Subsoil payphone

Guinea pigs in the MGTS office
Long time I wanted to write this article, but only after a series of articles about phreaking and hacking payphones passed through not so long ago, I decided to do it. It stirred in me those long-forgotten notes. The very ones through which I began to study electronics, programming, and became who I am now. In the post “Rise and fall of the novice fricker” in the comments began a discussion of the design features of payphones, so I decided to publish here a revised and updated article “the guts of a payphone”. We understand that the payphone inside. Do not forget that the article 2006 release!
We understand the device payphone
Probably every phreaker, from beginner to experienced, wants to look inside the payphone. And not just to look, but also to tell him about why a piece of hardware is needed, about the intricacies of the protection system. The task is almost not solvable. It is possible, of course, to rest against a payphone, but to understand how it functions is very difficult. When I worked at Hacker magazine, taking advantage of the opportunity of a journalist, I contacted MGTS about writing a payphone. And, lo and behold!, The telephone company MGTS provided us with this opportunity and consulted us in detail on how it works. Now we will debunk many rumors or, on the contrary, we will confirm some of them.
Meeting and meeting
We met with the MGTS press secretary and were taken to the MGTS office with courtyards. Over the years, I can not remember the geography of the place (it was 2006!). In my opinion it was M. Baumanskaya. And then we were met by MGTS employees. We went up to the second floor, where almost all generations of payphones, which were installed in Moscow, hang in the hall.
')

Walk of Fame
Then we came to the office, and saw the workplace of telephone
Guinea pig

Object to be opened
A private payphone in many cities turns out to be not as simple as it seems. In a sense, this is a full-fledged computer, which implements all the anti-grip and anti-vandal achievements of technical progress: a shock-resistant body; molded card reader, which is quite difficult to break; various systems of protection against opening, both program, and hardware. To open a payphone on the right, it has a combination lock, the code of which for each payphone is its own. The payphone detects penetration by the built-in opening sensors and calls back to the PBX, reporting it. At the same time, installers must type a secret password on the keypad of the payphone, which will tell the PBX that it has been opened authorized. If this is not done, the automatics will call the police squad to the place and the person who has encroached on the payphone will be detained. The coin acceptor works in a similar way, the only difference is that instead of a combination lock, a regular turnkey lock is used.
And so, we are opening authorized, first acquaintance.
We open and what is there?
The payphone consists of two parts: the front and the body of the filling. Run through the base nodes, after opening:

Open payphone
So, the points:
1. Code lock
Used to open a payphone As in a safe, twist-twirl - I want to confuse.
2.Cash lock
Opens cashier for uncle stuffing. The same parsley, as in the opening lock.
3. Card reader wire
Used to connect the card reader to the motherboard of a payphone.
4. Hole for coins
This money rushes
5. Coin return compartment
Drop down here or left coins fall
6. Capacity of collection
Used to store received money
7. Flex line connection
I need to communicate with the PBX (I'm afraid, for years I don’t remember what I had in mind when I wrote this).
Continue familiarity with the giblets, go to the insides of the front
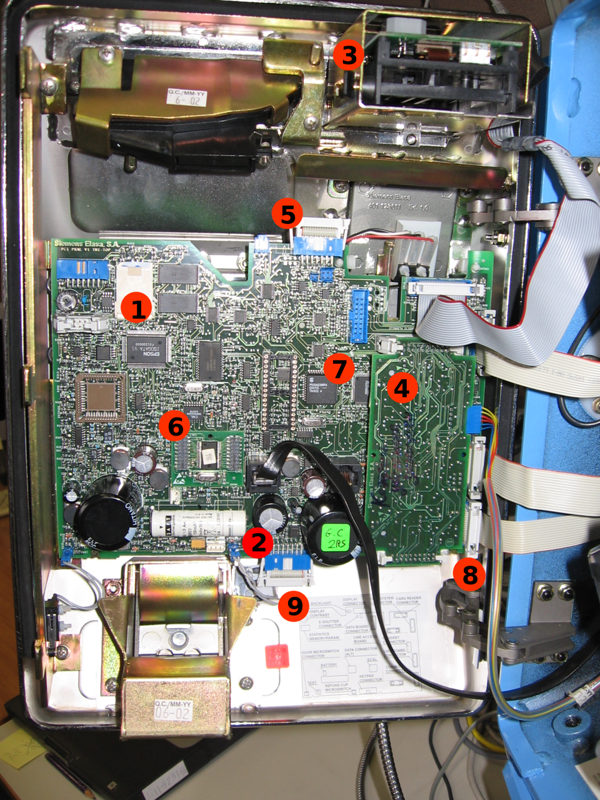
The insides of the front
1. Crypto switch
With its help, check whether the real card Below I’ll stop a little more detailed what it is. It looks like a normal full-size SIM card
2. Keyboard connector
The plume from Claudia is inserted into it.
3. Card reader
Card poke point
. Details of the reader will be disassembled below.
4. Communication board
Connects payphone with PBX. Instead, it may be a GSM modem
5. Display Connector
It connects LCD display
6. Integrated clock
Internal timer, it checks the date of the card and the time of the call to the PBX. Below you can see the cylinder - this is a battery.
7. Processor
Payphone brain
8. Payphone opening sensor
If you open a payphone with a friend, then a picena will come
9. Description of the location of elements
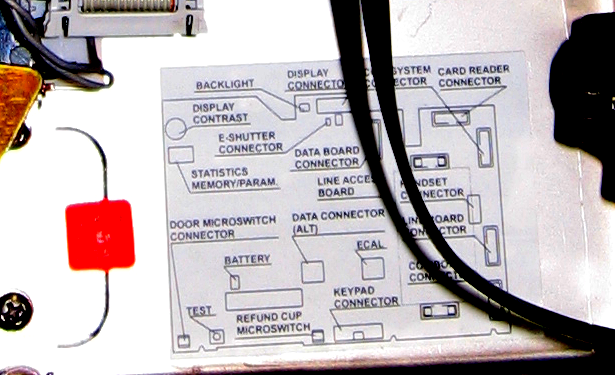
The layout of the connectors, chips, etc.
The interior of the main body

Gut body
1. Coin Acceptor Controller
Detects which money fell
2. Sound controller with speaker
Sounds when an error or in the future will call
3. Coin acceptor
Swallows coins and determines their denomination.
4. Preliminary storage of coins
First, the coins go to the preliminary storage, then poured into the collector
5. The mechanism of return of coins
On this slide, the coins fall back to the user.
6. Sticker description
Main nodes
So, in general, we looked at what a payphone looks like. Now let's go through its main nodes, and find out what they are for. It should be noted that I am not a developer of this device. I wrote it down from the words of the engineers, as I understood it, I was looking for something myself on the Internet, so this information may not be entirely correct. I will be glad if someone corrects me.
Modem
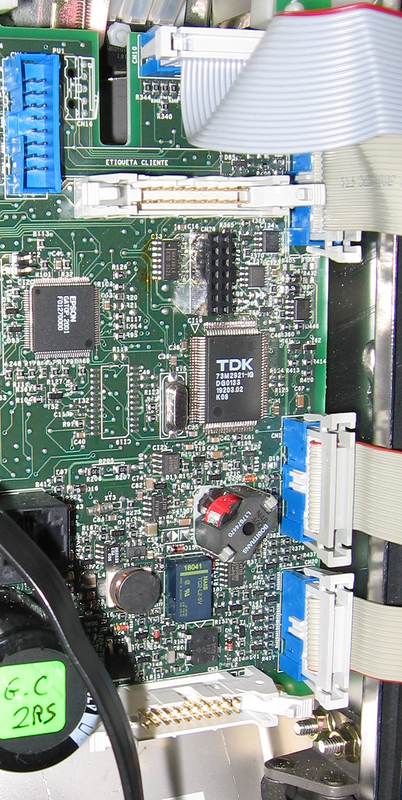
Modem bay
Each Moscow payphone has a modem that communicates with an exchange in the evening or at opening. The modem uses a 73M2921 chip, providing an exchange rate of up to 9600 bps. Above the modem is a switching card with a line. Usually, this is just a line matching fee, however, if there is no possibility to bring a telephone line to the payphone, the GSM modem may well be.
CPU

P51XAG30KFA processor
The basis of the payphone is the central processor P51XAG30KFA . This is a 16-bit processor capable of addressing up to one megabyte of program memory, a clone of the most common architecture C51. Early versions of payphones were also made on the C51-architecture of younger models. The continuation of the tradition is most likely due to the portability of the codes, which makes it possible not to rewrite the firmware to each payphone.
Cryptography
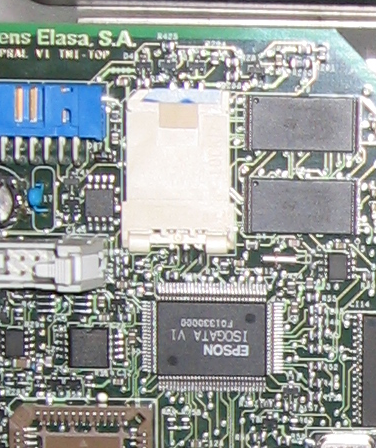
Crypto Security Chip
All the protection systems in the payphone are able to bypass even the beginner flicker, except for one - the built-in cryptographic protection. The payphone has a cryptographic key that identifies the payphone card. By direct emulation of a payphone card, it is almost impossible to bypass this place of protection. At this stage, all the emulators made according to the hacking rules described on the Internet break off.
The principle of operation is quite simple. A payphone card is a Non-rewritable ROM, which stores its serial number and rewritable (you can change the bits set to one to zero, all). Part of the katochka is occupied by some dump, which m0n5ter says in its article
The second measure of protection was that some code was stored in the non-rewritable part of the memory card, generated on the basis of the serial number and the original face value of the card (perhaps something else). The algorithm for the formation of this code has remained a mystery to us. This code did not allow us to achieve complete perfection and to generate fresh dumps on the fly in the microcontroller each time; we had to flash dumps from the actual used cards. Then we hoped that by collecting a sufficient number of memory dumps of cards, we could calculate the hashing algorithm. But, as I have already written, these hopes were not destined to come true.
This crypto switch and verifies that the dump in the rewritable part corresponds to the serial number. It is almost impossible to calculate the keys (we know the price for this “impossible” :))) (say hello to darksimpson ;)))
Note : In fact, there is still one ambush system - this is a check of the pulse durations, which gives the card and the quality of the fronts. It is technically sooo hard to emulate.
Card reader
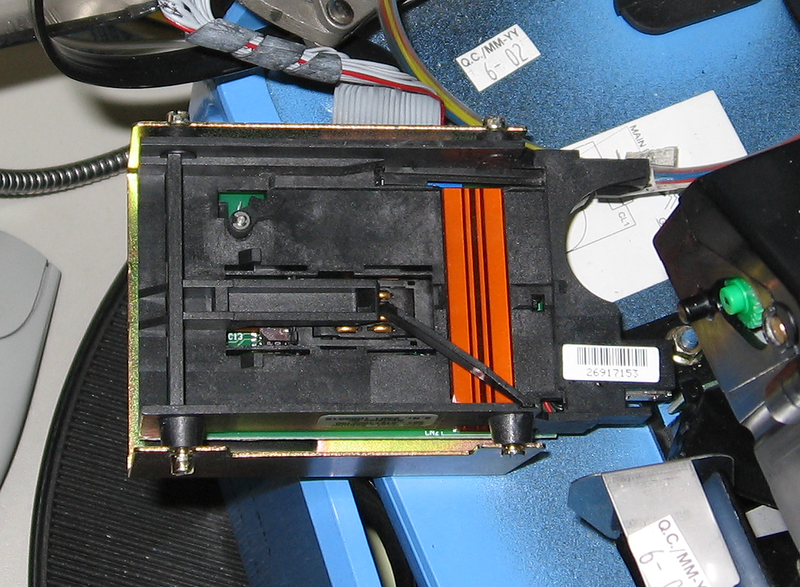
Card reader The orange bar is a wire detector.
The subject of many rumors in phreaking circles is the card reader. From the rumors it was confirmed only that there is a sensor of the output wires, which is easy to get along if you solder the emulator chip directly to the pads of the payphone card. There is no other emulator recognition system in the card reader.
Server

MGTS servers
Each payphone in normal operation mode calls back to the telephone node and transmits information about the calls, the telephone cards used in it, and about its working capacity. He does this at night, when the telephone network is least loaded. With this operation, various settings and modifications of the soft part can be performed in the payphone. At this stage, emulators are often detected and tracked where the calls were made. When calls are made in Russia, it is easy to calculate the person using this emulator. If the payphone does not ring off, it means that it is either faulty, or it is simply not there. The next day, the master goes to the payphone to figure out the reason for his “silence”.
Myths about eternal cards

Installer Card
Each installer is given such a card with the signature “for official use”. At one time there were rumors that this card was everlasting. Unfortunately, no, the card is not eternal. It contains a very large number of units, but they are eventually exhausted. The card is recycled, and a new one is issued to the monter.
Fricker youth
To my credit, the dream of waving a payphone encouraged me to study electronics and program microcontrollers. Has reduced to many interesting people, and even got to work in the "Hacker". I never broke a payphone (no regrets), although there were many attempts. But I got a huge experience. I even made a PCB as thick as a card, but the truth was a little wrong with the long

Printed circuit board
As a result, the pads are located just in the metal card reader, but it was possible to shove it. One of the experiments of that time was this. The cards have pins: data, clock and reset (plus power). So, the primary readout comes from the data card, and then the pin goes to the empty card using the toggle switch (of course, the other pins are connected in parallel). Everything was mounted in a box. I remember probably doing the day three (shkoloshnikom was still).
February. Frost minus 30 for sure! Night, moment of truth! Stuck in a handkerchief, the reading was successful. There was then no wire gauges, no checks on the fronts (there would be hells of fronts because of the capacity of the wires), no current consumed (we feed two cards! And! Drum roll: switch the toggle switch! And ...
I almost put in the pants. Then I learned that there is a buzzer in the payphone. What has a very powerful. Night,
Oh, romance. Now it's so nice to remember the phreaking youth. Albeit not very effective, although how to look.
Total
The conclusion in the magazine was very naive, but fun.
Conclusion from the magazine:
Unfortunately, within one article I can tell you about all the intricacies of a payphone device, the topic is quite extensive and excites the minds of many hackers around the world. As far as possible I will try to cover it in my lj-community (ru_radio_electr), as well as share information on soap. One thing I can say for sure: phreaking in the form of manufacturing emulators has died. According to MGTS, the last emulator was recorded 3 years ago. Cryptography is not defeated by one small controller. To do this, you just need to be a genius. Of course, nothing is impossible, but for inexperienced people it will be an impossible task, and for professionals this is simply not interesting. I recommend to leave the idea of making a payphone card emulator and look for easier ways to make free calls.
I can only say, thanks to MGTS and in general to telephone networks for our happy childhood! And a big human thanks to the MGTS company , which did give a glimpse into the depths of what we wanted to break. These and other photos in full size can be found here.
To be fair, the original article lives here (30th p. PDF, 71 megabytes!).
ZY DIHALT can rightly accuse me of necropolitanism, but on the other hand, lately I don’t want to post junk at all (and you can write so much: RFID, a computer in oil, and much more). Since the inspiration of that time has passed, and there is already no inspiration to write. This article is just like a continuation of phreaking articles from different authors. They inspired me to the feat.
ZZY Remember, the best thanks to the author for the post: left a comment!
Source: https://habr.com/ru/post/194166/
All Articles