Many of the largest pirated BBS-ki collaborated with them, disseminating information, which made it possible to more closely combine the scene.
Releases spread slowly - we had to call each BBS separately, and the speeds of the modems were limited. From those times the famous phrase “0 day warez” went. This meant that you received a release the same day it was released. The phrase is often used to refer to good BBS approx.
Gradually, with the expansion of the scene, the role of the phreaker turned into the role of a courier. The only task of the courier was to shift releases between BBS-kami. What exactly to shift and where depended on communications between release groups. At the beginning of the 90s, couriers were considered on stage not as respected as the rest. Being a courier was not difficult, almost anyone could handle it. It was necessary to take risks and spend time on it, but no special skills or abilities were required.
At that time, many BBSes had to pay monthly fees for partnerships with groups. Relationships in the groups were important, as they gave the opportunity to receive their releases first, which increased the prestige of the site. Sysops (BBS operators) usually did not like to pay out of pocket, so they created special accounts, known as 'leech accounts'. These were users who received full access to Wares for money, as they had no connections in the pirate world, and could not offer anything else in return.
The money received from partner nodes was used by groups to purchase software and hardware, and to pay third parties. (comment. I do not know what I mean, maybe the seller in the store, so he gave them to rewrite the floppy disks?) A group that did not have money, risked remaining without releases. As a result, the BBS sysop had to pay these fees, pay phone bills, and buy equipment that he himself needed. But this financial investment paid off with great respect from its users.
3. Legal issues
Keeping a BBS with illegal software was a risky business. Unlike today's Internet sites, they are usually located right at the sysop at home. Therefore, the police could easily determine the address of the operator. The phone number for which they called the BBS-ku was often registered in the name of its owner. For this reason, the scene was very secret and underground. Phone numbers and names were communicated only to people you knew well. To gain access, it was necessary to find out the system password and the second password for registering a new user. The decision on whether to accept a new participant was taken by vote or on the recommendation.
There were good reasons for such secrecy. Some companies are eager to block the illegal flow of their programs. These corporations, including Microsoft and Novell, worked with local and federal police in the hope of closing down pirated BBS. For this purpose, informers or undercover agents who collected evidence were used to carry out a capture operation.
Interestingly, before adopting the Net Act in the United States in the late 1990s, piracy was not a criminal offense. Therefore, they usually arrested only people who tried to earn money from it. The police could not arrest you if you just exchanged copies of programs for free.
Another option to fight against pirates was the institution of a civil case. There was nothing good about this either, and usually the case ended in the complete confiscation of all computer equipment in the house. Such cases were started by large companies, and they were considered according to completely different rules, unlike criminal ones. It is difficult to judge how effective these measures were; let's say, some companies were more successful than others. At one time in the mid-90s, many BBS-ki completely banned laying out product releases Novell. This was the result of their successful anti-piracy activities, which in a few years destroyed several of the largest BBS-ok across the world.

4. Text files
Unfortunately, there are very few historical documents from the PC scene of the 80s. Unlike Commodore 64, Amiga and Atari, text files for releases were almost never made at that time. The programs were then opened by individuals, not groups. These people usually left their signature, for example, on the game screensaver in the lower corner of the cracked by Lord Blix. By the end of the 80s, more and more groups began to appear, and to maintain prestige, they sometimes began to insert additional screens made specifically for each release into the games. For example, Bentley Sidewell Productions, a well-known band from the late 80s, usually used a CGA shny picture or animation to show that they had opened the game. International Network of Crackers used ANSI graphics.
If the one who hacked the program wanted to add some information, he would attach a text file to the release. Over time, all groups began to add explanatory text to their releases. Usually it was a message from the hacker, some information about how to play the game (for example, the keys used), and sometimes a list of BBS numbers ok.
It was in the 80s that hacker groups were the first to use abbreviations to hide their name. Perhaps this has knocked down any of the detractors, but the main thing is that it was just a shorter way to type the name. Reducing to 3 letters became the standard in the early 90s. This was due to the limitation of the length of the file name (8 characters, 3 characters of extension). Around that time, groups began to adhere to the constant format in file names. The program name was reduced to 8 characters, with the extension .DOC, or three-letter designation of the group name.
As far as we know, the existing .NFO standard was introduced in 1990 by The Humble Guys. First, the 8-letter name of the file corresponded to the name of the game, with time it was replaced by the name of the group.
5. Death of floppy disks
Simultaneously with the development of the Internet, the gaming industry revolutionized the scene using CDROMs. Although games on a CD for PC appeared as early as 1989, the scene did not switch to this new medium until the mid-90s. And even then, no one took him seriously, and the groups basically created separate subgroups for CD-ROM releases. This was done to ensure that all "junk" was issued under a different name. They called it “crapware” - something like modern iND releases.
First, release groups of the entire CD, but not in ISO format, but simply all the files copied from the disc. But people are not used to such large volumes, and then the European group Hybrid invented the first CD-Rip. They threw away unnecessary parts of the game, such as music or speech. People who made rips thought in categories of diskettes: the smaller the volume, the better. Therefore, the games turned out to be too circumcised, in addition, they did not spend too much effort on opening them, so third-party utilities, such as CD emulators, were often required to run.
When game makers began to usefully use all available space on the CD, most of the scene groups adopted a new standard. The limit on the size of releases has been increased. In 1997, when the prices of recordable CDs fell, and there was a demand for full disc images, ISO groups appeared, but this was already in a new era, the Internet era.
6. Death BBS-ok and the arrival of the Internet
Most would agree that the end of the old era came when in 1996 Park Central closed in New York city. At the time, it was the most respected and well-known BBS in the world, the center of communication for the entire scene. Groups have always competed, who will make the first release: if two groups released a program at the same time, the winner was the one that spreads its version to a larger number of BBS. Park Central has often been in this process an informal arena and referee.

Some tricky groups were the first to decide to leave BBS-ok and distribute their releases only on the Internet. This put the scene in an incomprehensible situation, when one group won with the release among BBS, and the other on the Internet. Although the BBS system had prestige and history, everyone understood that its departure was only a matter of time.
The last nail in the coffin of the system was the infamous Cyberstrike campaign in February 1997, when the five largest BBS-ok were covered by the FBI in one week. Operation Cyber Strike was the result of an 8-month closed investigation conducted by the FBI’s International Computer Crime Unit in San Francisco. Searches were conducted in 10 locations in the United States. This caused many other BBS and some sites to close forever, fearing that they could be the next victim.
For various reasons, the scene used the Internet, but until the early 90s, no one took it seriously. At that time, people could not imagine how much the Internet would change the scene, and that piracy of a new generation would actually arise.
At the time of the BBS, piracy was a secret affair defined by the underground. It was incredibly difficult for a beginner to get access even to the usual local BBS. Most people faced the difficult task of getting a system password, just to go in there, and then a second password to send a request for registration.
But the Internet has changed everything: everything that was once difficult was made incredibly simple. IRC, e-mail, FTP, and the web have opened up vast opportunities for piracy for ordinary users. And since 1994, they have rushed there in flocks, causing despair attacks to many of the old actors. Many of them could not stand the fact that so-called lamers flooded their territory and closed their doors. But although the old doors were closing, new ones opened: newsgroups, websites, anonymous FTP and IRC servers — they were ready to meet the needs of the masses.
The dominant among these new methods of piracy have become IRC channels. Initially, they were created by stsenovyh groups to transfer releases to their friends, but once FATE (Fast Action Transfer Exchange, the leading courier group of 1995) opened its #fatefiles channel to the public, and the public did not refuse. Then many followed their example, which caused discontent on the stage, many groups did not approve of this practice at all.
Over time, the popularity of these methods has passed like a honeymoon, but they have left some niche for themselves. Many of them turned out to be too complicated for the ordinary public, while others, such as sites that are in the top 100, often turned out to be just scammers whose owners made money on porn advertising.
As a result, the scene was finally fenced off from the public, and after numerous FBI operations that took place in the early and mid-2000s, it became even more secret and closed than in the days of the BBS. Piracy has become mainstream, millions of ordinary people participate in it, gradually mastering new technologies - peer-to-peer networks, starting with napster, and ending with torrents. And the stage still keeps its traditions: the stage is only for sceners and no business.
Source: https://habr.com/ru/post/196022/
All Articles