Snowden has shed light on the cryptographic hacking situation. Everything is bad
 A fresh piece of secret documents from Edward Snowden makes it clear how the US National Security Agency manages to bypass the cryptographic protection of Internet communications.
A fresh piece of secret documents from Edward Snowden makes it clear how the US National Security Agency manages to bypass the cryptographic protection of Internet communications.Immediately in three editions ( The Guardian , The New York Times and ProPublica ) excerpts from the secret budget of the NSA were posted, according to which since 2000, when encryption tools were massively introduced, the US intelligence agencies spent billions of dollars on breaking into cryptography as part of the secret Bullrun program ( named in honor of the first major battle of the American Civil War, which occurred on July 21, 1861 near Manassas, Virginia).
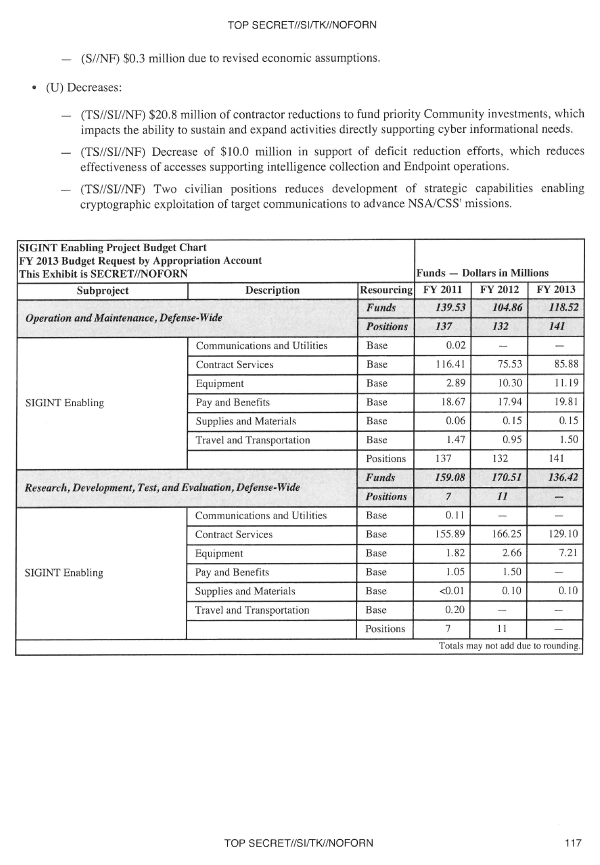
The activity of the Agency was not limited to the research of algorithms and the construction of data centers for hacking communications using the key search method. It turned out that the Agency has long been successfully working with IT companies on embedding tabs in their products for the US intelligence services, and also is working to detect vulnerabilities in encryption mechanisms and purposefully weaken international data protection algorithms (an unnamed international encryption standard reported by the International standardization organization in 2006). For the integration of backdoors into popular commercial products alone, under the SIGINT program, $ 250 million is spent annually.
')
According to the documents, the greatest efforts are being made to crack the SSL protocol, which ensures the security of most communications on the modern Internet. VPN and 4G security technologies are also among the priorities. The NSA maintains an internal encryption key database that allows you to instantly decrypt connections. If the necessary keys are not provided, then the request goes to a special “Recovery Service”, which tries to obtain it in various ways.
Several published documents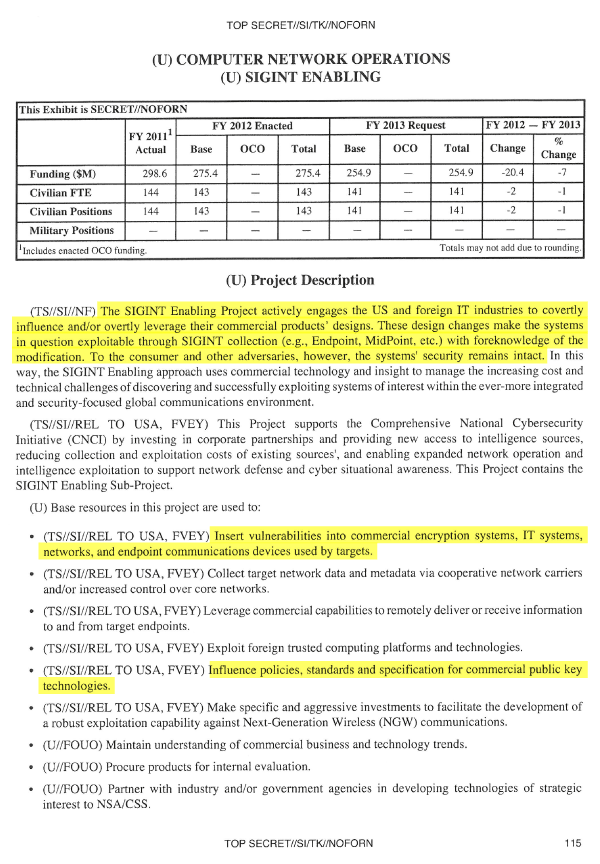




Along with the NSA, GCHQ (Government Communications Headquarters, Center for Government Communications), a British intelligence agency responsible for electronic intelligence and information security of government agencies, participated in the program. According to The Guardian, over the course of three years, she has been developing ways of hacking into encrypted data through Hotmail, Google, Yahoo and Facebook. According to the documents, by 2012 GCHQ had developed “new access features” to Google systems.
According to The New York Times, the documents received from Snowden indicate that the NSA considers the ability to decrypt information as one of its priorities and “competes in this area with the special services of China, Russia and other countries.” “In the future, superpowers will appear and fall into disrepair depending on how strong their cryptanalytic programs are. This is the price that the US must pay to keep unlimited access to the use of cyberspace, ”the NSA’s 2007 document quotes the newspaper.
The ability of the NSA to decipher fully is known only to a limited number of organizations, the so-called "Five Eyes": the NSA and their counterparts in the UK, Canada, Australia and New Zealand.
Recently, more and more large companies began to switch to special hardware solutions for VPN and cryptography, so for 2013 the NSA planned to either build a hardware backdoor into encryption chips through the manufacturer, or detect and secretly use existing vulnerabilities in the implementation. What exactly is happening now is unknown, because Snowden documents for several years.
Well-known expert in cryptography Bruce Schneier expressed an opinion in The Guardian that "the US government betrayed the Internet" and has already published its recommendations on how to (try) to avoid NSA surveillance.
Source: https://habr.com/ru/post/192722/
All Articles