Attachment of the link layer ARP-spoofing and how to protect the Cisco switch
This article is not a guide for kulhackers. Everything written below is part of a Cisco SECURE course study.
In this article, I will show how in practice to conduct a data link attack on a Cisco switch, and also show how to protect my network from this. For the lab stand, I used the Cisco 881 and the Catalyst 3750G.
Probably everyone who has come across a bit with networks knows what ARP is.
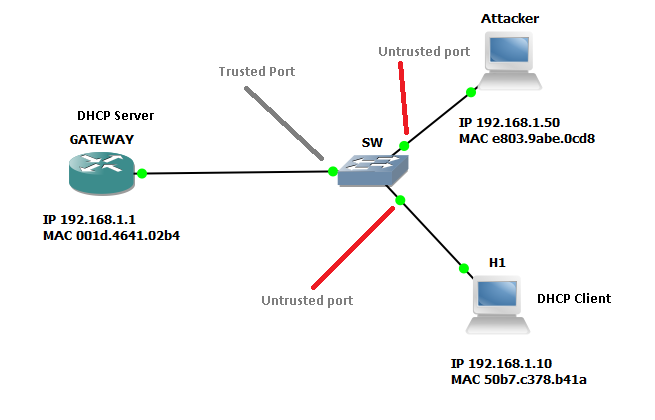
Briefly recall. ARP is used to convert an IP address to a MAC address. Consider this topology:
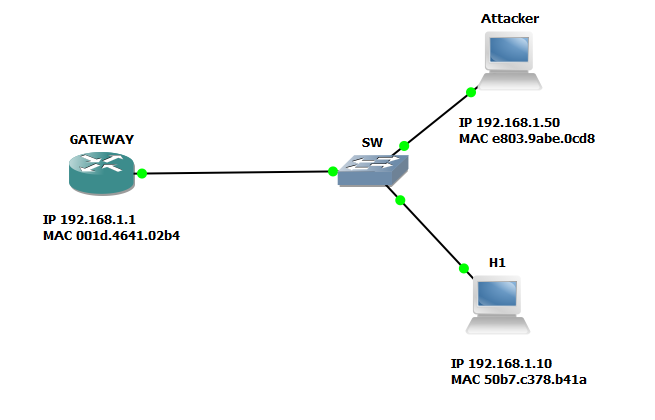
What happens if you ping the Gateway from the H1 host? First of all, the ARP protocol will work. H1 will send a broadcast request (ARP-request), which will indicate the MAC and IP of the H1 host and the recipient IP (GATEWAY). Then GATEWAY will receive a request and seeing that the recipient's IP field contains its address, appends its MAC to it and sends an ARP-reply reply. Host H1 receives the answer and puts it into the ARP table.
How can I intercept traffic going from H1 to GATEWAY? Suppose an attacker (ATTACKER) is in the same broadcast domain as GATEWAY and H1. If an attacker launches a sniffer, for example, Wireshark, then he will not see anything interesting in the sniffer, except for his broadcasts and other proprietary information. You can use ARP weaknesses to intercept traffic. This protocol has no protection, no authentication requests. And it is also possible to send ARP responses without ARP requests, this is the so-called gratuitous-ARP.
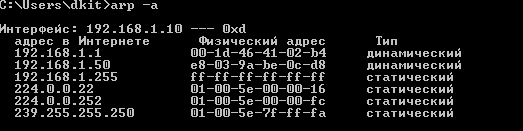
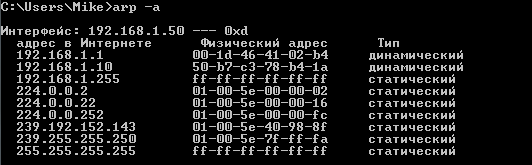
This is just what you need. We will use Cain & Abel software for the attack, but first we will look at the ARP tables on the H1 host and on ATTACKER:
')
H1 ARP table
ATTACKER ARP table
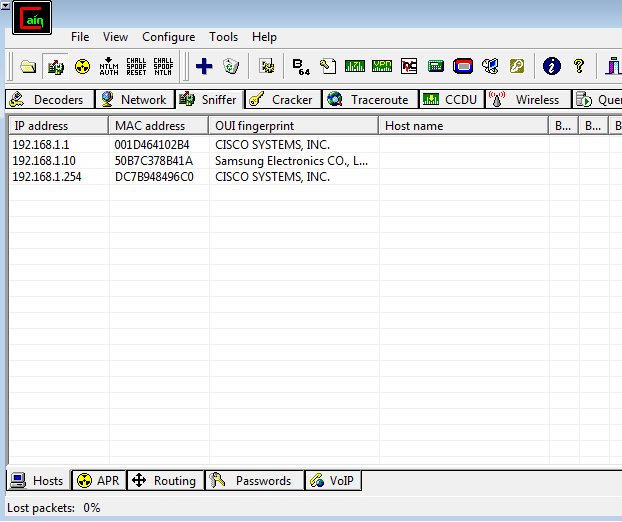
Next, run Cain & Abel, turn on the sniffer and add all the hosts from the broadcast domain.
Next, go to the ARP tab, click + and select the gateway address and the host from which we will intercept traffic.
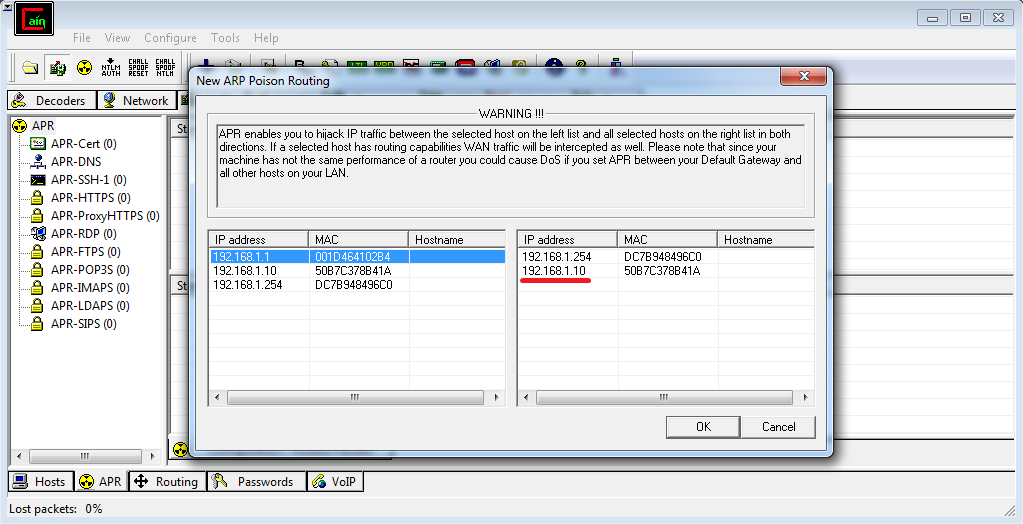
We press the ARP-poisoning button and the process of changing the ARP table on the H1 host has started.
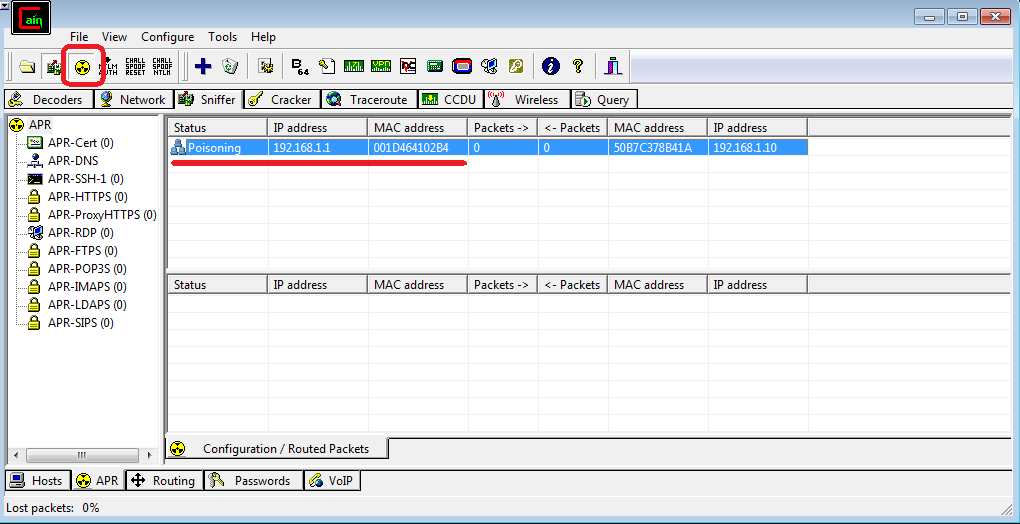
Now let's see how the ARP table has changed on the H1 host.
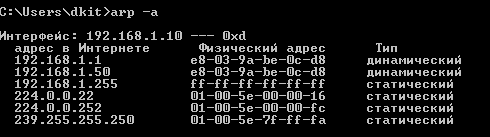
We see the substitution of the MAC address for IP 192.168.1.1
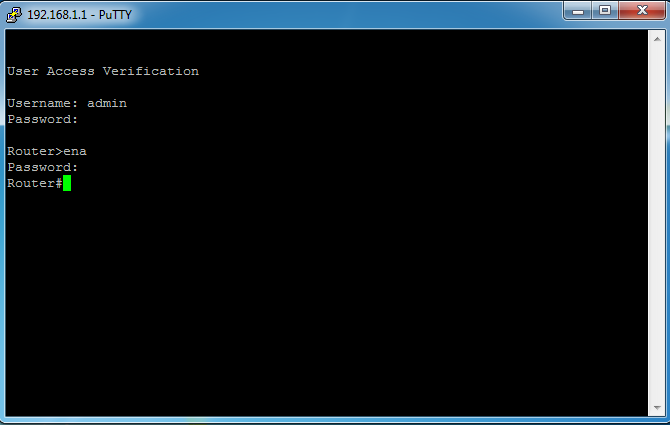
Now we will run putty on the H1 host and try to access GATEWAY via the insecure telnet protocol. Since the telnet protocol transmits data in plain text, the attacker in the sniffer will have to see all the necessary information, that is, the login and password. Go and enter the login / password and password enable.
Now on ATTACKER in sniffer, Passwords tab. It can be seen that some information caught
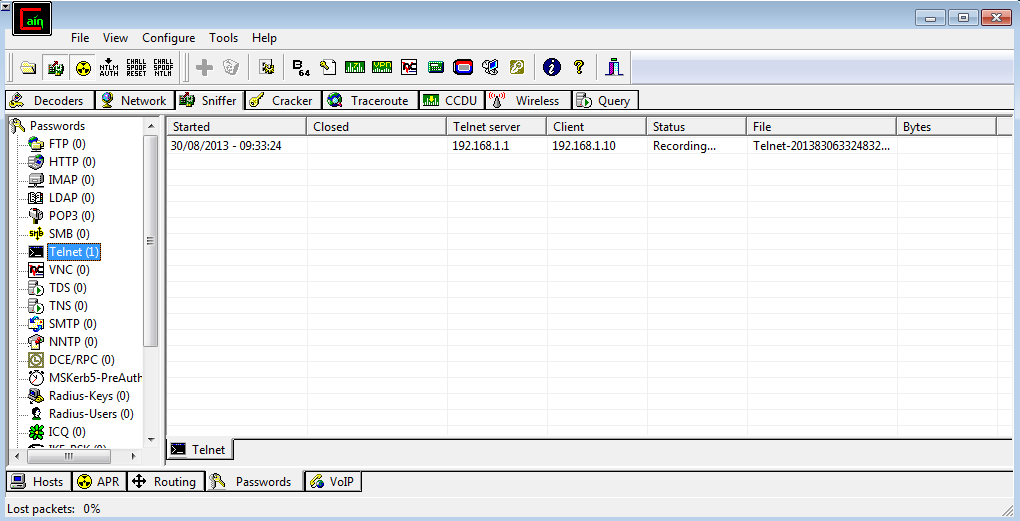
We look at this entry and see the text of this content:
Everything. Password from telnet intercepted.
And now the most important thing. How to protect your network from such attacks. We come to the aid of the tool Dynamic ARP Inspection (DAI).
DAI is designed to adjust ARP requests, that is, decides which ones to skip and which ones to drop. Roughly speaking, DAI fully protects the network from ARP-spoofing attacks, which occur at the link level, due to the unprotectedness of the ARP protocol.
A little bit about how DAI works. In order for this mechanism to work, we need to use DHCP on the network and DHCP snooping must be enabled on the switch. If the network uses static addressing, then DAI will not work.
How does DHCP snooping work? Suppose we have a DHCP server configured for GATEWAY. The ATTACKER attacker decided to raise his dhcp server and distribute some of his addresses. DHCP snooping is designed to adjust requests and will discard requests from the attacker's server. Everything is very simple. There are Untrusted and Trusted ports. With a reliable port, we assign the port that leads to GATEWAY, since we will have it as an authorized DHCP server. All other ports will be unreliable and server requests from them will be dropped.
At the same time, a dchp snooping database address matching table is built. We turn on the SW switch DHCP snooping function
On the port looking towards GATEWAY
We look what happened
And see what appears in the correspondence table.
Now, if an attacker wants to become a dhcp server, his switch will discard requests.
Based on the dhcp snooping database, which contains the correspondence of all MAC and IP addresses and the Dynamic ARP Inspection mechanism will work.
Let's go to the setting. On the Cisco switch, this tool is enabled for each vlan separately. In our case, it is enough to give the command on the SW switch:
Both the host and the gateway are in vlan 1. DAI for switch ports has two settings: Trusted and Untrusted. By default, all switch ports
Untrusted, that is unreliable. The port that goes to the gateway or the port to which another switch is connected to the trunk can be made Trusted, then ARP requests coming through it will be considered reliable.
Now repeat the attack from the beginning. We try to do ARP-poisoning through Cain & Abel. The attack fails and the following entries appear in the switch logs:
The switch discards "incorrect" arp requests. Now the attacker will not be able to intercept.
Let's include another additional DAI check.
This option allows you to restore the port and the state of errdisabled after 300 seconds. If, of course, the MAC-IP mismatch continues on this port, the port will not be restored.
You can view the trusted and untrusted ports and statistics with the command
That's all.
Thanks for attention.
UPD added about dhcp-snooping
In this article, I will show how in practice to conduct a data link attack on a Cisco switch, and also show how to protect my network from this. For the lab stand, I used the Cisco 881 and the Catalyst 3750G.
Probably everyone who has come across a bit with networks knows what ARP is.
Briefly recall. ARP is used to convert an IP address to a MAC address. Consider this topology:

What happens if you ping the Gateway from the H1 host? First of all, the ARP protocol will work. H1 will send a broadcast request (ARP-request), which will indicate the MAC and IP of the H1 host and the recipient IP (GATEWAY). Then GATEWAY will receive a request and seeing that the recipient's IP field contains its address, appends its MAC to it and sends an ARP-reply reply. Host H1 receives the answer and puts it into the ARP table.
How can I intercept traffic going from H1 to GATEWAY? Suppose an attacker (ATTACKER) is in the same broadcast domain as GATEWAY and H1. If an attacker launches a sniffer, for example, Wireshark, then he will not see anything interesting in the sniffer, except for his broadcasts and other proprietary information. You can use ARP weaknesses to intercept traffic. This protocol has no protection, no authentication requests. And it is also possible to send ARP responses without ARP requests, this is the so-called gratuitous-ARP.
This is just what you need. We will use Cain & Abel software for the attack, but first we will look at the ARP tables on the H1 host and on ATTACKER:
')
H1 ARP table

ATTACKER ARP table

Next, run Cain & Abel, turn on the sniffer and add all the hosts from the broadcast domain.

Next, go to the ARP tab, click + and select the gateway address and the host from which we will intercept traffic.

We press the ARP-poisoning button and the process of changing the ARP table on the H1 host has started.

Now let's see how the ARP table has changed on the H1 host.

We see the substitution of the MAC address for IP 192.168.1.1
Now we will run putty on the H1 host and try to access GATEWAY via the insecure telnet protocol. Since the telnet protocol transmits data in plain text, the attacker in the sniffer will have to see all the necessary information, that is, the login and password. Go and enter the login / password and password enable.

Now on ATTACKER in sniffer, Passwords tab. It can be seen that some information caught

We look at this entry and see the text of this content:
============================================
=== Cain's Telnet sniffer generated file ===
============================================
ya ya yae yae
User Access Verification
Username: ya ya ya ya'yae ya ya ya P P yar yu yaryayu ya y y XTERMyarya y yay $ admin
Password: cisco
Router> eennaa
Password: Cisco
Everything. Password from telnet intercepted.
And now the most important thing. How to protect your network from such attacks. We come to the aid of the tool Dynamic ARP Inspection (DAI).
DAI is designed to adjust ARP requests, that is, decides which ones to skip and which ones to drop. Roughly speaking, DAI fully protects the network from ARP-spoofing attacks, which occur at the link level, due to the unprotectedness of the ARP protocol.
A little bit about how DAI works. In order for this mechanism to work, we need to use DHCP on the network and DHCP snooping must be enabled on the switch. If the network uses static addressing, then DAI will not work.
How does DHCP snooping work? Suppose we have a DHCP server configured for GATEWAY. The ATTACKER attacker decided to raise his dhcp server and distribute some of his addresses. DHCP snooping is designed to adjust requests and will discard requests from the attacker's server. Everything is very simple. There are Untrusted and Trusted ports. With a reliable port, we assign the port that leads to GATEWAY, since we will have it as an authorized DHCP server. All other ports will be unreliable and server requests from them will be dropped.

At the same time, a dchp snooping database address matching table is built. We turn on the SW switch DHCP snooping function
ip dhcp snooping vlan 1ip dhcp snooping database flash:/dhcp-snoop.dbip dhcp snoopingOn the port looking towards GATEWAY
SW(config-if)# ip dhcp snooping trust
We look what happened
SW # sh ip dhcp snooping
Switch DHCP snooping is enabled
DHCP snooping is configured on the following VLANs:
one
DHCP snooping is configured on the following Interfaces:
Insertion of option 82 is enabled
circuit-id format: vlan-mod-port
remote-id format: MAC
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Interface Trusted Rate limit (pps)
- - - FastEthernet1 / 0/47 yes unlimited
And see what appears in the correspondence table.
SW # sh ip dhcp snooping binding
MacAddress IpAddress Lease (sec) Type VLAN Interface
- - - - - - E8: 03: 9A: BE: 0C: D8 192.168.1.50 26268 dhcp-snooping 1 FastEthernet1 / 0/13
50: B7: C3: 78: B4: 1A 192.168.1.10 69421 dhcp-snooping 1 FastEthernet1 / 0/1
Total number of bindings: 2
Now, if an attacker wants to become a dhcp server, his switch will discard requests.
Based on the dhcp snooping database, which contains the correspondence of all MAC and IP addresses and the Dynamic ARP Inspection mechanism will work.
Let's go to the setting. On the Cisco switch, this tool is enabled for each vlan separately. In our case, it is enough to give the command on the SW switch:
SW(config)#ip arp inspection vlan 1Both the host and the gateway are in vlan 1. DAI for switch ports has two settings: Trusted and Untrusted. By default, all switch ports
Untrusted, that is unreliable. The port that goes to the gateway or the port to which another switch is connected to the trunk can be made Trusted, then ARP requests coming through it will be considered reliable.
SW(config-if)#ip arp inspection trustNow repeat the attack from the beginning. We try to do ARP-poisoning through Cain & Abel. The attack fails and the following entries appear in the switch logs:
18:11:19:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa1 / 0/1, vlan 1. ([50b7.c378.b41a / 192.168.1.10 / 0000.0000.0000 / 192.168.1.1 / 18 : 11: 19 UTC Mon Mar 1 1993])
18:11:19:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/1, vlan 1. ([50b7.c378.b41a / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:19 UTC Mon Mar 1 1993])
18:11:19:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/13, vlan 1. ([e803.9abe.0cd8 / 192.168.1.1 / 50b7.c378.b41a / 192.168.1.10 (18: 11: 19 UTC Mon Mar 1 1993])
18:11:19:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/13, vlan 1. ([e803.9abe.0cd8 / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:19 UTC Mon Mar 1 1993])
18:11:21:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/1, vlan 1. ([50b7.c378.b41a / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:21 UTC Mon Mar 1 1993])
18:11:21:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/13, vlan 1. ([e803.9abe.0cd8 / 192.168.1.1 / 50b7.c378.b41a / 192.168.1.10 (18: 11: 21 UTC Mon Mar 1 1993])
18:11:21:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/13, vlan 1. ([e803.9abe.0cd8 / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:21 UTC Mon Mar 1 1993])
18:11:24:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Fa1 / 0/1, vlan 1. ([50b7.c378.b41a / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:24 UTC Mon Mar 1 1993])
18:11:25:% SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Fa1 / 0/1, vlan 1. ([50b7.c378.b41a / 192.168.1.10 / 001d.4641.02b4 / 192.168.1.1 / 18:11:25 UTC Mon Mar 1 1993])
The switch discards "incorrect" arp requests. Now the attacker will not be able to intercept.
Let's include another additional DAI check.
SW(config)#errdisable recovery cause arp-inspectionThis option allows you to restore the port and the state of errdisabled after 300 seconds. If, of course, the MAC-IP mismatch continues on this port, the port will not be restored.
You can view the trusted and untrusted ports and statistics with the command
SW#show ip arp inspection interfacesThat's all.
Thanks for attention.
UPD added about dhcp-snooping
Source: https://habr.com/ru/post/192022/
All Articles