Zabbix + Cisco ISR: we monitor the loading of VPN tunnels via SNMP + Perl script + LLD
Task: There is a Cisco router with a bunch of configured site-to-site IPsec-VPN tunnels. You need to configure the monitoring of loading of tunnels in Zabbix 2.0.x
It is assumed that SNMP on Ziska and Zabbix is already configured.
The main problem is that we need to monitor the SNMP OIDs with traffic counts are dynamically generated. Moreover, the lists of these numbers are also formed dynamically.
This is due to the fact that the tunnel building algorithm itself is rather complicated. First, an ISAKMP service tunnel is formed, then a basic IPSEC tunnel for data. You can read more about this here: linkmeup.ru/blog/50.html (by the way, an excellent training cycle of articles by this author on the basics of configuring Cisco equipment was already on Habré).
The specific algorithm for extracting the cherished traffic samples is so muddy that it seems impossible to implement it using the purely built-in Zabbix tools. Why, even the artistic transfer did not work for me. Let me describe from the forum www.networking-forum.com :
')
Fortunately, good people from the Cacti forum wrote a pearl-barley script that does all the dirty work by itself.
Download the script and drop it into the ExternalScripts folder (/ usr / local / share / zabbix / externalscripts by default).
Since there are many tunnels and sometimes they change, we apply LLD (low-level detection rules) in Zabbix so that all the tunnels themselves are detected and registered in our system.
We make a new pattern, and in it - the detection rule and prototypes of data elements for incoming and outgoing traffic:


Full key: query_asa_lan2lan.pl ["{$ SNMP_COMMUNITY}", "{HOST.IP}", "ASA", "get", "RX", "{#SNMPVALUE}"]
Link in the description of OID: tools.cisco.com/Support/SNMP/do/BrowseOID.do?local=en&translate=Translate&objectInput=1.3.6.1.4.1.9.9.171.1.2.3.1.35#oidContent
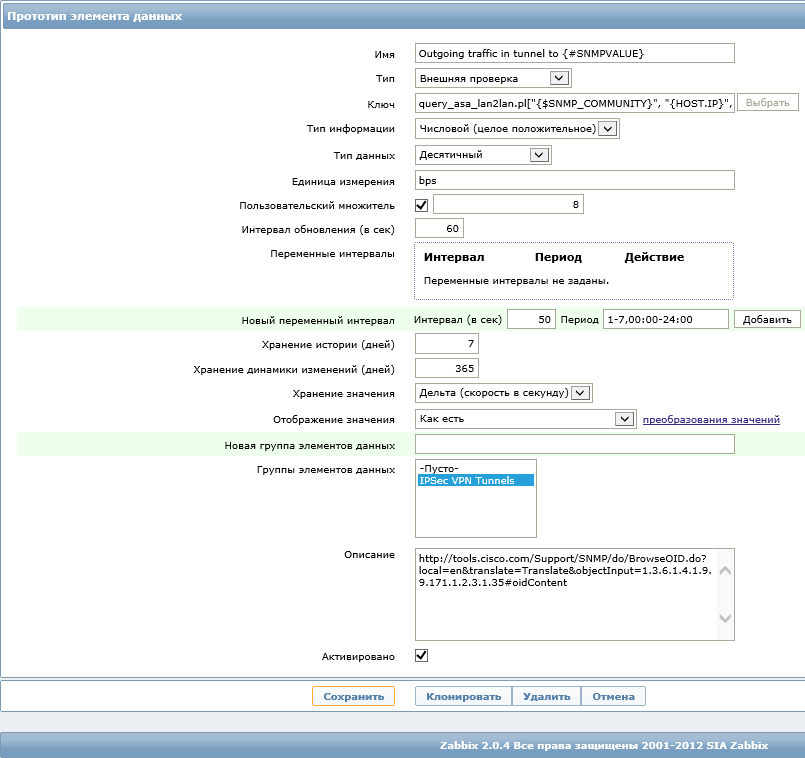
Full key: query_asa_lan2lan.pl ["{$ SNMP_COMMUNITY}", "{HOST.IP}", "ASA", "get", "TX", "{#SNMPVALUE}"]
Link in the description of OID: tools.cisco.com/Support/SNMP/do/BrowseOID.do?local=en&translate=Translate&objectInput=1.3.6.1.4.1.9.9.171.1.2.3.1.35#oidContent
We apply the template to the necessary hosts, waiting for auto-detection and contemplate our tunnels.
It remains to make graphics for the tunnels. Unfortunately, LLD does not allow you to automatically make consolidated graphs from several data prototypes, you have to add the detected data elements manually:

Hooray! You can boast of live pictures of the boss.
It is assumed that SNMP on Ziska and Zabbix is already configured.
The main problem is that we need to monitor the SNMP OIDs with traffic counts are dynamically generated. Moreover, the lists of these numbers are also formed dynamically.
This is due to the fact that the tunnel building algorithm itself is rather complicated. First, an ISAKMP service tunnel is formed, then a basic IPSEC tunnel for data. You can read more about this here: linkmeup.ru/blog/50.html (by the way, an excellent training cycle of articles by this author on the basics of configuring Cisco equipment was already on Habré).
The specific algorithm for extracting the cherished traffic samples is so muddy that it seems impossible to implement it using the purely built-in Zabbix tools. Why, even the artistic transfer did not work for me. Let me describe from the forum www.networking-forum.com :
these OIDs are used solely over the phase 1 tunnel. In the case of the tunnels, you must get the index 1 ID using the endpoint address from the SNMPv2-SMI :: enterprises.9.9.171.1.2.3.1.7, then you will get the index 2 s) from SNMPv2-SMI :: enterprises.9.9.171.1.3.2.1.2, then you can use SNMPv2SMI :: enterprises.9.9.171.1.3.2.1.26 and SNMPv2-SMI :: enterprises.9.9.171.1.3.2.1.39 with the phase 2 index ID appended for the actual phase 2 traffic.
')
Inquisitive can pull the right OIDs handles to personally see the scale of the disaster:
zabbix-host:~ # snmpwalk -v2c -c <community> <IP- > SNMPv2-SMI::enterprises.9.9.171.1.2.3.1.7 SNMPv2-SMI::enterprises.9.9.171.1.2.3.1.7.479 = STRING: "091.092.093.094" SNMPv2-SMI::enterprises.9.9.171.1.2.3.1.7.483 = STRING: "012.013.014.015" SNMPv2-SMI::enterprises.9.9.171.1.2.3.1.7.499 = STRING: "162.163.164.165" SNMPv2-SMI::enterprises.9.9.171.1.2.3.1.7.505 = STRING: "217.218.219.220" zabbix-host:~ # snmpwalk -v2c -c <community> <IP- > SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2: SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8830 = INTEGER: 462 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8831 = INTEGER: 462 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8832 = INTEGER: 462 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8833 = INTEGER: 462 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8834 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8835 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8836 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8837 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8838 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8839 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8840 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8841 = INTEGER: 499 SNMPv2-SMI::enterprises.9.9.171.1.3.2.1.2.8842 = INTEGER: 499 Fortunately, good people from the Cacti forum wrote a pearl-barley script that does all the dirty work by itself.
Download the script and drop it into the ExternalScripts folder (/ usr / local / share / zabbix / externalscripts by default).
Let's play with this script manually:
Works!
zabbix-host:/usr/local/share/zabbix/externalscripts # perl query_asa_lan2lan.pl <community> <IP- > ASA get RX <IP- - remote endpoint> 70546023 Works!
Since there are many tunnels and sometimes they change, we apply LLD (low-level detection rules) in Zabbix so that all the tunnels themselves are detected and registered in our system.
We make a new pattern, and in it - the detection rule and prototypes of data elements for incoming and outgoing traffic:


Full key: query_asa_lan2lan.pl ["{$ SNMP_COMMUNITY}", "{HOST.IP}", "ASA", "get", "RX", "{#SNMPVALUE}"]
Link in the description of OID: tools.cisco.com/Support/SNMP/do/BrowseOID.do?local=en&translate=Translate&objectInput=1.3.6.1.4.1.9.9.171.1.2.3.1.35#oidContent

Full key: query_asa_lan2lan.pl ["{$ SNMP_COMMUNITY}", "{HOST.IP}", "ASA", "get", "TX", "{#SNMPVALUE}"]
Link in the description of OID: tools.cisco.com/Support/SNMP/do/BrowseOID.do?local=en&translate=Translate&objectInput=1.3.6.1.4.1.9.9.171.1.2.3.1.35#oidContent
We apply the template to the necessary hosts, waiting for auto-detection and contemplate our tunnels.
It remains to make graphics for the tunnels. Unfortunately, LLD does not allow you to automatically make consolidated graphs from several data prototypes, you have to add the detected data elements manually:

Hooray! You can boast of live pictures of the boss.
Source: https://habr.com/ru/post/195622/
All Articles