Its Certificate Authority - in 5 OpenSSL teams
Why do you need it?
Imagine that we have two servers, they work for themselves, and periodically they want to ask each other something over the HTTP / HTTPS protocol.
The HTTP protocol is not secure and it is logical to use the HTTPS protocol to communicate between servers.
To organize such communication, we need 2 SSL certificates.
')
If the servers belong to the same organization, then it may be easier and safer to sign the certificates yourself, rather than buy.
Create our CA
The first command creates a root key.
openssl genrsa -out rootCA.key 2048 For me, the 2048 bit key is sufficient, if you want, you can use the 4096 bit key.
The second command creates a root certificate.
openssl req -x509 -new -key rootCA.key -days 10000 -out rootCA.crt Here you can answer questions as you please.
Country Name (2 letter code) [AU]: State or Province Name (full name) [Some-State]: Locality Name (eg, city) []: Organization Name (eg, company) [Internet Widgits Pty Ltd]: Organizational Unit Name (eg, section) []: Common Name (eg server FQDN or YOUR name) []: Email Address []: 10,000 days is its expiration date, roughly the certificate lives that google requires you to sign an android application for Google Play. If you are alarmist, sign up for a year or two.
Everything! Now we can create certificates for our servers and install the root certificate on our client machines.
Create a certificate signed by our CA
We generate the key.
openssl genrsa -out server101.mycloud.key 2048 Create a certificate request.
openssl req -new -key server101.mycloud.key -out server101.mycloud.csr It is important to specify the server name: domain or IP (for example, server101.mycloud domain)
Common Name (eg, YOUR name) []: server101.mycloud and sign the certificate request with our root certificate.
openssl x509 -req -in server101.mycloud.csr -CA rootCA.crt -CAkey rootCA.key -CAcreateserial -out server101.mycloud.crt -days 5000 Now clients need to install the root certificate rootCA.crt
rootCA.crt - you can give to friends, install, copy not servers, upload to public access
rootCA.key - should be kept private
Install Root Certificate
Windows
IE, Chrome - use Windows certificate repository.
My path to it is this:
Chrome - Settings - Manage Certificates ...
Choose tab Trusted Root Certificate Authorities - Import - rootCA.crt
restart chrome
FireFox on Windows has its own repository.
Java has its own repository.
Mac os x
Safari, FireFox, Chrome - use a system repository.
Launch KeyChain Access.
Go to the menu File - Import Items (login or System) - select the file rootCA.crt .
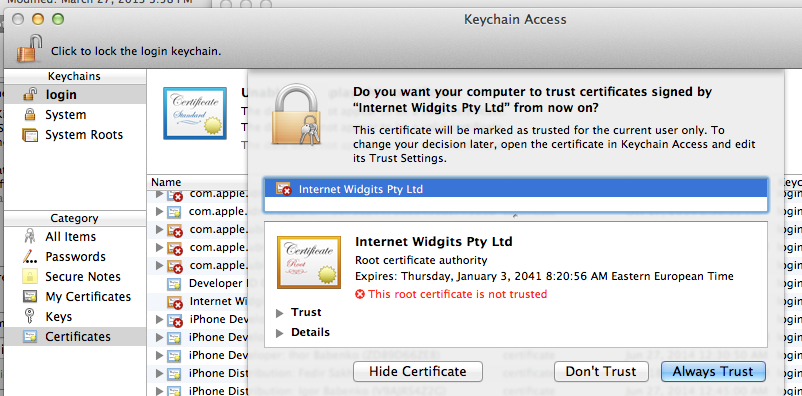
When they ask us, we answer - Always Trust.
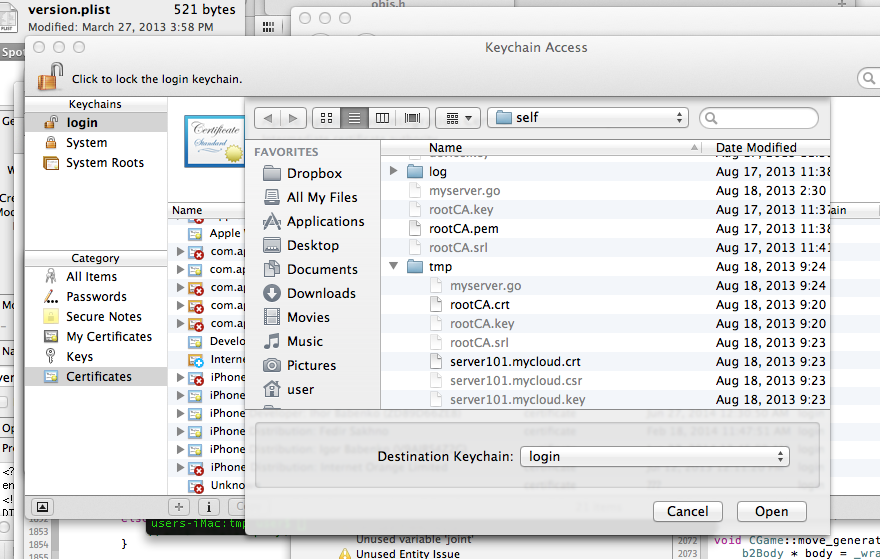
For your personal Safari, just select login.
In ubuntu
sudo mkdir /usr/share/ca-certificates/extra sudo cp rootCA.crt /usr/share/ca-certificates/extra/rootCA.crt sudo dpkg-reconfigure ca-certificates sudo update-ca-certificates Go server program
A server program on Go myserver.go that uses our signed certificate.
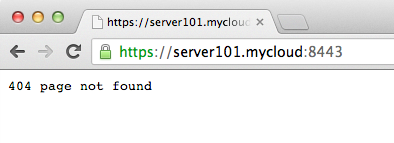
package main import ( "log" "net/http" ) func main() { http.Handle("/files/", http.StripPrefix("/files/", http.FileServer(http.Dir("./files/")))) go func() { log.Fatal(http.ListenAndServeTLS(":8443", "server101.mycloud.crt", "server101.mycloud.key", nil)) }() http.ListenAndServe(":8080", nil) } go run myserver.go running the program on server101.mycloud server, your browser will not swear on the page https: //server101.mycloud: 8443 / , and open it as a native if you have installed rootCA.crt in the system as a root certificate.
Server on python
import BaseHTTPServer, SimpleHTTPServer, ssl httpd = BaseHTTPServer.HTTPServer(('localhost', 8443), SimpleHTTPServer.SimpleHTTPRequestHandler) httpd.socket = ssl.wrap_socket (httpd.socket, certfile='server101.mycloud.pem', server_side=True) httpd.serve_forever() # cat server101.mycloud.key server101.mycloud.crt > server101.mycloud.pem # python myserver.py PS
I consider it important to mention that wildcard certificates are not safe, if an attacker takes possession of a wildcard certificate from one server, then this will put all other servers at risk. Virtual cloud servers are more popular than ever. Often background tasks run on separate virtual servers. The number of such servers is constantly growing. Its Certificate Authority is an important element of security for the entire system.
Source: https://habr.com/ru/post/192446/
All Articles