0day in the Any.DO extension - access to data on all sites (bypass gmail 2-steps auth). Public disclosure. ~ 500 thousand users affected
Introduction
We very often hear about vulnerabilities in browser plugins, especially Java. Security departments in companies aware of this, disable java / flash and other plugins from users, monitor updates, read security mailings. We hear about them so often that already enterprising people have created special sites with a count of days when 0day of the exploits would not be published - java-0day.com

Extensions VS Plugins
But there are also extensions that are embedded in browsers and interact with the data. Their safety was raised not so long ago, and the first, rather deep, research was conducted by Krzysztof Kotowicz . A brief retelling of his research and the found 0day vulnerability ( allowing access to data on all sites via XSS by sending a special letter to gmail ), which the vendor ignores - under the cat.
Extensions Vulnerability
We consider WebKit (Opera / Chrome).
In short - browser extensions are written in javascript using the browser API. They interact with the content, modify it (for example, center the images), collect additional statistics, encrypt mail, invoke additional utilities, etc. Before installation, permissions are asked for which sites / data they will have access to, and very often access to all sites is requested.
This is where the bottlenecks begin, when extensions incorrectly process the input data for them. Using the example of the Cr-gpg v 0.7.4 extension (gpg in gmail), we consider some vulnerabilities that have already been fixed in new versions.
')
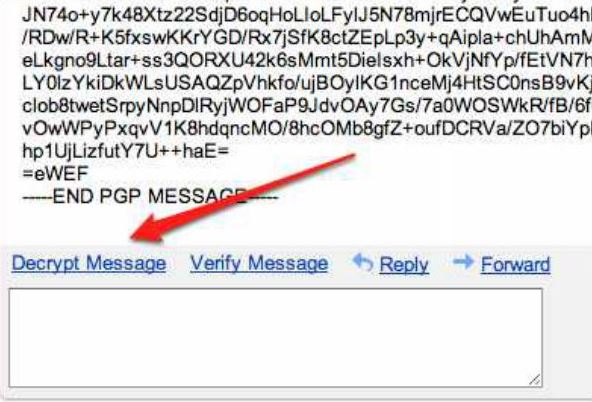
Letter decryption
When decrypting the letter, we could execute XSS, since the data was substituted "as is"
// content_script.js, line 26 $($(messageElement).children()([0]).html( tempMessage); And also to execute system commands, since for decryption there was an appeal to NPAPI

Team injection
This is all fixed, usually the vulnerabilities were in not very popular extensions.
0day to Any.DO (459,692 users)
There is a fairly popular extension - Any.DO , which I myself used (until recently). Regular TODO list, with some chip - parsit letters in gmail when they are opened and offers to add some new task. The extension substitutes its element in the gmail interface.
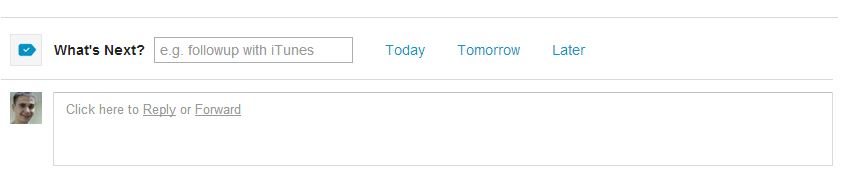
In which the XSS vulnerability was found. And now the main thing is not just XSS, which can be performed only in the context of this domain (mail.google.com), this XSS allows you to turn the user's browser into a proxy server, which we can use to access any site with the victim's browser data . Why? Because XSS runs in the context of an extension that has privileges to access all sites.
The vulnerability was reported to the developer, but there was no response . Log:
08/16/2013 - the first letter of vulnerability;
08/26/2013 - a tweet that was ignored;
08/31/2013 - repeated letter to the developer;
09/06/2013 - public disclosure of vulnerability, no response from the developer.
Krzysztof has developed two tools for conducting attacks through vulnerabilities in Google Chrome extensions (naturally, the vulnerabilities are repeated in Opera). One of them, the mosquito, will be shown in the next video (includes a demonstration of the circumvention of 2-factor Gmail authorization)
Links
Source: https://habr.com/ru/post/192294/
All Articles