Cisco IOS Authentication
AAA (Authentication Authorization and Accounting) is an authentication and event accounting system built into the Cisco IOS operating system that provides users with secure remote access to Cisco network equipment. It offers various methods of user identification, authorization, as well as collecting and sending information to the server.
However, not only is aaa disabled by default; The configuration of this system is rather complicated. Defects in the configuration can lead either to an unstable, unsafe connection, or to the absence of any connection in principle. In this article, we will examine in detail the authentication configuration scheme using aaa .
In general, the authentication scheme is as follows:
')

Fig. 1. Authentication scheme (click to open in full size)

Fig. 2. Authentication scheme (continued, on click, opens in full size)
The scheme is divided into two parts not accidentally: the first describes the main path from the control lines (vty or con) to authentication methods, the second - the authentication methods themselves.
But first things first.
In this case, we are talking about the right side of the scheme (see Fig. 1).

Fig. 3. Authentication scheme without aaa new-model
As already mentioned, the default service aaa new-model is disabled. Connection to the device can be made either physically, by connecting via the console port (line console 0) without entering any credentials, or via the TELNET protocol (line vty). Moreover, in the latter case, even if you set the IP address on Cisco, you will not be able to access the device due to the lack of a password (the “line” authentication method, see Figure 3). If the password on the vty line is set, then the device will require you to only enter the password, which significantly reduces the security of the connection, since no login is required to enter; however, everything here, of course, also depends on the complexity of the password that you set up.
When executing the “login local” command, the device, after establishing a connection, will be required to enter a login and password to enter.
So: in the absence of aaa new-model, the maximum you can demand from Cisco IOS is using a password (authentication method “line”) and using a login and password from a local database (authentication method “local”).

Fig. 4. Authentication methods without aaa new-model
The advantage of the aaa configuration is that it contains many authentication methods (as opposed to the previous case). Enabling aaa occurs by adding the aaa new-model command in global configuration mode. Next is the choice of authentication methods. All methods are organized into lists that are assigned either a default value or a specific list name ( list-name ). Thus, on different types of lines ( aux, vty, con ... ) it is possible to “hang” different authentication methods, delimiting access between users.
An example of setting up aaa new-model and authentication lists:
As mentioned earlier, there are quite a few authentication methods in aaa. Let's try to list the most common:
• Local - the database of logins and passwords is stored on the network device itself. Requires username {password | secret}.
• Local-case - the same method as local, but case-sensitive when entering a login.
• Enable - authentication is required enable {password | secret} .
• Line - password is required for authentication (see Fig. 4 “line” authentication method).
• None - authentication is not required, access to the device is provided without entering a login and password.
• Group {tacacs + | radius} —connects servers with Tacacs + installed ( http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scftplus.html#wp1000899 ) or Radius ( http: // www. cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfrad.html#wp1000902 ) to extend the capabilities of the aaa configuration.
• Group {group-name} - allows you to configure a group of servers with Tacacs + or Radius installed or configure a private server group.
The most interesting authentication method is group: it is quite common in medium and large companies.
Below is an example of setting up the group method, which must be implemented in conjunction with authentication lists.
An example of adding a server group and a private Radius server:
This example shows that three Radius servers are configured. But the question arises: how will they work? The first thing that comes to mind is that, most likely, they will work in turn: if 192.168.1.1 is unavailable, 192.168.1.2 is accessed, etc. But this is not so. In this example, the following error was made: 192.168.1.1, 192.168.1.2, 192.168.1.3 are configured incorrectly, and therefore will not be used in authentication. This configuration lacks the Router (config) # radius-server host command for each of the servers. A more detailed description of the settings can be found on the vendor’s resources (for example: http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfrad.html ). Schematically it can be represented as follows:
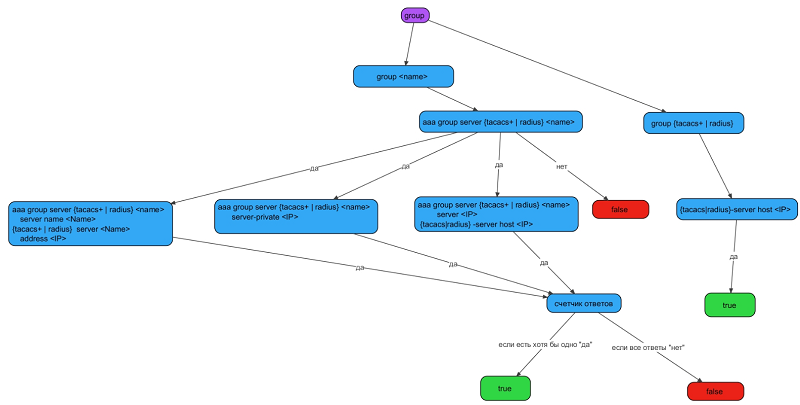
Fig. 5. Setting up authentication for the group method
Here, in fact, all the information that will help you successfully set up authentication on your network device. Follow the scheme, and if your settings resulted in “true”, then there will be happiness, and if “false” - look at the configuration carefully: perhaps there is an error somewhere or access to the device is possible without entering a login and password (authentication method “ none ”). I hope the article was helpful and helped you understand the nuances of the aaa configuration.
We, in turn, always try to automate such complex checks. As an example, the result of the MaxPatrol test against the AAA service:

Fig. 6. Requirement status
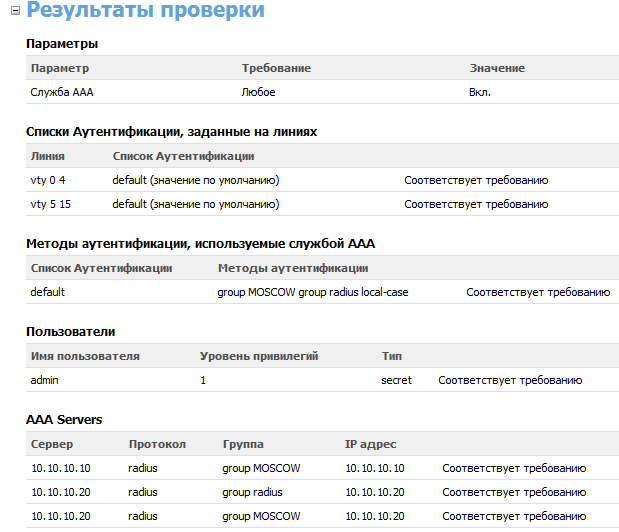
Fig. 7. Results of the requirement regarding the AAA service
Author : Maxim Habrat, Positive Research Research Center
However, not only is aaa disabled by default; The configuration of this system is rather complicated. Defects in the configuration can lead either to an unstable, unsafe connection, or to the absence of any connection in principle. In this article, we will examine in detail the authentication configuration scheme using aaa .
In general, the authentication scheme is as follows:
')

Fig. 1. Authentication scheme (click to open in full size)

Fig. 2. Authentication scheme (continued, on click, opens in full size)
The scheme is divided into two parts not accidentally: the first describes the main path from the control lines (vty or con) to authentication methods, the second - the authentication methods themselves.
But first things first.
Absence aaa new-model
In this case, we are talking about the right side of the scheme (see Fig. 1).

Fig. 3. Authentication scheme without aaa new-model
As already mentioned, the default service aaa new-model is disabled. Connection to the device can be made either physically, by connecting via the console port (line console 0) without entering any credentials, or via the TELNET protocol (line vty). Moreover, in the latter case, even if you set the IP address on Cisco, you will not be able to access the device due to the lack of a password (the “line” authentication method, see Figure 3). If the password on the vty line is set, then the device will require you to only enter the password, which significantly reduces the security of the connection, since no login is required to enter; however, everything here, of course, also depends on the complexity of the password that you set up.
When executing the “login local” command, the device, after establishing a connection, will be required to enter a login and password to enter.
So: in the absence of aaa new-model, the maximum you can demand from Cisco IOS is using a password (authentication method “line”) and using a login and password from a local database (authentication method “local”).

Fig. 4. Authentication methods without aaa new-model
Aaa new-model configuration
The advantage of the aaa configuration is that it contains many authentication methods (as opposed to the previous case). Enabling aaa occurs by adding the aaa new-model command in global configuration mode. Next is the choice of authentication methods. All methods are organized into lists that are assigned either a default value or a specific list name ( list-name ). Thus, on different types of lines ( aux, vty, con ... ) it is possible to “hang” different authentication methods, delimiting access between users.
An example of setting up aaa new-model and authentication lists:
Router(config)#aaa new-modelRouter(config)#aaa authentication login {default | list-name} method1 [method2…]Router(config)#line {vty | aux | con…} line-numbersRouter(config-line)#login authentication {default | list-name}Methods
As mentioned earlier, there are quite a few authentication methods in aaa. Let's try to list the most common:
• Local - the database of logins and passwords is stored on the network device itself. Requires username {password | secret}.
• Local-case - the same method as local, but case-sensitive when entering a login.
• Enable - authentication is required enable {password | secret} .
• Line - password is required for authentication (see Fig. 4 “line” authentication method).
• None - authentication is not required, access to the device is provided without entering a login and password.
• Group {tacacs + | radius} —connects servers with Tacacs + installed ( http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scftplus.html#wp1000899 ) or Radius ( http: // www. cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfrad.html#wp1000902 ) to extend the capabilities of the aaa configuration.
• Group {group-name} - allows you to configure a group of servers with Tacacs + or Radius installed or configure a private server group.
The most interesting authentication method is group: it is quite common in medium and large companies.
Below is an example of setting up the group method, which must be implemented in conjunction with authentication lists.
An example of adding a server group and a private Radius server:
Router(config)#aaa authentication login default group servradius1Router(config)#aaa group server radius servradius1Router(config-sg-radius)#server 192.168.1.1Router(config-sg-radius)#server 192.168.1.2Router(config-sg-radius)#server 192.168.1.3Router(config-sg-radius)#server-private 192.168.1.10This example shows that three Radius servers are configured. But the question arises: how will they work? The first thing that comes to mind is that, most likely, they will work in turn: if 192.168.1.1 is unavailable, 192.168.1.2 is accessed, etc. But this is not so. In this example, the following error was made: 192.168.1.1, 192.168.1.2, 192.168.1.3 are configured incorrectly, and therefore will not be used in authentication. This configuration lacks the Router (config) # radius-server host command for each of the servers. A more detailed description of the settings can be found on the vendor’s resources (for example: http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scfrad.html ). Schematically it can be represented as follows:

Fig. 5. Setting up authentication for the group method
Here, in fact, all the information that will help you successfully set up authentication on your network device. Follow the scheme, and if your settings resulted in “true”, then there will be happiness, and if “false” - look at the configuration carefully: perhaps there is an error somewhere or access to the device is possible without entering a login and password (authentication method “ none ”). I hope the article was helpful and helped you understand the nuances of the aaa configuration.
We, in turn, always try to automate such complex checks. As an example, the result of the MaxPatrol test against the AAA service:

Fig. 6. Requirement status

Fig. 7. Results of the requirement regarding the AAA service
Author : Maxim Habrat, Positive Research Research Center
Source: https://habr.com/ru/post/192668/
All Articles