FileCoder ransomware families intensified
Malicious software that encrypts user files and then asks for decryption is not new. Such families have received the general name Filecoder and are a common type of threat - they are called extortionists (ransomware). Over the past few months, we have noted a significant increase in FileCoder encryption activity. ESET antivirus products detect these threats as Win32 / Filecoder and Win32 / Gpcode .
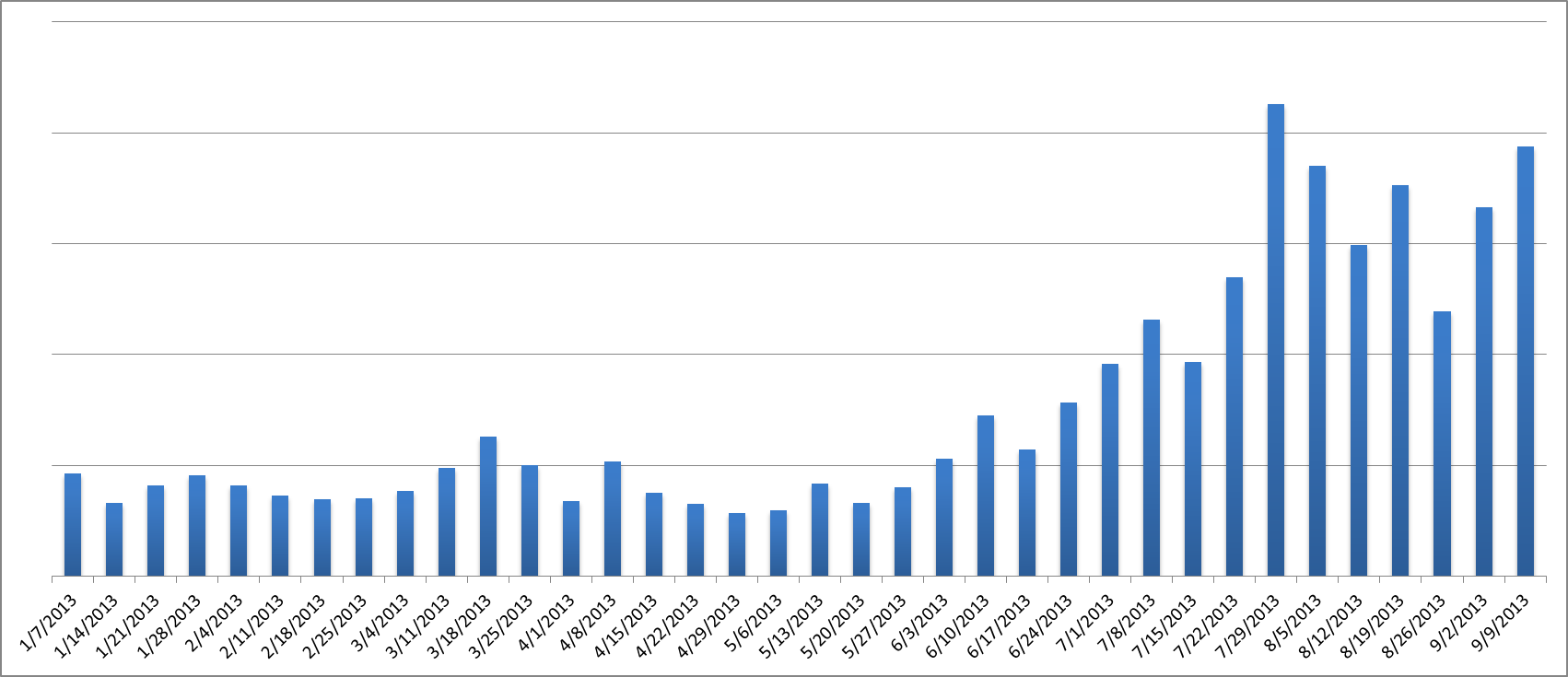
Our ESET Live Grid telemetry system shows that the weekly number of detections of Win32 / Filecoder objects has grown by more than 200% since July 2013 - in comparison with the average for January-June of the same year.
')
Most affected by the activities of this malware Russia. In other countries, activity is present to a lesser extent.

As with other types of Trojan programs, cybercriminals use different methods to install Filecoder on users' computers:
In one of the infection scenarios, we observed that the Win32 / Filecoder.Q modification (and later Win32 / Filecoder.AA , Win32 / Filecoder.W ) was distributed through backdoors, for example, Poison Ivy RAT. The attackers sent the user a backdoor via email. If it was installed on the user's computer, the malicious code contacted its C & C server manager and received the Filecoder extortioner through it.
In another scenario, the attackers used RDP to manually install Filecoder on the computer. We do not have enough information to say how attackers could use RDP for this purpose and obtain access credentials .
FileCoder uses a wide range of capabilities when encrypting files in various of its modifications.
The extortioner uses the following encryption methods:
... and encryption keys can be:
The Filecoder family, which is distributed via RDP, has noticeably improved its tactics using tricks of rogue software (scareware / rogueware) and through the GUI interface presents itself as “Anti-Child Porn Spam Protection” or “ACCDFISA” Security Agency). Of course, such an agency does not exist. Comprehensive information on such options can be found in the Emsisoft blog . This modification is detected by ESET as Win32 / Filecoder.NAC , it has been used by hackers for a long time. It should be noted that it is this modification that differs from the others in the amount of the ransom money, which he asks for decryption - 3000 €. Apparently, this is due to the potential targets of the attackers, who choose various organizations to compromise. At the same time, other representatives of this family extort amounts of € 100–200.
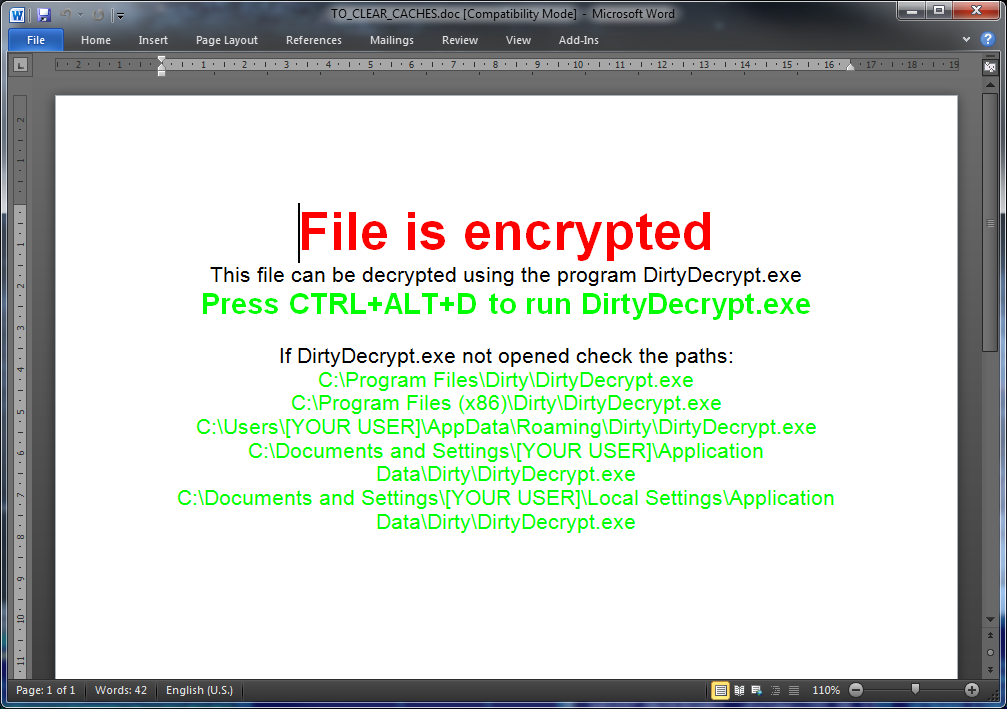
The Win32 / Filecoder.BH option , also known as DirtyDecrypt, has an interesting way to display a buyback message for the user. During the cycle of encrypting the contents of graphic files and documents, the malicious code adds information to the end of the encrypted file with the message shown below.
Another Win32 / Filecoder.BQ option attempts to influence the user by displaying a countdown timer that indicates how much time is left before the ability to decrypt files expires. Interestingly, along with the usual extortionist methods of paying ransom in the form of MoneyPak or Ukash, it allows using Bitcoins for this. More detailed information can be found in our Win32 / Filecoder.BQ Threat Encyclopedia.
Some variants of FileCoder are generated by attackers using a special tool - the builder, similar to the builder of banking Trojans. This tool allows an attacker to select the file types to be encrypted, the encryption method, the message text, and so on.

Some modifications of FileCoder use a weak cipher, incorrect implementation of encryption, or store a password for decryption from where it can be simply received. In this case, it can be much easier to decrypt files, but in most cases attackers do not allow such errors and it is almost impossible to recover encrypted files without a key.
If you are using RDP, take appropriate security measures that prevent arbitrary users from gaining remote access to your system. Consider using a VPN with a two-factor authentication mechanism that allows you to remain secure. In addition, it is good practice to protect your anti-virus software settings with a special password so that an attacker cannot change them.

Our ESET Live Grid telemetry system shows that the weekly number of detections of Win32 / Filecoder objects has grown by more than 200% since July 2013 - in comparison with the average for January-June of the same year.

')
Most affected by the activities of this malware Russia. In other countries, activity is present to a lesser extent.

As with other types of Trojan programs, cybercriminals use different methods to install Filecoder on users' computers:
- Drive-by attacks using exploits for covert installation;
- Email attachments;
- The use of other malware, such as a downloader;
- Manual installation of attackers via RDP.
In one of the infection scenarios, we observed that the Win32 / Filecoder.Q modification (and later Win32 / Filecoder.AA , Win32 / Filecoder.W ) was distributed through backdoors, for example, Poison Ivy RAT. The attackers sent the user a backdoor via email. If it was installed on the user's computer, the malicious code contacted its C & C server manager and received the Filecoder extortioner through it.
In another scenario, the attackers used RDP to manually install Filecoder on the computer. We do not have enough information to say how attackers could use RDP for this purpose and obtain access credentials .
FileCoder uses a wide range of capabilities when encrypting files in various of its modifications.
- Encryption can be implemented using a proprietary code or using a third-party legitimate tool (for example, LockDir , WinRar, etc.).
- Some modifications of malicious code encrypt the entire file, others only part of the file.
- Various methods are used to get rid of the original file. In some cases, the file is deleted, but then it can be restored using various recovery tools. In the other case, the file is permanently deleted by special means (for example, using the Microsoft SysInternals SDelete utility ) or simply completely overwritten.
The extortioner uses the following encryption methods:
- Blowfish
- AES
- RSA
- TEA
... and encryption keys can be:
- Hard coded in FileCoder;
- Received manually (via the command line option or a dialog box, if the attacker has access to the computer via RDP);
- Randomly generated by malicious code.
The Filecoder family, which is distributed via RDP, has noticeably improved its tactics using tricks of rogue software (scareware / rogueware) and through the GUI interface presents itself as “Anti-Child Porn Spam Protection” or “ACCDFISA” Security Agency). Of course, such an agency does not exist. Comprehensive information on such options can be found in the Emsisoft blog . This modification is detected by ESET as Win32 / Filecoder.NAC , it has been used by hackers for a long time. It should be noted that it is this modification that differs from the others in the amount of the ransom money, which he asks for decryption - 3000 €. Apparently, this is due to the potential targets of the attackers, who choose various organizations to compromise. At the same time, other representatives of this family extort amounts of € 100–200.
The Win32 / Filecoder.BH option , also known as DirtyDecrypt, has an interesting way to display a buyback message for the user. During the cycle of encrypting the contents of graphic files and documents, the malicious code adds information to the end of the encrypted file with the message shown below.

Another Win32 / Filecoder.BQ option attempts to influence the user by displaying a countdown timer that indicates how much time is left before the ability to decrypt files expires. Interestingly, along with the usual extortionist methods of paying ransom in the form of MoneyPak or Ukash, it allows using Bitcoins for this. More detailed information can be found in our Win32 / Filecoder.BQ Threat Encyclopedia.
Some variants of FileCoder are generated by attackers using a special tool - the builder, similar to the builder of banking Trojans. This tool allows an attacker to select the file types to be encrypted, the encryption method, the message text, and so on.

Some modifications of FileCoder use a weak cipher, incorrect implementation of encryption, or store a password for decryption from where it can be simply received. In this case, it can be much easier to decrypt files, but in most cases attackers do not allow such errors and it is almost impossible to recover encrypted files without a key.
If you are using RDP, take appropriate security measures that prevent arbitrary users from gaining remote access to your system. Consider using a VPN with a two-factor authentication mechanism that allows you to remain secure. In addition, it is good practice to protect your anti-virus software settings with a special password so that an attacker cannot change them.

Source: https://habr.com/ru/post/195014/
All Articles