Banking Trojan Hesperbot - Detailed Analysis
We already wrote about Hesperbot , this threat is a new banking malware and has a modular architecture. Malefactors used it for carrying out attacks to users of various countries, including Turkey, the Czech Republic, Portugal and Great Britain. The main purpose of the attacks was to steal confidential data from online banking of users and install the mobile component of malicious code on devices running Symbian, Android, Blackberry. Cybercriminals used a convincing phishing scheme to lure users into malicious links, which made their approach even more practical.

Compromise user occurs when clicking on a malicious link. Below is a diagram used by attackers.
')

Fig. Scheme of compromise user.
The main task of the dropper is to inject the payload (payload or core) into the context of the trusted explorer.exe process. This code then downloads from the network and executes additional modules.
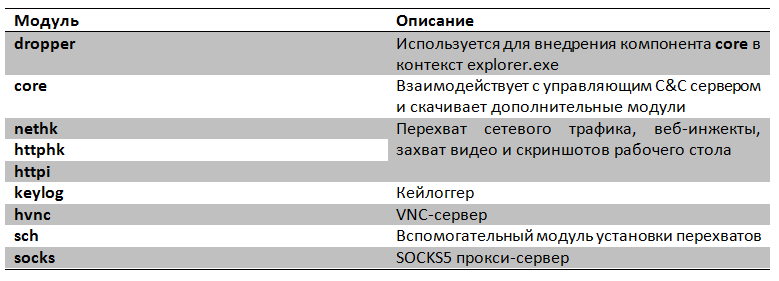
Win32 / Spy.Hesperbot is a cross-platform threat and the various modules listed are available in x86 and x64 versions. Various internal functions of some modules are available for use in other modules through a special table of virtual methods (vtable). Most of the Hesperbot code is written in C and compiled using Visual Studio 2010 without using the run-time library.
Payload
A dropper can use one of the following methods to inject the core component into the explorer.exe address space:
After successful implementation, the core component starts its work in the system: it is responsible for interacting with the C & C managing server, launching auxiliary modules, and writing the startup parameters of the malicious code to the registry. To work with C & C, Hesperbot uses a list of hard-wired URLs in the body (which differ in the case of different countries and botnets) or generates a list of new addresses using a special DGA-algorithm. The malicious code sends the following information to the C & C server:
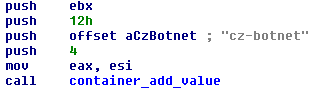
Fig. ID of the Czech botnet.
The server response may contain the following information or files:
The malicious code retrieves a list of active smart cards in the system using the following APIs: SCardEstablishContext , SCardListReaders, and SCardConnect . Unlike other, more complex cases of threats [ 1 , 2 ], Win32 / Spy.Hesperbot collects only the names of smart cards and does not have the ability to interact with them.
Downloadable files (configuration files and executable plug-in files) are encrypted using the Twofish algorithm , whose 256-bit hash is based on data:
To store data downloaded from C & C and other auxiliary files (for example, a keylogger log file), Hesperbot creates a directory with an arbitrary name in the% APPDATA% folder.
The Core module has the ability to embed its code not only in explorer.exe, but also in other running processes. Malicious code uses an undocumented trick to intercept UserNotifyProcessCreate inside csrss.exe in order to ensure that its code is active in every running process.
The keylogger component intercepts keystrokes through the functions GetMessage and TranslateMessage . The symbols are then saved to a log file with information about the process and the name of the window in which they were entered. After that, the file is sent to the attackers server.
The capture module screenshots of the desktop and the video is called httpi. Video capture was also used in the Zeus banking Trojan program. This feature allows attackers to see a more complete picture of what is happening with the user in the system. This feature is implemented using the AVIFileCreateStream API, AVIFileMakeCompressedStream , AVIStreamWrite from the Avifil32.dll library.
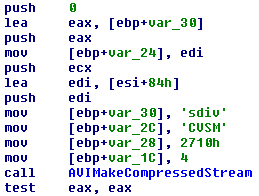
Fig. Video creation code.
Screenshots of the desktop are created using the functions of the Gdi32.dll library.
The possibility of a VNC connection was previously observed in the famous Carberp Trojan program. It allows you to create a VNC server on the side of the infected computer, which the attacker will have access to. Since, unlike RDP, VNC does not perform a user log off operation, an attacker can connect to the victim during its operation. This is achieved by creating an auxiliary desktop ( CreateDesktop ), which is invisible to the user. This module provides an attacker with the ability to run a browser process installed on the system. In this case, the attacker gets access to his stored data (cookies, sessions, etc.).
Networking and Web Injecting
Hesperbot is not the first banking malware that uses WinSock library functions ( send , WSASend , etc.) and WinInet libraries ( HttpSendRequest , InternetReadFile , etc.) to gain complete control over user HTTP / HTTPS network traffic. Similar mechanisms were used in the famous Zeus and SpyEye trojans. Using this approach allows attackers to perform web injections (web-injects), receive form-grabbing data and perform other operations to steal information that the user enters into the pages opened in the web browser. These methods are called "Man-in-the-Browser" attack. Win32 / Spy.Hesperbot uses a slightly different approach when attacking a user, which we have already seen in another Win32 / Gataka banking Trojan.
Interception of traffic and the introduction of HTML-code modules nethk, httphk and httpi, which were mentioned above in the table of components.
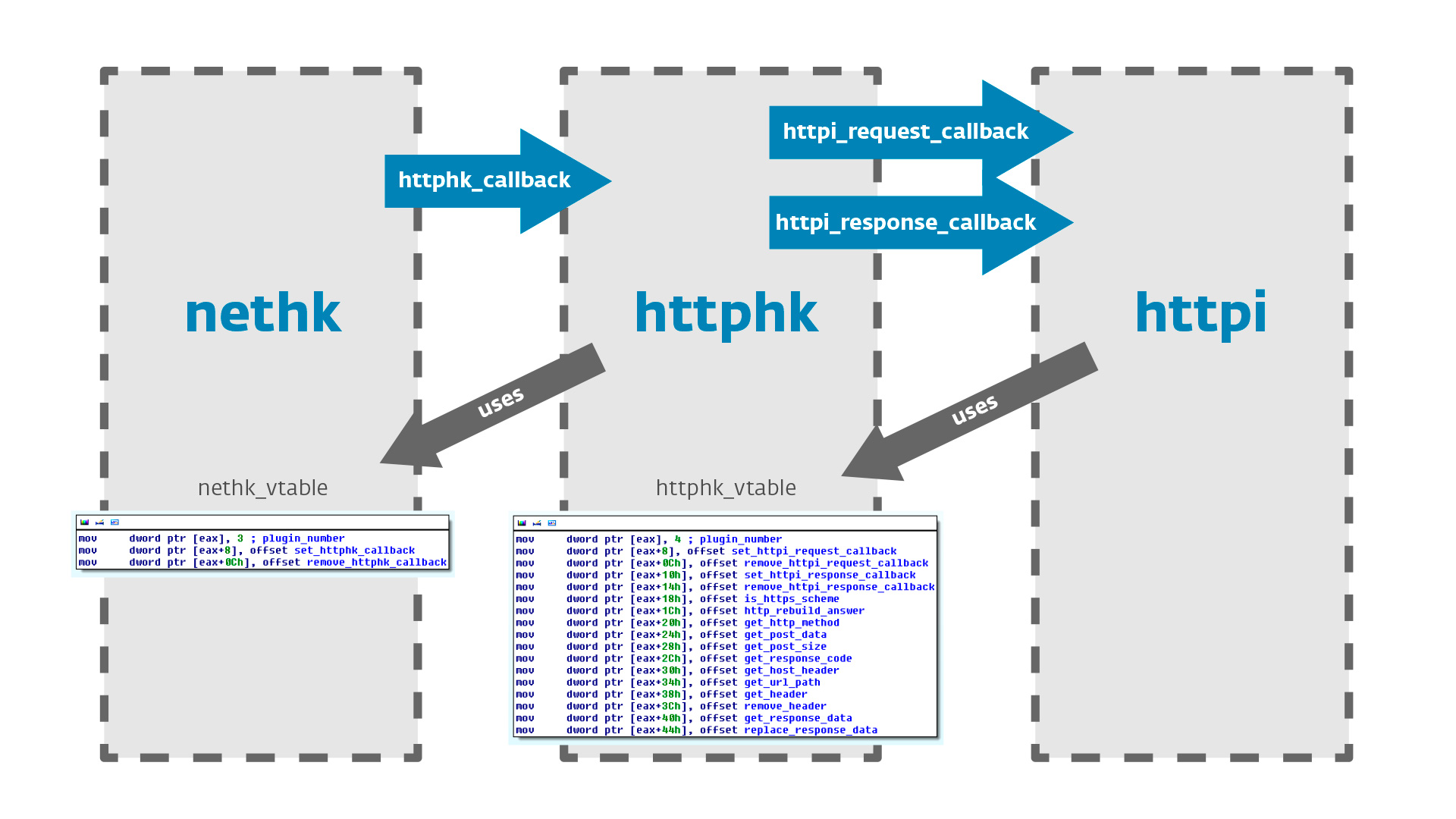
Fig. The interaction of different modules Hesperbot.
The nethk module is the first downloadable malicious code plugin. It is downloaded by the core component. Win32 / Spy.Hesperbot performs a man-in-the-middle attack by creating a local proxy (local proxy) through which it can control all connections initiated by the browser process.
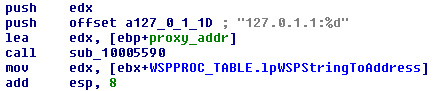
Fig. Proxy creation code.
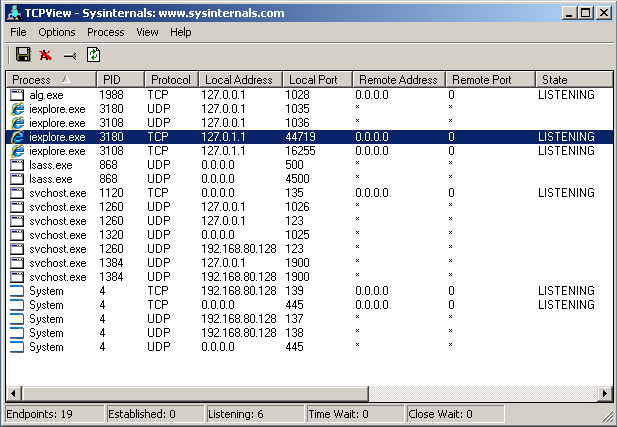
Fig. Internet Explorer network connections through the established Hesperbot proxy.
A Trojan program using the nethk module creates a proxy on an arbitrary port with the address 127.0.1.1 and intercepts the following functions of the mswsock.dll library: WSPSocket , WSPIoctl, WSPConnect , WSPCloseSocket . Pointers to these functions are modified in the WSPPROC_TABLE table. To understand how this redirection works, the malicious version of WSPConnect is presented below.

Fig. Malicious version of WSPConnect API.
For example, if a user wants to log in to the online banking system and the browser tries to establish a secure connection to the bank’s website, the connection request will be intercepted by the Hesperbot code to create a local proxy, after which the online banking system will deal with the attacker's socket.
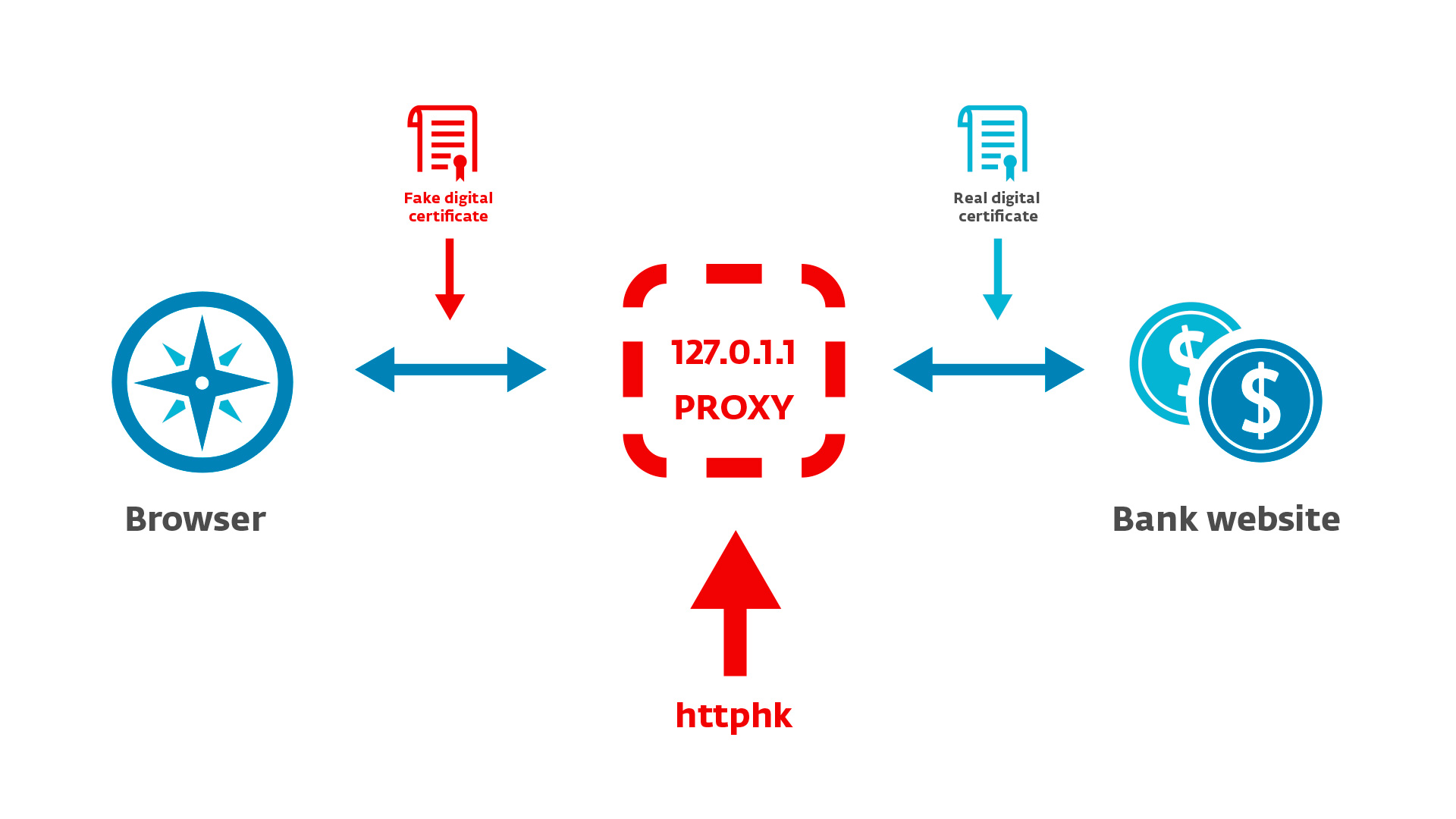
Fig. Scheme of the malicious proxy.
The httphk module's callback function is called each time the proxy intercepts the request from the browser before sending it to the real server. In addition, httphk is called every time a proxy intercepts a response to a request from a real server, before sending it to the browser. Further httphk continues to work with traffic.
There are differences in the processing of HTTP and HTTPS traffic. In the case of a simple HTTP connection, the data in request / response mode is simply transmitted from httphk and vice versa. In the case of a secure HTTPS connection, the malicious code uses the capabilities of the nethk module in order to “get rid of encryption”. When an HTTPS request initiated by the browser is intercepted (the request data is already encrypted using a fake certificate, see below as), it is decrypted and this data is sent to the httphk module via the callback function and then encrypted with this server certificate (i.e. certificate of the bank’s website), and then sent to the destination. With the arrival of the server's response, i.e., the HTTPS response, the proxy decrypts it using this certificate and sends this data to the httphk for encryption with a fake certificate before sending it to the browser.
Thus, using the "man-in-the-middle" proxy, Win32 / Spy.Hesperbot can access the victim's outgoing HTTPS traffic before it is encrypted with this certificate. Zeus and SpyEye use a similar approach, but their MitB implementation is different from that used in Hesperbot.
Malicious code gives the browser its certificate to simulate an HTTPS connection. The nethk module has its own self-signed SSL certificate on board.

Fig. SSL certificate inside nethk.

Fig. An example of using a fake certificate Hesperbot. On a regular system, you can see a real Google certificate instead of a fake.
In order to trick the browser certificate validation component, the malicious code intercepts the corresponding certificate verification functions. The release of such interceptions depends on the victim’s browser. The table below shows the browsers supported by Win32 / Spy.Hesperbot and the functions that are intercepted.

The authors of the malicious code used hashes of process names, instead of string-based comparisons to complicate the analysis.

The screenshot below shows the interception code CertVerifyCertificateChainPolicy .
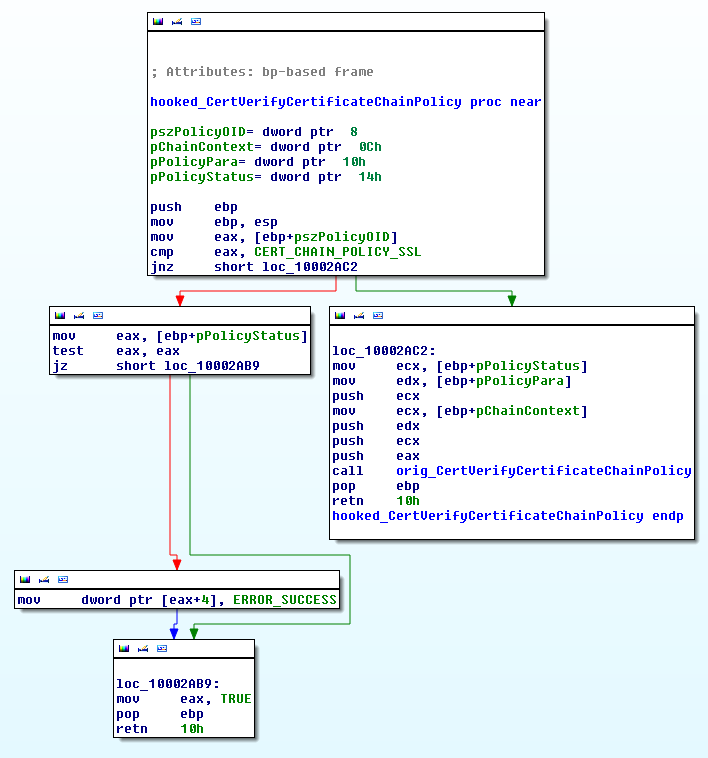
The httphk module is responsible for analyzing the HTTP protocol data. When the callback function of this module is called, it performs the analysis of HTTP headers, data, and fills its internal data structures. In the future, this structure will be available through the module httpi . httphk provides two callback functions to call httpi: httpi_request_callback and httpi_response_callback.
The httpi module modifies the HTTP protocol data according to the configuration file settings. When it calls httpi_request_callback, the following actions are performed.
When you call httpi_response_callback, the Trojan program checks the HTTP response code for the value 200 (OK). After that, the configuration file is read and if web injections are specified for the site, they are inserted into the web page.
The figure below shows the decrypted configuration file that was used in the Portuguese botnet. You may notice that the first group of domains will be ignored by the httpi module. This suggests that Facebook and Google account data is considered to be not as valuable to attackers as the online banking account data below.

It seems that people who wrote the code for web-inject scripts speak Russian, as evidenced by the accompanying comments. However, it should be noted that the scripts could have been written by quite different people, other than the authors of Win32 / Spy.Hesperbot. The web-inject scripts are quite similar among different families of malicious programs and their use is quite common among cybercriminals.
Mobile component
Hesperbot is not the first such malware that uses mobile components (ZitMo or SpitMo) to bypass the SMS-based authentication confirmation system ( Mobile Transaction Authentication Number ). This banking transaction confirmation system is widely used in many European countries and in Russia.
Hesperbot implements the introduction of special JS scripts into web pages through which the user is asked to install an application for a mobile phone. The compromised user is offered a special list of phone models and after entering the phone number, he is sent a link to download a malicious mobile application. The application exists in versions for Symbian, Android and Blackberry.
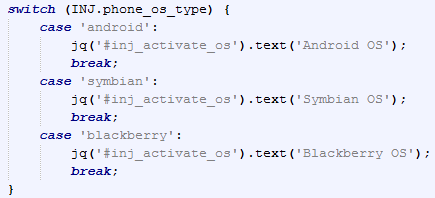
We were able to analyze malicious components for the Symbian and Android platforms. They have similar capabilities. First, this is the “activation procedure” (activation procedure). A special web injection on the infected computer generates a random “activation number” that is displayed to the user. Next, he will need to duplicate this number on his device when such an action is offered by the mobile application. The mobile application displays the "response code", which is calculated through the activation code. This user code must be entered back into the web page for confirmation. The malicious script is equipped with the same algorithm for calculating the code as the mobile one. Thus, by simulating a trusted application on a user's mobile device and using a fake web page on his computer, attackers can bypass the code verification system for conducting operations related to online banking.
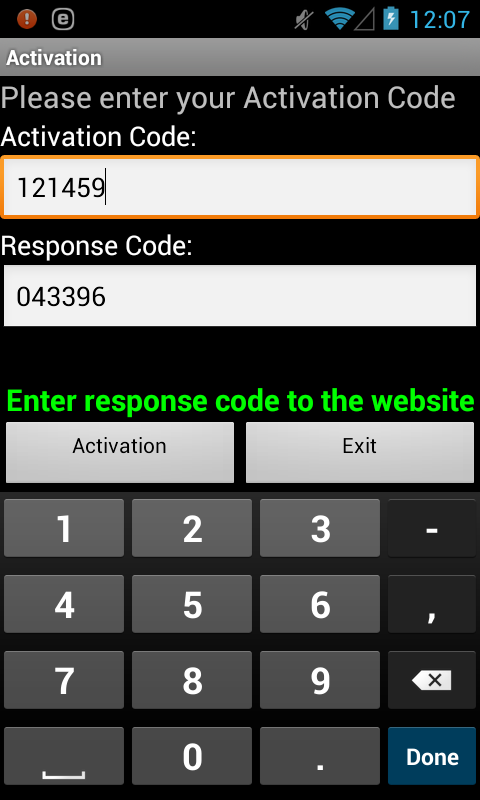
Fig. Screenshot malware component for Android [ Android / Spy.Hesperbot.A ].
This malicious mobile application registers a special service that waits for incoming SMS messages and forwards them to the attacker's number. Thus, the attacker will receive this code to conduct a transaction or other banking transaction.
ESET anti-virus applications detect mobile malware like Android / Spy.Hesperbot.A and SymbOS9 / Spy.Hesperbot.A .

Compromise user occurs when clicking on a malicious link. Below is a diagram used by attackers.
')

Fig. Scheme of compromise user.
The main task of the dropper is to inject the payload (payload or core) into the context of the trusted explorer.exe process. This code then downloads from the network and executes additional modules.

Win32 / Spy.Hesperbot is a cross-platform threat and the various modules listed are available in x86 and x64 versions. Various internal functions of some modules are available for use in other modules through a special table of virtual methods (vtable). Most of the Hesperbot code is written in C and compiled using Visual Studio 2010 without using the run-time library.
Payload
A dropper can use one of the following methods to inject the core component into the explorer.exe address space:
- Start a new instance of explorer.exe and fix (patching) the bytes of its entry point using ntdll! NtGetContextThread and ntdll! NtWriteProcessMemory . After that, the entry point will point to the malware code.
- Embed your code in the already existing explorer.exe process using the method based on the Shell_TrayWnd / SetWindowLong / SendNotifyMessage functions . This method was used in the malicious code PowerLoader, which was previously described by Alexander Matrosov [ 1 , 2 , 3 ].
- Deploy code to explorer.exe using the regular CreateRemoteThread function.
After successful implementation, the core component starts its work in the system: it is responsible for interacting with the C & C managing server, launching auxiliary modules, and writing the startup parameters of the malicious code to the registry. To work with C & C, Hesperbot uses a list of hard-wired URLs in the body (which differ in the case of different countries and botnets) or generates a list of new addresses using a special DGA-algorithm. The malicious code sends the following information to the C & C server:
- The name of the bot, which is based on the Computer Name.
- The name of the botnet, which is formed on the basis of the country to which the threat was aimed by the attackers. For example, “cz-botnet”, “tr-botnet”, “pt-botnet”, “uk-botnet” and “super-botnet” (the latter was used in early beta versions).
- IP addresses of network adapters.
- Names of installed smart cards.
- Information about installed Hesperbot plugins.

Fig. ID of the Czech botnet.
The server response may contain the following information or files:
- Configuration file
- Plugin files.
- Arbitrary executable file for later launch.
- New version of Hesperbot.
The malicious code retrieves a list of active smart cards in the system using the following APIs: SCardEstablishContext , SCardListReaders, and SCardConnect . Unlike other, more complex cases of threats [ 1 , 2 ], Win32 / Spy.Hesperbot collects only the names of smart cards and does not have the ability to interact with them.
Downloadable files (configuration files and executable plug-in files) are encrypted using the Twofish algorithm , whose 256-bit hash is based on data:
- Computer Name (Computer Name).
- The “InstallDate” parameter of the [HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion] registry key.
- OS versions.
- Processor Architecture (x86, x64, IA64).
- The "MachineGuid" setting of the [HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Cryptography] registry key.
- The "DigitalProductId" parameter of the registry key is [HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion].
To store data downloaded from C & C and other auxiliary files (for example, a keylogger log file), Hesperbot creates a directory with an arbitrary name in the% APPDATA% folder.
The Core module has the ability to embed its code not only in explorer.exe, but also in other running processes. Malicious code uses an undocumented trick to intercept UserNotifyProcessCreate inside csrss.exe in order to ensure that its code is active in every running process.
The keylogger component intercepts keystrokes through the functions GetMessage and TranslateMessage . The symbols are then saved to a log file with information about the process and the name of the window in which they were entered. After that, the file is sent to the attackers server.
The capture module screenshots of the desktop and the video is called httpi. Video capture was also used in the Zeus banking Trojan program. This feature allows attackers to see a more complete picture of what is happening with the user in the system. This feature is implemented using the AVIFileCreateStream API, AVIFileMakeCompressedStream , AVIStreamWrite from the Avifil32.dll library.

Fig. Video creation code.
Screenshots of the desktop are created using the functions of the Gdi32.dll library.
The possibility of a VNC connection was previously observed in the famous Carberp Trojan program. It allows you to create a VNC server on the side of the infected computer, which the attacker will have access to. Since, unlike RDP, VNC does not perform a user log off operation, an attacker can connect to the victim during its operation. This is achieved by creating an auxiliary desktop ( CreateDesktop ), which is invisible to the user. This module provides an attacker with the ability to run a browser process installed on the system. In this case, the attacker gets access to his stored data (cookies, sessions, etc.).
Networking and Web Injecting
Hesperbot is not the first banking malware that uses WinSock library functions ( send , WSASend , etc.) and WinInet libraries ( HttpSendRequest , InternetReadFile , etc.) to gain complete control over user HTTP / HTTPS network traffic. Similar mechanisms were used in the famous Zeus and SpyEye trojans. Using this approach allows attackers to perform web injections (web-injects), receive form-grabbing data and perform other operations to steal information that the user enters into the pages opened in the web browser. These methods are called "Man-in-the-Browser" attack. Win32 / Spy.Hesperbot uses a slightly different approach when attacking a user, which we have already seen in another Win32 / Gataka banking Trojan.
Interception of traffic and the introduction of HTML-code modules nethk, httphk and httpi, which were mentioned above in the table of components.

Fig. The interaction of different modules Hesperbot.
- nethk - used to deploy a local proxy, intercepts functions for working with sockets when tracking connections; contains hooks for SSL certificate validation functions in the browser.
- httphk - used when parsing HTTP traffic.
- httpi - used for taking screenshots, capturing video, removing data forms and introducing HTML-code (web-injects).
The nethk module is the first downloadable malicious code plugin. It is downloaded by the core component. Win32 / Spy.Hesperbot performs a man-in-the-middle attack by creating a local proxy (local proxy) through which it can control all connections initiated by the browser process.

Fig. Proxy creation code.

Fig. Internet Explorer network connections through the established Hesperbot proxy.
A Trojan program using the nethk module creates a proxy on an arbitrary port with the address 127.0.1.1 and intercepts the following functions of the mswsock.dll library: WSPSocket , WSPIoctl, WSPConnect , WSPCloseSocket . Pointers to these functions are modified in the WSPPROC_TABLE table. To understand how this redirection works, the malicious version of WSPConnect is presented below.

Fig. Malicious version of WSPConnect API.
For example, if a user wants to log in to the online banking system and the browser tries to establish a secure connection to the bank’s website, the connection request will be intercepted by the Hesperbot code to create a local proxy, after which the online banking system will deal with the attacker's socket.

Fig. Scheme of the malicious proxy.
The httphk module's callback function is called each time the proxy intercepts the request from the browser before sending it to the real server. In addition, httphk is called every time a proxy intercepts a response to a request from a real server, before sending it to the browser. Further httphk continues to work with traffic.
There are differences in the processing of HTTP and HTTPS traffic. In the case of a simple HTTP connection, the data in request / response mode is simply transmitted from httphk and vice versa. In the case of a secure HTTPS connection, the malicious code uses the capabilities of the nethk module in order to “get rid of encryption”. When an HTTPS request initiated by the browser is intercepted (the request data is already encrypted using a fake certificate, see below as), it is decrypted and this data is sent to the httphk module via the callback function and then encrypted with this server certificate (i.e. certificate of the bank’s website), and then sent to the destination. With the arrival of the server's response, i.e., the HTTPS response, the proxy decrypts it using this certificate and sends this data to the httphk for encryption with a fake certificate before sending it to the browser.
Thus, using the "man-in-the-middle" proxy, Win32 / Spy.Hesperbot can access the victim's outgoing HTTPS traffic before it is encrypted with this certificate. Zeus and SpyEye use a similar approach, but their MitB implementation is different from that used in Hesperbot.
Malicious code gives the browser its certificate to simulate an HTTPS connection. The nethk module has its own self-signed SSL certificate on board.

Fig. SSL certificate inside nethk.

Fig. An example of using a fake certificate Hesperbot. On a regular system, you can see a real Google certificate instead of a fake.
In order to trick the browser certificate validation component, the malicious code intercepts the corresponding certificate verification functions. The release of such interceptions depends on the victim’s browser. The table below shows the browsers supported by Win32 / Spy.Hesperbot and the functions that are intercepted.

The authors of the malicious code used hashes of process names, instead of string-based comparisons to complicate the analysis.

The screenshot below shows the interception code CertVerifyCertificateChainPolicy .

The httphk module is responsible for analyzing the HTTP protocol data. When the callback function of this module is called, it performs the analysis of HTTP headers, data, and fills its internal data structures. In the future, this structure will be available through the module httpi . httphk provides two callback functions to call httpi: httpi_request_callback and httpi_response_callback.
The httpi module modifies the HTTP protocol data according to the configuration file settings. When it calls httpi_request_callback, the following actions are performed.
- Capture video and desktop screenshots. The malicious code reads the configuration file data and checks the requested URL. In the case of a match, the video is captured or screenshots are created.
- Extract form data (form grabbing). The malicious code checks the content-type parameter in the header of the HTTPS POST request for a match with “application / x-www-form-urlencoded” or “text / plain”. In the event of a match, it is assumed that data is being transmitted for the login form. If this URL is specified in the configuration file, then the data is written to a log file.
When you call httpi_response_callback, the Trojan program checks the HTTP response code for the value 200 (OK). After that, the configuration file is read and if web injections are specified for the site, they are inserted into the web page.
The figure below shows the decrypted configuration file that was used in the Portuguese botnet. You may notice that the first group of domains will be ignored by the httpi module. This suggests that Facebook and Google account data is considered to be not as valuable to attackers as the online banking account data below.

It seems that people who wrote the code for web-inject scripts speak Russian, as evidenced by the accompanying comments. However, it should be noted that the scripts could have been written by quite different people, other than the authors of Win32 / Spy.Hesperbot. The web-inject scripts are quite similar among different families of malicious programs and their use is quite common among cybercriminals.
Mobile component
Hesperbot is not the first such malware that uses mobile components (ZitMo or SpitMo) to bypass the SMS-based authentication confirmation system ( Mobile Transaction Authentication Number ). This banking transaction confirmation system is widely used in many European countries and in Russia.
Hesperbot implements the introduction of special JS scripts into web pages through which the user is asked to install an application for a mobile phone. The compromised user is offered a special list of phone models and after entering the phone number, he is sent a link to download a malicious mobile application. The application exists in versions for Symbian, Android and Blackberry.

We were able to analyze malicious components for the Symbian and Android platforms. They have similar capabilities. First, this is the “activation procedure” (activation procedure). A special web injection on the infected computer generates a random “activation number” that is displayed to the user. Next, he will need to duplicate this number on his device when such an action is offered by the mobile application. The mobile application displays the "response code", which is calculated through the activation code. This user code must be entered back into the web page for confirmation. The malicious script is equipped with the same algorithm for calculating the code as the mobile one. Thus, by simulating a trusted application on a user's mobile device and using a fake web page on his computer, attackers can bypass the code verification system for conducting operations related to online banking.

Fig. Screenshot malware component for Android [ Android / Spy.Hesperbot.A ].
This malicious mobile application registers a special service that waits for incoming SMS messages and forwards them to the attacker's number. Thus, the attacker will receive this code to conduct a transaction or other banking transaction.
ESET anti-virus applications detect mobile malware like Android / Spy.Hesperbot.A and SymbOS9 / Spy.Hesperbot.A .
Source: https://habr.com/ru/post/193318/
All Articles