Building a provider network on Cisco switches using Option 82 and Dynamic ARP Inspection
Prologue
On Habré there were quite a few topics describing certain options for building provider networks, including using the technologies specified in the header. In part, they helped me in solving my task, but I had to dig a lot myself. I want to share what happened and try to save time for followers.
So, the task setting:
It is necessary to organize a network that is as convenient for the end user as possible, and also convenient (in terms of minimum load on technical support) and safe (in terms of fraud) for the operator. In addition, the network should be inexpensive. Someone will argue that Cisco and “inexpensive” are incompatible concepts, however, End of Life also suits old men, which can be purchased at very affordable prices.
')
To ensure user convenience, the following options were dropped:
- static assignment of ip-addresses is inconvenient for the user, the address needs to be recorded somewhere, users who have lost the address are called to tech support
- dhcp with mac-address binding is inconvenient for the user, when changing the device, you need to re-register it with the provider or change the mac on it.
- all kinds of tunnels, mainly pptp - requires configuration at the client, forgotten logins and passwords
Of all the options considered for the user, the most convenient option is with DHCP, but for the provider there are a number of difficulties:
Binding on mac is inconvenient, since you will have to re-register new mac-addresses. User authentication in billing only by ip-address also seems unreliable at first glance, a cunning user can manually set his neighbor’s ip-address and introduce confusion. However, there is a solution and it is built on technologies from the title of the article - option 82 and dynamic arp inspection
Who cares a solution - I ask under the cat
Decision
The DHCP server for issuing addresses will be guided by option 82, which determines from which physical port of the switch a request for an address came. Thus, we achieve that Vasya Pupkin from the 14th apartment, whose cable is connected to the 7th port of our SW-01 switch, will always receive the address 10.10.1.7, for example, regardless of what device he connects to his cable. This approach allows us to identify Vasya Pupkin only by IP-address, but there is a problem. Neighbor Jora, who does not want to pay for the Internet, will put his hands on Vasya Pupkin’s address, will create an IP address conflict on the network and will use the Internet at the expense of Vasya.
To prevent this from happening, there is Dynamic ARP Inspection technology. The essence of the technology comes down to checking the mac + ip bundles received from the DHCP server and comparing them with ARP requests arriving at the port. Thus, even if the neighbor Jora set himself the same mac and IP as Vasya’s, the switch will check if DHCP has sent such an IP to this port on this port. If not issued, the packet will be dropped.
Actually setting
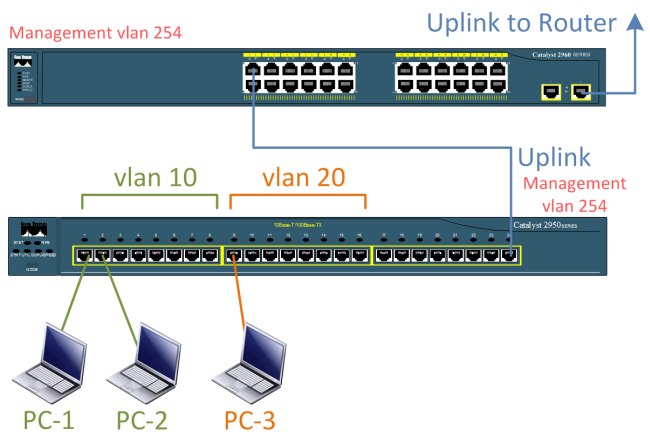
We have two switches at our disposal: Cisco 2950-24 and Cisco 2960-24-TT-L
Switch 2950 will be used to connect subscribers. It is configured with Management vlan 254 for management.
Switch IP - 10.0.254.10 , mac - 00: 11: 92: 1B: 3A: 00
The 2960 switch will act as a DHCP server and handle the ARP inspection task.
Switch IP - 10.0.254.2 , mac - 00: 16: C8: D7: D2: 80
MAC can be viewed with the show version command
cisco WS-C2950-24 (RC32300) processor (revision P0) with 19911K bytes of memory. Processor board ID FOC0825Z1GD Last reset from system-reset Running Standard Image 24 FastEthernet/IEEE 802.3 interface(s) 32K bytes of flash-simulated non-volatile configuration memory. Base ethernet MAC Address: 00:11:92:1B:3A:00 The 2950 switch does not support Dynamic ARP Inspection, but we can solve this problem on the upstream switch. In the example, Cisco 2960-24-TT-L is used as such a switch, although it is more appropriate to use an L3 switch, for example, 3550-12T or 3550-12G , then it can solve the Inter-VLAN Routing task too.
And so, on the C2950, we configure the following:
- In the global configuration mode, we indicate the need to add options to the dhcp-relay message:
ip dhcp relay information option - In the settings of the management interface, specify that DHCP requests should be sent to the 2960th switch at 10.0.254.2
interface Vlan254 ip address 10.0.254.10 255.255.255.0 ip helper-address 10.0.254.2 - In global configuration mode, enable DHCP snooping for all our vlans.
ip dhcp snooping vlan 10 ip dhcp snooping vlan 20 ip dhcp snooping vlan 254 ip dhcp snooping - Determine that DHCP offer is allowed only from port 24, to which the upstream 2960 with a DHCP server is connected.
interface FastEthernet0/24 ip dhcp snooping trust
Configuration C2960 is a bit more complicated:
- For each user, you must create an entry ip dhcp class
ip dhcp class user01 remark SW2950-1 port 01 relay agent information relay-information hex 01060004000a0001020800060011921b3a00
It is enough to specify only relay-information in the class, but for convenience it is also recommended to use the comment remark , in which you can write, for example, subscriber data.
Here the most important thing is to understand the principle of forming the hex-string. This is 18 bytes contained in option 82
Its content consists of two fields: circuit-id and remote-id
The circuit-id contains the vlan number and the physical port number from which the dhcp request came.
The remote-id contains the mac-address of the switch that sent this request.
This line can be extracted with the wireshark analyzer, but it is inconvenient to do this for each subscriber, so let's consider how to generate it.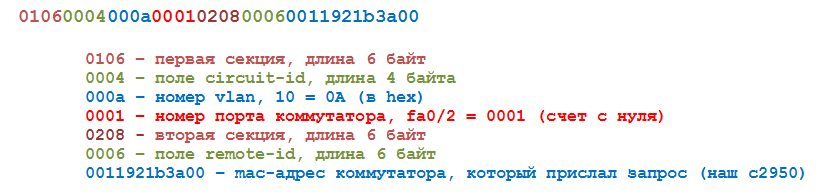
- After creating dhcp-classes for subscribers, we will configure pools of addresses for each vlan
The rental time is 5 minutes. This is necessary so that when a new device with a different address is connected to its port, the subscriber quickly gets the address to it. Otherwise there will be an error that this pool is exhausted, since there is only 1 address in it. In addition, the rest of the dhcp-pool settings, such as gateway, dns, etc., are omitted in the example.ip dhcp pool vlan10 network 10.0.10.0 255.255.255.0 lease 0 0 5 class user01 address range 10.0.10.11 10.0.10.11 class user02 address range 10.0.10.12 10.0.10.12 - It is necessary to configure the corresponding ip-interfaces for each pool on the switch. This is done via interface vlan
Despite the fact that the C2960 is a second-level switch, it allows you to keep several ip interfaces active, but cannot route traffic between them.interface Vlan10 ip address 10.0.10.2 255.255.255.0 ! interface Vlan20 ip address 10.0.20.2 255.255.255.0 ! interface Vlan254 ip address 10.0.254.2 255.255.255.0 - On this switch, we also need to configure dhcp-snooping, since this option forms the base for mapping the issued IP addresses to the mac addresses.
Using the ip dhcp snooping database command, we will determine the storage location for the database, in the example it will be stored in the dhcp file on the flash. You can also specify ftp, tftp, http, https, scp and other url as storage locations.
The ip dhcp snooping information option allow-untrusted command allows receiving requests with option 82 from all switch ports.ip dhcp snooping vlan 10 ip dhcp snooping vlan 20 ip dhcp snooping information option allow-untrusted ip dhcp snooping database flash:dhcp ip dhcp snooping - At the moment, we have a binding ip-address to the physical port of the switch. It remains to configure Dynamic ARP Inspection. This is done in one simple command:
ip arp inspection vlan 10,20
Proof of concept
Let's check the address assignment to the client connected to the 9th switch port. The port is in the 20th vlan, according to our scheme, the client should receive the address 10.0.20.9
Let's form the value hex: 01060004 0014 0008 02080006 0011921b3a00
where 0014 is the 20th vlan,
0008 - 9th switch port
0011921b3a00 - his mac.
ip dhcp class user09 remark SW2950-1 port 09 relay agent information relay-information hex 0106000400140008020800060011921b3a00 ip dhcp pool vlan20 network 10.0.20.0 255.255.255.0 lease 0 0 5 class user09 address range 10.0.20.9 10.0.20.9 So this exchange looks like in wireshark:
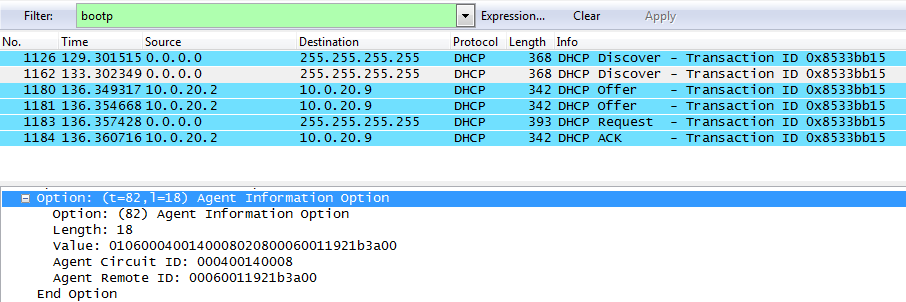
And this is what the output of the debug ip dhcp server events command looks like.
2d00h: DHCPD: Sending notification of DISCOVER: 2d00h: DHCPD: htype 1 chaddr 000a.e45b.dcc6 2d00h: DHCPD: remote id 00060011921b3a00 2d00h: DHCPD: circuit id 000400140008 2d00h: DHCPD: interface = Vlan20 2d00h: DHCPD: class id 4d53465420352e30 2d00h: DHCPD: out_vlan_id 0 2d00h: DHCPD: DHCPOFFER notify setup address 10.0.20.9 mask 255.255.255.0 2d00h: DHCPD: Sending notification of ASSIGNMENT: 2d00h: DHCPD: address 10.0.20.9 mask 255.255.255.0 2d00h: DHCPD: htype 1 chaddr 000a.e45b.dcc6 2d00h: DHCPD: lease time remaining (secs) = 300 2d00h: DHCPD: interface = Vlan20 2d00h: DHCPD: out_vlan_id 0 000a.e45b.dcc6 - client mac-address
Now we connect another laptop to the same port.
2d00h: DHCPD: Sending notification of DISCOVER: 2d00h: DHCPD: htype 1 chaddr 089e.012b.6ce1 2d00h: DHCPD: remote id 00060011921b3a00 2d00h: DHCPD: circuit id 000400140008 2d00h: DHCPD: interface = Vlan20 2d00h: DHCPD: class id 4d53465420352e30 2d00h: DHCPD: out_vlan_id 0 2d00h: DHCPD: no free address within the address range for class user09 in pool vlan20 2d00h: DHCPD: Sending notification of ASSIGNMENT FAILURE: First, we receive a message stating that there are no free addresses in the pool (since 5 minutes allocated to renting this address to another Mac have not yet expired).
However, after a while we get the address we need, but already for a client with a poppy 08-9e-01-2b-6c-e1
2d00h: DHCPD: Sending notification of DISCOVER: 2d00h: DHCPD: htype 1 chaddr 089e.012b.6ce1 2d00h: DHCPD: remote id 00060011921b3a00 2d00h: DHCPD: circuit id 000400140008 2d00h: DHCPD: interface = Vlan20 2d00h: DHCPD: class id 4d53465420352e30 2d00h: DHCPD: out_vlan_id 0 2d00h: DHCPD: Adding binding to radix tree (10.0.20.9) 2d00h: DHCPD: Adding binding to hash tree 2d00h: DHCPD: assigned IP address 10.0.20.9 to client 0108.9e01.2b6c.e1. (316 0) 2d00h: DHCPD: DHCPOFFER notify setup address 10.0.20.9 mask 255.255.255.0 2d00h: DHCPD: Sending notification of ASSIGNMENT: Now we’ll check if our client’s neighbor, connected to switch port 10, can manually set the address 10.0.20.9
Since the Cisco 2950 does not support Dynamic ARP Inspection, this technology needs to be configured on the Cisco 2960 upstream switch.
The show ip dhcp snooping binding command on the C2960 will show the binding of IP addresses to mac
MacAddress IpAddress Lease(sec) Type VLAN Interface ------------------ --------------- ---------- ------------- ---- -------------------- 08:9E:01:2B:6C:E1 10.0.20.9 288 dhcp-snooping 20 FastEthernet0/1 Total number of bindings: 1 FastEthernet0 / 1 is a 2960 switch interface, which includes a downstream 2950.
We will connect a computer with the manually configured address 10.0.20.9 to the 10th port of the C2950
And right there we will see an error notification, from which it can be seen that it occurred in the 20th vlan on the 1st switch port. In addition, we see the ip and poppy addresses that caused the error. 000a.e45b.dcc6 / 10.0.20.9 /
2d01h: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa0/1, vlan 20.([000a.e45b.dcc6/10.0.20.9/0000.0000.0000/10.0.20.9/23:48:25 EEST Mon Sep 2 2013]) You can find out who specifically tried to cheat by visiting the C2950 switch and looking at the switching table
SW2950-1#show mac-address-table Mac Address Table ------------------------------------------- Vlan Mac Address Type Ports ---- ----------- -------- ----- 20 000a.e45b.dcc6 DYNAMIC Fa0/10 20 089e.012b.6ce1 DYNAMIC Fa0/9 We see that the mac we are interested in is hanging on port 10.
On this, perhaps, everything, additional information can be found in these articles:
Features and DHCP settings on Cisco routers
Features and DHCP settings on Cisco routers (Part 2)
IPoE, as well as Client-VLAN and DHCP Option 82
IPoE problem - I'd add from myself that there is just no problem if everything is set up correctly.
The link-level attack of ARP-spoofing and how to protect a Cisco switch is a good article showing another benefit from Dynamic ARP Inspection - improving network security in general.
Source: https://habr.com/ru/post/192136/
All Articles