New cross-Internet Explorer vulnerability exploited in-the-wild
Microsoft reports a targeted attack on Internet Explorer 8 & 9 users, which uses a 0day vulnerability (CVE-2013-3893 MSHTML Shim), present in all versions of IE (6-10) for all versions of XP (SP3) - Vista-Seven-8-RT x32 / x64. As in the case of many other vulnerabilities in IE, it is of the Remote Code Execution type and is used by attackers to stealthily install malicious code. Operation refers to the type of memory-corruption and is associated with improper access of the browser code to a remote memory block (use-after-free). In this case, the executable code will receive the same rights in the system as the current user.
')
The company has released a Fix it utility to solve this problem (covers 32-bit versions of the browser), which can be downloaded here . Please note that you need to install the KB2870699 update from the latest patch tuesday (MS13-069: Update for Internet Explorer: September 10, 2013).
The EMET tool, which we wrote about in detail in our blog, can successfully block mitigation actions. By default, after installation, EMET is enabled for Internet Explorer. The following enabled options allow you to block the actions of the exploit (enabled by default).
UPD : exploitation details blogs.technet.com/b/srd/archive/2013/09/17/cve-2013-3893-fix-it-workaround-available.aspx .
Microsoft is investigating online versions of Internet Explorer. This is a bug that prevented users from exploiting this explorability in Internet Explorer 8 and Internet Explorer 9. Advisory for more information.
The vulnerability is a remote code execution vulnerability. The Internet Explorer has been selected or has been allocated. It can be an attacker to use the Internet Explorer. This is a site where you’ve been able to access this website.
')

The company has released a Fix it utility to solve this problem (covers 32-bit versions of the browser), which can be downloaded here . Please note that you need to install the KB2870699 update from the latest patch tuesday (MS13-069: Update for Internet Explorer: September 10, 2013).
The EMET tool, which we wrote about in detail in our blog, can successfully block mitigation actions. By default, after installation, EMET is enabled for Internet Explorer. The following enabled options allow you to block the actions of the exploit (enabled by default).
- Forced ASLR
- ROP
- Memprot
- Caller
- SimExecFlow
- Stackpivot
- Heap spray
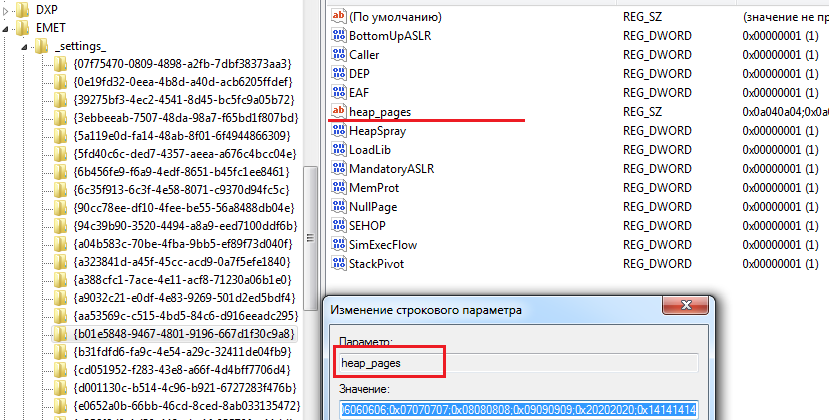
- Find the value of the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ EMET \ iexplore.exe \ * \ Internet Explorer \ iexplore.exe parameter
- Open the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ EMET \ _settings_ \ previous_parameter \ heap_pages section
- Add the value 0x12121212 to the list.

UPD : exploitation details blogs.technet.com/b/srd/archive/2013/09/17/cve-2013-3893-fix-it-workaround-available.aspx .
Source: https://habr.com/ru/post/194184/
All Articles