Typical vulnerabilities on sites with statistics
This topic will be devoted to:
- vulnerability statistics
- administration reactions (speed and adequacy)
- danger
and all sorts of other factors. Examples will be given.
What was the impetus
Fasting can begin like this: “it was evening, there was nothing to do.” Or: “They brought back the past successes (the last topic was a plus)”.
In short, I have absolutely nothing to do in the summer. And therefore, while my last project (habrascanner) is slowly being sawed, I thought quickly to sketch the next post. A little content is already above. We analyze it (fasting in the sense).
Very important: all the data given in the topic is rather approximate. I checked more than 1000 sites, about 200 were vulnerable.
')
Search process
By the way, whoever is interested, the sites were found completely random and checked literally by hand.
Google was searching for me. I wrote a small python script that entered the search query (the list of queries was initially taken) and clicked “I’m feeling lucky!” And then copied this data into the textbook that I later used for pentesting.
By the way, there were 1322 requests, and therefore the same number of sites. From here it is possible to calculate that about 15% of them are vulnerable.
general Statistics

Vulnerable module
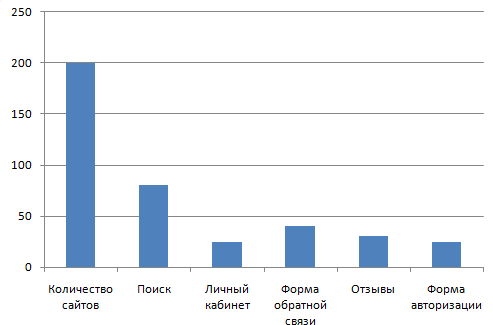
Type of Vulnerability
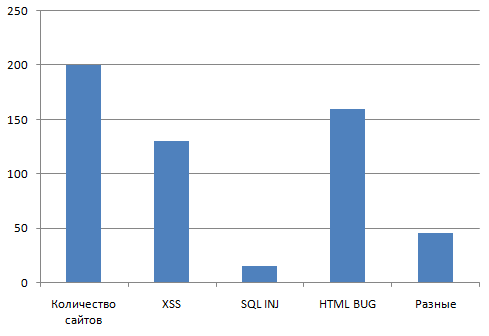
I have to clarify that HTMLBUG = changing the html view using some form, but without XSS (tags are still filtered).
Examples
Again, I simply have to say here that there will be no real examples. It may simply be dangerous for the site studied.
But why.
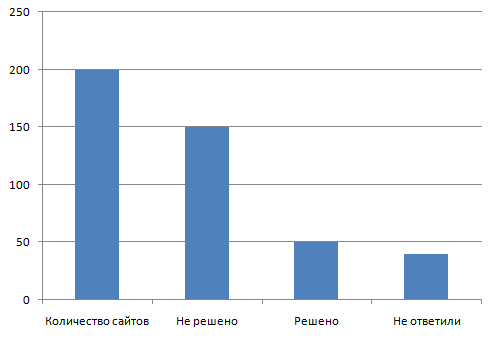
Here “Not Solved” is included and “Not answered”.
In addition, in most of the projects I was approached rudely, scornfully and even threatened ...
It looks something like this.
The words in the histogram are deliberately distorted in order to somehow soften my calculations.
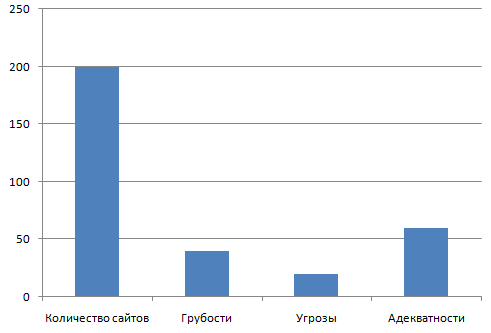
The rest either did not answer, or got off with a dry "Thank you."
Separately, I want to highlight the employees of the online store kronya.ru, not only did they answer me within 15 minutes (on Friday), and ALL my complaints were resolved within an hour.
In addition, I highlight the user art_karetnikov , his site was checked by me by chance, and, to my regret, and to everyone's joy, did not at all contain the errors I checked.
And now finally to the examples.
I will give a couple of examples. I think most of the users of Habr can find and use XSS, so this is brief.
http://******************d=%22%3E%3Cscript%3Ealert%280%29%3C%2Fscript%3Ejs, outputting an alert. ">
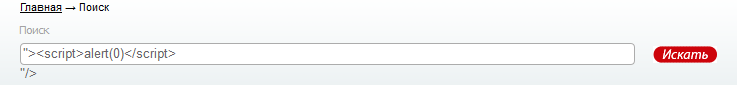
(The window is already closed) That is, here and XSS and weirdness with dis. (well, strangeness with html is always observed where it came out to break through the input, so I will no longer link them together).
At one of the sites there was a form, after which its contents were present on the site as many as 5 (!) Times. And it looked something like this.


An incredible amount of not filtered requests I found on the Internet.
Most of all I liked this one. By the way, it is located on a large site of a Moscow store.

Just a quote in one correct field. On this site, I was never answered ...
Problem solution
For the most part, all these vulnerabilities are encountered on sites with frameworks (found documentation in root folders) or with CMS (found signs of using ©). Therefore, the solution is simple as boots. Switch the filtering switch to the ON position. Or add somewhere 2 words ...
Why all this?
I hope this topic will be able to:
- Make users be more attentive to links.
- Admins to be more attentive to their creations.
- Managers to be kinder to those with whom they communicate.
- Programmers to be adequate and understand when they are trying to help, and not to crap (forgive me the habrasoobschestvo for this word).
PS In conclusion, I want to say:
"Dear habrovchane, I, undoubtedly, like to check websites for vulnerabilities and learn something new for myself."
If someone is interested, I could check your sites, and then add to the list with specific examples (I’m not sure there is enough, I think), with your permission and, of course, after the correction.
PSS I hope my article will be a useful read for someone. Someone will serve as a lesson, or guide to action (I hope the admins, not hackers). And in general, I hope the article will be worthy of habra.
UPD.
Hello anonymous miners! (I would like to comment)
UPD2.
Screenshots of real examples, screenshots of correspondence with admins (of course, podzaterty), and rounders instead of histograms I will do later. (you need to prepare all this)
Source: https://habr.com/ru/post/192122/
All Articles