Summary of Kevin Mitnick's speech in Moscow

On September 10, Krok held a conference at which Kevin Mitnick was a speaker.
For me, this man is an idol and a legend (I wrote a diploma in part from his books), so getting to his performance was a matter of honor for me.
I learned about the conference 3 days before it started and I was not able to officially get to the conference.
Well, I learned a lot from Mitnick, and therefore, using social engineering , I made physical access (penetration to the protected perimeter).
Under the cut a short summary of the performance
First, Kevin told the story about the theft of 10 million dollars, where the attacker used social engineering.
approximate text here
Some theory and statistics
Kevin said that in 10 years, little has changed in the area of employee illiteracy.
In London, 7 people out of 10 give their password in exchange for the Easter Egg
10 years ago, 9 people out of 10 revealed their password.
')
Demonstrations
Kevin has demonstrated the tools for attacks in action.
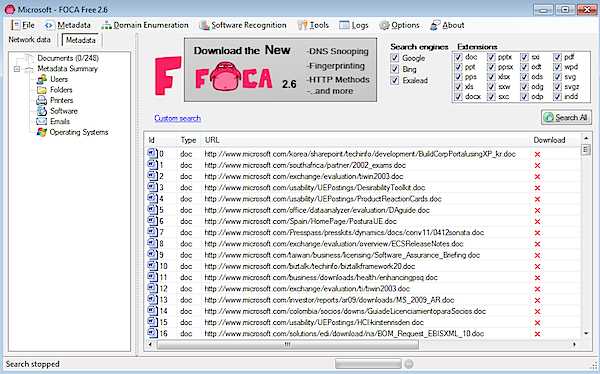
FOCA
Program for collecting meta-data (OS version, software, user list, etc.)
" Diving in the trash "
“What is rubbish for some is treasure for others”
Kevin showed a corporate directory with the names and contacts of all officials, which he “caught” in the trash and which was of great value to a social engineer.
Analysis of P2P networks to identify the topology of the entire network.
Kevin showed a topological diagram of one such network. Then he showed an inscription with the name of this network - "Pentagon". I asked her not to Fota.
"Combat" flash drive and "combat" PDF
Mitnick showed that a stuck flash drive (specially left by the attacker in a prominent place) or an open PDF file can provide the hacker with full control of the victim’s computer, up to capture the control of the camera and display the entire contents of the desktop.
Java applets
Kevin has demonstrated a malicious site that mimics under VTB24 (be careful when clicking on the link )
Spoofing
Kevin showed in action how the service works on this link (it is password protected)
mitnicksecurity.com/sms.php
He clearly demonstrated how you can send SMS messages on behalf of his wife to a mobile phone number of a person from the audience. The SMS text was the following: “Tell Kevin all your passwords.”
Phishing with a fake bank tech support number.
Kevin demonstrated a man in the middle attack
The person receives a letter asking him to call a fake number in bank technical support, and the attacker receives a sequence of pressing buttons on the victim's phone.
Smart card reader / copier.
Kevin showed in action a phreaker device that allows you to duplicate contactless smart cards
At the end of his speech, Kevin answered questions, including how often do “watchful trainings” for employees. According to Mitnick - at least once every six months.
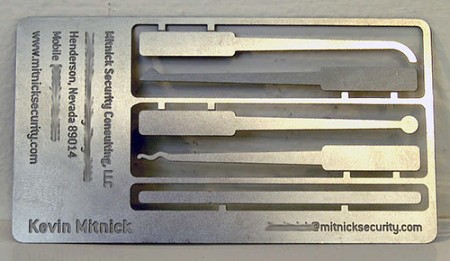
Ten lucky ones got legendary business cards of the “former” hacker in the form of a set of master keys.
Recommended resources:
"The Art of Deception"
"The Art of Invasion"
"Ghost in the network"
"Psychology of influence" Cialdini
trustedsec.com
KnowBe4.com
mitnicksecurity.com
P.S. The moderator (at the end of the speech): “Kevin’s rider was told to announce that photo, audio and video recording was prohibited, but the rider did not say WHEN this had to be announced.”
PPP
“You can only believe God. All others are under suspicion. ” Kevin Mitnick
Biography of a hacker on Habré habrahabr.ru/post/68273
Source: https://habr.com/ru/post/193418/
All Articles